Explore Python for MITRE PRE-ATT&CK, network scanning and Scapy
MITRE PRE-ATT&CK
The MITRE ATT&CK® framework is a tool developed by the MITRE Corporation to help build understanding of how cyberattacks work. It breaks the cyberattack lifecycle into several stages (called tactics) and describes various means of achieving the goals of each tactic.
Previously, MITRE PRE-ATT&CK was its own matrix within the MITRE ATT&CK framework; however, a recent edit revised it into the first two columns of the enterprise matrix. The tactics associated with MITRE PRE-ATT&CK are reconnaissance and resource development, covering what an attacker may do before initiating an attack.
When implementing PRE-ATT&CK functionality in Python, most of the focus is on the reconnaissance tactic. This is because Python makes it possible to automate some reconnaissance functionality, and the steps needed for resource development are more difficult to predict and automate.
Learn Python for Cybersecurity
Introduction to network scanning
Network scanning is one of the techniques used to accomplish reconnaissance goals in MITRE ATT&CK. Scapy is a useful tool for implementing reconnaissance in Python.
Introduction to Scapy
Scapy is one of the many packages available for the Python programming language. Scapy is an invaluable tool for cybersecurity because it makes it possible to build custom packets and send them over the network and to sniff, dissect and analyze received traffic.
Scapy is useful for reconnaissance because it provides all of the necessary building blocks for building a custom network or vulnerability scanner like Nmap or Nessus. A penetration tester can quickly and easily define a network scan or a custom packet to test for a particular vulnerability over the network.
Network scanning with Python
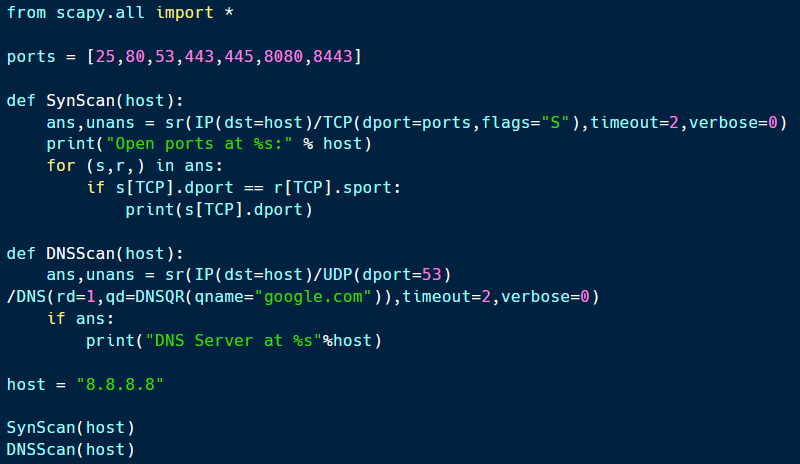
The network scanning demo for the Python for Cybersecurity Learning Path focused on building a custom network scanner using Python and Scapy.
The sample code for this is shown above and available on Github. As shown, this code is designed to perform a SYN scan against a particular IP address and to perform DNS lookups for a domain name.
This combination can identify the IP address of an organization’s servers using DNS and determine if services are listening on certain TCP ports on the target machine. The code can easily be tweaked to implement other scans, such as an XMAS tree or ACK scan.
Introduction to open technical databases
The use of open technical databases is another technique in the MITRE PRE-ATT&CK framework for performing reconnaissance. This technique takes advantage of the fact that there are a number of different publicly accessible sources of information about companies and their IT infrastructure, such as the DNS system.
DNS exploration with Python
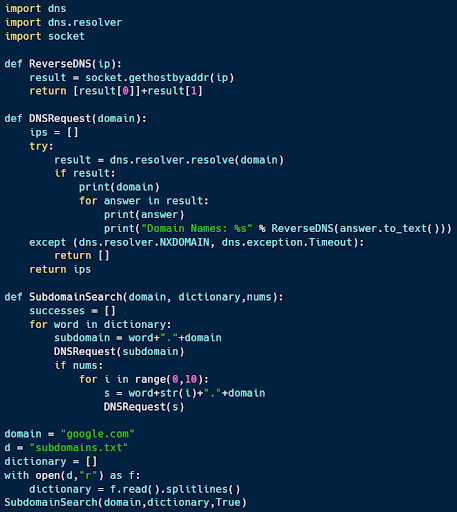
The previous example showed how to use scapy to perform a DNS lookup for a particular domain name. The demo for this section uses DNS infrastructure to explore the registered hostnames within a target environment.
The code sample above (available here) performs forward and reverse DNS lookups to explore a target environment. Using a base domain (Google.com in this case) and a list of common subdomains, the script tests to see if a DNS record exists for each combination.
For each IP address found, the script also performs a reverse DNS lookup, which sees which DNS records are associated with a particular IP address. This makes it possible to identify multiple different roles that a particular machine may be filling (such as a combined email and web server).
Using Python for reconnaissance penetration testing
Reconnaissance is an important part of penetration testing because it gives the tester an understanding of the purpose of different elements of the target environment. Python can be used to automate the reconnaissance process in a variety of ways, including acting as a network scanner and crawling DNS records.
Learn Python for Cybersecurity
Sources:
MITRE ATT&CK, MITRE
Nmap, Nmap
Nessus, Tenable
Python for Cybersecurity, Github