Fitting cyber attacks to jus ad bellum — Target-based approach
I. Essence
The target-based is the second approach that theorists and practitioners use to tuck cyber warfare into the unfitting law framework that jus ad bellum represents, at least concerning the implementation of such non-kinetic means. Deeming the instrument-based approach to be crippled and ineffective as far as unconventional attacks are concerned, the target-based approach views as an armed attack any cyber attack that is directed towards critical infrastructure, especially if it has national importance (DeLuca, 2013).

FREE role-guided training plans
The main purposes of this methodology are to establish when a cyber attack bodes harm to a critical national structure and to trigger the legal mechanisms allowing preemptive strikes and anticipatory self-defense (Hathaway et al., 2012).Usually, the government is most interested in protecting the critical infrastructure of the country.
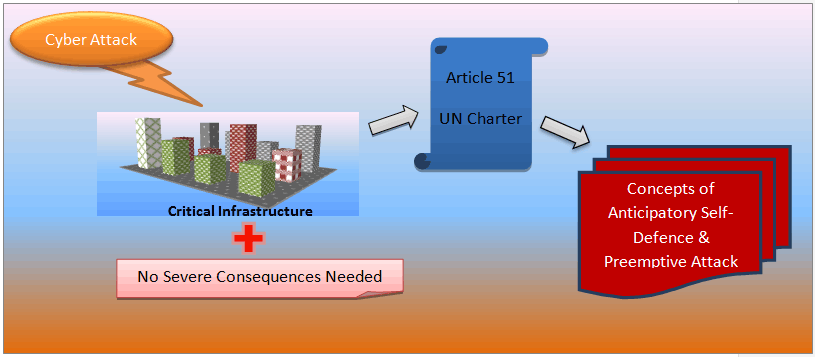
Fig:Target-based Interpretation of a Cyber Attack
Hence, pursuant to this doctrine, cyber attacks are considered a use of force if they penetrate critical national infrastructure, even though not in the presence of resulting casualties or damages (DeLuca, 2013).
In fact, the origin of the target-based approach is due to the many legal experts' opinion that to focus solely on grievous consequences fails to account for contemporary society's dependence on information infrastructures and interconnectedness (Waxman, 2013).
To see the matter from another perspective, a concept that turns attention to the critical infrastructure may serve as a useful transferring tool that will implement in practice the "scale and effects" criterion laid out by ICJ in the Nicaragua case (1985). Therefore, cyber attacks unlikely to produce death/injury or destruction/damage will still amount to an "armed attack" if their purpose is to incapacitate sovereign critical infrastructures (Melzer, 2011). Thereupon, in the absence of distinct negative effects, reference could be made to the phrase "critical infrastructure."
II. What Is Considered a Critical Infrastructure?
The problem of identifying national critical infrastructures is further complicated by the fact that, in most countries, the majority of such infrastructures are owned by the private sector. At the end of the day, the notion of "critical infrastructure" is linked to that of "national security," which is equally difficult to define, both in domestic and international law (Roscini, 2010).
There is no universally acknowledged definition of the term "critical infrastructure" in the international commonwealth; but here are some of the most notorious treatments of various institutions and countries:
- USA Patriot Act
"…systems and assets, whether physical or virtual, so vital to the United States that the incapacity or destruction of such systems and assets would have a debilitating impact on security, national economic services, government, defense industrial base, information and telecommunications, energy, transportation, banking and finance, chemical industry and hazardous materials, and postal and shipping" (USA Patriot Act, 2001, par. 42 U.S.C. §5195c (e)).
- UN General Assembly
"…those used for, inter alia the generation, transmission and disruption of energy, air and maritime transport, banking and financial services, e-commerce, water supply, food distribution and public health—and the critical information infrastructures that increasingly interconnect and affect their operations" (UN General Assembly, 2004, p. 1).
- European Union
"Critical infrastructure include those physical resources, services, and information technology facilities, networks and infrastructure assets which, if disrupted or destroyed, would have a serious impact on the health, safety, security or economic well-being of Citizens or the effective functioning of governments" (European Commission, 2005, par. 3.1).
Given that motley bundle of definitions, it is no wonder that the UN General Assembly recognizes in a direct fashion "that each country will determine its own critical infrastructures (General Assembly, 2004, p. 1).
Jus in bello and Critical Infrastructure
Provision of interest:

One can draw more information on what the term critical national infrastructure consists of from the law of armed conflict or jus in bello. Article 56(1) of AP I grants special protection to vital facilities such as dams, dykes, nuclear power plants, because attacking them may subsequently lead to unleashing dangerous forces that will, in turn, cause serious losses among the civilian population.
By indirection, therefore, this provision defines what type of facilities may be referred to as a critical infrastructure. For the sake of completeness, it must be added that this prohibition is not absolute, meaning that belligerents are allowed to engage if they preclude the possibility of the release of dangerous forces (Kodar, 2012).
Real-life cyber incidents through the magnifier of the target-based mode
The object of this writing could serve as a tool for adjusting the current legal norms to some of the most eminent cyber attacks happened over the last six years:
- The massive DoS attack against Estonia in 2007 is the winner, having the strongest argument to pretend that its critical infrastructure was scrambled, and therefore decisive defense measures would have been justified to a certain extent.
- Considering the damage that Stuxnet worm inflicted on the nuclear facility in Iran, this case can also be seen as an attack against critical infrastructure under the methodology in hand.
- In applying the current approach to the cyber attacks preceding the 2008 conflict in South Ossetia, an analyst must rather pose the question whether government websites qualify as critical national infrastructure (DeLuca, 2013).
Supervisory Control and Data Acquisition (SCADA)
It is a matter of common knowledge that many critical infrastructure installations such as electrical power grids, water treatment facilities, oil and gas pipelines frequently use supervisory control and data acquisition (SCADA) technology. In a few words, SCADA computer systems exercise monitoring and control over a variety of industrial process, for example, the transportation of gas and oil or transmission of electricity). Whereas it is highly recommended that the system be operated in offline mode, the comfort of the remote conduct of abovementioned functions often leads to cases where the IT security is compromised (Kodar, 2012).
Critical National Infrastructure – 'Im Westen nichts Neues' (German)
Today, IT is essential and ubiquitous in virtually every national infrastructure, especially when we are talking about Western societies. Private business firms of every size rely on IT infrastructure to perform dealings and services such as banking transactions, payroll management, research and development, sales and inventory tracking, venture operations, etc. Because the nationwide interweaving demands simplicity in order to function at every level, the architecture in many places demands easy access and use. Yet this openness represents the Achilles' heel of the system (Shackelford, 2009).
With regard to this point, the man in charge of the US military's Cyber Command, Keith Alexander made an official statement: "On a scale of one to 10, with 10 being strongly defended, our critical infrastructure's preparedness to withstand a destructive cyber attack is about three based on my experience" (Reuters, 2013, par. 3).
Recently, private companies participating in one form or another in the infrastructure services have been put on notice to watch out for cyber attacks aiming at sabotage. According to the US government, probing efforts of hackers, presumably from the Middle East, are on the rise. After the alleged onslaught on Saudi Aramco in August 2012, followed by disruption on US banking operations a couple of months later, Iran again is the prime suspect (Adhikari, 2013).
After all that has been said so far, the eloquent statement of readiness to counter-attack anything that moves the wrong way, made by Alexander in a casual reminiscence of the good old cold war deterrence style, adds up somehow:
While we feel confident that most foreign leaders believe that a devastating attack on the critical infrastructure and population of the United States by cyber means would elicit a prompt and proportionate response, it is possible, however, that some regime or cyber actor could misjudge the impact and the certainty of our resolve (Reuters, 2013, par.7).
It makes perfect sense if these vulnerable societies begin to search for some resolution to anchor their hope on. Will the target-based approach perhaps accommodate cyber attacks more easily to the law of resort to war?
III. Act on the Target-Based Approach
Closely linked to the interpretation method that comes under review here is the presumption that the injured or threatened state is authorized to take necessary counter-measures as soon as it is found that its critical infrastructure is attacked at sufficient "scale and effects." With many, inter alia, contentious issues such as the matter of imminence, anticipatory self-defense, and attribution, the things are not really black and white. Let us have a glimpse at several of the moot points that relate to the target-based method.
An active measures policy
The advocates of the approach in question contend that attempts to bring down critical national infrastructures should demand more than just sitting and waiting for the Second Advent to come. Embracing passive measures policy on the one hand means that the one who defend should seek protection through firewalls, antivirus, encryption, and similar measures. An active measures policy, on the other hand, is a totally different thing. First and foremost, they must comply with several of the longstanding limitations the laws and principles governing the use of force:
a) Attribution of the attack
b) Characterization /intent/ of the attack
c) Inviolability of neutral nations
However, in order for such a policy to function, the legal scheme must evolve to permit a nation to defend itself effectively (Jensen, 2003).
Immediate response in self-defense pursuant to Article 51 of the UN Charter
A provision of interest:

In situations of attack against a critical national infrastructure, many scholars advocate an immediate response considering that all attacks reach the armed attack threshold, pointing out that it would be too risky to waste time assessing the magnitude of the attack while a vital critical national infrastructure is at stake.
Moreover, the states that react against these critical national infrastructure attacks would respond in self-defense, pursuant to Article 51 of UN Charter, and hence they would be not held liable for their actions (Sklerov, 2009).
A justificative quote with regard to this logic asserts that "in no way does effects-based analysis require a state to delay its response until it can fully measure a cyber attack against all six of Schmitt's proposed axes. Decision-makers, at times, must make choice with imperfect information"
(Sklerov, 2009, p. 70).
Therefore, by analogy it can be inferred that it will be difficult either way to make the correct choice, so why not attack then?
Open up the doctrine to its full extent—Halfway is no good
Again, the people who support protecting the critical infrastructure at almost any cost from potentially disastrous occurrences such as cyber warfare opine that international law and institutions should provide more options to the states to protect themselves in self-defense without first characterizing and defining the source of the attack. Reasons and recommendations in favor of this policy:
-
A state should be allowed to act in a good-faith response, that is, to act without needing to furnish conclusive evidence of the culprit (Condron, 2007).
- Because the state is at risk, it should have the opportunity to respond in an "immediate, robust, and aggressive" manner (Hoisington, 2009, p. 453).
- International norms should not demand that the state comprehensively abide by the principle of necessity when the state acts in self-defense of a primary state value (Hoisington, 2009).
- Anticipatory self-defense should be permitted in certain cases when a cyber attack endangers a critical national infrastructure (Hoisington, 2009).
- Liability of states should be limited in these cases (Condron, 2007).
-
The international community should promulgate a list of critical national infrastructure that a state may protect with active defense measures; when a cyber attack is directed towards critical national infrastructure included in the list, then the victim state would have a legal right to initiate a good-faith counterattack (Condron, 2007).
Finally, the proponents of consequence-based method arrive at the conclusion that
If the critical infrastructure identified on the list were subjected to a cyber attack, a state could respond in presumptively good-faith self-defense without first attributing or characterizing the attack to the level of specificity required under the traditional formulation. Such an exception would not fundamentally alter the jus ad bellum framework (Hoisington, 2009, p. 453).
IV. Criticism
The main flaw of the target-based approach is that it "tends to be too over-inclusive"
(Hollis, 2007, p. 1042). While the proponents of the theory have a point in arguing that attacks that endanger critical national infrastructure should be regarded with a special attention, there is always a "risk with of unlawfully escalating a situation (Sklerov, 2009, p. 70)."
Although the target-based approach gives the victim state a chance to defend itself better and in a timely fashion, especially against attacks on critical national infrastructure, the expansion of the resort to force may lead to superfluous causation of armed conflicts, both conventional and virtual. Thus, a resort to self-defense would be legally just and permissible with the mere fact of slightest penetration in such essential national system, leading to a potential full-scale conventional armed clash (Hathaway et al., 2012).
Given this point, many scholars argue that, with this approach put into use, peace would be endangered considerably (Hathaway et al., 2012). Then, if we prima vista take all this information into account, we could see that the "sum of all fears" happening is not something difficult to imagine.
Reference List
Adhikari, R. (2013). DHS Raises Alarm Over Cyberattacks on Critical Infrastructure. Retrieved on 02/07/2013 from http://www.technewsworld.com/story/78023.html
Condron, S. (2007). Getting it right: Protecting American critical infrastructure in cyber space. Harvard Law Review, 20, 403-422.
DeLuca, C. D. (2013). The Need for International Laws of War to Include Cyber Attacks Involving State and Non-State Actors. Retrieved on 02/07/2013 from http://digitalcommons.pace.edu/pilronline/34/
European Commission (2005). Communication from the Commission to the Council and the European Parliament—Critical Infrastructure Protection in the fight against terrorism. Retrieved on 02/07/2013 from http://eur-lex.europa.eu/LexUriServ/LexUriServ.do?uri=CELEX:52004DC0702:EN:HTML
International Court of Justice (1985). Military and Paramilitary Activities in and against Nicaragua (Nicaragua v. United States of America). Retrieved from http://www.icj-cij.org/docket/index.php?p1=3&p2=3&k=66&case=70&code=nus&p3=90
ICRC (1977). Protocol Additional to the Geneva Conventions of 12 August 1949, and relating to the Protection of Victims of International Armed Conflicts (Protocol I). Retrieved from http://www.icrc.org/IHL.nsf/FULL/470
Hathaway, O., Crootof, R., Levitz, P., Nix, H., Nowlan, A., Perdue, W., Spiegel, J. (2012).
California Law Review, 100 (4), 817-886.
Hoisington, M. (2007). Cyberwarfare and the Use of Force Giving Rise to the Right of Self-Defense. Boston College International and Comparative Law Review, 32, 439.
Hollis, D. B. (2007). Why states need an international law for information operations. Lewis & Clark Law Review, 11, 1023-1061.
Jensen, E. T. (2003). Unexpected consequences from knock-on effects: A different standard for computer network operations? American University International Law Review, 1145.
Kodar, E. (2010). Applying The Law of Armed Conflict to Cyber Attacks: From The Martens Clause to Additional Protocol I. Retrieved on 02/07/2013 from http://www.ksk.edu.ee/wp-content/uploads/2012/12/KVUOA_Toimetised_15_5_Kodar.pdf
Melzer, N. (2011). Cyberwarfare and International Law. Retrieved on 02/07/2013 from http://www.unidir.org/files/publications/pdfs/cyberwarfare-and-international-law-382.pdf
Reuters, (2013). NSA chief says U.S. infrastructure highly vulnerable to cyber attack. Retrieved on 02/07/2013 from http://news.yahoo.com/nsa-chief-says-u-infrastructure-highly-vulnerable-cyber-181148007.html
Roscini, M. (2010). World Wide Warfare - Jus ad bellum and the Use of Cyber Force, Max Plank Yearbook of United Nations Law, 14, 85-130.
Shackelford, S. J. (2009). From Nuclear War to Net War: Analogizing Cyber Attacks in International Law. Retrieved on 02/07/2013 from http://papers.ssrn.com/sol3/papers.cfm?abstract_id=1396375
Sklerov, M. (2009). Solving the dilemma of state responses to cyberattacks: A justification for the use of active for the use of active defences against states who neglect their duty to prevent. (Master's Thesis, The Judge Advocate General's School, USA)
United Nations (1945). United Nations Charter. Retrieved from http://www.un.org/en/documents/charter/
UN General Assembly (2004). Creation of a global culture of cybersecurity and the protection of critical information infrastructures. Retrieved on 02/07/2013 from http://www.itu.int/ITU-D/cyb/cybersecurity/docs/UN_resolution_58_199.pdf

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!
U.S.A. government (2001). Patriot Act. Retrieved from http://www.fincen.gov/statutes_regs/patriot/index.html