China vs US, cyber superpowers compared
Introduction
In the last months, the press agencies and government official bulletins have reported several news regarding continuous cyber-attacks having Chinese origin, most of them with cyber espionage purpose, but the risk for sabotage operations is concrete and not to underestimate.
The country that suffers the Chinese offensive most of all is the US. The official list of cyber-attacks that hit US is very long and it is considered just the tip of the iceberg, every sector is under pressure, military, technology sector, and also the media.

FREE role-guided training plans
The Chinese attackers operate in a manner very similar, the techniques and the malicious code that has been adopted in different attacks are substantially the same, this observation and the ascertainment that the Chinese Government operates a strict control over the access to the Internet led security experts to think that the events are conducted by state-sponsored hackers.
The government in Beijing is considered one of the most active in the cyberspace. It reserved great attention and huge investments to the subject of information cyber warfare, exactly as the US, it has constituted various cyber units located in the country that monitor the digital worlds and operate in a stealth way to steal intellectual property by foreign states and explore the possibility to attack an adversary from the fifth domain, the cyberspace.
China thanks to the impressive economic growth has bridged the technological gap with the more advanced countries such as the U.S., Israel, and Japan and this was possible due to an intense espionage activity.
On the other end, also US are dedicating great attention to the cyber space, the government is conscious that cyber threats could hit a country and it is accused to have developed the first cyber weapon in the modern warfare. US officials have highlighted with insistence the risks related to a cyber-attack against national critical infrastructures. In this article, I propose some useful information on the cyber organizations of the two countries and regarding their cyber strategies.
The "Cyber China"
Early this year circulated the news that reported an intelligence source inside the PLA, which confirmed the presence of hackers in Chinese army that are trained for cyber operations. The group of elite hackers in the China's People's Liberation Army is known as "cyber blue team" that will be engaged in both defensive and offensive campaigns, their mission is the protection of the country from cyber-attacks.
Despite the fact that US intelligence is aware of the fact that PLA includes skilled cyber units it is the first time that an official source mentioned the presence of hackers. The presence of cyber units in the Chinese army was also confirmed by a Chinese Defense Ministry spokesman, Geng Yansheng, in a briefing in Xinhua as he declared that:
"The team was set up to better safeguard the internet security of the armed forces. Cyber security was an international problem, affecting civil and military areas. China is still "relatively weak" in internet security protection, and vulnerable to cyber-terrorism."
The British intelligence analyst Glenmore Trenear-Harvey added his views on the issue by saying that:
"The intelligence agencies of many countries believe that China has elite hacking team within the army for over 5 years. There can be "literally thousands" of hackers within China had been recruited to form a "botnet army, "attacking from unsuspecting computers. They can then use this capability either to conduct a denial of service, taking down sites, or acting as a Trojan horse to get within computers and steal information."
"As an offensive tool that is very much something the People's Liberation Army would do,"
"This is not just conventional military powers. Put bluntly, everyone's at it. It is a game anyone can play. For example Japan has a formidable capacity and we have no idea what it is doing with it – and Singapore, Switzerland, Israel,"
"But do remember that we – the US and UK – are doing this in reverse and we are very successful. It's an incredibly potent weapon which will certainly be utilized."
The Chinese authorities before others have understood the importance of a strategic hegemony in cyber space despite their cyber-capabilities were initially limited. The government has promoted various initiatives to improve both offensive and defensive capabilities, it constituted dedicated military organization that had as first missions intelligence operations of foreign state's cyber capabilities and intellectual property.
After many years of intense cyber activities the country today can boast a high potential for cyber offensive but according many security experts its defensive systems are still not really advanced.
China began to implement an Information Warfare strategy in 1995 conducting a huge quantity of exercises in which malicious code have been used to exploit vulnerabilities in military and private communications with the intent to cause their interruption or to gain their control. In 2000, Chinese Government established a strategic Information Warfare unit, Net Force, which is responsible for "wage combat through computer networks to manipulate enemy information systems spanning spare parts deliveries to fire control and guidance systems." But when we discuss about China and cyber space the principal units are known as PLA GSD Third Department and Fourth Departments, they are considered in fact the two largest players in China's burgeoning cyber-infrastructure.
In November 2011, Desmond Ball, a professor in the Strategic and Defense Studies Centre at Australia's National University argues that the Chinese offensive capabilities today are pretty limited and he has also declared that the internal security has a bunch of vulnerabilities.
Ball says that China's cyber-warfare capabilities are "fairly rudimentary," he sustained that Chinese cyber units don't represent a serious menace due leak of sophistication of the attacks. The malware detected since 2011 revealed a low complexity and in many cases where intercepted before to cause damage. The professor sustained that the capabilities of Chinese cyber units cannot be sufficient to penetrate foreign networks. I mentioned these affirmations because it is representative of the perception of Chinese cyber menace just a couple of years ago, the recent events demonstrated that also in that period were ongoing cyber espionage operations based on complex malicious code that operated undetected for various years compromising computers and also entire networks also of government offices.
The suspect that behind the recent attacks there are state-sponsored hackers would be confirmed by a similar different digital fingerprint in the incursions, easily recognizable by analyzing the command and control servers and dissecting the malicious code used.
US analysts are convinced that the responsibility of the attacks is of the Chinese Government, in various occasions they have tracked a meaningful number of intrusions originated from networks attributable to Beijing cyber structures. Chinese authorities coordinate a persistence offensive spreading malware mainly oriented to intelligence operations, many cyber espionage campaigns have been conducted against numerous countries, including the United States, UK, Australia, New Zealand, Canada, Germany, France, the Netherlands, Portugal, Japan, South Korea, Taiwan, India, Pakistan, Iran, Thailand, the Philippines and Indonesia.
The Office of the National Counterintelligence Executive has issued various reports that mentioned the prevalent usage of cyber operations to attempting to gain business and industrial secrets from companies.
PLA GSD Third and Fourth Departments
The Chinese GSD Third Department is responsible for monitoring foreign communications, and conducting cyber-surveillance on priority targets around the world. The same department also assures the security of communications networks and PLA computer.
Specialized linguists in sectors such as banking and financial transactions, military activities, energy, and diplomatic exchanges are involved in operation of SIGnals INTelligence (SIGINT) and they could count on the sophisticated wiretapping system that include automatic voice recognition technology and software engine for mining large quantity of data real time. China maintains the most extensive SIGINT network of all the countries in the Asia-Pacific region.
It's important to note that the communications stations established by the Third Department of the PLA General Staff Headquarters are not under the control of the provincial military district and the major military region of where they are based.
One of the principal task of the unit is the control of information through monitoring of communications, email accounts, websites, and internal networks.
Functional Third Department bureaus may operate and process communications intercept systems (e.g. Intercept and recording of VHF and UHF communications, including cellular phone and microwave networks within line of sight of collection sites). A special sub-division is responsible for intercept of foreign satellite communications not only related to communications from sites around the country, the 12th Bureau may be also capable of intercepting communications around the world from Chinese space-based systems. US counter intelligence units sustain also that PLA is already operating electronic reconnaissance campaigns.
According intelligence analysis the PLA has a dedicated Bureau to foreign countries; Third Department Second Bureau in Shanghai conducts operations mainly focused on the United States meanwhile the Third Department Fourth Bureau is focused on Japan and Korea.
One of its bureaus is responsible for encryption of communications securing of internal Third Department networks maintaining the alignment of data acquired by various offices spread within the country.
Within the same tasks assigned to the Department is the vulnerability assessment of internal networks and communication systems, the intent is to prevent that foreign governments could intercept sensitive communications or violate protected lines.
The Fourth Department (ECM and Radar) under the control of PLA has primary responsibility for the electronic intelligence (ELINT) portfolio within the PLA's SIGINT apparatus. It coordinates electronic countermeasures, requiring them to collect and maintain databases on electronic signals, to fulfill the task is could count on at least 25 ELINT receivers.
The Unit 61398
The PLA Unit 61398 (also known as "Advanced Persistent Threat 1" ("APT1") and "Byzantine Candor"), is a sort of legend in the hacking world, it is the Military Unit Cover Designator (MUCD) of a PLA responsible for majority of persistent cyber espionage campaigns against foreign governments and it has been alleged to be the primary source of Chinese cyber-attacks. Various investigations conducted by private entities and intelligence agencies locate the headquarters of the group in a 12-story building off Datong Road in a public, mixed-use area of Pudong in Shanghai, sources of intelligence speculated that the unit is composed by a thousand of skilled hackers.
A recent report issued by Mandiant intelligence agency stated that PLA Unit 61398 operates under the control of PLS 2nd Bureau of Third Department cited in the above session. According the report the unit was responsible of a huge number of attacks and cyber espionage operation against enterprises and governments all over the world since at least 2006.
Intelligence agencies suspect that group has stolen trade secrets and many other confidential information from foreign corporations and organizations such as Lockheed Martin and Telvent, and many other companies in the defense, energy, manufacturing, engineering, electronics and financial.
Many security experts, including researchers at Dell SecureWorks linked the group to an historical espionage campaign known as Operation Shady RAT. It was a large scale operation uncovered in 2011 in which more than 70 organizations we targeted over a period of five years, the list of victims includes US government agencies, the United Nations and organizations located in various countries such as Canada, South Korea and Taiwan.
The Mandiant Report
In January it was spread the news regarding a sophisticated cyber espionage campaign against principal media agencies in US, included NYT and Washington Post, the hackers have tried to compromise the email account of journalists to steal sensitive information. The attackers have tried to infiltrate the network of the journal using 45 instances of targeted malware, as revealed by forensic analysis conducted by the Mandiant security firm.
Mandiant researchers observed that the hackers began work, for the most part, at 8 a.m. Beijing time operating for a standard work day, but the group of hackers has also stopped the attacks for a couple of weeks periodically.
A few weeks after The Mandiant® Intelligence Center™ released a shocking report that revealed an enterprise-scale computer espionage campaign dubbed APT1.
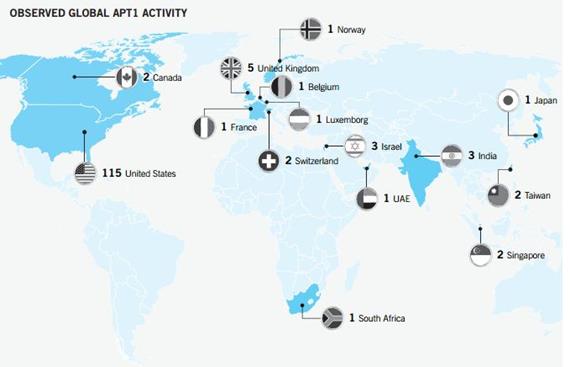
Figure 1 - APT1 cyber-espionage campaign (Mandiant Report)
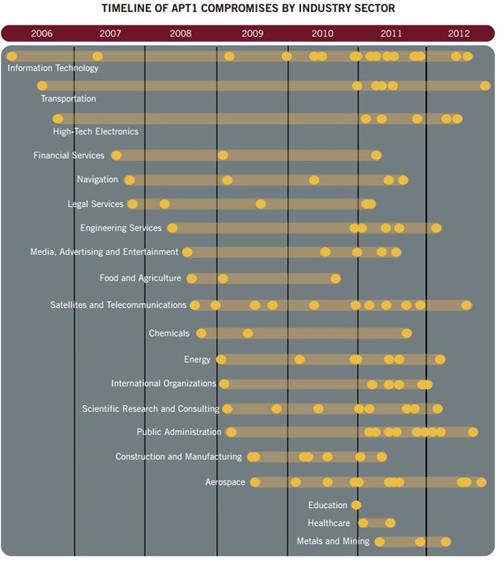
Security experts linked the cyber espionage operation APT1 to China's 2nd Bureau of the People's Liberation Army (PLA) General Staff Department's (GSD) 3rd Department (Military Cover Designator 61398). The concerning new is that the campaign has been started in 2006 targeting numerous victims, around 141, across multiple industries.
Figure 2 - Timeline APT1 campaign by industry sector - Mandiant
The report provided various interesting information on the PLA's cyber unit known as "Unit 61398, experts believe it engages in harmful "Computer Network Operations."
- Unit 61398 is partially situated on Datong Road (大同路) in Gaoqiaozhen (高桥镇), which is located in the Pudong New Area (浦东新区) of Shanghai (上海). The central building in this compound is a 130,663 square foot facility that is 12 stories high and was built in early 2007.
- The experts estimate that Unit 61398 is staffed by hundreds, and perhaps thousands of people based on the size of Unit 61398's physical infrastructure.
- China Telecom provided special fiber optic communications infrastructure for the unit in the name of national defense.
- Unit 61398 requires its personnel to be trained in computer security and computer network operations and requires its personnel to be proficient in the English language.
- Mandiant has traced APT1's activity to four large networks in Shanghai, two of which serve the Pudong New Area where Unit 61398 is based.
The Mandiant has also identified more than 3,000 indicators to improve defenses against APT1 operations and is releasing a specific document that will address them including APT1 indicators such as domain names, IP addresses, and MD5 hashes of malware.
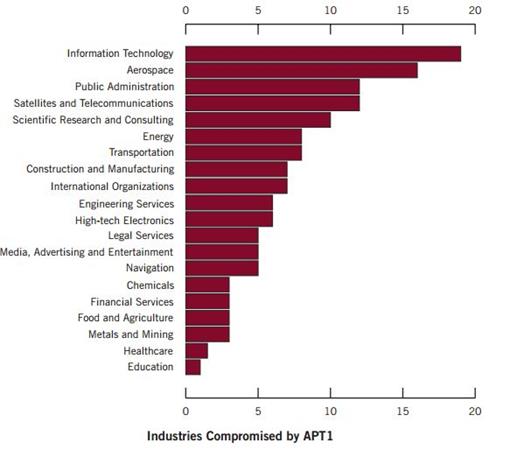
APt1 has systematically stolen hundreds of terabytes of data from victim organizations and has demonstrated the capability and intent to steal from dozens of organizations simultaneously.
Figure 3 - Industries hit by APT1 campaign - Mandiant
APT1 is a persistent collector, once APT1 has established access, they periodically access to victim's network stealing sensitive information and intellectual property for a long time, typically maintaining access to victim networks for an average of 356 days. The longest time period APT1 maintained access to a victim's network was 1,764 days, or four years and ten months.
US cyber units
The first Air Force Cyber Command was created in a provisional status in November 2006, on 23 June 2009, the Secretary of Defense directed the Commander of U.S. Strategic Command (USSTRATCOM) to establish USCYBERCOM that reached full operational capability on 31 October 2010 when the command assumed responsibility for several existing organizations.
The United States Cyber Command (USCYBERCOM) is an armed force subordinate to United States Strategic Command (USSTRATCOM) that is one of nine Unified Combatant Commands of the US Department of Defense.
Among the responsibilities of USSTRATCOM, there are informational operations such as information warfare intelligence, surveillance, and reconnaissance (C4ISR where C4I stands for command, control, communications, computers, and (military) intelligence).
"The United States Cyber Command (USCYBERCOM) plans, coordinates, integrates, synchronizes, and conducts activities to: direct the operations and defense of specified Department of Defense information networks and; prepare to, and when directed, conduct full-spectrum military cyberspace operations in order to enable actions in all domains, ensure US /Allied freedom of action in cyberspace, and deny the same to our adversaries."
The command is located in Fort Meade, and today directed by General Keith B. Alexander, the command performs a critical task to centralize and synchronize the numerous resources and activities within the US Army.
U.S. Cyber Command is composed of several operative commands and units from military services, following a graphic representation of its structure.
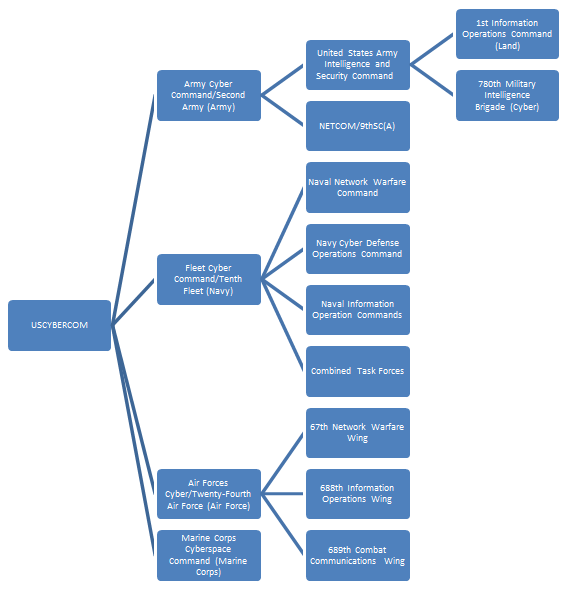
Figure 4 - USCYBERCOM structure
To design the organization of US Cyber Commands is not so hard respect the analysis of secret Chinese cyber units, but the reader should consider that these organizations are very dynamic to respond to the different emerging needs. The cyber threats are constantly changing and the response of cyber structures within the Army of any country must be adaptive.
One of the most complex issue to approach when the cyber structure is analyzed it the military's right to respond to cyber-attacks and the rules of engagement in case of conflict, GEN Alexander expressed his position in response to incidents such as a 2008 operation to take down a government run extremist honeypot in Saudi Arabia:
"The U.S. must fire back against cyber-attacks swiftly and strongly and should act to counter or disable a threat even when the identity of the attacker is unknown" "Elite U.S. military computer specialists, over the objections of the CIA, mounted a cyber-attack that dismantled the online forum". "The new U.S. Cyber Command needs to strike a balance between protecting military assets and personal privacy".
"This command is not about an effort to militarize cyber space," he said. "Rather, it's about safeguarding our military assets." With last sentence, the official focused the mission of the command on building capacity and capability to secure the networks and educating the public on the command's intent.

Figure 5 - USCYBERCOM logo
"We have, within Cyber Command, a full spectrum of capabilities, but the thrust of the strategy is defensive." "The strategy rests on five pillars, he said: treat cyber as a domain; employ more active defenses; support the Department of Homeland Security in protecting critical infrastructure networks; practice collective defense with allies and international partners; and reduce the advantages attackers have on the Internet." declared the Deputy Defense Secretary William Lynn during a conference in July 2011.
Budget for cyber operations
US is considered one of the most advanced government in cyber information warfare, and the investment in the constitution of new cyber units demonstrate the great attention of American authorities in the matter.
For first time the Pentagon has detailed $30 million in spending on Air Force cyber-attack operations and new Army funding, public disclosure of the budget for cyber campaigns, in particular the Defense Department, desires to provide to national taxpayer's evidence of effort spent in what is being considered a critical component of the modern military.
The Pentagon revealed the intent to constitute and fund new staff dedicated to offensive cyber-operations for the exploitation of opponent networks and infrastructures.
The document titled "Fiscal Year (FY) 2014 Budget Estimates – OPERATION AND MAINTENANCE, AIR FORCE" details how US intends to invest for The Air Force in fiscal 2014, it will reserve $19.7 million on "offensive cyber operations," the expense will support operative cyber operations, personnel training and research and development activities. In cyber warfare scenario a crucial role is played by cyber tools used to exploit opponent's structures, for this reason US estimate needing $9.8 million for development of new cyber tools to use in cyber operations.
The Pentagon proposed also the hiring of new personnel, 65 units, to dedicate to the cyber missions, the mission assigned to Cyber Command is critical because it is responsible to deflect incoming assaults from cyber space against critical infrastructures of the country.
Of course, part of the funds will be dedicated to Defense Cyber Operations to protect data and infrastructures of the country from cyber-attacks, sabotage, and cyber-espionage.
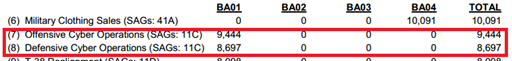
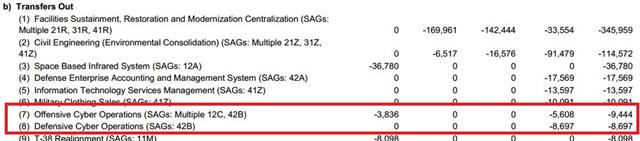
Following an extract from the "Summary of funding Increases and Decreases" related to the "cyber commitment":
Transfers In
Transfers Out
Nextgov portal reported the US government chose to divulge this information "because cyber offense will be a standard line item from now on and the public needs to understand what it is paying for."
To those taxpayers that as justification for the investments in cyberspace while defense budget is under cutting Air Force spokesman Maj. Eric Badger replied:
"We are committed to maintaining the right balance of integrated cyber capabilities and forces that are organized, equipped, and trained to successfully conduct operations in cyberspace. We're equally as committed to doing so in a way that's respectful of the taxpayers' dollar,"
"We know the Air Force's capabilities in cyber are going to continue to be touchstones for the whole joint team, the whole of government and for the private sector," the official added.
According Nextgov further $4.9 million will be dedicated to the development of "computer network exploitation" and "computer network attack" capabilities.
US and China, mutual accusations
Recently an alarming news has been reported by the US Government; the designs for many of the nation's most sensitive advanced weapons systems have been compromised by Chinese hackers, according to a report prepared for the Pentagon and to official sources from government and the defense industry.
Among more than two dozen major weapons systems whose designs were breached, there were critical programs to U.S. Missile defenses and combat aircraft and ships, according to a previously undisclosed section of a confidential report prepared by the Defense Science Board for Pentagon leaders. Intelligence Experts warn that the continuous intrusions gave China the access to advanced technology allowing the country to accelerate its technological growth.
The Defense Science Board, a senior advisory group composed of government and civilian experts did not accuse the Chinese of stealing the designs but senior military and industry officials that investigated on the data breaches are convinced that the majority of the attacks were part of "ordinary" Chinese cyber espionage campaigns against defense contractors and government agencies of foreign governments.
US government and intelligence agencies have tracked back numerous attacks from Chinese IPs, of course this is not considerable a proof of Chinese state-sponsored attacks, conducted with intent to acquire intellectual property for technological modernization of the country.
The significance and extent of the targets help explain why the Obama administration has escalated its warnings to the Chinese government to stop what Washington sees as rampant cyber theft. In March, the advisory panel warned with the public version of its report that the Pentagon is unprepared to counter a full-scale cyber-conflict.
China, which is pursuing a long-term, comprehensive strategy to modernize its military, is dedicating a great attention to cyber-espionage activities, for the first time, the Pentagon specifically addressed Chinese state sponsored hackers behind intrusions into government networks.
But US isn't the unique government to blame Chinese authorities to support cyber espionage campaigns against foreign government, China and US continue to exchange accusations about the continuing incursions into the respective national networks.
Cyber experts estimate that about 90% of all cyber-attacks against US networks are originated from China. The Pentagon's annual report to Congress recently released is the first government document that explicitly accuses People's Liberation Army (PLA) for organizing a campaign of attacks to gain a strategic technological advantage over the United States.
Figure 6 - Pentagon's annual report to Congress
"In 2012, numerous computer systems around the world, including those owned by the U.S. Government, continued to be targeted for intrusions, some of which appear to be attributable directly to the Chinese government and military,"
The US Government accused China's military of sustaining a campaign of cyber-attacks against American government computer systems and defense contractors to qualify "military capabilities that could be exploited during a crisis." The Chinese Government rejects every accusation and blames US for attacks against national infrastructures and networks defining US the "real hacking empire."
The Government of Washington raises many doubts on the capabilities of Chinese industry to sustain a so rapid technological evolution of the country, providing as an example the development of a new generation of stealth aircraft that could be resultant of intense activity of espionage over the years that hit US Governments, defense companies and various subcontractors.
The People's Liberation Army Daily defined the document a "gross interference in China's internal affairs"; it accuses US Government of fomenting the discussion to create a climate of tension that would benefit the usual group of companies operating in the US military sector and close to the central government.
[US is] "trumpeting China's military threat to promote its domestic interests groups and arms dealers," the newspaper said, adding that it expects "U.S. arms manufacturers are gearing up to start counting their money."
The two governments are focusing the confrontation in cyberspace, both states understood the potential of the cyber tools for espionage and sabotage, and both governments continue to provide direct support and investment to support research on new technologies to compromise adversary's networks.
The Chinese Government has expressed in the past great concerns on the attacks that are targeting its network and that result originated from West. Xinhua agency revealed that China's Internet security watchdog detected from September 2012 to February 2013 various attacks against national cyber assets, 85 government websites and high-profile private companies suffered serious offensive.
Chinese authorities are concerned on the huge quantity of attacks originated from West, 46% of the offensives were traced back to the United States based, also in this case it is impossible to establish a precise responsibility of Washington.
Surprising the number of overseas Internet Protocol (IP) addresses originating the attacks, CNCERT (National Computer Network Emergency Response Technical Team Coordination Center) identified in 2012 73,000 different addresses involved in hijacking nearly 14.2 million mainframes in China via Trojan or Botnet.
The majority of malware-based attacks have originated in the US; the attackers gathered unauthorized access to 16,388 web pages in China, the percentage of government websites is 11% in 2012, up 6.1 percent respect previous year.
The People's Daily has weighed the allegations against the US proposing a declaration of the spokesman of the Chinese Communist Party;
"As we all know, the United States is the real 'hacking empire' and has an extensive espionage network," in recent years, the United States has continued to strengthen its network tools for political subversion against other countries."
"Cyber weapons are more frightening than nuclear weapons," the People's Daily said. "To establish military hegemony on the Internet by repeatedly smearing other countries is a dangerous and wrong path to take and will ultimately end up in shooting themselves in the foot."
Conclusions
No doubts that in the short term the mutual attacks will continue despite the effort spent by each government to improve the security of cyberspace and prevent intrusion within its network. New and future conflicts will involve new actors in the geopolitical scenarios such as independent hackers, state sponsored hackers, cyber criminals and cyber terrorists that could influence the delicate balance between the two giants. The battlefield is deeply changed, the conflicts are primary conduced in virtual and immaterial global network in which concept of time is changed because the offence is instantaneous and unpredictable. Conflicts have an asymmetric nature and the element of surprise is crucial causing the need to totally review of the concept of deterrence.
The concept of cyber threat evolves day by day and every Government need a proper cyber strategy to mitigate it and of course must guarantee the needed effort in term of resource and investment.
To defuse the tensions generated the US and China have agreed to hold regular talks on how to set approach cyber security and commercial espionage issues. These meetings will not resolve anyway the situation but is an essential step to regulate a dangerous situation.
US Officials involved in the negotiations declare
"We need to get some norms and rules."
"It is a serious issue that cannot simply be swatted away with talking points," "Our concerns are not limited to that, but that's what needs urgent attention,"
The talks over network intrusions is part of the Strategic and Economic Dialogue between the two countries that will arrange an annual meeting of Chinese and American officials and will establish working groups operative on the topic that will compete in a continuous manner.
References
http://www.defense.gov/pubs/2013_china_report_final.pdf
http://www.saffm.hq.af.mil/shared/media/document/AFD-130403-076.pdf
http://www.amazon.com/21st-Century-Chinese-Cyberwarfare-Governance/dp/1849283346
http://news.clearancejobs.com/2013/05/06/cybersecurity-round-up-u-s-confronts-top-cyber-adversaries/
http://project2049.net/documents/pla_third_department_sigint_cyber_stokes_lin_hsiao.pdf
http://hackread.com/china-admits-cyber-warfare-unit-in-peoples-liberation-army/

FREE role-guided training plans