Windows registry analysis with RegRipper – A ‘hands-on’ case study
Every analysis begins with specific goals in mind. As a forensics investigator, you are expected to know the type and importance of information you are looking for while investigating a computer crime. Computer forensics investigations involving a Windows box rely heavily on meticulous inspection of the keys, subkeys and relevant values that exist within the Windows registry. You are expected to know what you are looking for in the registry, where it is located and how it will help your investigation. 'RegRipper' is an easy-to-use tool that makes the process of extracting information from the registry easier by providing pre-written Perl 'plugins' (details in the previous paper). In this paper, we experiment further with the Windows registry (Windows XP and Windows 7) using more RegRipper plugins and take a quick look at RegRipper's graphical interface.
Role: Computer Forensics Investigator
Purpose: Locate inculpatory or exculpatory evidence in the disk so that it may be presented in the court of law.
Assumptions: It is assumed that you have read the previous paper on 'Windows Registry Forensics using RegRipper' and have access to the Windows XP and/or Windows 7 registry hive files.
Evidence Disk: You can grab the EnCase image of the Greg Schardt hacking case here: part1 and part2.
Tools used: You can download RegRipper for Linux here, and RegRipper for Windows here.
Tasks performed: During the course of this investigation, you will be required to perform the following tasks:
- Determining whether auditing is enabled
- Examining Windows Shellbags
- Determining the information stored in banners
- Extracting information from the SAM hive using 'samparse'
- Examining the Browser Helper Objects
- Determining if the 'NukeOnDelete' value is set
- Determining the presence of Trojans such as clampi, brisv, etc
- Determining the common dialogues available
- Determining the remote systems that the suspect connected to
- Determining the default browser in use
- Determining the Google Toolbar search history
- Determining the 'TypedPaths'
- Determining the wireless access points information
- Determining WinZip information
- Registry analysis using RegRipper's graphical interface
Some facts that you should know:
- As a forensics investigator, you will not be interacting with the Windows registry using the standard 'regedit' (Registry Editor) that ships with Windows. You will mostly be working over dormant registry hives that are nothing more than 'files' resident in the evidence disk drive.
- Information relevant to specific users of the system is located in the 'NTUSER.DAT' file.
- The hives files (SAM, security, software and system) can mostly be located in the 'Windows/System32/config/' folder.
- Some of these hives are 'volatile' and the contents are lost as soon as power is interrupted. These include: HKEY_CURRENT_USER, HKEY_LOCAL_MACHINEHARDWARE, etc.
- Registry contains multifarious keys and subkeys. Each of these keys contains: Values, Data Type and Data.
Windows Registry Analysis
We begin with analyzing the Windows XP registry first and then move on to experiment with Windows 7 registry.
Determining whether auditing is enabled
As forensics investigators, we are interested to know if security audits are enabled on the suspect's system. We will obtain this information using the 'auditpol' (Audit Policy) plugin in RegRipper:
perl rip.pl -r /mnt/forensics/WINDOWS/system32/config/SECURITY -p auditpol
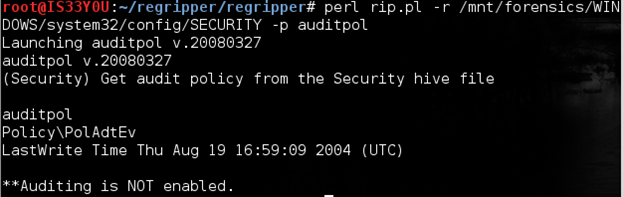
Figure 1
Notice that auditing is disabled on the suspect's computer [Figure 1].
Examining windows shellbags
Recall that in Windows XP there is a setting under 'Folder Options' that allows the system to 'Remember each folder's view settings'. This particular setting is stored in the registry at the following paths:
- HKCUSoftwareMicrosoftWindowsShellBags
- HKCUSoftwareMicrosoftWindowsShellBagMRU
- HKCUSoftwareMicrosoftWindowsShellNoRoamBags
- HKCUSoftwareMicrosoftWindowsShellNoRoamBagMRU
The information revealed by this key is of interest to us since Shellbags store information about the folders (such as size, icon, position, etc) even after the folder has been removed. This means that we are able to gather information about mounted volumes, files that have been deleted, user modifications, etc. It can also reveal information about the use of Windows Explorer to access remote shares and removable storage devices. The 'bagtest' plugin in RegRipper is used to test these bagMRU keys in the registry:
perl rip.pl -r /mnt/forensics/Documents and Settings/Mr. Evil/NTUSER.DAT -p bagtest
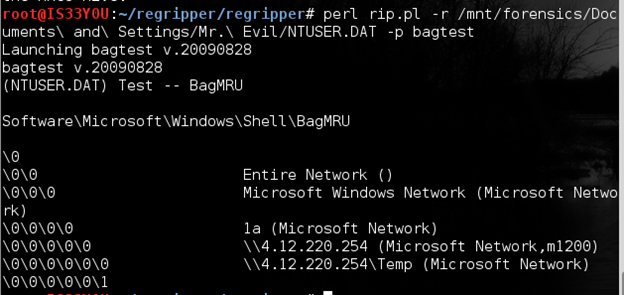
Figure 2
Determining the information stored in banners
A banner is a message that is displayed to the user before he/she logs on to the system. These are used by organizations to give legal notice to the users regarding the ethical use of its systems. This information is stored in the following registry key:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionWinLogon
We use the 'banner' plugin in RegRipper to obtain the banner information:
perl rip.pl -r /mnt/forensics/WINDOWS/system32/config/software -p banner
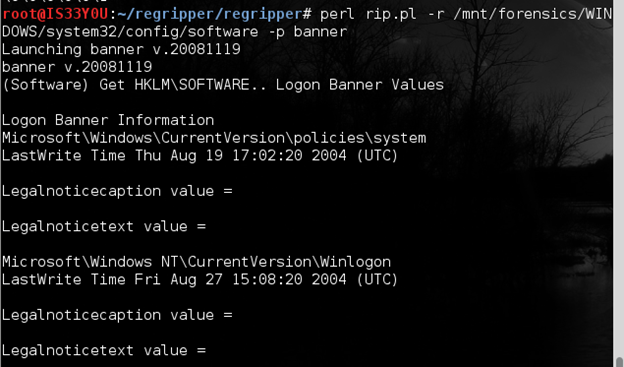
Figure 3
Notice that in this particular case, the suspect's system does not contain any banners [Figure 3].
Extracting information from the SAM hive using 'samparse'
The 'samparse' plugin in RegRipper is used to extract both 'user' and 'group' information from the 'SAM' hive file.
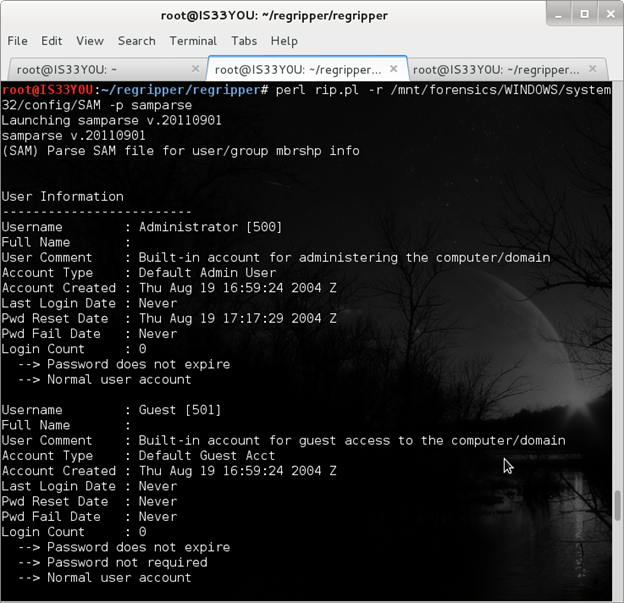
Figure 4
Note: Here RID is the specific Windows user's 'relative identifier'. The Administrator account has an RID value of 500 and the Guest account has an RID value of 501 [Figure 4].
Notice that the Login Count for both the Administrator and the Guest account is '0' which indicates these accounts are not in use on this system [Figure 4].
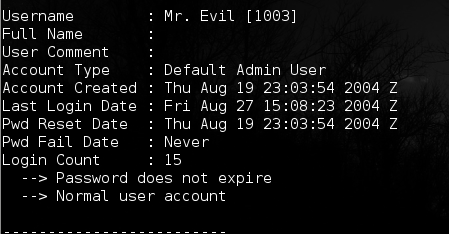
Figure 5
Notice that 'Mr. Evil' is the account that is in use on this system (Login Count = '15'). Also notice the last login date and the account creation date. The RID for this user is '1003' [Figure 5].
Examining the browser helper objects
Browser Helper Objects (BHOs) are DLL files that Internet Explorer can use to provide additional functionality to the user. BHOs can help in customizing the browser (much like the add-ons on Firefox). These BHOs are only loaded when IE is launched. These BHOs may also be targeted by Malware to interfere with the user's online activities. We use the 'bho' plugin in RegRipper to inspect these:
perl rip.pl -r /mnt/forensics/WINDOWS/system32/config/software -p bho
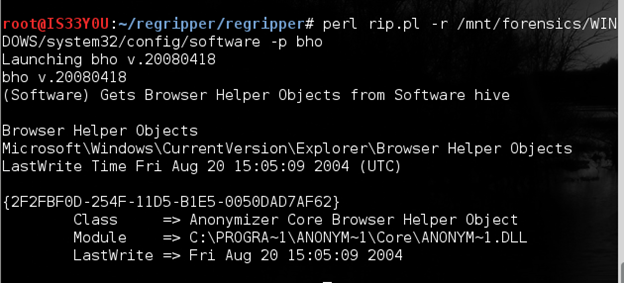
Figure 6
Determining if the 'NukeOnDelete' value is set
'NukeOnDelete' allows one to disable the 'Recycle Bin' function. This means that when a file or folder is selected and the 'delete' key is pressed, the file or folder will be permanently deleted (instead of going to the Recycle Bin). A Windows user can set this feature by going to "Recycle Bin Properties" and then checking "Do not move files to the Recycle Bin. Remove files immediately when deleted". 'NukeOnDelete' can found at the following registry location:
MicrosoftWindowsCurrentVersionExplorerBitBucket
We check to see if the 'NukeOnDelete' bit is set using the 'bitbucket' plugin in RegRipper:
perl rip.pl -r /mnt/forensics/WINDOWS/system32/config/software -p bitbucket
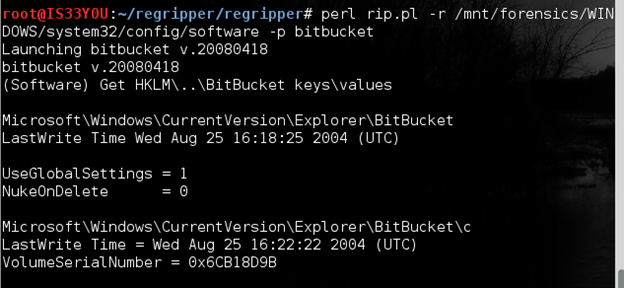
Figure 7
Notice that in this case the NukeOnDelete bit is not set [Figure 7].
Determining the presence of Trojans such as clampi, brisv, etc
Specific plugins in RegRipper allow the investigator to look for the presence of certain viruses or Trojans in the system. These malware are known to modify certain keys in the Windows registry and these plugins check for such modifications to confirm the existence of the malware. In this example, we check for the presence of the 'Ilomo/Clampi' Trojan that is known to create 'Microsoft9593275321' key in the Software hive [1]. We use the 'clampi' plugin in RegRipper for this purpose:
perl rip.pl -r /mnt/forensics/Documents and Settings/Mr. Evil/NTUSER.DAT -p clampi
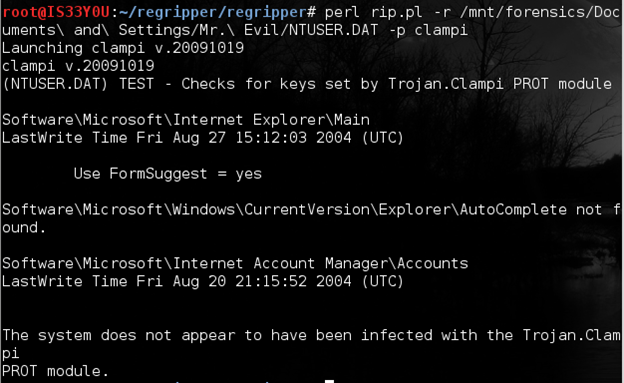
Figure 8
Notice that this system is not found to be infected by the 'Ilomo/Clampi' Trojan [Figure 8].
Determining the common dialogues available
The common dialogues available on a Windows box are reflected by the 'ComDlg32' key in the registry. The 'OpenSaveMRU' can be found under the 'ComDlg32' key. This 'OpenSaveMRU' is used for tracking the files that are accessed via the 'Open and Save As' common dialogue [1]. In simple words, when the user opens an application (such a 'MS Word') on the Windows box, he/she clicks on 'File' menu item which presents the drop down option of 'Open and Save As'. So this key and its relevant subkeys can be used to track past files that were opened or saved by the suspect.
We use the 'comdlg' plugin in RegRipper to obtain this information:
perl rip.pl -r /mnt/forensics/Documents and Settings/Mr. Evil/NTUSER.DAT -p comdlg32
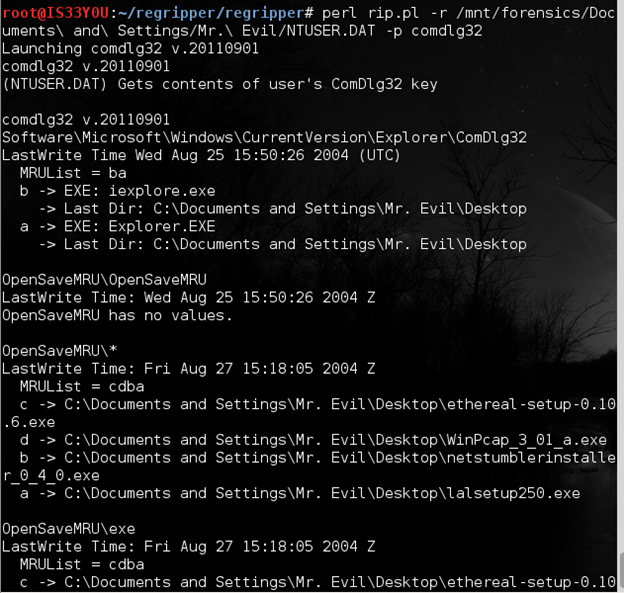
Figure 9
Notice that the suspect has been saving set ups of some 'hacking' related tools (Ethereal, WinPcap, Net Stumbler, Look@LAN Network Monitor, etc) [Figure 9].
Determining the remote systems that the suspect connected to
Windows maintains information about the systems that a specific user of this box connected to or whether it belonged to a particular Local Area Network. This information is stored in the 'Computer Descriptions' key in the registry. This key is found at the following location in the registry:
HKCUSoftwareMicrosoftWindowsCurrentVersionExplorerComputerDescriptions
We use the 'compdesc' plugin in RegRipper to pull this information from the registry:
perl rip.pl -r /mnt/forensics/Documents and Settings/Mr. Evil/NTUSER.DAT -p compdesc
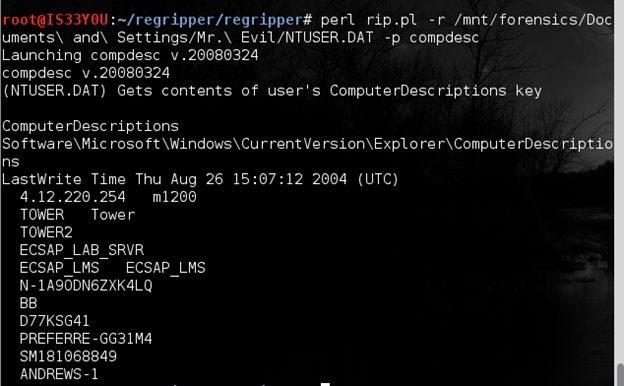
Figure 10
Notice the systems that the suspect connected to. These can be added to the scope of the investigation if needed [Figure 10].
Determining the default browser in use
The 'defbrowser' plugin in RegRipper is capable of extracting information about the default browser that is in use on this system:
perl rip.pl -r /mnt/forensics/WINDOWS/system32/config/software -p defbrowser
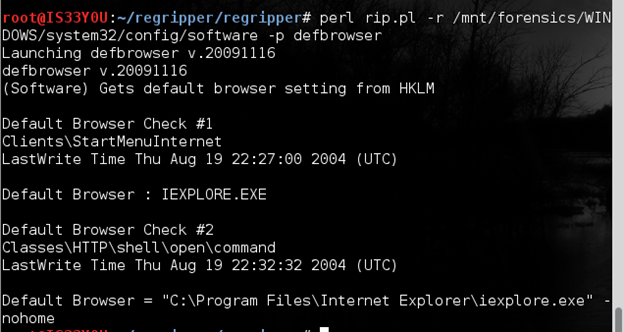
Figure 11
Notice that the suspect was using 'Internet Explorer' as the default browser on this box [Figure 11].
Determining the Google Toolbar search history
To gather information about web searching habits of the suspect, we leverage the Google Toolbar in the browser (if available) which is capable of storing the user's search history. We use the 'gthist' plugin in RegRipper for this purpose:
perl rip.pl -r /mnt/forensics/Documents and Settings/Mr. Evil/NTUSER.DAT -p gthist
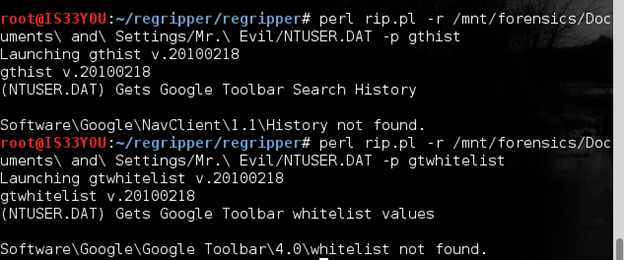
Figure 12
Notice that we could not obtain 'Google Toolbar Search History' or the 'Google Toolbar whitelist values'. This may indicate that Google Toolbar is not installed on this box [Figure 12].
RegRipper Analysis for a Windows 7 box
Until now, we have been extracting information from the registry of a Windows XP box according to our case (see case details here). Now we extract information from a Windows 7 registry. There are slight differences in the structure of the registry in the various versions of Windows. This fact affects the successful execution of a plugin.
The following examples are meant to exhibit that registry analysis using RegRipper on a Windows 7 box is not different from that on a Windows XP. This is because the RegRipper plugins offer us certain abstraction when it automatically locates information in the Windows registry. However, a plugin (Perl script) in RegRipper that is written for a Windows XP box may or may not work correctly on a Windows 7 box. It depends on 'where' exactly in the registry this plugin is pulling the information from, and whether this location of the key is common between the hives of a Windows XP and Windows 7 (or Windows Vista or Windows 8) box.
Determining the 'TypedPaths'
The TypedPaths key is in the user's 'NTUSER.DAT' hive file. It stores information about the folder paths that this user typed in the Windows Explorer Address Bar in the system. We obtain information from this key using the 'typedpaths' plugin as follows:
perl rip.pl -r /media/5CBC1A50BC1A24D4/Users/intellikid/NTUSER.DAT -p typedpaths
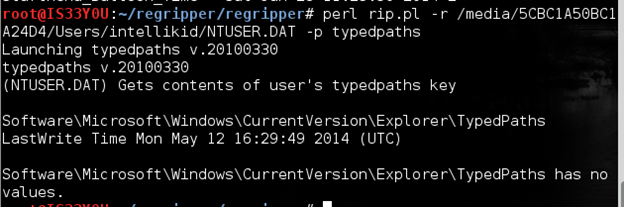
Figure 13
Determining the wireless access points information
To determine which wireless access points the suspect has connected to, we use the RegRipper plugin 'vista_wireless' as follows:
perl rip.pl -r /media/5CBC1A50BC1A24D4/Windows/System32/config/SOFTWARE -p vista_wireless
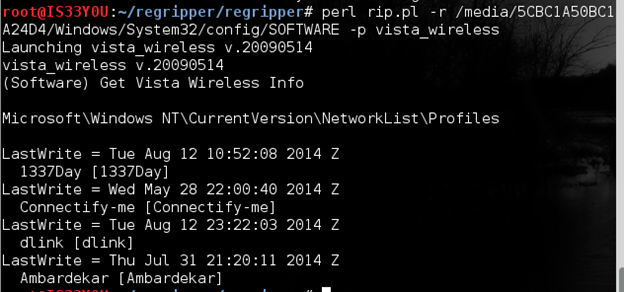
Figure 14
Notice that we have obtained a list of wireless access points that the suspect has connected with ('1337Day', 'Connectify-me', 'dlink', etc) and the time and date of last write [Figure 14].
Note: During our experimentation, we found that most of the plugins for Windows Vista worked for Windows 7 as well (as in this case).
Determining WinZip information
If the suspect's computer has WinZip utility installed then we can use the 'winzip' plugin in RegRipper for gathering information about compressed archives that were accessed by the suspect using the WinZip program:
perl rip.pl -r /media/5CBC1A50BC1A24D4/Users/intellikid/NTUSER.DAT -p winzip
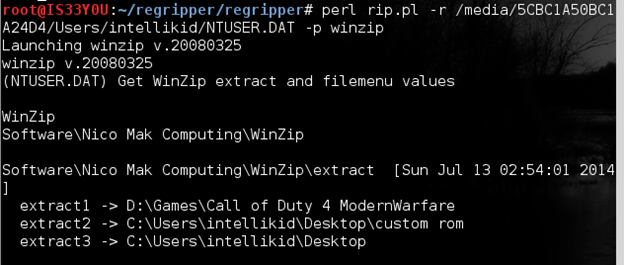
Figure 15
Notice that in this case the user has extracted 'Call of Duty 4: Modern Warfare' to 'D:Games', a 'custom ROM' to 'Desktop', etc [Figure 15].
Note: If you do not have information on which hive file is required by a specific plugin, you need to view the Perl script in a text editor of your choice (vi, nano, leafpad, notepad, etc). You will notice a mention of the hive file that the script uses. For example, the 'winvnc' plugin [Figure 16] requires 'NTUSER.DAT' [Figure 17].

Figure 16
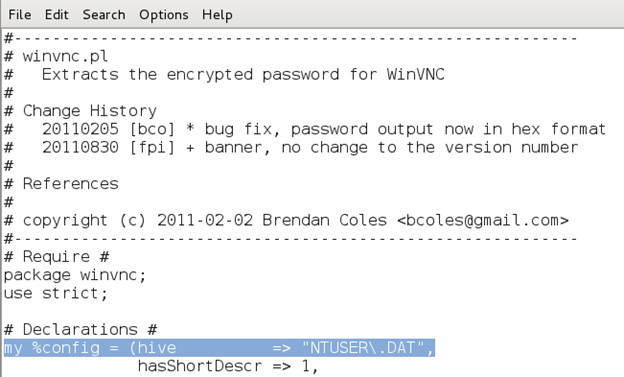
Figure 17
Registry analysis using RegRipper's graphical interface
RegRipper comes with a GUI that makes the process of ripping the registry easier. You need to browse for the 'hive' file (such as 'SAM', 'system, 'security', etc) and the text file where the results of the "ripping" process will be stored.
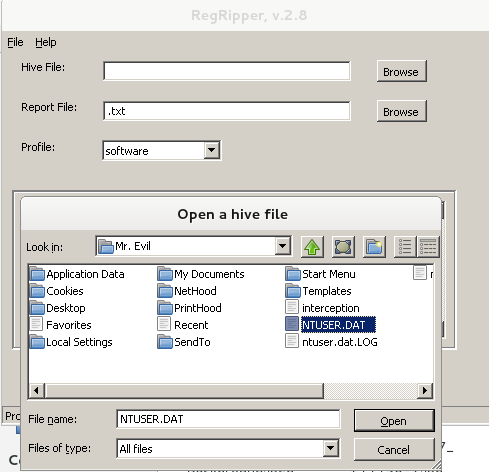
Figure 18
As an example, we load 'NTUSER.DAT' file from our evidence disk [Figure 18], select the 'ntuser' profile in RegRipper and 'rip it' [Figure 19].
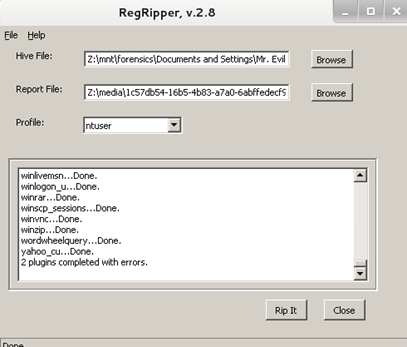
Figure 19
This causes RegRipper to 'rip' the 'NTUSER.DAT' file using all available relevant plugins. The result will be stored in the 'Report File' along with a 'Log file'. The log file contains a log of the success/failure of the plugins executed [Figure 20].
Figure 20
Conclusion
Although registry analysis offers vital information to forensics investigators, it can become complex. As Harlan Carvey rightly pointed out in his book Windows Registry Forensics [1], there are two primary reasons why Windows registry analysis is not easy: 1. The Windows registry is not very well understood. 2. The Windows registry structure changes considerably across different versions of Windows. If an analyst is successful in documenting procedures to rip specific registry keys and relevant values, these may become obsolete as a newer of the application or the Operating System is released.
Overall, the process of registry analysis is governed by the goal of the forensics investigation. How you use the information given by the analysis depends on the case that you are investigating. In any case, insouciant attitude towards the Windows registry will lead to the collection of fragmentary information during investigations. For a thorough analysis during complex investigations, it is incumbent that you are familiar with the subtleties of the Windows registry structure.
Sources
Harlan A. Carvey, "Windows Registry Forensics: Advanced Digital Forensic Analysis of the Windows Registry", Syngress, 2011.










