Sharkfest 2014 Part II
In the first part of our article, we solved the first three challenges, so in this article we will continue with rest of the challenges.
CHALLENGE #4: Browsing Buddy
TRACE FILE: BrowsingAlong.pcapng
QUESTIONS:
1. What version of dumpcap was used to capture this trace file?
Analysis - We need to find the dumpcap version. This can be done by selecting Statistics>Summary.
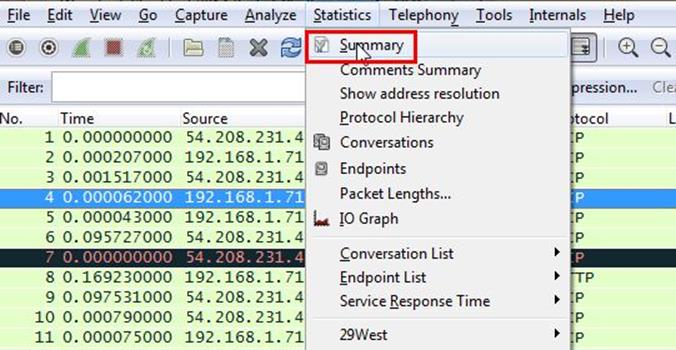
As can be seen below in screenshot the dumpcap version is 1.10.7
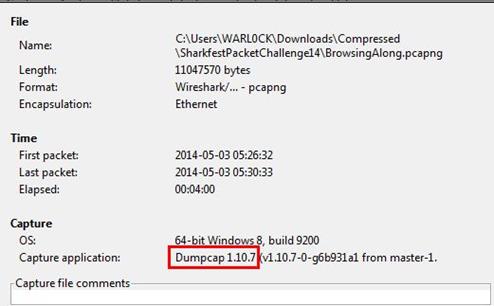
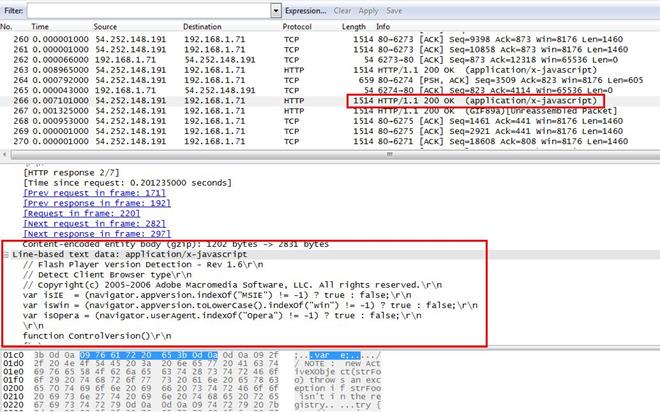
2. Which frame contains the 200 OK response to the GET request for /scripts/AC_OETags.js?
Analysis - First, we will locate this GET request by simply applying filter that is http contains "/scripts/AC_OETags.js ". Now, we can see our request
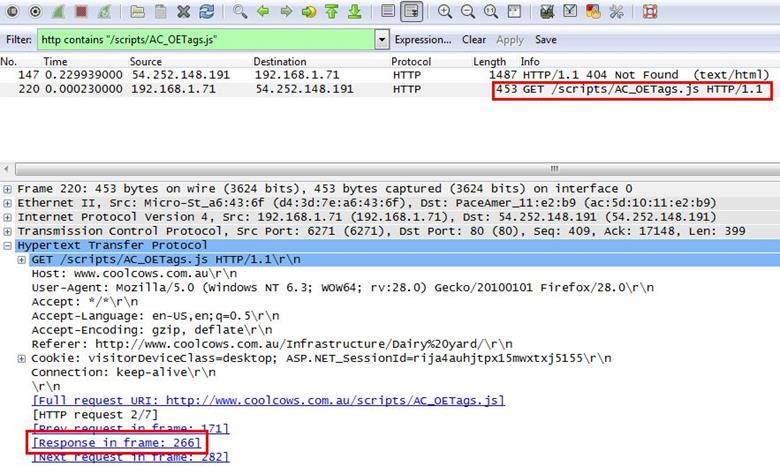
We selected the request and expanded the Hypertext Transfer Protocol tab and we can see the response in frame, which is showing frame number 266.
We jumped to the frame number 266, and we found the 200 OK response.
3. In what kind of "bar" is the client interested?
Analysis - We will search for this keyword bar by using regular expression. Apply frame matches "(?!)bar"
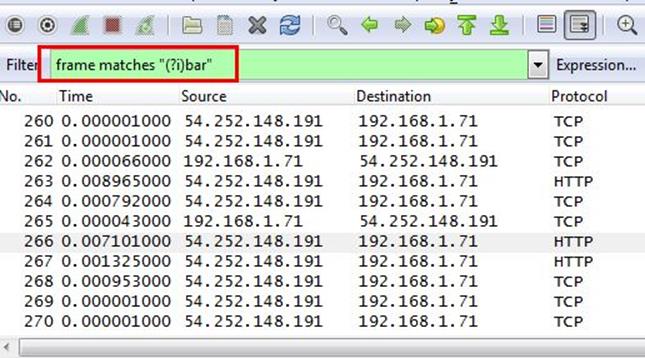
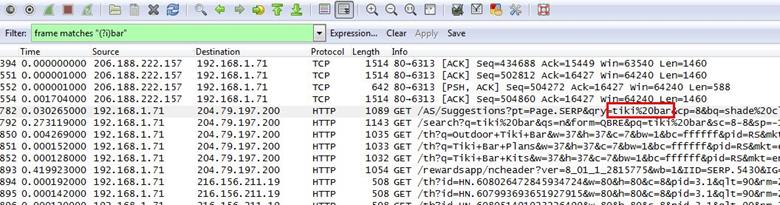
After applying the filter, we can see that there are some frames, which are displaying bar. In the first HTTP GET request we found that bar name is tiki bar.
4. Which TCP stream experienced the most retransmissions?
Analysis - We will now set the stream index as column so we can clearly see all stream index number as columns. Select any frame and expand the Transmission Control Protocol tab then right click on Stream index and Apply as column.
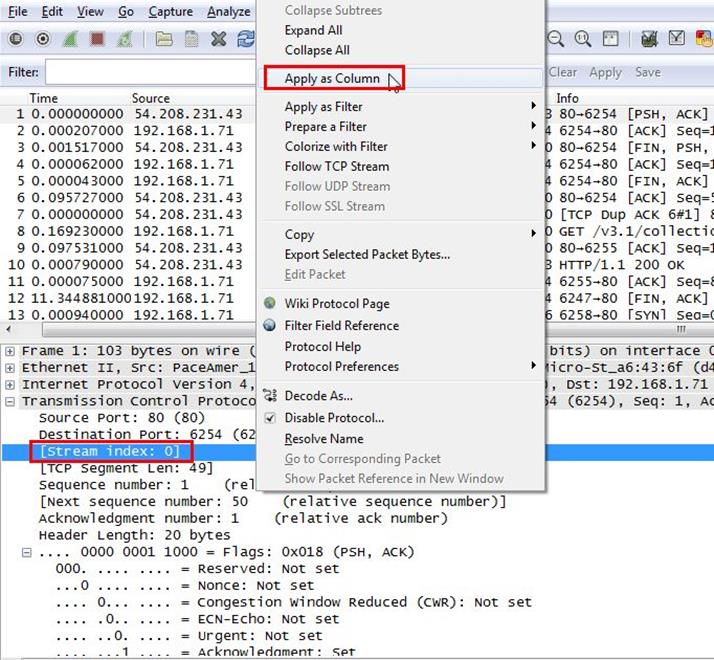
After applying the stream index as columns now we have a clear view for all frame and now we will apply a another filter: tcp.analysis.retransmission which will sort all retransmission frames.
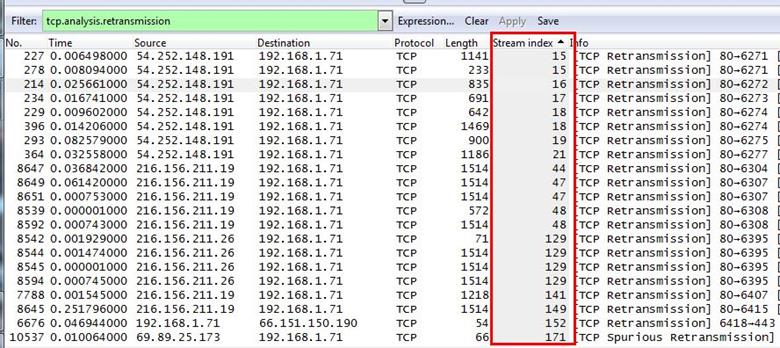
We sorted the index column-heading grouping together like numbers and we found that stream number 129 occurs four times, which has the most retransmission.
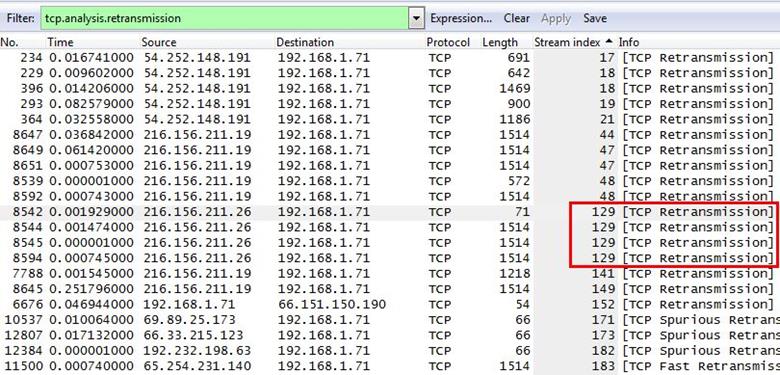
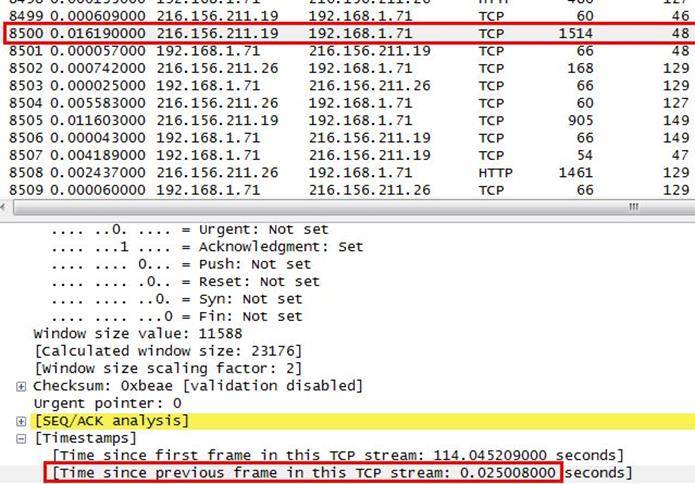
5. Frame 8500 is a retransmission triggered by duplicate ACKs. Why isn't it marked as a FastRetransmission?
Analysis - Let's jump to packet number 8500.
After getting into the frame 8500, we also noticed that there are two duplicate ACK packet before frame 8500.
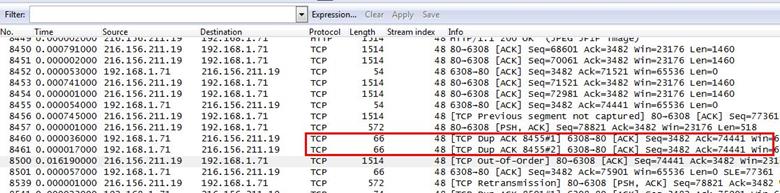
The question is why frame 8500 is not here fast transmission. We have to be clear about what is fast transmission. We google it the term and found the exact term.
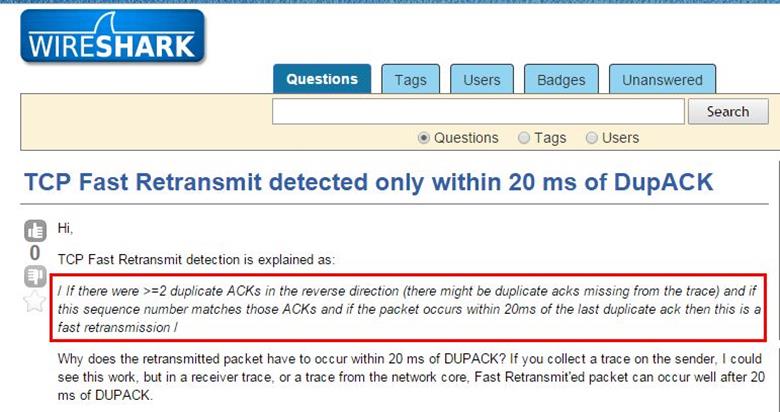
As can be seen in above screenshot, it is mentioned that if there are two duplicate ACKs are in the reverse direction and if the packet occurs within 20ms of the last duplicate ACK then it will consider as fast retransmission.
Our scenario is also the same we have the two duplicate ACKs and we need to find the time of the ACK packet, which is in frame 8500. We selected the frame 8500 and right click on it select Protocol Preferences>Calculate conversation timestamps.
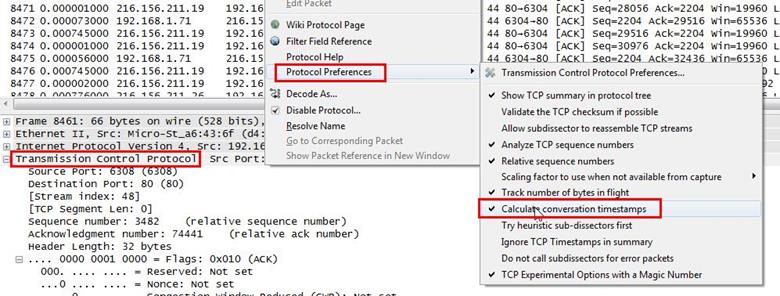
Now we can see our timestamp, which is showing which is 0.02500 seconds and it is greater than 20ms so that's why it is not a fast retransmission.
CHALLENGE #5: OUCH!
TRACE FILE: AskSnopes.pcapng
QUESTIONS:
1. What web server software issued by www.snopes.com?
Analysis - The domain name be found from host header so we will set host header column where we will see all domain name. Select any HTTP request and expand the Hypertext Transfer Protocol then right click on Host header and then Apply as Column.
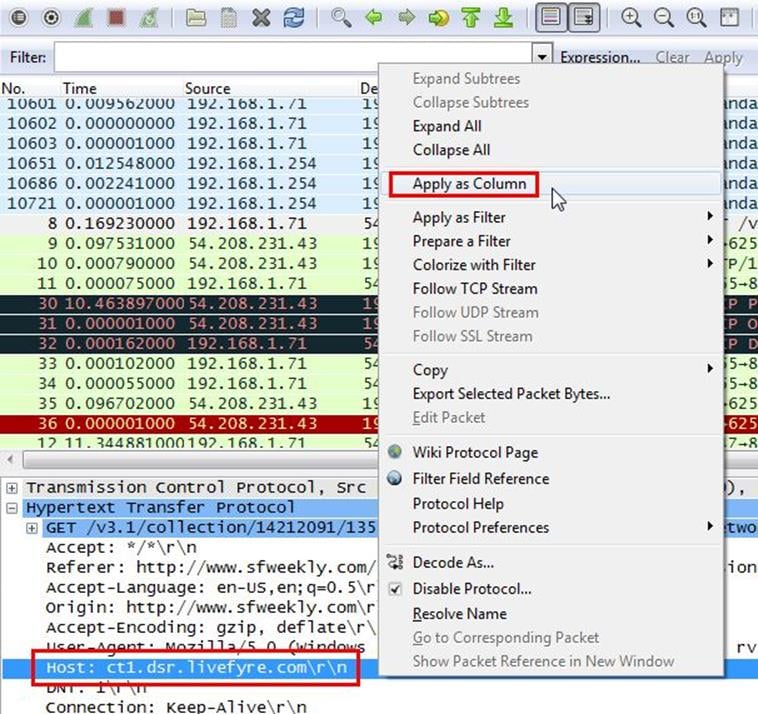
Now we can see our host www.snopes.com in host column.
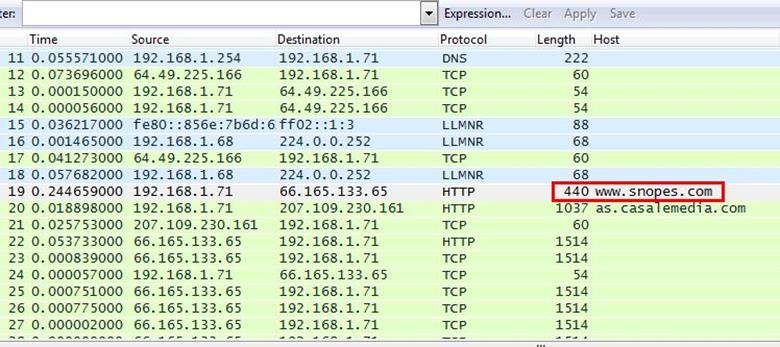
Right click on the selected packet and then select Follow TCP stream.
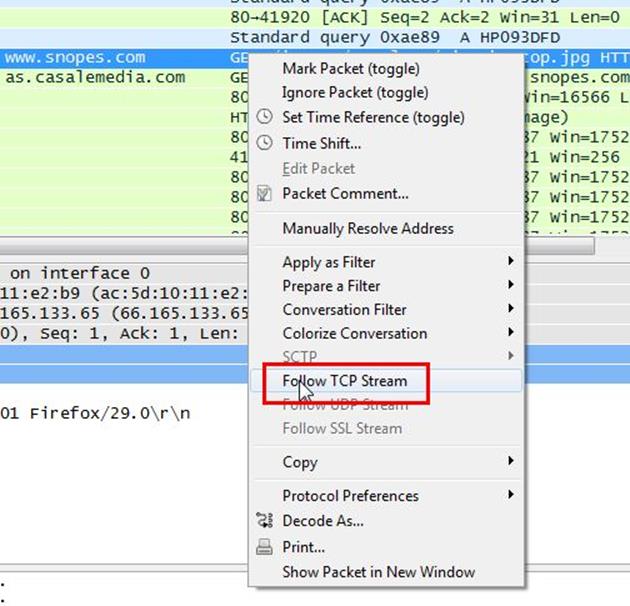
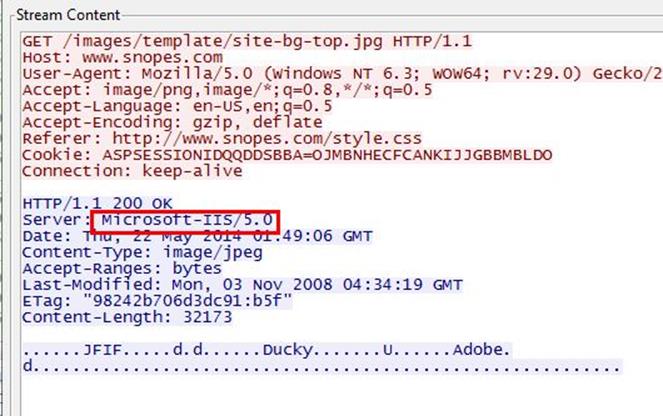
Now we can see the webserver name in server header it is Microsoft IIS 5.0
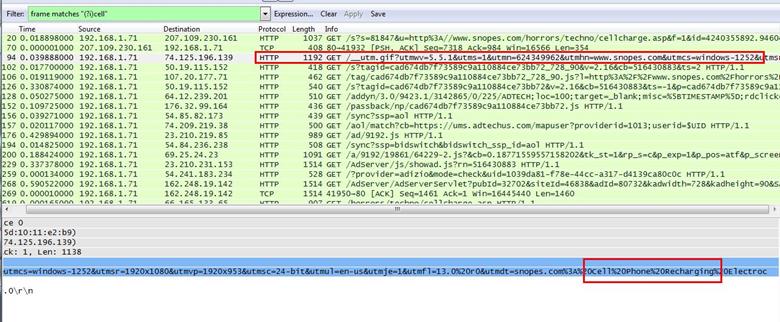
2. About what cell phone problem is the client concerned?
Analysis - Client talking about cell so we search for cell keyword in whole packets. We will use regular express for searching the cell keyword. Apply frame matches "(?!)cell"
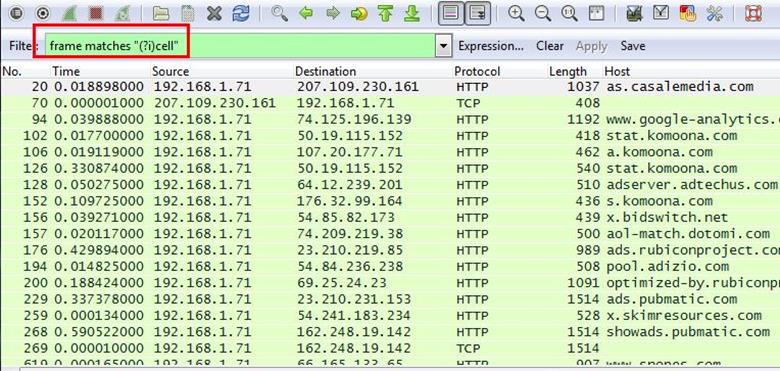
After applying the filter now, we will start to check every HTTP request. We noticed in the first HTTP request cell keyword is in URL and it was about cell phone charging issue.
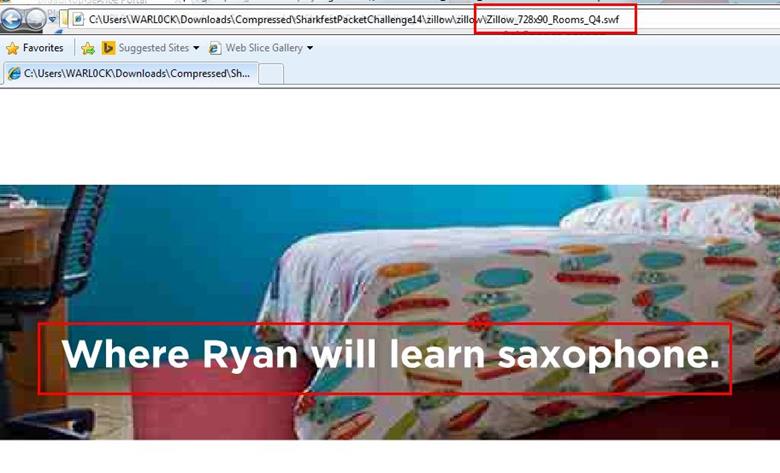
3. According to Zillow, what instrument will Ryan learn to play?
Analysis - As we did in the last challenge, we will apply a regular express filter for the Zillow keyword. Apply frame matched "(?!)zillow"
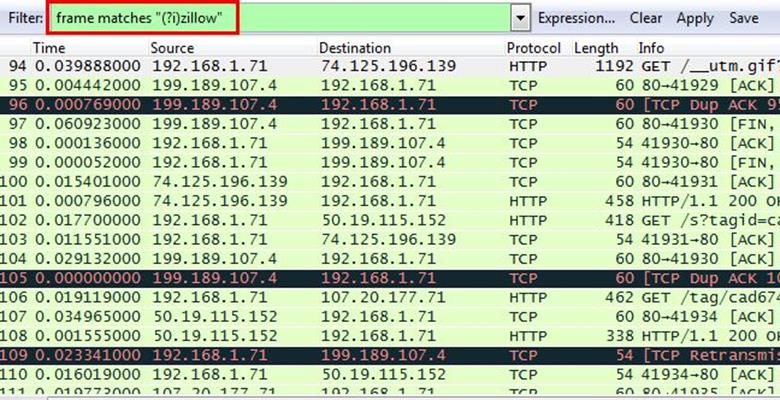
After applying the filter, we found only one packet with the Zillow keyword
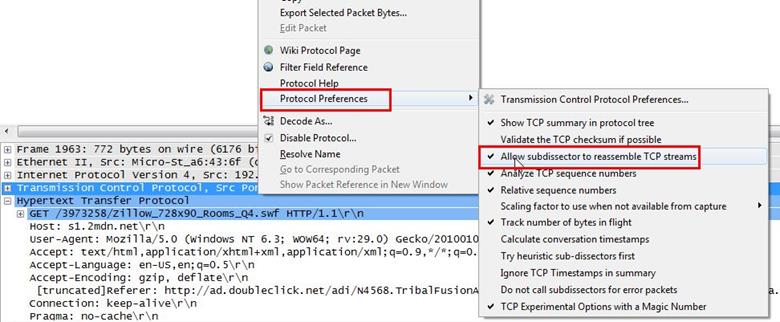
Select the packet and expand the Hypertext Transfer Protocol tab right click on it go to Protocol Preferences and check Allow subdissector to resemble TCP stream.
Now go to file and select Export Objects > HTTP. It will save all objects from the packet.
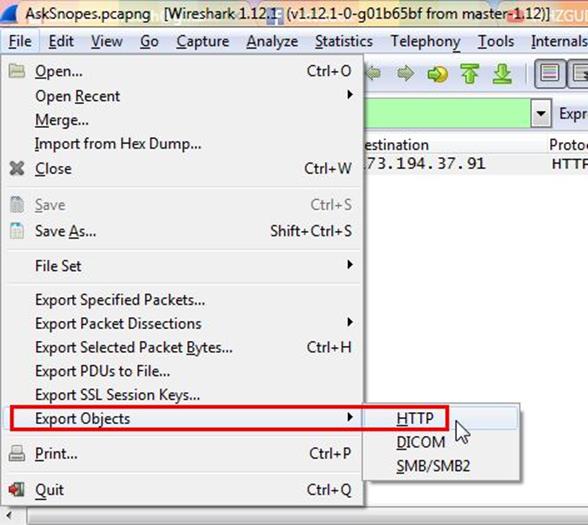
Click on save all.
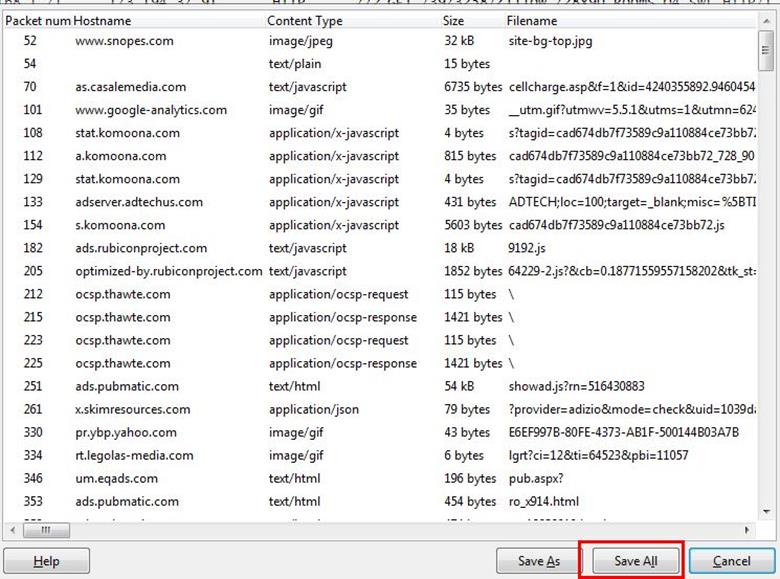
After saving all files in a directory and we found a swf file with name Zillow. After opening the flash file, we saw that Zillow was trying to learn saxophone.
4. How many web servers are running Apache?
Analysis - The web server name can be retrieved from HTTP response header. So will apply filter http.response and we can see all http response packets.
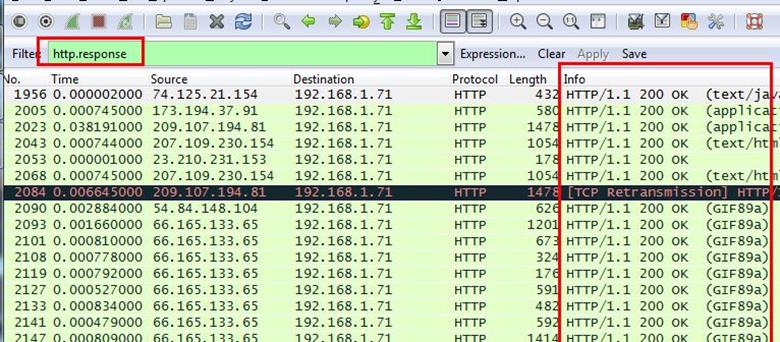
Now we will set the server header as column select any packet and right click on it then select Apply as Column.
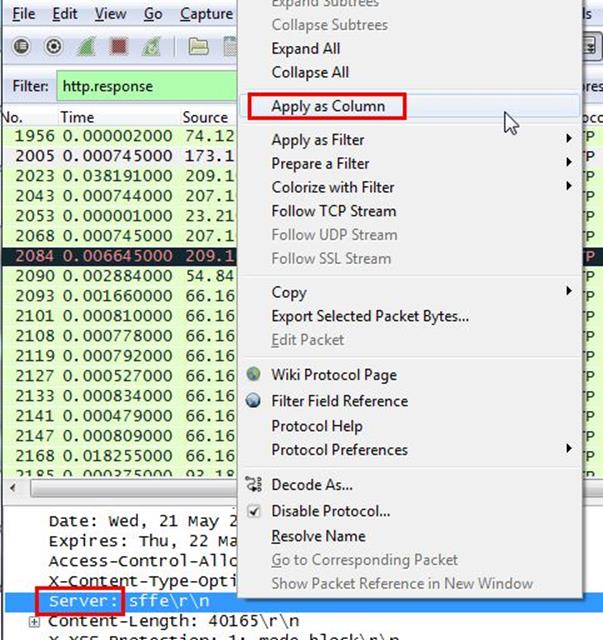
Now can see the server column where all server name is showing.
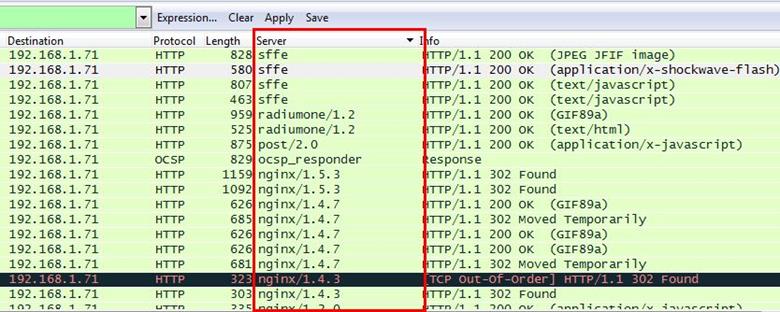
Now we have to check how many Apache packets are there we can't count manually for each packet so we will apply another filter http.server contains "Apache"
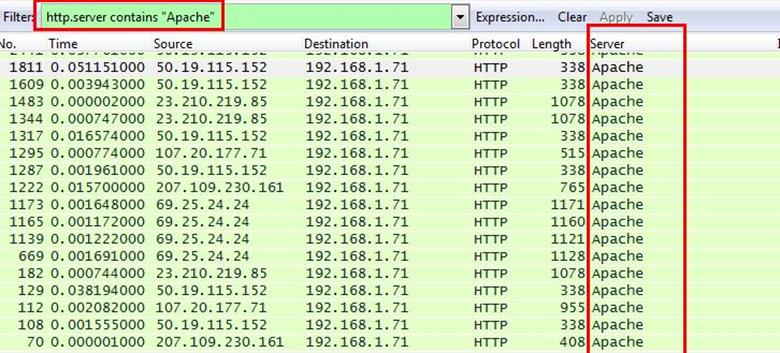
After applying filter go to Statistics > Endpoints
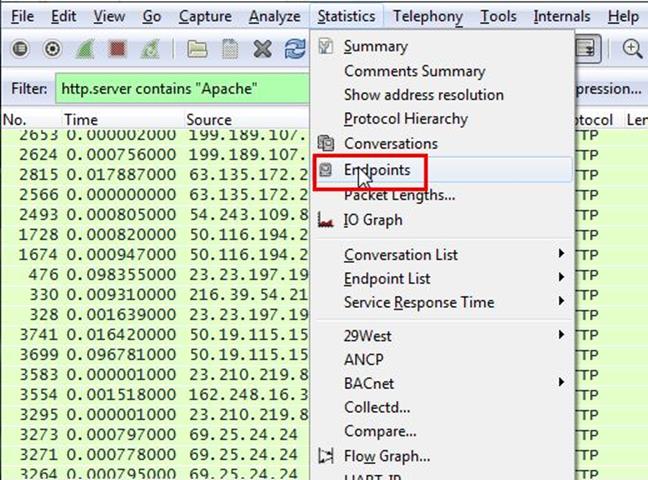
It will show all connections
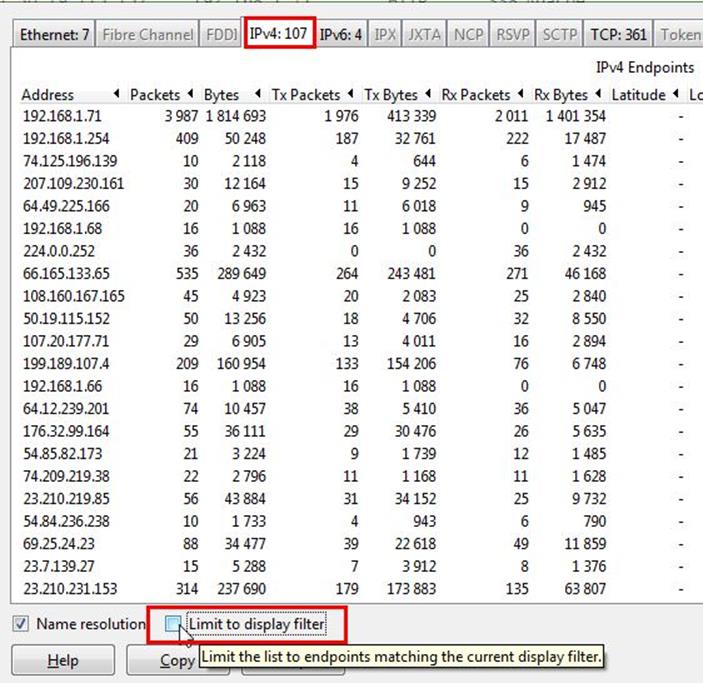
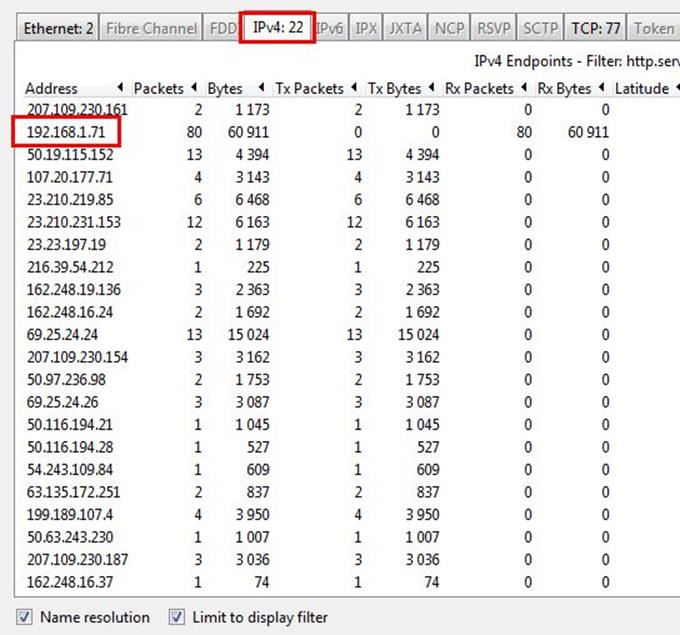
Check the limit to display filter then it will show the actual Apache connections. Now there are showing 22 connections but will exclude 192.168.1.71 because it is client's IP not a server IP so there are actual 21 Apache servers.
5. What hosts (IP addresses) think that jokes are more entertaining when they are explained?
Analysis - Lets apply the filter with joke keyword apply frame contains "joke" and now we can see all requests with joke keyword
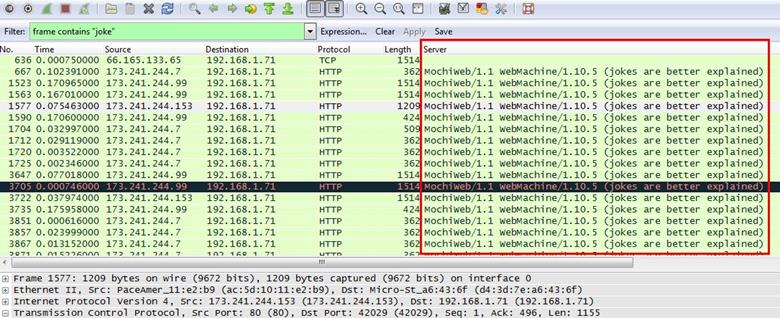
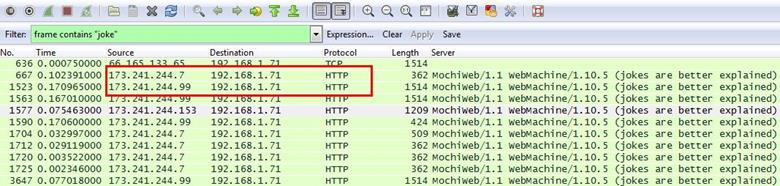
We can see the messages are coming from 173.241.244.7 and 173.241.244.99.
End of the challenge.
References - http://www.wiresharktraining.com/sharkfest2014.html










