Windows registry forensics using ‘RegRipper’ command-line on Linux
Windows registry is a gold mine for a computer forensics investigator. During case analysis, the registry is capable of supplying the evidence needed to support or deny an accusation. There are other sources of information on a Windows box, but the importance of registry hives during investigations cannot be overstated.
The registry is a hierarchical database that houses several keys. This hierarchical structure can get complex, and locating relevant information resident in the registry can become time-consuming and tedious. 'RegRipper' attempts to solve this issue by deploying pre-fetched scripts that can extract and display specific information located in the registry hive files. RegRipper is written by Harlan Carvey, who has also written a number of other useful tools. In this paper, we perform an in-depth exploration of Windows registry forensics using RegRipper.
Role: Computer Forensics Investigator
Purpose: Locate inculpatory or exculpatory evidence in the disk so that it may be presented in the court of law.
Assumptions: We assume you have access to Windows registry 'hives' for analysis. These may be extracted from the EnCase image (Downloads) or you may use your own.
Evidence Disk: You can grab the EnCase image of the Greg Schardt hacking case here: part1 and part2.
Tools used: You can download RegRipper for Linux here, and RegRipper for Windows here.
Tasks performed: During the course of this investigation, you will be required to perform the following tasks:
- Converting and Mounting an E0? (EnCase image) on-the-fly over a Linux box
- Using RegRipper to analyze Windows registry hives for the purpose of extracting evidence
- Comprehending the different 'plugins' available for RegRipper and the purpose that they serve
- Using RegRipper in command-line mode and grasping the available options
Why RegRipper?
RegRipper is a flexible open source tool that can facilitate registry analysis with ease. It contains pre-written Perl scripts for the purpose of fetching frequently needed information during an investigation involving a Windows box. We are using RegRipper because of the simplicity of the tool and the availability of numerous plugins that capture specific information from the registry.
What are registry hives?
Hives are groups of keys, subkeys and relevant values that govern the Windows Operating System environment. Hives hold information about: user profiles, applications, configurations, desktop, network connections, printers, etc. RegRipper works by pulling information from the supporting files of the Windows registry hive.
Where are these Windows registry hive files located?
Before we start our analysis, it is important that you are familiar with the locations of the Windows registry hive files. In this case, we have analyzed registry hives from a Windows XP box. However, we are mentioning the location of registry hive files both, on Windows XP box, and a Windows 7 box. On a Window XP system, you can find them at:
- WINDOWS/system32/config/software
- /WINDOWS/system32/config/system
- /WINDOWS/system32/config/SAM
- /WINDOWS/system32/config/SECURITY
- /Documents and Settings/Mr. Evil/NTUSER.DAT
On Windows 7 box, you can find them at:
- /Users/intellikid/NTUSER.DAT
- /Windows/System32/config/SOFTWARE
- /Windows/System32/config/SAM
- /Windows/System32/config/SECURITY
- /Windows/System32/config/SYSTEM
- Note: Please substitute profile name (or username) above with what is relevant in your case.
After downloading the EnCase image, use 'ewfinfo' to see the stored metadata. Notice that the acquisition MD5 hash is: aee4fcd9301c03b3b054623ca261959a [Figure 1].
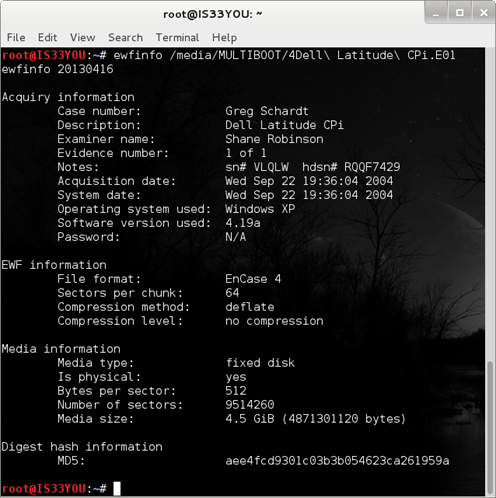
Figure 1
How to convert an E0* (EnCase image) to a 'dd' image on-the-fly on a Linux box
Before we start our analysis using RegRipper, it is useful to learn how to convert an EnCase image file into a 'dd' image which can then be easily mounted on our Linux machine. We will use the tool 'xmount' for this purpose. Xmount can help convert 'on-the-fly' between many disk image types.
Make sure you have xmount on your system, if not, install it using:
apt-get install xmount
The following commands will create a directory and mount the case image there:
mkdir /mnt/xmount/
xmount --in ewf /media/MULTIBOOT/4Dell Latitude CPi.E?? /mnt/xmount/
Now calculate an MD5 hash of the mounted 'dd' image, by using 'md5sum':
md5sum /mnt/xmount/4Dell Latitude CPi.dd
Make sure the acquisition hash matches the verification hash. Preserving the integrity of the evidence image is of paramount importance during the investigation. Read more here.
Once you have converted the EnCase image into a 'dd' image using 'xmount', it can be easily mounted using 'mount' in Linux. But first you will need the value corresponding to the 'start sector' of the NTFS volume inside the dd image. Use the 'fdisk' partition table tool in Linux for this purpose:
fdisk -l 4Dell Latitude CPi.dd
Notice the start sector is located at '63' [Figure 2]. Multiply this value by 512 bytes and we get: 32256
Now, we can mount the NTFS volume using 'mount' in Linux:
mount -t ntfs -o ro,offset=32256 /mnt/xmount/4Dell Latitude CPi.dd /mnt/forensics/
(Notice that here we are mounting the 'dd' image at '/mnt/forensics')
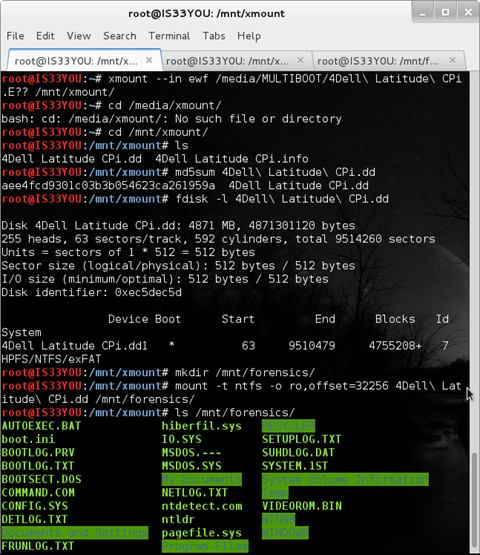
Figure 2
How to use RegRipper's command-line interface
We will start with using the command-line interface of RegRipper for our analysis.
Execution of the main Perl script of RegRipper ('rip.pl') shows you the different options that it has [Figure 3].
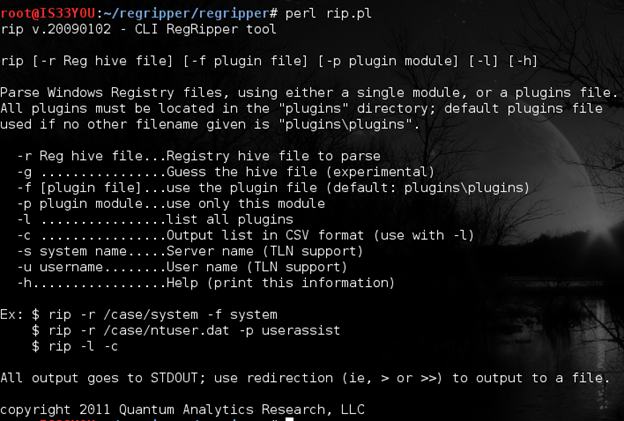
Figure 3
Notice that –r is used to load a registry hive file, while –p is used to load a specific plugin module. You can use –l to list all of the available plugins [Figure 4].
Note: You will notice that we are using RegRipper on a Linux box. However, you are free to work on a Windows machine. RegRipper works well on both.
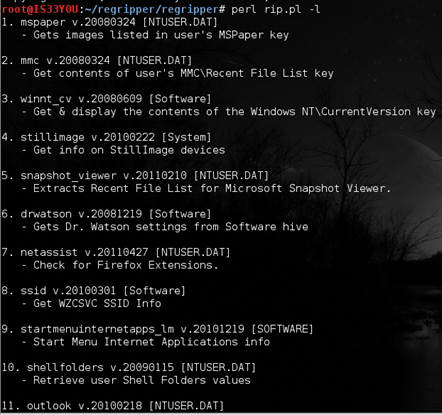
Figure 4
Beginning Windows Registry Forensics with RegRipper
Now, we can begin analyzing the registry hives located in the dd image that we have just mounted. We will explore specific registry keys for information one at a time using relevant RegRipper plugins.
Determining installed product information
To get information about the Operating System installed on this computer, we use the 'product' plugin as follows:
perl rip.pl -r /mnt/forensics/WINDOWS/system32/config/software -p product
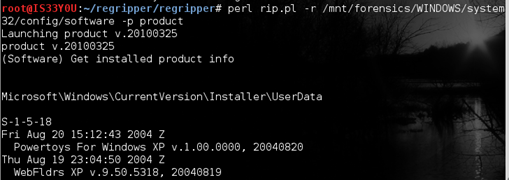
Figure 5
Determining the product type
The suspect's Windows box could have been a workstation, a standalone server or a domain controller. To determine this information, we use the 'producttype' plugin as follows:
perl rip.pl -r /mnt/forensics/WINDOWS/system32/config/system -p producttype
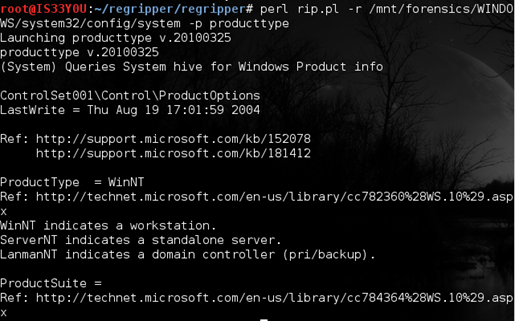
Figure 6
The result indicates that this was a WinNT workstation [Figure 6].
Determining the Windows version
In order to determine the version of Windows installed on this computer, we use the 'winver' plugin:
perl rip.pl -r /mnt/forensics/WINDOWS/system32/config/software -p winver
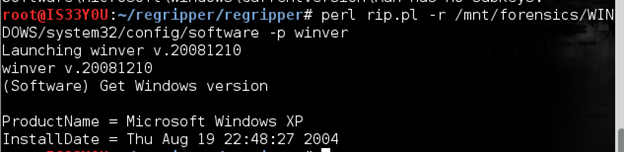
Figure 7
Notice that this computer has Microsoft Window XP installed and the date of installation is Aug 19, 2004 [Figure 7].
Determining the network cards used
Here, we pull information regarding the network cards that were in use on this computer using the 'networkcards' plugin. The command used for this purpose is:
perl rip.pl -r /mnt/forensics/WINDOWS/system32/config/software -p networkcards
The result shows the two network cards that were in use over the Ethernet (wired) and the wireless interface. It also indicates the date and time when these cards were last used [Figure 8].
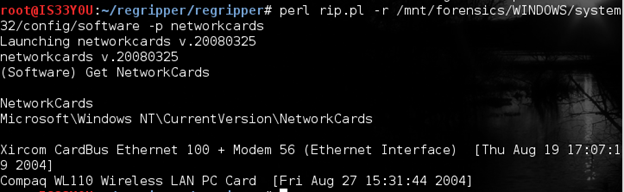
Figure 8
Note: During experimentation, it is best that you do not run RegRipper on a live registry hive file.
Determining the DHCP information
DHCP is the Dynamic Host Control Protocol that is responsible for allocating IP addresses to computers on a network. We use the 'nic' plugin to get the DHCP information from the Network Interface Card, as follows:
perl rip.pl -r /mnt/forensics/WINDOWS/system32/config/system -p nic
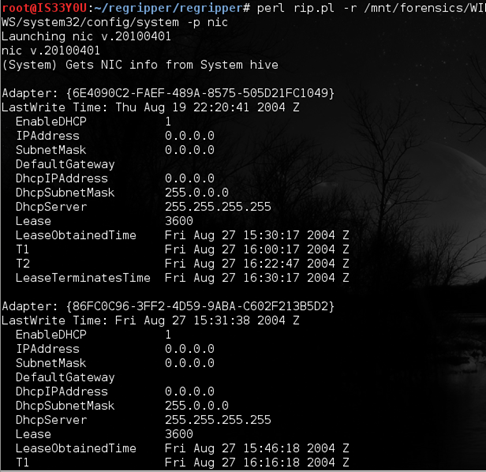
Figure 9
Notice that DCHP is enabled on both the network adapters and time when the lease was obtained from the DHCP server. Also notice that lease lasted for 3600 seconds or 60 minutes (expires after one hour).
Determining the wireless access points information
Since this is a wireless hacking case (see case details here), we are interested in determining the SSIDs that this computer authenticated to. We can pull this information using the 'ssid' plugin as follows:
perl rip.pl -r /mnt/forensics/WINDOWS/system32/config/software -p ssid
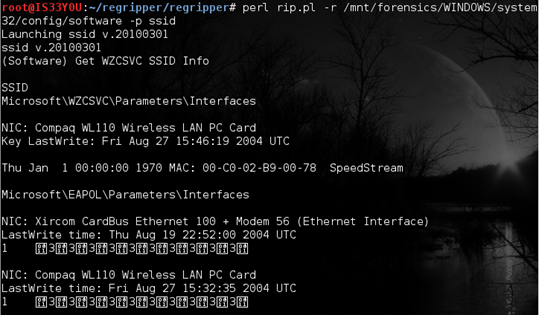
Figure 10
Determining the shutdown time
To get the time this computer was last shutdown, we use the 'shutdown' plugin as follows:
perl rip.pl -r /mnt/forensics/WINDOWS/system32/config/system -p shutdown
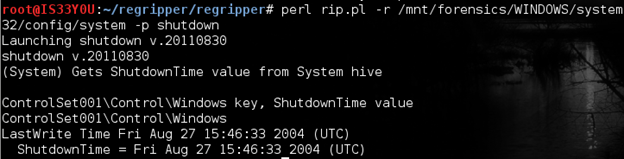
Figure 11
Determining the time zone
To get information about the time zone that this computer was in, we use the 'timezone' plugin as follows:
perl rip.pl -r /mnt/forensics/WINDOWS/system32/config/system -p timezone
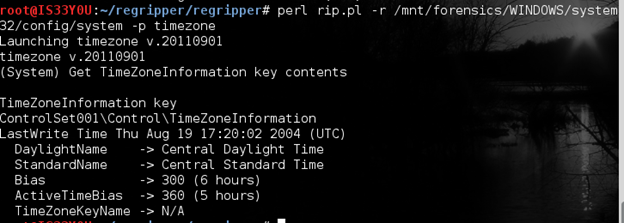
Figure 12
We notice that this computer was in the Central Daylight Time or CDT. [Figure 12]
Determining all installed applications
To get information about the applications that are installed on this computer, the 'uninstall' plugin loops through the keys stored under 'uninstall' in the registry. We obtain this information as follows:
perl rip.pl -r /mnt/forensics/WINDOWS/system32/config/software -p uninstall
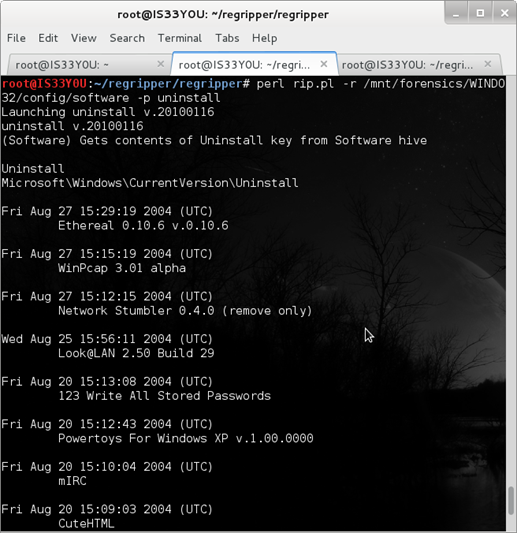
Figure 13
Notice that this plugin sorts the list of installed applications according to date and time (latest first). Also notice the various hacking tools installed on the suspect's computer such as 'Ethereal', 'Network Stumbler', 'WinPcap', etc [Figure 13].
Determining user SIDs
The 'ProfileList' key in the registry can be used to resolve SIDs to users on the machine. If a user has logged onto this machine, a subkey with that user's SID as its name will be created under ProfileList. Use the 'profilelist' plugin in RegRipper to pull this information:
perl rip.pl -r /mnt/forensics/WINDOWS/system32/config/software -p profilelist
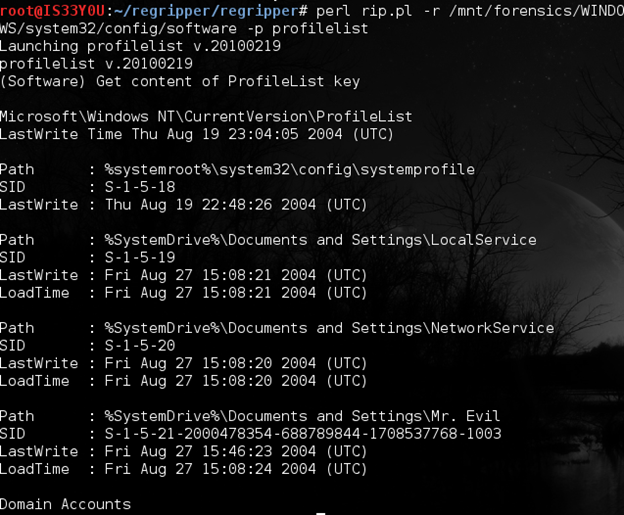
Figure 14
Determining the recent documents used
While performing a forensics investigation, recent documents used on the suspect's computer are of special interest to the investigator. To take a look at what recent documents the suspect has used, we use the 'recentdocs' plugin:
perl rip.pl -r /mnt/forensics/Documents and Settings/Mr. Evil/NTUSER.DAT -p recentdocs
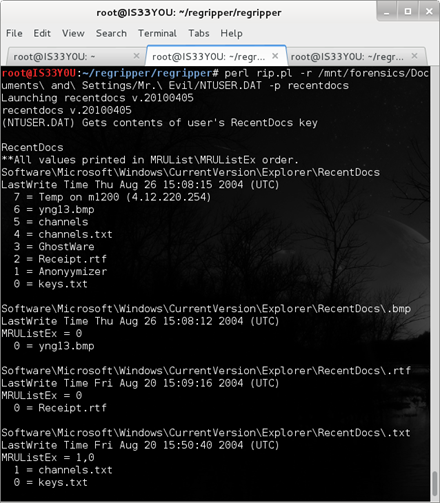
Figure 15
Note: By default, Windows stores 15 items in the My Recent Documents option.
Extracting information from the 'winlogon' key
Winlogon is a valuable key that can help in determining autostart information for the machine. This key is responsible for controlling the events that occur after you logon to a Windows machine. The 'winlogon' plugin is a comprehensive plugin that is capable of extracting information from the winlogon key, as follows:
perl rip.pl -r /mnt/forensics/WINDOWS/system32/config/software -p winlogon
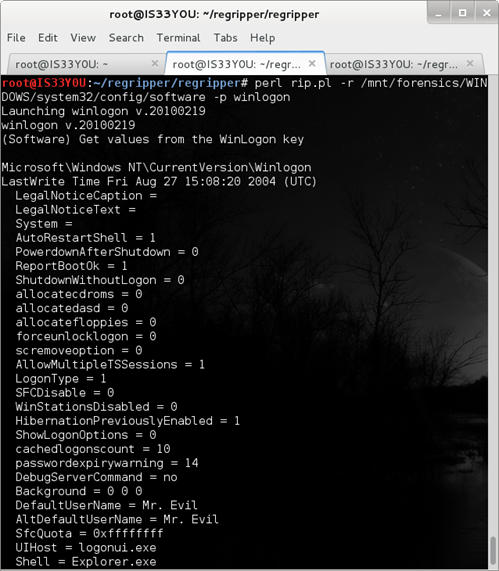
Figure 16
Determining suspect's web-browsing history
The 'TypedURLs' key in the registry holds information about the web addresses that this specific user has previously typed in the browser. The purpose of this key is to populate the drop down menu pertaining to URLs in order to improve user experience. We use the 'typedurls' plugin in RegRipper to access the information stored in this key, as follows:
perl rip.pl -r /mnt/forensics/Documents and Settings/Mr. Evil/NTUSER.DAT -p typedurls
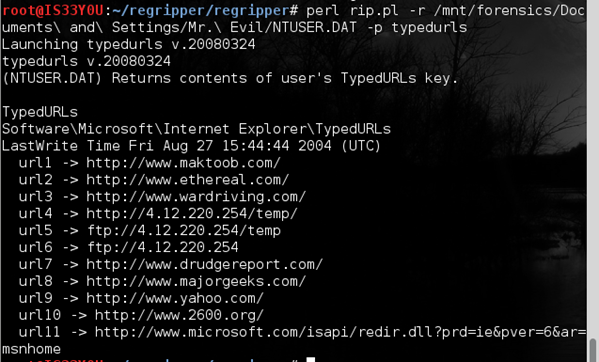
Figure 17
Notice that the suspect has been visiting websites related to 'hacking' tools. [Figure 17]
Collecting information about unread emails
Windows registry stores information about the unread emails of the outlook user. We use the 'unreadmail' plugin to extract this information:
perl rip.pl -r /mnt/forensics/Documents and Settings/Mr. Evil/NTUSER.DAT -p unreadmail
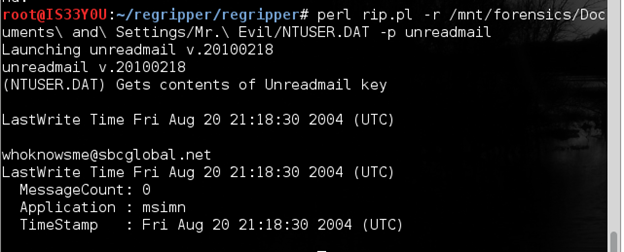
Figure 18
Notice that the registered email account of the suspect is 'whoknowsme@sbcglobal.net'. There are no unread emails [Figure 18].
Determining applications set to auto start
The 'Run' key in the NTUSER.DAT file contains the locations of the programs that are set to autostart once this specific user logs into the machine. We capture the contents of the 'Run' key using the plugin 'user_run':
perl rip.pl -r /mnt/forensics/Documents and Settings/Mr. Evil/NTUSER.DAT -p user_run
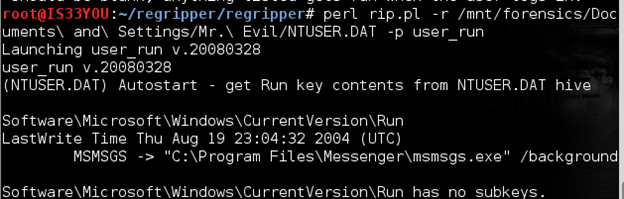
Figure 19
Determining the value of the 'userinit' registry key
The registry key 'UserInit' is used to indicate what applications can be launched once a user logs onto the computer. The default application stored in this key is: 'C:WINDOWSsystem32userinit.exe'. We use the plugin 'userinit' to pull information from this key:
perl rip.pl -r /mnt/forensics/WINDOWS/system32/config/software -p userinit
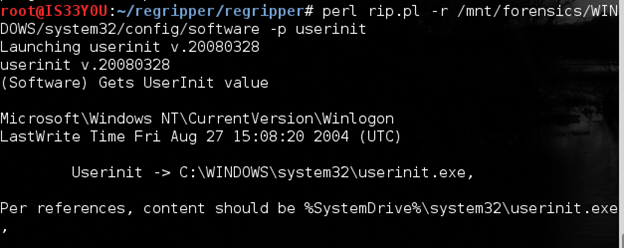
Figure 20
Determining the user's printers
Printers are of interest during investigations since they may have been used to print sensitive documents that can help shed further light on the case. The investigator determines the printers used by the suspect on this computer using the 'printers' plugin:
perl rip.pl -r /mnt/forensics/Documents and Settings/Mr. Evil/NTUSER.DAT -p printers
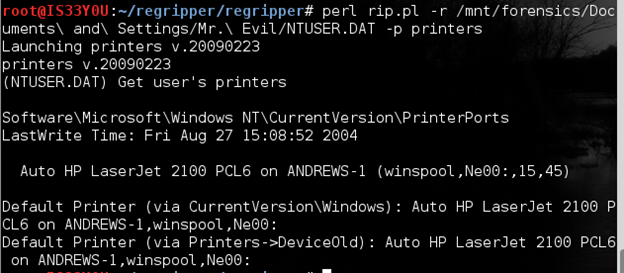
Figure 21
Notice that the default printer used on this device is an 'Auto HP LaserJet 2100 PCL6' and the last write time was Aug 27, 2004 at 15:08:52 [Figure 21].
Collecting information about 'Cain & Able'
We have noticed the presence of Cain & Able sniffing and password cracking utility installed on this system. We use the 'cain' plugin to pull more information about this tool:
perl rip.pl -r /mnt/forensics/Documents and Settings/Mr. Evil/NTUSER.DAT -p cain
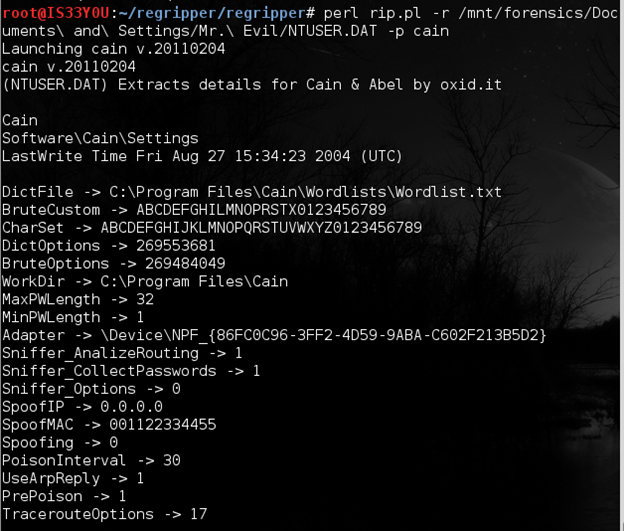
Figure 22
Notice the location of the Dictionary file set as: 'C:Program FilesCainWordlistsWordlist.txt' [Figure 22]. Also notice other settings like the Sniffer is set to collect passwords and analyze routing protocols. The spoofed MAC (hardware) address of the computer is set to be '001122334455' and the password character length is set to range from 1 to 32. The working directory is set as 'C:Program FilesCain'.
Conclusion
These are only a handful of the plugins available with the RegRipper tool used in Windows registry forensics. The beauty of this tool lies in its flexibility and scalability. The plugins are Perl scripts that are contributed by the forensics community. During your forensics case investigations, if you find yourself extracting information from a particular part of the registry frequently, you may consider writing a Perl script to automate the task. The script can be shared as a new plugin that can be used by other investigators.
Computer crimes pose preposterous threats to modern society, as computers are omnipresent. These crimes can be: fraud, intrusions, unavailability attacks, piracy, etc. Computer forensic investigators locate inculpatory and exculpatory evidence from a suspect's computer system. When they encounter a Windows box, Windows registry proves to be a critical source of information during the investigation. Windows registry is a complicated database of multitudinous keys that are concealed at numerous locations. Tools like RegRipper provide us an undemanding way of drawing information from the registry hives.
In the next paper, we take a look at the graphical interface of RegRipper and numerous other plugins of interest to the forensics investigator.










