Getting started with android forensics
This article introduces Android forensics and the techniques used to perform Android forensic investigations. We will discuss Android file systems, data acquisition, analysis, and various tools available for Android Data Extraction.
The smart phone market is growing higher and higher. With the drastic changes in technology, smart phones are becoming targets of criminals. Because of the fact that most of the people are completely addicted to the mobile devices to do our daily tasks, ranging from setting up a reminder to wish our dear ones well on special occasions, to online banking transactions, mobile devices contain a lot of sensitive data which is of an investigator's interest. As Android is one of the leading smart phone operating systems, it it is important to have knowledge of Android forensics.
Android forensics is different from regular disk forensics because of various reasons. It supports various file systems which are specific to Android. We may look for the following data on Android devices: SMS, MMS, emails, call logs, contacts, photos, calendars, notes, browser history, GPS locations, passwords, data stored on SD cards, etc.
It is important to understand file systems, directory structures, and how and where the data is stored on the devices before getting into actual forensics.
Android directory structure
Android has got a directory structure specific to it. We can look at the directory structure of the device using "adb shell". It is also possible to see the directory structure of the device using DDMS. The following figure shows the file system of my device "Sony Xperia E" using "adb shell".
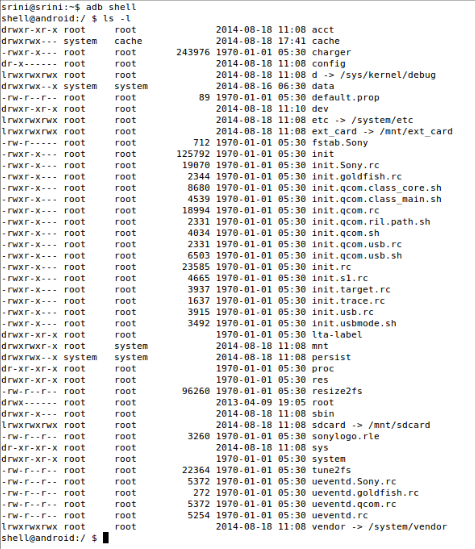
The above figure shows many files and folders on the current device. The most important locations for a forensic analyst are /system, /data, /sdcard, /ext_card.
/system: It contains operating system-specific data.
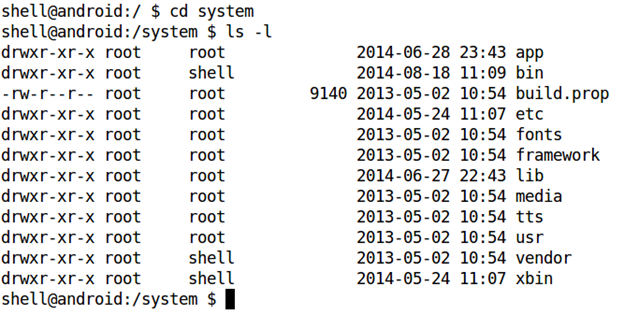
As we can see in the above figure, this directory contain various sub directories to hold information about the system apps, fonts, libraries, executable etc.
/data: It contains user-specific data such as data stored by an SMS application. We can see the executable files of each application installed in the "/data/app" directory. This requires root privileges, which mean a user without a rooted device cannot see the contents of this directory. The following figure shows how each installed application's binary can be seen on the device (the output is truncated).
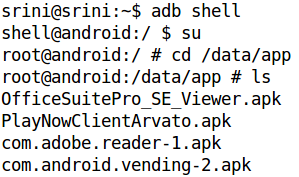
User data resides on the "/data/data/[app package]/" directory. Due to security reasons, data in each directory cannot be accessed by other applications.
/sdcard and /ext_card: In this specific case, we got sdcard for internal storage and ext_card for external storage. Usually, sdcard is given for external storage. These are used to store user data such as images, music files, videos etc.
Android file systems
Having basic knowledge of Android file systems is always good before diving into Android forensics. This is because Android has support for various file systems. The main partition of Android file system is often partitioned as YAFFS2 (Yet Another Flash File System). YAFFS2 is specifically designed for embedded systems such as smart phones. It provides greater efficiency and performance.
To see the listing of supported file systems, we can use the following command on "adb shell".
"cat /proc/filesystems"
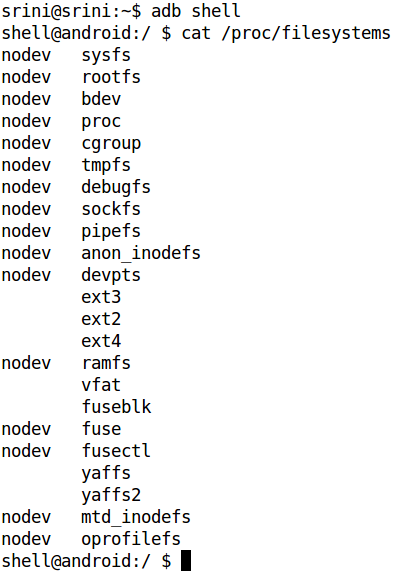
As we can see in the above figure, we got a list of file systems supported by the device. The "nodev" entry next to the file system indicates that there is no physical device associated with that particular file system. Android supports ext2, ext3, and ext4 file systems (used by Linux systems) and the vfat file system used by Windows-based systems. Since it is targeted for mobile devices, Android supports YAFFS and YAFFS2 file systems, since it requires supporting NAND chips used in these devices.
Android's file system is divided into different partitions. In order to see the different partitions that are mounted on an Android device, we can get a shell on the device and execute the following command: "mount". This is shown in the following figure.
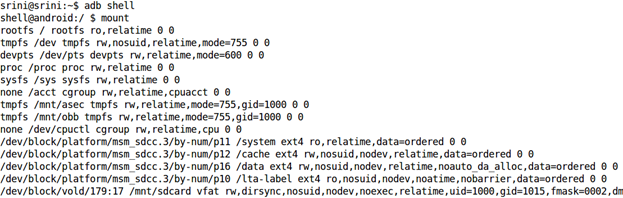 As we can see in the above figure, there are various partitions mounted on the device.
As we can see in the above figure, there are various partitions mounted on the device.
If we observe the above figure, there are few important file system partitions such as /system, /cache, /data using ext4 as their file system type rather than YAFFS. This is because, starting from Gingerbread, Android has replaced YAFFS file system with ext4.
Data acquisition methods
Data acquisition is the process of extracting data from the evidence. As we discussed earlier, data acquisition on mobile devices is not as simple as standard hard drive forensic acquisition. These data acquisition techniques are broadly divided into the following types.
- Manual Acquisition:
The examiner utilizes the user interface of the mobile device to investigate the content. While browsing the device, the examiner takes pictures of each screen. This method does not require any tools to perform data acquisition. Apart from the advantages, the biggest disadvantage of this method is that only data visible to the users on the phone can be recovered, and obviously it is time consuming.
- Physical Acquisition:
Similar to physical acquisition process on standard digital forensics, physical acquisition process on mobile devices creates a bit-by-bit copy of an entire file system. It creates a copy of the entire file system which contains data present on a device, including the deleted data and unallocated space.
- Logical Acquisition:
Logical extraction acquires information from the device using the original equipment manufacturer application programming interface for synchronizing the phone's contents with a personal computer.
Most of the tools available for free perform Logical Acquisition. Logical Acquisition is the process of extracting data that is accessible to the users of the device and hence it cannot acquire deleted data or the data in unallocated space. The above statement has limitations in some cases.
Imaging an SD card with FTK Imager
FTK Imager can be downloaded from the following link. http://www.accessdata.com/support/product-downloads
It is important to get a bit by bit copy of the phone's SD card, since it can be used as a valuable data treasure during investigations. As a best practice, we need to use a write blocker to maintain integrity of the evidence.
SD cards generally are of the FAT32 file system. So, we can use traditional imaging tools and acquire the image of the SD card. In this section, we are going to use a popular tool known as FTK Imager to get the image of the SD card.
Here are the steps:
- Safely remove the SD card from the mobile device and connect it to the workstation using a card reader.
- Launch FTK Imager tool. This appears as shown in the figure below.
- Now, navigate to "File" and click "Create Disk Image" as shown below.
- The above step opens a new window to select the type of acquisition.
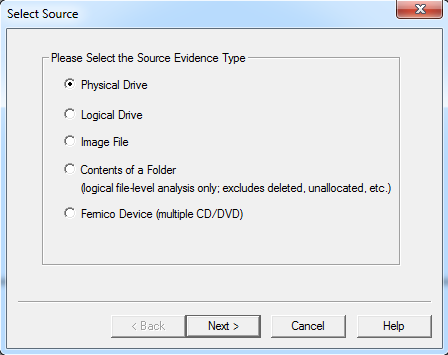
- Since we are trying to create an image of the complete SD card, I have chosen "Physical Drive". It opens a new window to select the Physical Drive as shown below.
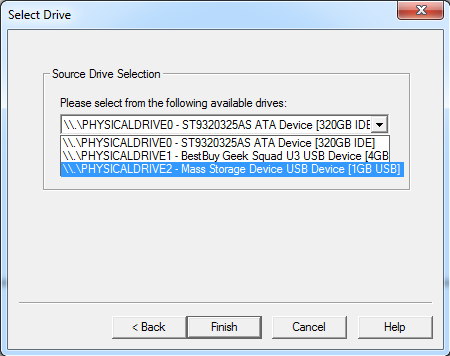
- I have chosen "PHYSICALDRIVE 2" of 1GB which in our case is the SD card. After selecting the appropriate option, click finish. It displays another window where we can add the destination as well as type of image to be created.
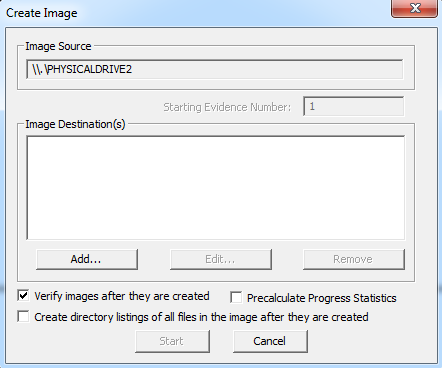
- Upon clicking "Add" button, it opens a new window to select the destination image type.
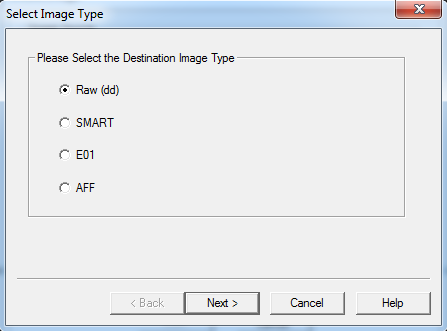
- In our case, we choose "Raw" which gives a "dd" image. Unlike other image formats like "E01", "dd" image will not store its metadata in the image. Upon clicking next, it shows another window where FTK Imager requests for Evidence Item Information. We can fill in the appropriate details and click "next" or skip it if we are doing it as a trail.
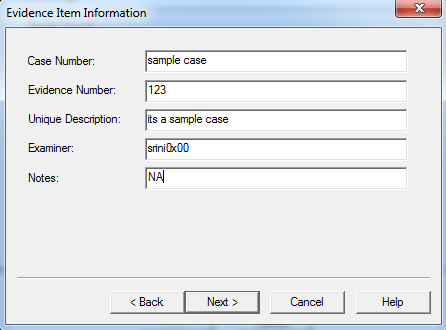
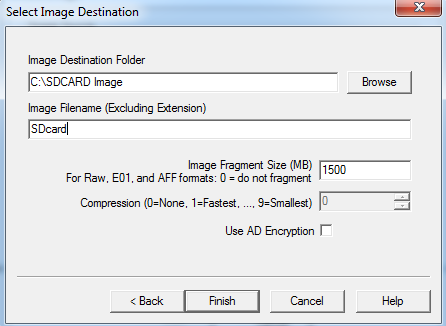
- As we can see in the above figure, we have provided the destination path and name of the output file. Finally, click finish to start imaging.
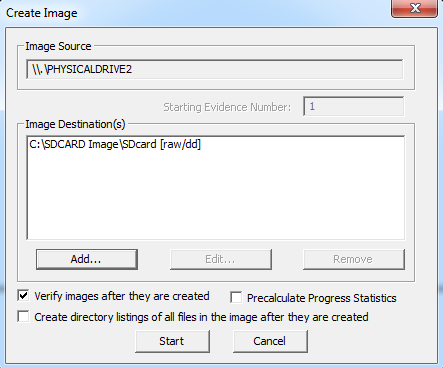
- Click "start" to begin the process.
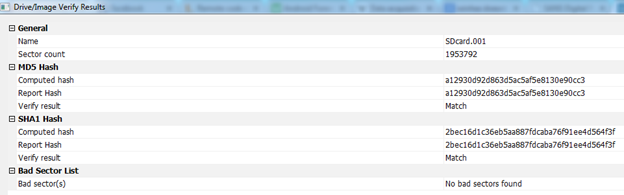
- After finishing the process, FTK Imager displays a new window where it shows hash verification results. This is shown in the figure below
Now, the created image can be further analyzed using traditional forensic analysis tools.
Imaging android file system
In this section, we will see how to perform data acquisition of Android file system partitions.
Note: in order to follow the below process, the device must be rooted.
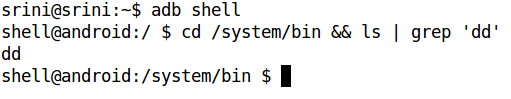
We will use the popular "dd" tool to do our job. "dd" is present in Android by default in "/system/bin" location. This is shown in the following figure.
Now, let's look at the partition locations of our interest using the mount command.
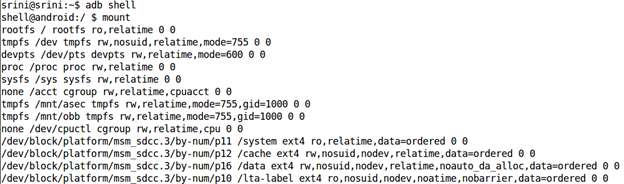
Following is the entry associated with "/data" partition from the above output.
/dev/block/platform/msm_sdcc.3/by-num/p16 /data ext4 rw,nosuid,nodev,relatime,noauto_da_alloc,data=ordered 0 0
So, let's use the following command to extract this particular partition using "dd".
dd if=/dev/block/platform/msm_sdcc.3/by-num/p16 of=/mnt/sdcard/output.img
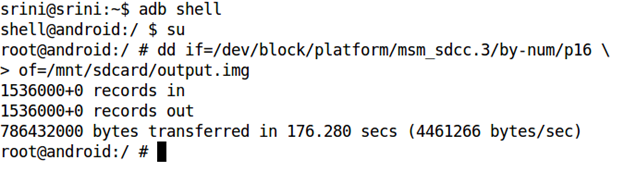
The above command is explained below.
if = input file
of = output file to be created
output.img = name of the output image to be created.
We can even specify the block size using the option "bs" in dd.
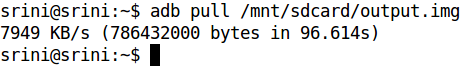
After finishing the above process, we can pull this file out using tools like Droid Explorer. We can even do it using the adb pull command.
The below screenshot shows the command to pull the image onto our workstation using the adb pull command.
Now, we can use this image to do our further analysis on the device.










