Forensics investigation of document exfiltration involving spear phishing: The M57 Jean case
Humans are often the weakest link in the security chain. In his book The Art of Deception, renowned hacker Kevin Mitnick explains how innate human tendencies are exploited to the attacker's advantage. It is a misconception that hackers seek to exploit convoluted vulnerabilities beyond comprehension of nontechnical employees. In fact, a meticulous hacker would begin by locating the simplest vulnerabilities. In this case study, we are presented with a similar situation.
"UPDATE March 31, 2015: This paper has been modified in consent with Dr. Simson Garfinkel since the M-57 Jean case is actively being used in digital forensics classes at institutions around the world. The actual solution to the case has now been replaced with hints and clues. The knowledge provided here is meant to aid your analysis of the case." –Pranshu Bajpai
Scenario: A document is leaked on the Internet which contains confidential information about M57's employees such as SSN, salaries and positions in the company. This sensitive Excel sheet has mysteriously appeared on a competitor's website. Jean, the CFO, is believed to be involved since she had access to this file. She claims that the president, Alison Smith, asked explicitly for this information. However, Alison denies having asked for it or having received it.
Role: Computer Forensics Investigator
Purpose: You are required to investigate the claims and determine how the documents ended up on the competitor's website.
Evidence Disk: You can obtain the EnCase image of the M57-Jean case here: part1 and part2 [Courtesy: Digital Corpora].
Tools that can be used: You can download Paraben's Email Examiner here.
Tasks performed: During the course of this investigation, you will be required to perform the following tasks:
- Mount evidence image and locate 'files-of-interest' pertaining to the case
- Extract information from these files
- Study emails and relevant details to hunt for discrepancies
- Perform document metadata analysis
- Create a timeline of critical events that lead to the leak
- Build a context to aid proceedings in the court of law
Delineating email headers
Before we go ahead, it would be prudent to discuss the importance of email headers in cases like this. Since the case discusses document exfiltration via email, knowledge of email headers might come in handy during analysis. Email headers store plenty of information relevant to a specific email message. Usually, these are hidden and only the 'text' (body) of the email is shown to the recipient. Recipients do however have the option of explicitly viewing the header of any email in many local and web-based email clients.
Firstly, and this is important, email headers are not always veracious and can be easily forged. Accordingly, the only part of an email header you can trust is the part generated by your service, that is, the 'Received' part. Now that you know what can and cannot be trusted about an email header, let us understand the various parts of it.
- Delivery-Date: The date on which your email client or service received the email.
- Message-ID: This is a unique identifier attached to this message when it was created.
- Content-Type: This will specify the formatting of the message which could be plaintext or HTML.
- X-Spam-Status and X-Spam-Level: These are used to specify a spam score for this message.
- Return-Path: After receiving an email, when you click 'Reply To' to send your reply, this is the address that your reply will be sent to.
- Received: Reading these lines from bottom to top will tell you the servers that the message traveled through while it was in transit.
- Priority: This is used to assign a priority to the message and is often abused by spammers to mark their spam as "urgent".
We have avoided self-explanatory parts of the header such as 'From', 'Subject', 'Date', 'To' and 'Body'.
Locating artifacts on the disk that are relevant to the case
You are advised to commence investigation by replicating the image provided to you and then mounting the replica for analysis. The image is in the proprietary EnCase format. You can mount this image using a variety of forensics software including 'Autopsy' which is a GUI front-end for the Sleuth kit tools [Figure 1].
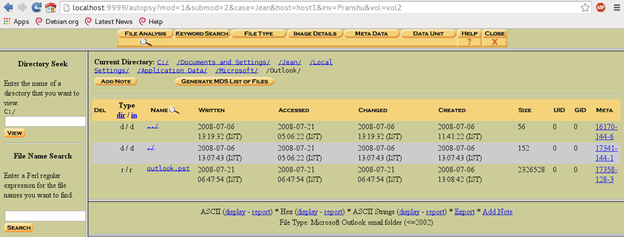
Figure 1
If you lack access to forensics software capable of mounting this EnCase image format, it is suggested that you convert these images to a more general 'dd' format [Figure 2]. You can do so using the procedure described in one of our previous papers.
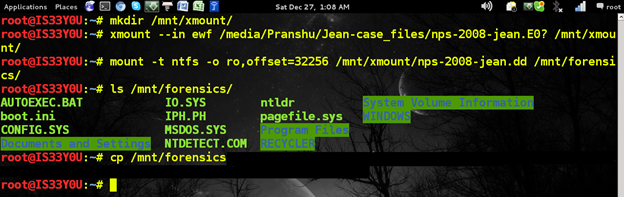
Figure 2
As evident from the scenario, this case revolves around a bunch of emails that were sent to and from Jean's computer. During your preliminary analysis of the disk, try to determine "the way" in which Jean accessed her emails. How did she access email on her computer? After you have an answer to that, try gaining further knowledge relevant to the functioning of the particular software/method in question. Is there a way you could locate a copy of the emails on the disk? Or, are the emails accessible only on the web using the browser?
Analysis of the case on a Linux box
Your choice of Operating System would not affect your analysis of the case. There are a variety of tools that you can use for the purpose of analyzing the artifacts relevant to this case file. On a Linux box, you can use some basic command-line tools for analyzing the artifacts of interest. Simple commands like 'cat' can be used for dumping ASCII content of interesting files that you may want to read.
If you discover more than a few messages, then it is better to avoid searching through the mail without a proper tool. In such as case, it would be better to use a GUI email forensics tool that can facilitate quicker analysis with ease.
Analysis of the case on a Windows box
There are several tools available that allow you to view the messages relevant to the case in Windows. For the purposes of this case, you are free to use any of these. We are using Paraben's Email Examiner which has a GUI and is capable of loading the messages just as you would see them in any other popular email client [Figure 3]. It also has the option of recovering deleted emails.
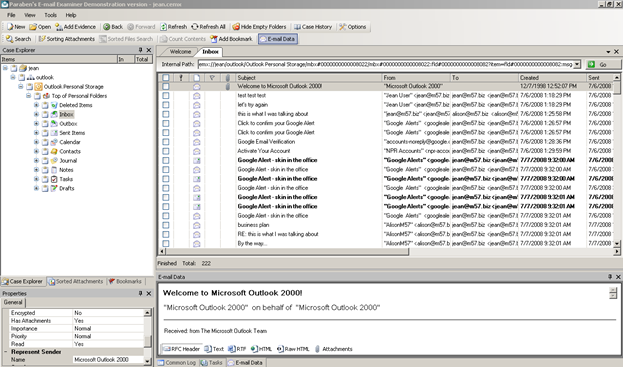
Figure 3
The first few mails are from Jean testing that the email client is properly set up. Next, there are several 'Google Alert' mails. It is for you to determine whether any of these hold relevance to the investigation. It seems that the president, Alison Smith, had her email configured to the name of 'Alison57', as evident from the emails received from her on 07/07/2008. You should ask yourself whether it is possible that Alison's email was "hacked", or did Alison author all of the emails. Furthermore, on 07/07/2008, in her second email to Jean, Alison explicitly asked Jean not to forward spam links to her. Is that relevant to the case in any way? Could that aid our analysis?
Document analysis
Consider asking yourself whether there are any documents of interest on Jean's computer and whether there could be some secret information hidden inside any of them. Are some documents not what they seem to be? Try answering all of these questions as you progress through the analysis.
Is there some way you could analyze 'who' created the documents, 'when' were the documents in question last accessed or modified, and by 'whom'? During analysis, do you feel that the documents would require some steganalysis, or would that be a futile exercise?
Timeline of significant events relevant to the leak
Based on your analysis, you could then construct a timeline of significant events surrounding the document exfiltration, which would help in comprehending exactly how the information leaked out. For example, as you progress through the analysis, consider adding information to the table given below:
Document exfiltration cause analysis
So how did the file end up on the competitor's website? Is it possible to trace the exact steps that the attacker took to leak information from the company? Could you determine the attacker's identity? Could the attacker be a disgruntled former employee or a job candidate turned down by M57? Or, is the attacker presently working for the company? Who has motive to hurt M57?
Conclusion
This case underscores the gravity of security training and awareness for employees within a company. It is unclear whether M57 took measures to educate employees about security attacks and security practices in general. To a trained eye, there were several clues during the attack—whether the attack was internal or external is for you to determine—that suggested malice. However, they might have been overlooked by company personnel involved simply due to lack of security awareness training.
This paper was written for the purpose of providing clues on how to approach the investigation. While formulating your report at the end of the investigation, you would want to avoid adding unsubstantiated conclusions or offering personal opinions about the character of personnel involved. For instance, intuition may tell you that certain employee(s) might be innocent or innocuous. However, you would avoid stating that in the report if you lack evidence to exculpate such personnel. Moreover, giving opinions about the case is the job of expert witnesses. You, as a forensics investigator, should simply investigate and present facts of the case that are backed by evidence.
Note: Please be advised that not all of the suggested questions would aid in your analysis of the case. Some are inserted to mislead you, and you should not take every question at face value. Instead, you are requested to critically reflect over the case and answer only the relevant questions. Here's one clue for you: the attack was unsophisticated, and the leak could have been easily averted.
Sources
- Bill Nelson, Amelia Phillips, and Christopher Steuart. Email Investigations. In "Guide to Computer Forensics and Investigations", Cengage Learning, 2009.
- Crocker, D., "STANDARD FOR THE FORMAT OF ARPA INTERNET TEXT MESSAGES", STD 11, RFC 822, August 1982.
- Spearphishing a new weapon in cyber terrorism










