Computer Forensics: Forensic Science
Forensic Science: Definition
Forensic science is defined as “the application of science to the investigation and prosecution of crimes, or just the settlement of conflicts” (Casey 2004).
It has also been described as “the use of science and technology to scrutinize and establish facts in a civil or criminal justice system” (Hankins & Jigang 2009).
In recent years, forensic science has gained tremendous popularity because of mainstream media entertainment. Many television channels broadcast shows involving popular crime investigations and forensic science, resulting in a massive interest in the field of forensic science throughout the world. As forensic science assists in the detection and deterrence of crimes, it has paramount importance in civil and criminal justice systems.
Fundamental Principles of Forensic Science
Securing the crime scene is very important in forensic science. Investigators secure a crime scene to preserve the evidence and to keep the information about the offense confidential because revealing the information could jeopardize the investigation process. To secure the crime scene, they use barrier tape to prevent passers-by from accidentally entering the crime scene and they ask law enforcement agents to prevent bystanders from entering the crime scene or taking videos and photos with mobile devices or with any other digital device. In many cases, a computer is involved in the crime scene. The computer can itself be a crime scene, within a crime scene, or a secondary crime scene, having evidence to be examined. The computer could also involve physical evidence, such fingerprints on the keyboard and mouse or DNA evidence.
The Philosophy of Science in Forensics
The philosophy of science embodies assumptions made by scientists. Also, it includes the principle claims made by them and how these principles can be verified. The four principle claims made by scientists are:
- Rationality: This approach helps scientists to form evidence based on good reasons, rather than on emotions.
- Truth: This is the fundamental element in any theory or fact-finding. The scientists must produce facts with truthfulness.
- Objectivity: Scientists develop knowledge that must be free from their beliefs, biases, prejudices, and desires.
- Realism: This is the belief that reality is universal and is dependent on what people touch, taste, hears, see, and feel.
Along with these four principles, there are also two other fundamental practices, namely, “verification and falsifiability,” which are essential in forensic science.
Verification means that the facts presented by scientists can be demonstrated to be genuine and scientific. On the other hand, falsifiability means that a particular scientific finding or statement so can be tested to determine whether it is true or false.
How Does the Scientific Method Relate to Computer Forensics?
Science is the process of investigation applying reasoning, using numerous observations, and carrying out experimentation. Science has paramount importance in forensic science. Answering fundamental investigative questions, such as when, what, who, how, why, is strongly related to the scientific method.
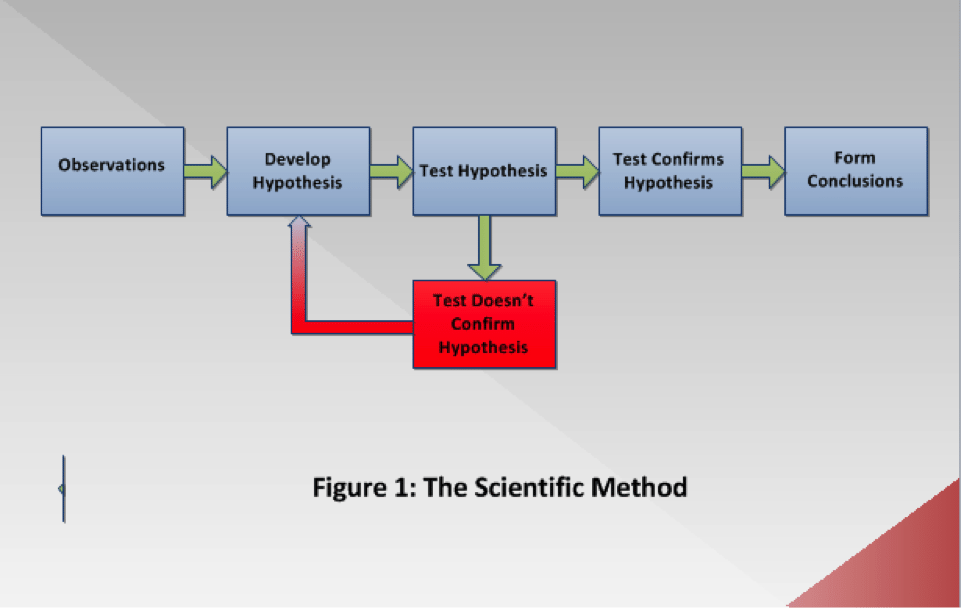
The scientific method involves some stages as illustrated in Figure 1 below.
Observations: The first stage, typically known in computer forensics as the examination phase, involves information gathering through making observations of the evidence. In this phase, the forensic scientists verify the authenticity and integrity of proof. They also perform data carving (a forensic technique of reassembling files from raw data fragments when no file system metadata is available), and keyword searching, among other activities.
Develop Hypothesis: In this second phase, the forensic professionals develop one or more hypotheses based on the observations that they have made in the first phase. When forming a hypothesis, the forensic practitioners try to determine what incident happened, when it happened, where it happened, why it happened, and how it happened.
Test Hypothesis: This phase involves the test of the hypothesis that has been developed.
Test Confirms Hypothesis: The result must be verified to prove or disprove the hypothesis. The case cannot be established unless the hypothesis is varied. This is a cyclic process and, therefore, requires the forensic scientists to repeat it unless the hypothesis is verified, as shown in Figure 1.
Form Conclusions: Once the test is verified, the forensic practitioners can form the correct conclusion based on the verified test.
Computer forensics examinations differ from one another based on the data being investigated, the objectives of the examination, and the resources available. However, when the scientific method is applied to a computer forensics investigation, the underlying fundamental process remains the same.
The Principle of Reproducibility: This is a basic principle of the scientific method whereby another forensic expert following precisely the same steps should form the same conclusion.
Locard’s Exchange Principle
Dr. Edmond Locard was the director of the world’s first forensic laboratory in France. He presented Locard’s Exchange Principle, also known as Locard’s Principle of Transference, in the early 20th century for the purpose of collecting the trace evidence. Locard firmly believed that no matter what a criminal does or where a criminal goes, he/she will certainly leave trace evidence at the crime scene. In fact, whenever two or more people come into contact with one another, a physical transfer takes place. Skin, hair, pollen, clothing fiber, glass fragments, makeup, debris from clothing, or any other material can be transferred from one person to another. This material helps the forensic examiners to collect the trace evidence.
The applicability of Locard’s Principle of Transference in computer forensics applies to cybercrimes involving computer networks, such as identity thefts and electronic bank frauds. To understand how Locard’s Exchange Principle applies to computer forensics, consider what happens when a computer is connected to a particular network. To establish an internet connection, the computer must have a network interface card (NIC). Once the connection is successfully established, the NIC transmits its MAC address to a relevant DHCP server. After that, the DHCP server logs record this MAC address and assign an IP address to the computer, which would receive and store this IP address. Noticeably, the interaction between computer and DHCP server causes the exchange of information, such as MAC and IP addresses, between both devices. This interaction can help the forensic experts to determine the specified date and time of the day when this interaction took place.
The Inman-Rudin Paradigm
Locard’s Exchange Principle set the stage for various other forensic scientists to develop new ways of investigating and analyzing evidence. Later on, the Inman-Rudin Paradigm was designed by Keith Inman and Norah Rudin. This paradigm, in fact, expanded the Locard’s Exchange Principle into two principles and four processes that were applicable not only in physical forensics but also in computer forensics.
The principles are:
- Transfer: The transfer, in fact, is Locard’s Exchange Principle, the exchange of material between two persons.
- The divisibility of matter: This represents the ability to impute the characteristics to the whole of something from a separate piece of it.
Four processes:
- Identification defines the physico-chemical nature of the evidence; for example, the number of heads, cylinders, and sectors of the hard drive.
- Classification/Individualization—Classification attempts to determine the source, whereas the individualization employs some characteristics to uniquely identify a specimen. For example, a security camera captured the crime scene and showed an unidentified perpetrator who killed the victim. On the other hand, the image was clear enough to recognize his gun. The investigators examined the bullet recovered from the victim corpse and found the gun manufacturer, based on bullet’s composition, size, and weight. In fact, these are all class characteristics.
When the perpetrator was arrested, the weapon recovered from him was the same as the weapon identified in the examination. Consequently, it was proved that the bullet had a common origin and, therefore was “class evidence.” This is a process of identification that provides the “individual evidence.”
Classification/individualization can be applied to digital evidence. For example, the structure and location of data on storage media can determine the file system and partition type.
Computer Forensics Boot Camp
If you are aspiring to CCFE or CMFE certification, InfoSec Institute offers you an Authorized Computer Forensics Boot Camp Course that teaches you the necessary skills to investigate computer crimes and computer threats.
Moreover, InfoSec Institute has been one of the most awarded (42 industry awards) and trusted information security training vendors for 17 years.
InfoSec also offers thousands of articles on all manner of security topics.