Security Awareness & Training Resource Center
Featured content

Deconstructing Human-Element Breaches | Infosec HRM
Human risk management isn’t just rebranded SA&T — it’s a profound change of mindset, strategy, process and technology that approaches human-related breaches in a new way.
![Inside an Infosec Boot Camp: All your questions, answered! [replay]](/globalassets/is-wb-24-05-inside-an-infosec-boot-camp_thumbnail2.webp?width=338&height=304&rmode=Max&bgcolor=transparent)
Inside an Infosec Boot Camp: All your questions, answered!
You need to get certified, but is an Infosec Boot Camp the right choice for you — or your team? Find out in this live Q&A with two Infosec instructors.

Emerging trend checklist: Which certifications cover which new skills?
Boost your team's cybersecurity skills with the right certifications. Discover the most in-demand skills and the certifications that cover them in our free guide.

Security Awareness Outcomes with Infosec IQ
See security awareness and training outcomes from more than five million Infosec IQ learners.
Our resources

IBM Rational Appscan: Part 2

New Linux Distro for Mobile Security, Malware Analysis, and Forensics
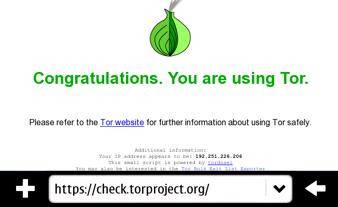
Achieving Anonymity with Tor Part 2: Proxies and DNS servers

Interview with Project Leader Sebastian Poeplau

The Evolution of a Technical Information Security Professional

Introduction to HTTP Response Headers for Security

Risk Management in Agile

Achieving Anonymity with Tor Part 1

Reversing Malware Loaders - The Matsnu-A Case

Defcon 20 Day 3 Review

A Review of the eSoft InstaGate UTM Appliance

IBM Rational Appscan Part 1
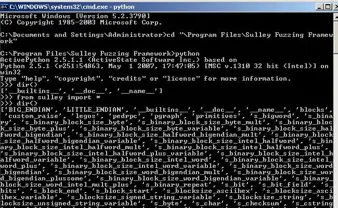
Sulley Fuzzing Framework Intro

Chapter 10 - Virtualization Security

Defending the Internet with Project Meshnet

WebDAV Application DLL Hijacking Exploitation

Social Engineering 2—What Do We Have To Watch?

Social Engineering - We Start Playing

Intrusion Prevention System: First Line of Defense
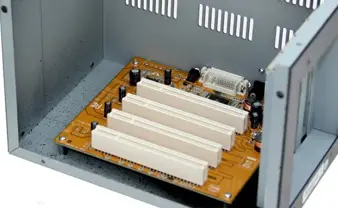
Malicious code execution in PCI expansion ROM

Reconnaissance with Images
Chapter 9: Securing remote access

Complete file upload vulnerabilities

Simple router pawning techniques - Getting the administrative privileges