Defending the Internet with Project Meshnet
Introduction
Topics related to Internet censorship have been debated frequently in the last few years. The main purpose of most Internet censorship actions is to deny access to certain information on the web. This information can be censored throughout the world, or in some cases, can be limited to certain countries. Some countries even have their own censorship policies. One of the many examples of such an act is the very famous SOPA (Stop Online Piracy Act), which had provisions to protect the publication of copyrighted material and intellectual property on the Internet. There are numerous ways to censor information on the Internet, including IP address blocking, DNS Filtering, URL Filtering etc.

What should you learn next?

What should you learn next?
In the past, concerns have been raised over whether Internet censorship is the answer to defend against scenarios that could generate online piracy. This issue has become so prominent because popular sites like Google and Facebook allows users to share information without bearing responsibility for the content posted. These websites do have facilities where copyright holders can file a complaint, and the content will be removed. However, Internet censorship makes it possible to block the entire website for the users, not just a single page or profile. An act which has enough power to take down entire websites like Facebook and Twitter could be used to suppress technology and threaten a free unified and open Internet.
Project Meshnet
Project Meshnet (originally called the Darknet) was born out of concerns over censorship and is aimed at setting up an open, decentralized, and censorship free Internet. The project started with a discussion on reddit, the text of which can be access here. The name Project Meshnet derived from the use of mesh networking topology, which demands that every node must not only capture and disseminate its own data, but also serve as a relay for other nodes in the same network. This architecture makes mesh topology completely decentralized, (i.e. without any centralized authority) thus making it impossible to censor any form of data.
Project Meshnet is still in its alpha stages and is available for testing purposes to its users. The future aim of the project is to use a combination of hardware (called mesh islands) and software (called CJDNS) to set up a decentralized Internet. CJDNS is a routing engine which helps us communicate over the mesh network. Right now, the communication happens over the current Internet infrastructure over a network called Hyberboria. The future aim of the project is to set up its own hardware across the globe through which the communication will take place.
How Does it Work?
The Meshnet network is built on an infrastructure of users. The future aim of the project is to have multiple computers connected to each other through a wireless connection over a virtual network interface. All the information will be encrypted, meaning that only the user at the destination will be able to see the actual data. Packets will be directed from the source to the destination through an intermediate set of nodes until it reaches its final destination. The flow of packets is explained in the wiki section of Project Meshnet's website. An excerpt from the wiki article is below:
"In the CJDNS net, a packet goes to a router and the router labels the packet with directions to a router which will be able to best handle it. That is, a router which is near by in physical space and has an address which is numerically close to the destination address of the packet. The directions which are added to the packet allow it to go through a number of routers without much handling, they just read the label and bounce the packet wherever the next bits in the label tell them to. Routers have a responsibility to 'keep in touch' with other routers that are numerically close to their address and also routers which are physically close to them."
Setting up CJDNS
First and foremost when setting up Project Meshnet is that a participant must set up the CJDNS routing engine on his or her system. In this article we will be looking at how to set up Meshnet on a Mac OS X operating system. Unfortunately, CJDNS only works with Mac OS X 10.7 or newer.
First of all, it is important to make sure that you have all the dependencies installed, which includes git and wget. Downloading the "Command Line Tools for Xcode" from the apple website would also be helpful in the overall process.
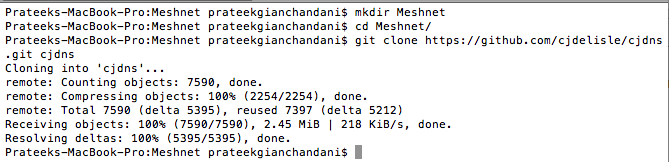
First, lets clone the latest from CJDNS's github repository.
Then, go to the CJDNS directory and build using the "./do" command as shown in the figure below. You will be required to have some dependencies like wget, etc. installed on your system in order to conduct a proper build. Otherwise, the build would fail.
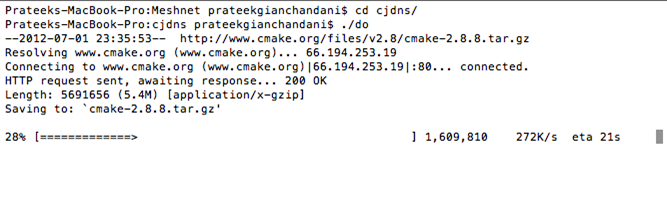
The build would take some time, so please be patient.
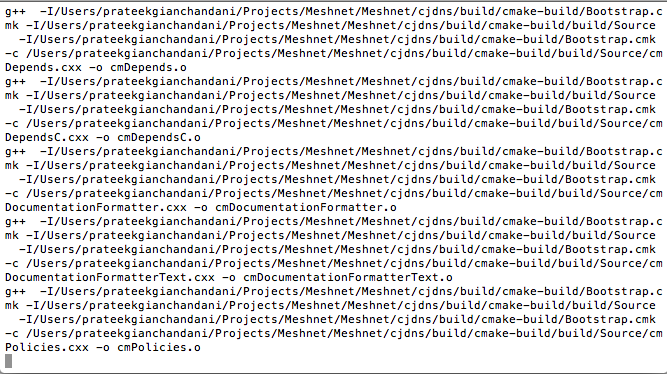
Here's how your CJDNS should look during building phase. Also, please note that you must have an Internet connection during this whole process.
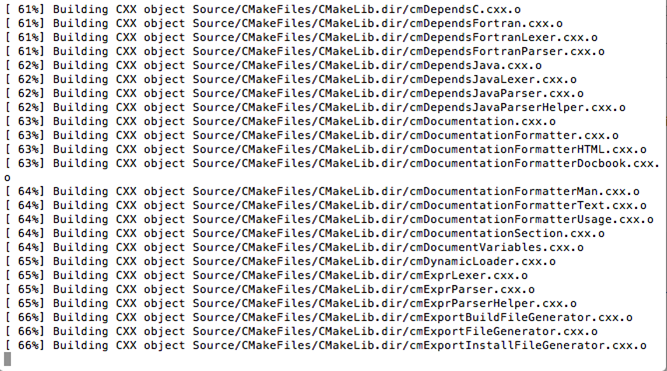
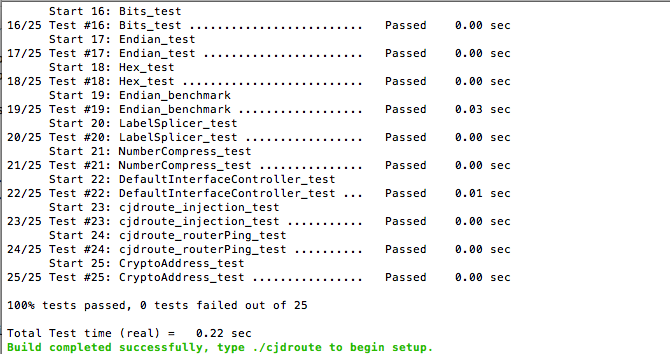
Once the build is complete, you will get a message stating "Build completed successfully" as shown in the figure below. If you don't see this message, then something is wrong and the build wasn't successful.
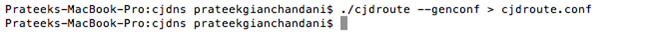
Now we need to create a config file that will provide us with a public key, a private key, and an IP address for our node. Run the command as shown in the figure below.
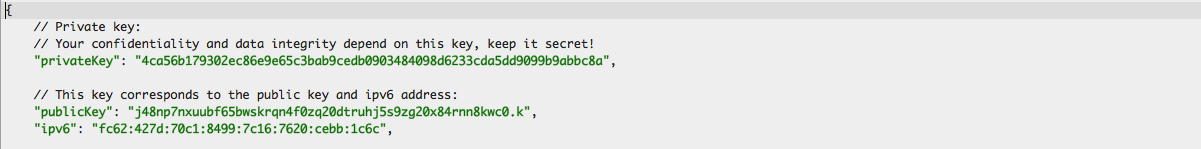
This will create the config file named cjdroute.conf. If you open the file, you will see that we have been assigned a private key, a public key, and an IPv6 address. Yes, Meshnet runs by tunneling IPv6 packets in UDP/IPv4 packets. This is because CJDNS and Hyperboria are still in the early stages of development.
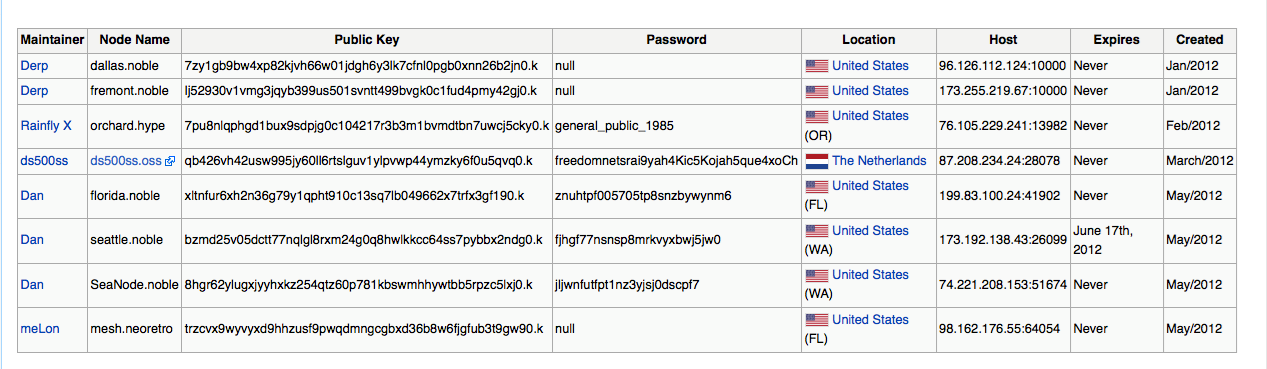
Right now, since Meshnet doesn't have a large user-base from around the world, the Meshnet team has made some public peers available globally for users to connect to. The figure below shows a snapshot from the page http://wiki.projectmeshnet.org/Public_peers , which displays all the public peers available to connect to.
It's always good to check if these servers can be reached by pinging them before trying to connect to them using Meshnet. For example, in the figure below I am pinging a server in the United States to see if it is reachable.
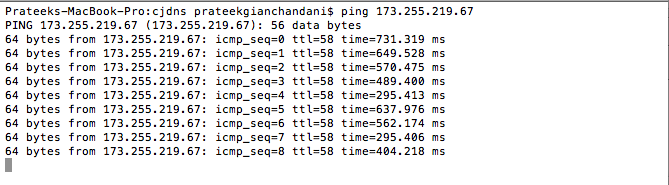
Next, we need to configure the config file in order to connect to that peer. If you open your config file, you will see the following section.
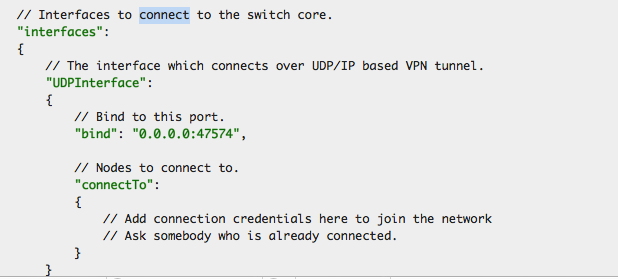
In this file, we need to provide information on the peer that we will be connecting . As you can see from the figure below, I have adjusted the config file to connect to two peers. We can connect to a maximum of three peers at once. We can also add some more options such as "Trust" and "Auth Type". The trust level signifies how much you trust a peer that you are connecting to. It is advisable to assign a higher trust value for those nodes which you have already been connected with in the past. The trust feature has not been implemented in Meshnet yet.
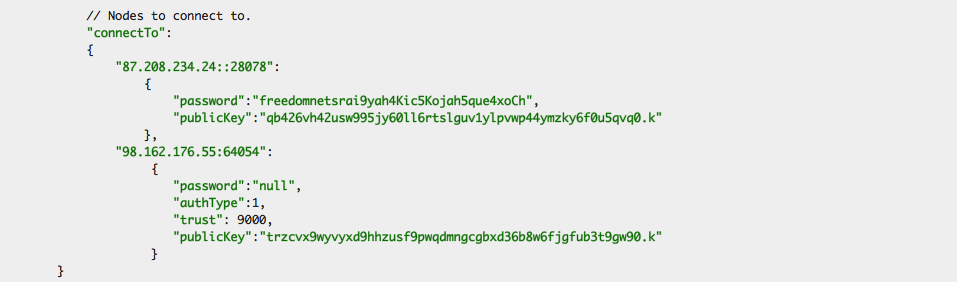
Once you are done with setting up the configuration, start up CJDNS by typing the command as shown in the figure below. You will need admin privileges to run the daemon.
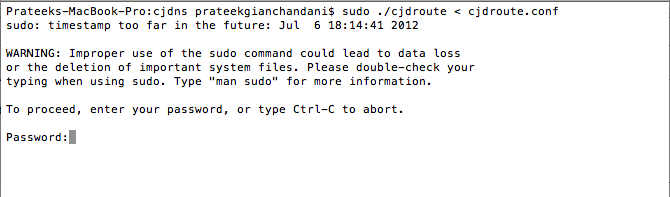
Once you have provided your password, CJDNS will run and you will see the log messages as shown below.
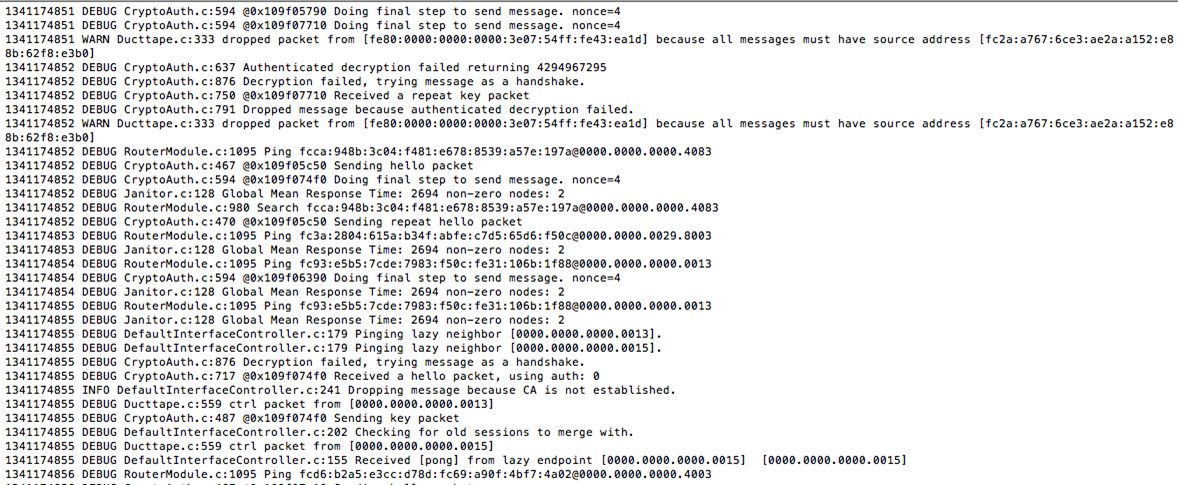
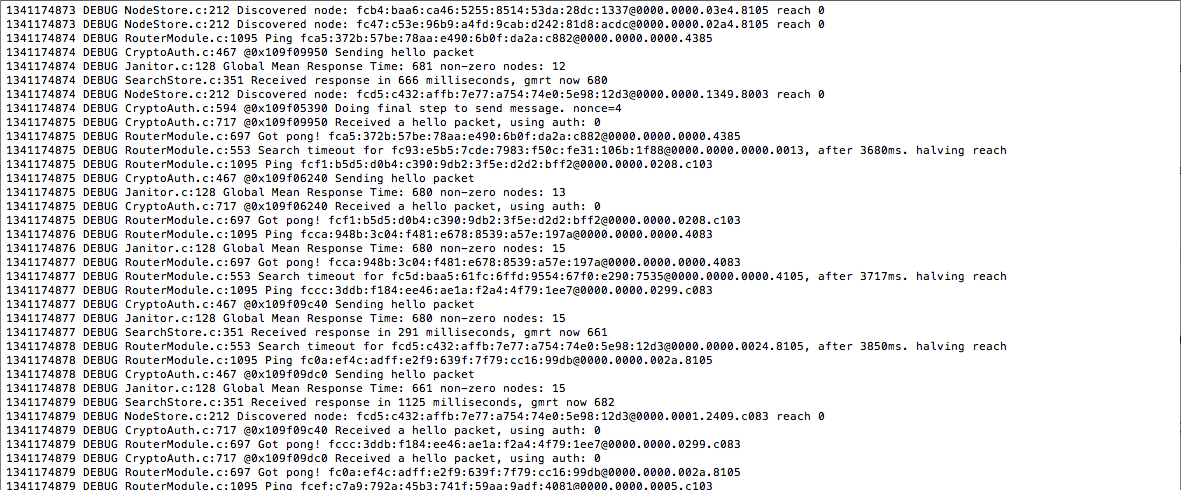
CJDNS is now running properly and communicating with other peers. If you perform a quick "ifconfig" on your system, you will see that a new interface by the name "utun0" has been created. This is the interface used by Meshnet to communicate with the other peers in Hyperboria.
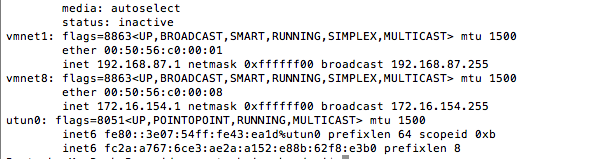
Conclusion
The aim of Project Meshnet is to build a decentralized Internet. This will enable users to exchange information easily without a central authority like an ISP, which can block or filter traffic. In this article we reviewed how to set up Meshnet on our local system, and how to use the network Hyperboria to initiate connections between some publicly available peers.
Help Project Meshnet
The creators of Project Meshnet are always looking for individuals to assist in technical and non-technical fields. Go to Project Meshnet to find out more.
References:
- Project Meshnet https://projectmeshnet.org/
- MeshWiki https://wiki.projectmeshnet.org/Main_Page
- Mesh Networking http://en.wikipedia.org/wiki/Mesh_networking










