A Review of the eSoft InstaGate UTM Appliance
It can take an organization several years to build out an information security infrastructure capable of providing them with sufficient protection. This is especially true of small to medium sized companies, who usually have to work within tighter financial constraints, and all too often are reluctant to add additional burden to an already stretched IT department (or IT person).
And it's not just a case of "fire and forget" either, the deployment is just the start. Someone then has to go around and tweak the infrastructure on a regular basis. Nurturing it to maturity to ensure that it continues to provide protection as threats, the network and the requirements of the business evolve. Of course, anyone who has ever worked in information security will know that these things evolve on an hourly basis.

FREE role-guided training plans

FREE role-guided training plans
Another reason smaller organizations struggle when it comes to security infrastructure is that to the uninitiated, it's an absolute minefield out there! Firewalls, email security gateways, web proxies, data loss prevention systems, intrusion prevention systems, web application firewalls – which do I need? Do I need them all? What's the difference between X and Y?
A minefield it may be, but it's a place more and more organizations are quite rightly finding themselves having to tip toe through. This is often driven by compliance requirements; but more and more frequently it's simply down to the fact businesses are waking up and realizing that data and reputation, although intangible, are incredibly valuable assets.
With that in mind, I'm happy to report that with their latest InstaGate UTM appliances, eSoft have made it ridiculously easy to go from having zero protection to a multifaceted security infrastructure in very little time at all.
The Basics
You can choose to go for a hardware appliance, three different models provide increasing levels of throughput depending on your needs, or you can run your InstaGate as a virtual machine for instant scalability.

InstaGate is modular, meaning that you can pick and choose which security features you need and easily add them to your appliance. These software modules are known as "ThreatPaks". As needs change, which they will, additional ThreatPaks can be dropped onto the platform on the fly. No need to add infrastructure, or make any complex changes.
Regardless of the form factor, with the addition of the Internet Failover ThreatPak InstaGate supports ISP redundancy and will run in a high availability pair. Availability is a very important, but often forgotten element of an information security program.
I took an InstaGate appliance for a spin in my lab, to see firsthand how it performed. I've had the privilege of performing penetration tests for a number of small to medium sized companies, nonprofits and educational establishments. While there are some out there who are really on top of security, the majority were lacking basic controls and were crying out for the type of protection an InstaGate provides. With that in mind, I wanted to see specifically how easy it would be for one of these organizations to deploy, manage and benefit from an InstaGate.
Initial Setup
All set up is performed via a web GUI (this was subjected to a wide variety of browsers without issue). There are six steps to complete, the most complex being the configuration of the network interfaces. The remainder is the usual license agreement and registration information.
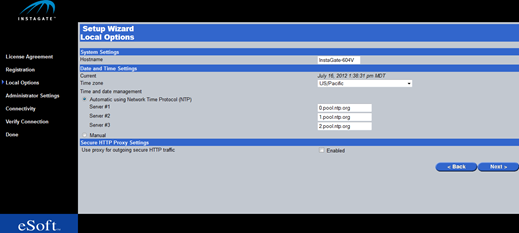
Once the basics are taken care of, we find ourselves at the main management GUI where we have full control over the appliance. Now as I've previously mentioned, the InstaGate's feature list can be expanded with the addition of extra ThreatPaks. On my appliance I had the Web and Email Total Security ThreatPaks installed; two of the most likely to be used by small businesses. The feature list provided by these ThreatPaks is pretty extensive and I was a bit concerned that having so many configuration options might make the device a little "cluttered", but eSoft have done a good job of keeping the GUI clean and logically organized. I'll level that it's not the prettiest GUI in the world, but I'd rather see the CPU being used to crunch network traffic than process a large amount of graphics for a fancy GUI.
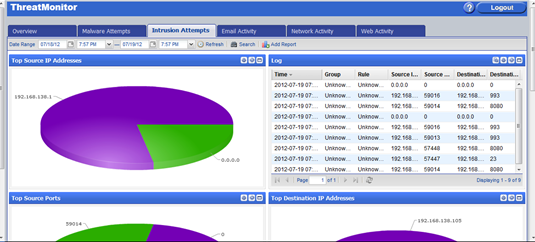
ThreatMonitor
The InstaGate's main dashboard is known as the "ThreatMonitor" and provides an at a glance overview of the happenings on your appliance.
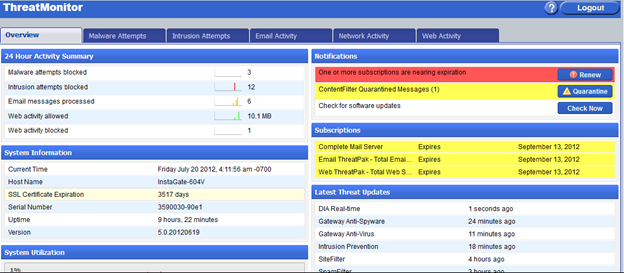
We can see instantly see stats regarding blocked attacks, web browsing and other system messages. Something that grabbed my attention was the notification area in the top right of the screen. System admins will love the fact that you can instantly see if any messages have been caught by the email content filter. Searching through quarantine for a message with someone on the phone screaming at you is always a situation you wish to expedite your way out of.
Firewall and Remote Access
At its core, without any of the additional ThreatPaks enabled, the InstaGate is a Firewall and VPN appliance.
There is nothing overly fancy about adding an access control list entry, you simply work your way through the options on the firewall policy page. Start off by telling the InstaGate what you want the rule to do and which interface it should sit on. Add source, destination and which services it should match. Finally choose the position of the entry in the access list and away you go. Clean, simple and easy to do.
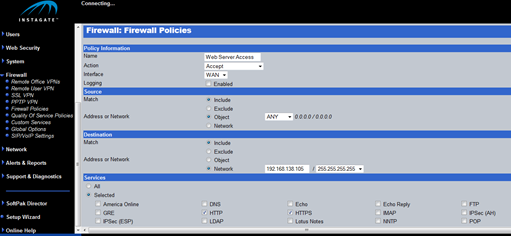
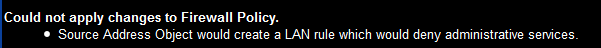
One thing I always like to test for when playing with firewalls is how easy it is to recover from a total screw up. Even the best engineers will have at some point blocked themselves from connecting to the firewall they are managing. In some cases this will require you to visit the device in person to reload it, or request that someone close by applies the "switch it off and on again" logic to revert to a startup configuration. Good news then that the InstaGate is built with human mistakes in mind. I tried to add an ACL entry that would prevent me from managing the device, only to be told that I was being silly.
There are a wide variety of VPN options depending on your requirements. Site-to-site and Remote access via PPTP or SSL. SSL VPN access is becoming an increasing popular feature as more organizations start to work more and more with staff based in remote locations. The InstaGate's SSL VPN offering was a standout feature for me. It took literally 10 seconds to configure. A single click to enable, set the listen IP, a DHCP pool for remote clients and it was done.
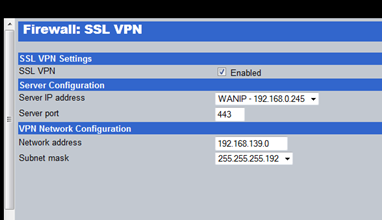
Once the SSL VPN is enabled, all you need to do is provide your user with a URL. They login, and the client configuration is taken care of by eSoft's VPN client.
Intrusion Prevention System
With the addition of either the Email or Web Security ThreatPak you'll get the InstaGate's IPS engine. The IPS will perform deep packet inspection and run the contents of a packet against its signature database. You can choose which signatures you want it to look for, and how the system responds if it finds a match (drop, log or both).
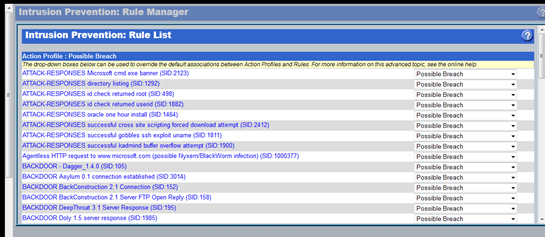
The IPS can be monitored from the main ThreatMonitor page. I placed the InstaGate in front of a couple of servers which were subjected to a selection of network and web based attacks. It stood up quite nicely to everyday automated attacks and probing. However, like anything signature based – if it doesn't have the signature, it can't match it. As I moved onto manual testing methods, I encountered less resistance from the IPS. That said, it will certainly provide a good starting point for an organization looking to acquire their first IPS. There are also options to manually create signatures, and signatures are update via a subscription service every few minutes. The IPS will also deal with any unwanted peer-to-peer file sharing traffic.
Web Filtering
This module is included with the Web Security ThreatPak and does exactly what you'd imagine. The InstaGate will act as a transparent proxy server and block sites based on categorization, or by URL.
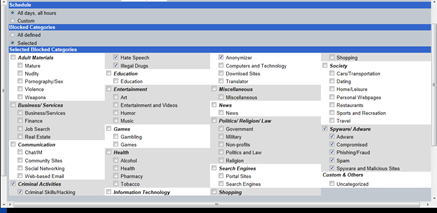
When trying to access a site that is blocked, the user receives a customizable warning page.
It's also possible for an administrator to add URL's to a whitelist, so that they will never be blocked.
The web filtering feature in particular makes the InstaGate a viable candidate for educational establishments.
Email Content Filtering
Email content filtering is included as part of the Total Email Security ThreatPak. With this ThreatPak, the InstaGate will sit in front of your existing email infrastructure and will examine the contents of inbound and/or outbound mail. If there are certain things that you don't want to see leave the organization via email, for example credit card numbers, you can configure the InstaGate to prevent this.
If an email is prevented by the content filter, it is sent to quarantine for review by an administrator. The admin can then chose to release the message or get rid of it forever.
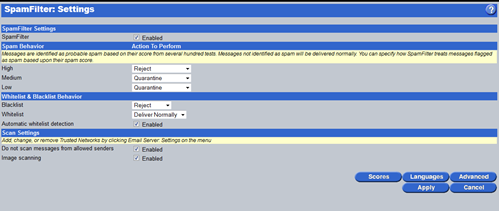
SpamFilter
The Email Security ThreatPak also includes a Spam Filter which uses a couple of different techniques to decide if a message is spam or legit. A Bayesian scoring system analyses the type of messages that are coming into your organization, to generate an initial score which is used as a baseline for future messages. In addition, the Spam Filter also subscribes to a Real Time Blacklist (RBL), which keeps track of IP's around the world that are currently sending spam. If the filter receives a message sourced from an IP on the RBL, it blocks it.
Depending on the score, spam messages are either blocked automatically or sent to quarantine. This is all configurable of course.
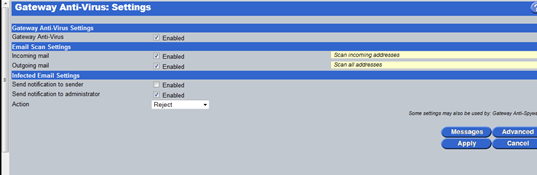
Gateway Anti-Virus and Anti-Spyware
With either of the Email or Web Total Security packages, the InstaGate will run a gateway Anti-Virus and Anti-Spyware engine. This scans email attachments, files transmitted over FTP and files downloaded via HTTP for malware.
The Anti-Spyware engine also blocks DNS requests for domains known to host malicious software.
Distributed Intelligence Architecture
eSoft maintains a network of information sharing that every InstaGate participates in (opt out is possible). This network is known as the distributed intelligence architecture and is designed to allow InstaGates to obtain knowledge of new and emerging threat trends.
Conclusion
There is no one size fits all for organizational security. Different places will have different concerns and different priorities. The modular nature of the eSoft InstaGate makes it a great option for growing organizations who want to step up, and start applying enterprise level security controls.
The ease of the configuration makes it appealing to those who may have never had to work with security tools before, or may not have the time to dedicate their entire work day to security administration.
The speed at which you can get a lot of things working together is impressive, and having everything integrated in one box takes away a lot of moving parts that could otherwise lead to confusion. Obviously, this model isn't suitable for everyone, but with this product eSoft have defined an audience, and have concentrated on building features suitable for that audience.
In my opinion, any tool that makes security more accessible for a wider audience is a very good thing.

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!
eSoft InstaGate does just this, and it does it very well indeed.









