Security Awareness & Training Resource Center
Featured content

Deconstructing Human-Element Breaches | Infosec HRM
Human risk management isn’t just rebranded SA&T — it’s a profound change of mindset, strategy, process and technology that approaches human-related breaches in a new way.
![Inside an Infosec Boot Camp: All your questions, answered! [replay]](/globalassets/is-wb-24-05-inside-an-infosec-boot-camp_thumbnail2.webp?width=338&height=304&rmode=Max&bgcolor=transparent)
Inside an Infosec Boot Camp: All your questions, answered!
You need to get certified, but is an Infosec Boot Camp the right choice for you — or your team? Find out in this live Q&A with two Infosec instructors.

Emerging trend checklist: Which certifications cover which new skills?
Boost your team's cybersecurity skills with the right certifications. Discover the most in-demand skills and the certifications that cover them in our free guide.

Security Awareness Outcomes with Infosec IQ
See security awareness and training outcomes from more than five million Infosec IQ learners.
Our resources

Pentesting for PCI DSS compliance: 6 key requirements

9 free risk management tools for IT & security pros

2017 OWASP A3 Update: Sensitive Data Exposure
Android penetration tools walkthrough series Dex2Jar, JD-GUI, and Baksmali
Android penetration tools walkthrough series: Apktool

Preventing Business Email Compromise (BEC) With Strong Security Policies

2017 OWASP A10 update: Insufficient logging & monitoring

Vulnerability scanning with Metasploit part I

XML vulnerabilities are still attractive targets for attackers

Introduction to the paros proxy lightweight web application tool
Advance persistent threat - Lateral movement detection in Windows infrastructure - Part II
Android penetration tools walkthrough series: MobSF
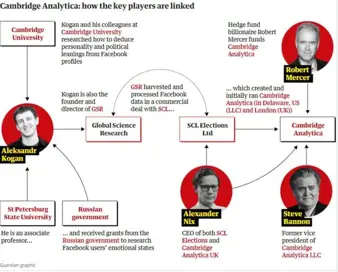
All You Need to Know About the Cambridge Analytica Privacy Scandal

2017 OWASP A9 Update: Using Components With Known Vulnerabilities

Basics of cryptography: The practical application and use of cryptography

Combat Business Email Compromise Scams With New Awareness Training Tools From SecurityIQ

Computer forensics investigation – A case study

2017 OWASP A6 Update: Security Misconfiguration

Reverse engineering tools

Building your own pentesting environment

2017 OWASP A4 Update: XML External Entities (XXE)

How to Prevent Business Email Compromise With Multi-Factor Authentication
Cryptanalysis tools

What is Business Email Compromise (BEC)?