Cryptanalysis tools
Some terms and definitions
- Alice – Sender of the message
- Bob – Receiver
- Eve – Eavesdropper or unintended party
- Plaintext – Message to be sent
- Ciphertext – Coded message
- Encryption – Coding of message
- Decryption – Decoding the message
- Cryptology – Science of study of ciphers
- Cryptography – Science (or art) of encrypted communication between Alice and Bob, such that even if Eve intercepts the ciphertext, she won't be able to make any sense of it.
- Cryptosystem – A term given to the system which turns a plaintext into ciphertext and back.
- Cryptanalysis
Cryptology is divided into – 1) Cryptography and 2) Cryptanalysis. Cryptography deals with the creation of ciphers and cryptosystems. Cryptanalysis deals with the breaking of ciphers and cryptosystems.
Cryptanalysis can be done by various approaches or attacks like brute force, chosen plaintext and man in the middle attack. Web-based cryptanalysis tools are also available that can break the cryptosystems, teach about network security and test the cryptosystems in general.
Some cryptanalysis tools
Brute force attack
As an old technique, brute force means exhausting very possibility until a match is found. Even in classic cryptography, brute force attack is considered time-consuming.
In modern cryptography, the length of a brute force attack depends exponentially on the length of the key. Since modern cryptography uses very long keys, brute force attack is considered inefficient for all practical purposes.
Chosen plaintext attack
The attacker, in this case, inputs a plaintext and observes the output ciphertext obtained. By examining the plaintext – ciphertext pair, he can easily guess the encryption key. The differential analysis done on RSA algorithm is an example of such attack.
Man in the middle attack
In this type of attack, Eve fools both Alice and Bob. Alice, who wants to communicate with Bob, relays her public key Ka. Eve impersonates Bob and sends her public key Ke. Alice transmits her plaintext P alongwithKa&Ke.
Now, Eve has Alice's key as well as the plaintext. She now impersonates Alice and sends her key as Alice's key to Bob. Bob transmits his public key Kb to Eve. To keep Bob from suspecting anything, Eve transmits P along with Kb &Ke to Bob.
Now, Eve has both the public keys of Alice and Bob, as well as the message i.e. the real information she needed.
Web-based cryptanalysis tools
CrypTool
CrypTool was first launched in 1998. It is an e – learning tool explaining cryptanalysis and cryptography. CrypTool aims at making people understand network security threats and working of cryptology. It includes asymmetric ciphers like RSA, elliptic curve cryptography. CrypTool1 (CT1) experiments with different algorithms and runs on Windows. It was developed in C++ language.
CT2, which was launched in 2014, also runs on Windows. It has an improved GUI and more than hundred cryptological functions. It is developed in .NET &C#. JCrypTool (JCT) which followed CT2 is platform independent.
JCT works on Linux, MacOS, and Windows. JCT is both a function – centric as well as a document – centric tool.In 2009, CrypTool – online (CTO) was launched.CTOconsists of a huge number of encryption methods and analysis tools. It is a web browser based tool and also targeted at smartphones.
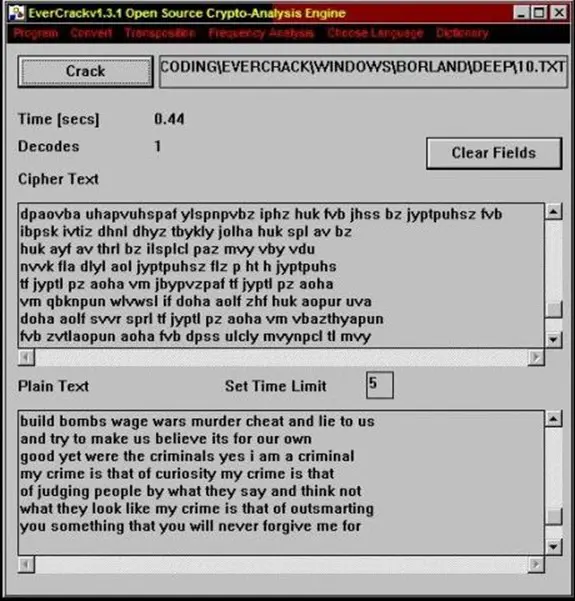
EverCrack
An open source GPL software, EverCrack deals chiefly with mono – alphabetic substitution and transposition ciphers. It is a cryptanalysis engine with a multi – language support for English, German, French, Spanish, Italian, Swedish, Dutch and Portuguese. It was initially developed in C language.It is currently concentrating on online web – based applications. Now, the programming is kernel based i.e. deciphering complex ciphers for the kernel.
The overall design goal is to break down complex ciphers systematically into their simplex components for cryptanalysis (by the kernel). The kernel consists of an algebraic design (comparison and reduction) for breaking unilateral, mono – alphabetic ciphers instantaneously. The computational speed is found to be proportional to O (log n).
An EverCrackGUI looks as shown below.
Cryptol
A software development firm named Galois Inc. developed Cryptol. It is a learning tool as well as a way to analyze algorithms and implementations. Originally designed for NSA, this tool is now used by private firms. The programming language is used for all aspects of developing and using cryptography, such as the design and implementation of new ciphers and the verification of existing cryptographic algorithms.
Cryptol is designed to allow the cryptographer to watch how stream processing functions in the program manipulate the ciphers or encryption algorithms. This aspect of Cryptol has been of particular interest to computer programmers who write new programming languages and to the field of artificial intelligence.
Cryptol deals with cryptographic routines rather than entire cryptographic suites. It was designed for efficiently implementing cryptographic algorithms in hardware circuits. Despite its flaws, the tool can help improve the trustworthiness of many cryptographic algorithms.
AlphaPeeler
AlphaPeeler is a freeware / non-commercial software product for educational and personal use.Its development started in 1997, and AlphaPeeler 1.0 was deployed in June 1998. It includes MD5, SHA – 1, RSA key generation, RIPEMD – 16, etc. Classic ciphers like Playfair are studied here.
AlphaPeeler Professional 1.0 beta was released on 4th July 2001 in public domain. AlphaPeeler was founded with a specific goal of providing the most up-to-date research to assist enterprises, vendors, and carriers to secure their business and development environment.AlphaPeeler development group also creates a wide range of software technology solutions listed in services section such as software development, system analysis and design, documentation and graphic designing.
Crypto Bench
Crypto Bench is a software that performs various cryptanalytic functions. It can generate 14 cryptographic hashes and two checksums. It can encrypt with 29 different secret key or symmetric schemes. It can Encrypt, Decrypt, Sign, and Verify with six different public key or asymmetric schemes.
Ganzúa
Ganzúa (the Spanish word for lockpick) is a cryptanalysis tool for monoalphabetic and polyalphabetic ciphers that can work with almost any set of characters. It is a Java application; it may be executed on Mac OS X, Linux or Windows.
Ganzúa is provided with features to cryptanalyse monoalphabetic and polyalphabetic ciphers. It is Java based, and version 1.01 is available in English and Spanish. In monoalphabetic ciphers, we have alphabet wide substitution tools for Caesar shift cipher. Also, relative frequencies of characters, bigrams and trigrams can be obtained and displayed.
Similarly, for polyalphabetic ciphers, alphabet-wide substitution tools for the Vigenère or Alberti ciphers are available. Relative frequencies for each alphabet is calculated and displayed here as well. Kasiski test is performed on cryptograms.
For both kinds of ciphers, the alphabet used is arbitrary for both plaintext and ciphertext. Indexes of coincidence of cryptograms and languages are calculated. Based on the index of coincidence of the ciphertext and language, the number of alphabets needed to generate a cryptogram is found out. Enforced injective character substitution is carried out. Save and load features are available for ongoing projects.
Elcomsoft Distributed Password Recovery (EPDR)
Elcomsoft Distributed Password Recovery (EPDR) installs "agents" on as many computers as possible. These agents use brute force attack to recover the lost password. EPDR is useful for recovering Office passwords (Office 97/2000/2003/XP) for Word and Excel documents.
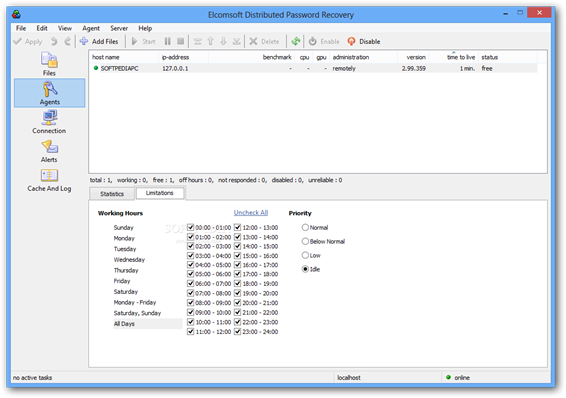
For example, Office 97/2000 compatible documents can be decrypted by recovering encryption keys instead of passwords. EDPR uses computing power of all computes in LAN or WAN. It works for Excel documents encrypted with 40 – bit keys.
Jipher
Cryptanalysis tool that can be used to attack old ciphers. Additional can be used to analyze cookies.
Advanced Archive Password Recovery
Advanced Archive Password Recovery supports the dictionary based attacks, plaintext attacks and the brute – force attacks. It has a multilingual interface and strong AES encryption support. Passwords for .zip, .arj , .rar & .ace extensions can be cracked.
CalcChecksum
CalcChecksum is a simple utility for calculating various checksums easily with a graphical user interface.
Kismet
Kismet is an 802.11b network sniffer and network dissector. It is capable of sniffing using most wireless cards, automatic network IP block detection via UDP, ARP, and DHCP packets, Cisco equipment lists via Cisco Discovery Protocol, weak cryptographic packet logging, and Ethereal and TCP dump compatible packet dump files. It also includes the ability to plot detected networks and estimated network ranges on downloaded maps or user supplied image files.
Lepton's Crack
Lepton's Crack is a generic password cracker. It is easily customizable with a simple plugin system and allows system administrators to review the quality of the passwords being used on their systems. It can perform a dictionary-based (wordlist) attack as well as a brute force (incremental) password scan. It supports standard MD4 hash, standard MD5 hash, NT MD4/Unicode, and Lotus Domino HTTP password (R4) formats.
Audio – entropyd
Audio-entropyd reads sound from a stereo soundcard, takes the difference between the left and right channels and feeds the result (via a secure hash) to the /dev/random entropy pool. This can be useful for machines which require a lot of random data (e.g., IPsec security gateways) to ensure that the kernel entropy pool does not deplete and /dev/random does not block.
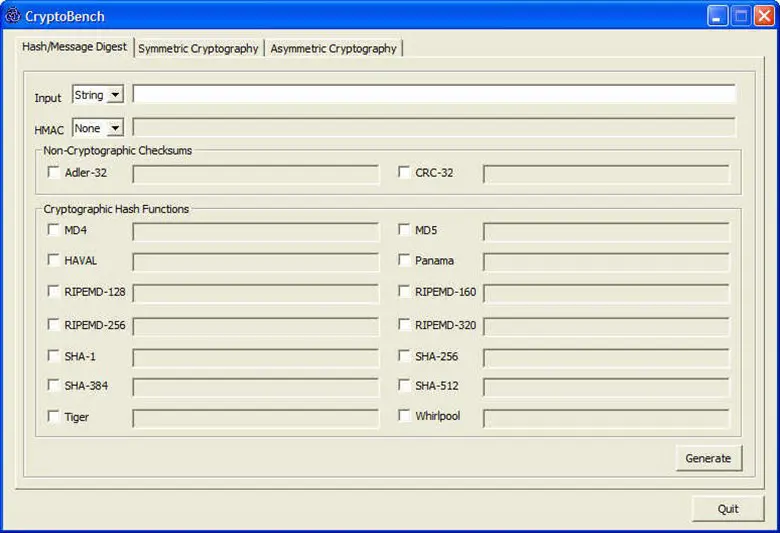
Crypto Bench
Crypto Bench is a software that performs various cryptanalytic functions. It can generate 14 cryptographic hashes and two checksums. It can encrypt with 29 different secret key or symmetric schemes. It can encrypt, decrypt, sign and verify with six different public key or asymmetric schemes.
Some concerns
Cryptosystems need to follow certain rules to be strong. Cryptanalysis works to find the flaws in these systems so that newer and better cryptosystems can be designed. Thus, the scope of both the systems needs to be defined.
Conclusion
Cryptanalysis is a useful tool for testing the cryptosystems. It is also useful to design new and stronger cryptosystems.









