Security Awareness & Training Resource Center
Featured content

Deconstructing Human-Element Breaches | Infosec HRM
Human risk management isn’t just rebranded SA&T — it’s a profound change of mindset, strategy, process and technology that approaches human-related breaches in a new way.
![Inside an Infosec Boot Camp: All your questions, answered! [replay]](/globalassets/is-wb-24-05-inside-an-infosec-boot-camp_thumbnail2.webp?width=338&height=304&rmode=Max&bgcolor=transparent)
Inside an Infosec Boot Camp: All your questions, answered!
You need to get certified, but is an Infosec Boot Camp the right choice for you — or your team? Find out in this live Q&A with two Infosec instructors.

Emerging trend checklist: Which certifications cover which new skills?
Boost your team's cybersecurity skills with the right certifications. Discover the most in-demand skills and the certifications that cover them in our free guide.

Security Awareness Outcomes with Infosec IQ
See security awareness and training outcomes from more than five million Infosec IQ learners.
Our resources
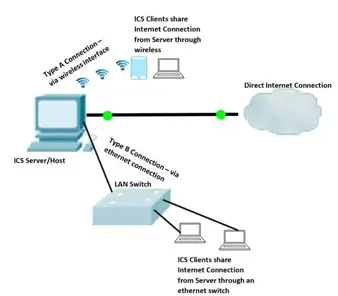
MyPublicWiFi – A Windows Utility to manage ICS

6 Days Lab 1.1 CTF Walkthrough

Business Email Compromise (BEC): How To Avoid CEO Fraud
Use of Various Windows Utilities to Manage ICS Processes

Differences between Security+ SYO-401 and SYO-501 exams [DECOMMISSIONED ARTICLE]

5 Business Email Compromise Attack Examples We Can Learn From

How to Prevent BEC with Security Awareness Training

Tools and resources to prepare for a hacker CTF competition or challenge
Kali reporting tools
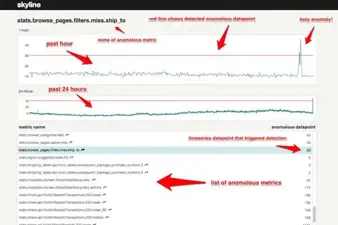
Top 10 Open-Source Security Tools Released by Tech Giants

Guiding principles in information security

Inspeckage: Dynamic Assessment Tool for Android
Tiredful API Part Two

ZLAB MALWARE ANALYSIS REPORT: RANSOMWARE-AS-A-SERVICE PLATFORMS
Tiredful API Part One

The Ultimate Guide to EC-Council Certifications: Overview & Career Paths
Android exploitation with Kali

Free & open source rootkit and malware detection tools

2017 OWASP A8 Update: Insecure Deserialization

2017 OWASP A7 Update: Cross-Site Scripting

How Secure Wire Transfer Procedures Can Prevent Business Email Compromise

How Business Email Compromise Attacks Work: A Detailed Case Study

5 real-world examples of business email compromise

Android vs. iOS Mobile App Penetration Testing