VENOM Vulnerability Opens Millions of Virtual Machines to Attack
The VENOM vulnerability
A security vulnerability recently patched is scaring the IT industry, its name is VENOM, and it is coded as CVE-2015-3456. The dreaded vulnerability was first discovered by Jason Geffner that is a senior security researcher at CrowdStrike. The cyber expert has reported that the VENOM vulnerability would allow an attacker to compromise any virtualization platforms, so practically any machine located in a data center's network.
Exactly like many other vulnerabilities discovered in the last couple of years, the VENOM flaw has existed for a long time. Experts say that it dates from 2004, when the virtual Floppy Disk Controller was first added to the QEMU codebase. The vulnerability affects the Xen, KVM, and native QEMU virtual machine platforms and appliances.
Learn Vulnerability Management
The impact of the vulnerability could be dramatic; potentially millions of virtual machines are vulnerable to the VENOM exploitation.
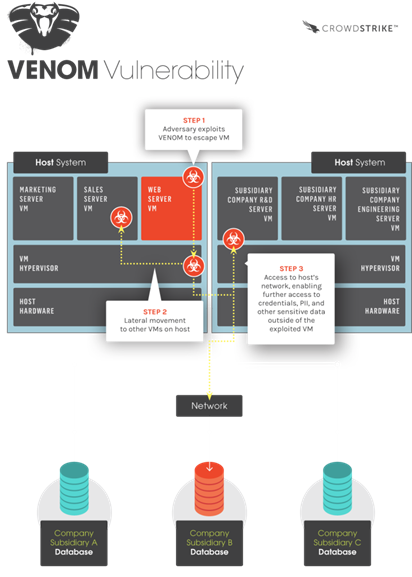
"VENOM, CVE-2015-3456, is a security vulnerability in the virtual floppy drive code used by many computer virtualization platforms. This vulnerability may allow an attacker to escape from the confines of an affected virtual machine (VM) guest and potentially obtain code-execution access to the host. Absent mitigation, this VM escape could open access to the host system and all other VMs running on that host, potentially giving adversaries significant elevated access to the host's local network and adjacent systems." explained Geffner in a blog post.
VENOM is the acronym for "Virtual Environment Neglected Operations Manipulation," as explained by Geffner. The vulnerability resides in the floppy disk controller driver for QEMU, which is an open-source computer emulator known as a hypervisor that is used for the management of virtualized platforms.
According to the security advisory, the attackers can trigger the VENOM vulnerability by sending commands and specially crafted parameter data from the guest system to the vulnerable Floppy Disk Controller to cause the data buffer overflow and execute arbitrary code in the context of the host's hypervisor process. The flaw is very dangerous because attackers could exploit it against a wide array of virtual machines, it is triggerable on default configurations, and would allow the arbitrary code execution.
Experts consider VENOM different from other vulnerabilities in the past that effect virtualized environments, since it exists in the hypervisor's codebase it is independent from the specific host operating system (Linux, Windows, Mac OS, etc.).
Figure 1 - Venom Vulnerability diagram - CrowdStrike Report
Thousands of organizations and millions of end-users are in danger due to the present of VENOM. As explained by the experts, a threat actor can crash the hypervisor obtaining the control of the targeted machine and all virtual machines running on it. Fortunately, as explained by CrowdStrike, principal security firms have seen the VENOM flaw exploited in the wild.
"Exploitation of the VENOM vulnerability can expose access to corporate intellectual property (IP), in addition to sensitive and personally identifiable information (PII), potentially impacting the thousands of organizations and millions of end users that rely on affected VMs for the allocation of shared computing resources, as well as connectivity, storage, security, and privacy." wrote the researcher.
Cloud providers like Amazon have promptly provided a fix for the VENOM flaw, experts at CrowdStrike have worked with principal software vendors to develop a patch for the vulnerability.
CrowdStrike reported that the following vendor have already released patches and advisories for the VENOM flaw:
- QEMU: http://git.qemu.org/?p=qemu.git;a=commitdiff;h=e907746266721f305d67bc0718795fedee2e824c
- Xen Project: http://xenbits.xen.org/xsa/advisory-133.html
- Red Hat: https://access.redhat.com/articles/1444903
- Citrix: http://support.citrix.com/article/CTX201078
- FireEye: https://www.fireeye.com/content/dam/fireeye-www/support/pdfs/fireeye-venom-vulnerability.pdf
- Linode: https://blog.linode.com/2015/05/13/venom-cve-2015-3456-vulnerability-and-linode/
- Rackspace: https://community.rackspace.com/general/f/53/t/5187
- Ubuntu: http://www.ubuntu.com/usn/usn-2608-1/
- Debian: https://security-tracker.debian.org/tracker/CVE-2015-3456
- Suse: https://www.suse.com/support/kb/doc.php?id=7016497
- DigitalOcean: https://www.digitalocean.com/company/blog/update-on-CVE-2015-3456/
- f5: https://support.f5.com/kb/en-us/solutions/public/16000/600/sol16620.html
CrowdStrike confirmed that it will not publicly release a proof of concept exploit code.
VENOM vs Heartbleed
Many sources online have compared the VENOM vulnerability to other vulnerabilities saying that is much "bigger than Heartbleed."
Jessica Lavery from the Veracode rapid response program and trigger event communications has provided, in my opinion, one of the most interesting analyses of the principal differences between the two flaws. VENOM has certainly a potentially bigger impact than Heartbleed due to the amazing amount of virtualization platforms and appliances it affects.
But, as highlighted by Jessica Lavery, the severity of VENOM is not so alarming for the following reasons:
-
A VENOM exploit is not available in the wild as confirmed by CrowdStrike, probably it is better to say that it is not known. This means that in the worst scenario, a limited number of threat actors could be in possess of the necessary knowledge to trigger the flaw, this means that the chances to be compromised due to a VENOM hack are very low.
-
The development of a VENOM exploit requests a significant effort.
-
The likelihood that the VENOM flaw will be exploited in large-scale attacks is very low. Experts consider vulnerabilities like VENOM mostly exploitable for highly targeted attack.
-
VENOM flaw is not exploitable for remote attacks, this means, this means that attackers need to access is some ways the targeted infrastructure.
The Venom flaw, a possible weapon in the NSA arsenal
Many experts speculate that a persistent attacker, like an intelligence agency, has the necessary knowledge and resources to easily exploit the VENOM flaw.
Rob Graham, CEO of security firm Errata Security, speculates that it will be easy for attackers to trigger the vulnerability to exploit the flaw, steal sensitive data and bitcoins.
The exploitation of the VENOM flaw could have serious impact on all on virtual private servers, which use virtualization to segregate different customers' data on the same physical machine. Graham is sure that a proof-of-concept exploit will be available very soon.
"This is a hypervisor privilege escalation bug. To exploit this, you'd sign up with one of the zillions of VPS providers and get a Linux instance. You'd then, likely, replace the floppy driver in the Linux kernel with a custom driver that exploits this bug. You have root access to your own kernel, of course, which you are going to escalate to root access of the hypervisor." States the expert in a blog post.
The experts believe that agencies like the NSA could exploit VENOM to hack systems worldwide.
"Once you gained control of the host, you'd then of course gain access to any of the other instances. This would be a perfect bug for the NSA. Bitcoin wallets, RSA private keys, forum passwords, and the like are easily found searching raw memory. Once you've popped the host, reading memory of other hosted virtual machines is undetectable. Assuming the NSA had a program that they'd debugged over the years that looked for such stuff, for $100,000 they could buy a ton of $10 VPS instances around the world, then run the search. All sorts of great information would fall out of such an effort—you'd probably make your money back from discovered Bitcoin alone."
How to fix VENOM vulnerability?
The experts urge the administrators of a system running Xen, KVM, or the native QEMU client, to assess their system and apply the latest patches provided by their vendors. It is important to operate following the instructions provided by vendors verifying the application for the last VENOM patch.
References
http://securityaffairs.co/wordpress/36787/hacking/venom-vulnerability.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3456
http://blog.erratasec.com/2015/05/some-technical-notes-on-venom.html#.VVTkZvntmko
https://www.veracode.com/blog/2015/05/venom-%E2%80%93-not-deadly-heartbleed
Learn Vulnerability Management
http://blog.erratasec.com/2015/05/some-technical-notes-on-venom.html#.VVTkZvntmko