The FREAK Vulnerability: From Discovery to Mitigation
A few weeks ago, security experts discovered a new major security SSL/TLS vulnerability, dubbed FREAK, that for more than a decade left users of Apple and Google devices vulnerable to hacking when they visited millions of legitimate and secure websites.
The FREAK critical vulnerability (CVE-2015-0204), also known as Factoring Attack on RSA-EXPORT Keys, could be exploited by an attacker to conduct man-in-the-middle attacks on encrypted traffic when Internet users visited supposedly secured websites.
Learn Vulnerability Management
By exploiting the FREAK flaw, an attacker can force clients to use older and weaker encryption, then he can crack the traffic protected with 512-bit key encryption in a few hours. Once he's decrypted the protected traffic, the attacker can steal sensitive information, including banking credentials, or launch an attack by injecting malicious code in the encrypted stream of data.
"The flaw resulted from a former U.S. government policy that forbade the export of strong encryption and required that weaker "export-grade" products be shipped to customers in other countries, say the researchers who discovered the problem. These restrictions were lifted in the late 1990s, but the weaker encryption got baked into widely used software that proliferated around the world and back into the United States, apparently unnoticed until this year," states The Washington Post on the FREAK vulnerability.
The FREAK vulnerability was discovered by security researchers of the French Institute for Research in Computer Science and Automation (Inria) and Microsoft. It affects both OpenSSL versions 1.01k and earlier and Apple's Secure Transport.
In a classic attack scenario, the exploitation of a vulnerable device (i.e. Android browsers, OpenSSL versions, Chrome versions before 41, Safari) is possible if the user visits a vulnerable HTTPS-protected website.
The attack could be effective if the server hosting the website visited by victims is still supporting 1990s-era "export-grade" cryptography or 512-bit RSA.
Many experts have associated the FREAK and POODLE vulnerabilities due to the similarity in the way they exploit flaws in protocols to make vulnerable a connection deemed secure.
The POODLE vulnerability stands for 'Padding Oracle on Downgraded Legacy Encryption'. It allows malicious attackers to lower the SSL/TLS communication to the weakest possible version. FREAK is quite similar in the way it affects the SSL/TLS implementations that supports and accepts export versions of protocols that use the RSA algorithm.
The "export-grade" encryption
Back in the 1990s, the US government endeavored to direct the export of items using "robust" encryption, and gadgets were stacked with weaker "export-grade" encryption before being dispatched out of the country, which allowed a maximum key length of 512 bits for "export-grade" encryption. The situation changed in 2000 due to a modification of the US export laws that authorized merchants to include 128-bit ciphers in their products and to disseminate them all over the world.
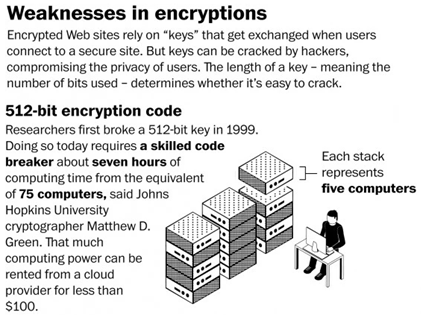
Figure 1 - FREAK vulnerability (The Washington Post)
The experts that found the FREAK vulnerability discovered that the "export-grade" cryptography support was never removed. Assistant Research Professor Matthew Green of Johns Hopkins University's Information Security Institute in Maryland has provided a detailed explanation of the FREAK attack in a blog post explaining how to run a MitM attack exploiting the vulnerability.
Professor Green detailed a Man-In-The-Middle attack that exploits the FREAK flaw:
- In the client's Hello message, client asks for a standard 'RSA' cipher suite from the server.
- The MitM attacker hampers the integrity of this message and changes this message to ask for 'Export RSA'.
- The server responds to the client's request with a 512-bit export RSA key, signed with its long-term key.
- The client accepts this weak key from the server due to the OpenSSL/ Secure Transport bug.
- The attacker factors the RSA modules to recover the corresponding RSA decryption key.
- When the client encrypts the 'pre-master secret' to the server, the attacker can now decrypt it to recover the TLS 'master secret'.
- From here on out, the attacker sees plain text and can inject anything it wants.
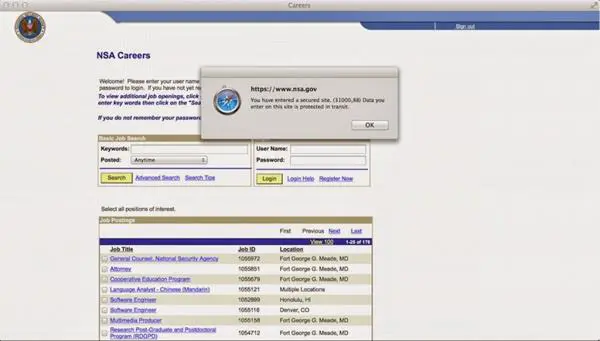
Figure 2 - NSA Website vulnerable to the FREAK attack
The researchers Alex Halderman, Zakir Durumeric and David Adrian at University of Michigan made a large-scale scan to identify vulnerable websites. The experts examined more than 14 million websites that support the SSL/TLS protocols and discovered that the FREAK vulnerability affects nearly 36 percent of SSL WEBSITES.
"Based on some recent scans by Alex Halderman, Zakir Durumeric and David Adrian at University of Michigan, it seems that export-RSA is supported by as many as 5.2% - 36.7% (!!!!) of the 14 million sites serving browser-trusted certs. The vast majority of these sites appear to be content distribution networks (CDN) like Akamai. Those CDNs are now in the process of removing export grade suites," states Matthew Green.
Several security experts speculate that the FREAK vulnerability was intentionally introduced by governments in order to conduct surveillance activities.
FREAK is a "good example of what can go wrong when government asks to build weaknesses into security systems," wrote Ed Felten, another respected professor of computer science at Princeton University.
All Windows systems are vulnerable to the FREAK attack
According to a security advisory published by Microsoft, all supported versions of Windows OS are affected by the recently discovered FREAK vulnerability. The impact of the vulnerability could be dramatic for Microsoft systems, as confirmed by the security advisory that informs its customers about the presence of the FREAK vulnerability in the Microsoft Secure Channel (Schannel) stack.
"Secure Channel, also known as Schannel, is asecurity support provider (SSP) that contains a set of security protocols that provide identity authentication and secure, private communication through encryption. Schannel is primarily used for Internet applications that require secure Hypertext Transfer Protocol (HTTP) communications."
Secure Channel is vulnerable to the FREAK encryption-downgrade attack and affects all supported releases of Microsoft Windows.
"Microsoft is aware of a security feature bypass vulnerability in Secure Channel (Schannel) that affects all supported releases of Microsoft Windows. Our investigation has verified that the vulnerability could allow an attacker to force the downgrading of the cipher suites used in an SSL/TLS connection on a Windows client system. The vulnerability facilitates exploitation of the publicly disclosed FREAK technique, which is an industry-wide issue that is not specific to Windows operating systems. When this security advisory was originally released, Microsoft had not received any information to indicate that this issue had been publicly used to attack customers." states the advisory.
The Windows version affected by the FREAK vulnerability (CVE-2015-1637) are:
- Windows Server 2003
- Windows Vista
- Windows Server 2008
- Windows 7
- Windows 8 and 8.1
- Windows Server 2012
- Windows RT
Microsoft experts explained that hackers that share the same network of the victims could exploit the FREAK flaw and force the software using the Schannel component (i.e. Internet Explorer) to adopt weak encryption over the web.
Microsoft confirmed that its experts are "actively working" to fix the issue and to protect its users from cyber attack exploiting the FREAK vulnerability.
"We are actively working with partners in our Microsoft Active Protections Program (MAPP) to provide information that they can use to provide broader protections to customers," continues the advisory.
Google immediately released an updated version of the Chrome browser for Mac systems, meanwhile Safari on Mac OS and iOS isn't vulnerable to the FREAK flaw.
Researchers hack NSA's website with only $104
After the disclosure of the FREAK vulnerability, a group of researchers demonstrated that it is possible to exploit the flaw to hack websites deemed armored. The experts highlighted that an attacker doesn't need specific resources in order to do it, even if the target is the official NSA website. The researchers in fact successfully ran the attack against the site by using 8 hours of Amazon's cloud computing power and spending only $104.
As explained by the researcher, who proposed a proof of concept for this attack, the attackers only need a "few ingredients" to mount the offensive:
- a collection of tools to run the MitM attack.
- the ability to (quickly) factor 512-bit RSA keys.
- a vulnerable client and server.
The Proof of Concept was made by Karthik Bhargavan and Antoine Delignat-Lavaud at INRIA, who assembled a MitM proxy to capture connections and modify them on fly to force the export-RSA against a vulnerable website.
"To factor the 512-bit export keys, the project enlisted the help of Nadia Heninger at U. Penn, who has been working on 'Factoring as a Service' for exactly this purpose. Her platform uses cado-nfs on a cluster of EC2 virtual servers, and (with Nadia doing quite a bit of handholding to deal with crashes) was able to factor a bunch of 512-bit keys — each in about 7.5 hours for $104 in EC2 time."
Be aware, it is profoundly wrong to say that the researchers hacked the NSA website because they ran an MitM attack exploiting the FREAK flaw, but haven't compromised the server that is hosting the government site.
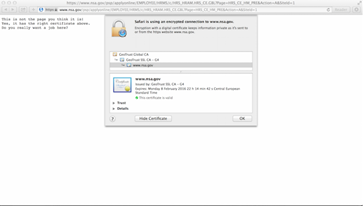
Figura 3 - MITM against NSA website PoC
"Some will point out that an MITM attack on the NSA is not really an 'MITM attack on the NSA' because NSA outsources its web presence to the Akamai CDN (see obligatory XKCD at right). These people may be right, but they also lack poetry in their souls," explained the crypto expert Matthew Green.
Among other vulnerable websites, there is connect.facebook.net, which hosts the script for Facebook's "Like" and login button that are included in several websites on the Internet.
At the time of this writing, the NSA is vulnerable to the FREAK attack. Despite that the website doesn't contain sensitive information, experts highlight that it has a careers section. A threat actor exploiting the FREAK flaw could potentially steal the credentials of would-be NSAers and access their job applications, as reported by Motherboard website.
Mitigation
To check whether your browser is vulnerable to this attack or not, visit freakattack.com. If your browser is safe from the FREAK attack, then it will prompt a message, 'Good News! Your browser appears to be safe from the FREAK Attack!' Otherwise it will prompt a warning message that your browser is vulnerable to CVE-2015-0204. The best way to make yourself free from this attack is to update your browser.
Figure 4 - FREAK test
The web server administrators are invited to disable support for export suites, including all known insecure ciphers, and enable forward secrecy.

Figure 5 - FREAK vulnerability Infograph (Symantec)
IT Giants and FREAK … it's time to update your solutions
The IT giants immediately started analysis of their products and solution to verify presence of the FREAK flaw. Google promptly distributed a patch for Android OS, and the fix was made available to its partners.
Apple has recently released the iOS 8.2 version for its mobile devices, iPhones and iPads, to avoid that its users could be victims of MITM attacks.
"Secure Transport accepted short ephemeral RSA keys, usually used only in export-strength RSA cipher suites, on connections using full-strength RSA cipher suites. This issue, also known as FREAK, only affected connections to servers which support export-strength RSA cipher suites, and was addressed by removing support for ephemeral RSA keys," reads the Apple advisory.
"For the protection of our customers, Apple does not disclose, discuss, or confirm security issues until a full investigation has occurred and any necessary patches or releases are available. To learn more about Apple Product Security, see the Apple Product Security website," states the advisory note issued by the company, which confirmed that the flaw affects iPhone 4s handsets and later, iPod touch (5th generation) and later, and iPad 2 and later.
Last week, Microsoft issued a security advisory to inform its users that almost every operating system of the company was affected by FREAK. For this reason the company released a fix for the FREAK vulnerability spread across 14 security bulletins.
"Vulnerability in Schannel Could Allow Security Feature Bypass (3046049) - This security update resolves a vulnerability in Microsoft Windows that facilitates exploitation of the publicly disclosed FREAK technique, an industry-wide issue that is not specific to Windows operating systems. The vulnerability could allow a man-in-the-middle (MiTM) attacker to force the downgrading of the key length of an RSA key to EXPORT-grade length in a TLS connection. Any Windows system using Schannel to connect to a remote TLS server with an insecure cipher suite is affected," states the description for the Bulletin MS15-031 rated as critical.
Appendix
Below the list of HTTPS websites (March 3, 9:00 PM EST) included in the Alexa Top 10K that support RSA Export Suites. This list is quite long and is available at https://freakattack.com/vulnerable.txt.
Alexa Rank Domain Address Tested
-
27 sohu.com 123.125.116.19
-
182 businessinsider.com 64.27.101.155
-
234 ppomppu.co.kr 110.45.151.212
-
243 smzdm.com 114.113.158.226
-
247 americanexpress.com 23.13.171.41
-
251 jabong.com 23.203.7.176
-
273 groupon.com 184.26.49.170
-
290 bloomberg.com 69.191.212.191
-
442 4shared.com 208.88.224.136
-
448 npr.org 216.35.221.76
-
519 hatena.ne.jp 59.106.194.19hatena.ne.jp 59.106.194.19
-
615 instructables.com 74.50.63.27
-
629 airtel.in 125.19.135.93airtel.in 125.19.135.93
-
649 kohls.com 23.202.240.45
-
767 adplxmd.com 205.186.187.178
-
795 mit.edu 23.202.254.127
-
799 tinyurl.com 23.220.249.147
-
808 suning.com 122.228.85.93
-
820 saramin.co.kr 182.162.86.29
-
891 vi-view.com 50.97.32.135
-
903 itau.com.br 23.38.106.190
-
951 huaban.com 115.238.54.162
-
959 zomato.com 54.151.251.33
-
960 nationalgeographic.com 74.217.81.233
-
999 marriott.com 23.45.45.5
-
1001 jobrapido.com 46.105.106.82
-
1029 forever21.com 23.202.233.118
-
1089 wiocha.pl 195.225.138.234wiocha.pl 195.225.138.234
-
1150 axisbank.com 119.226.139.40
-
1180 clarin.com 200.42.136.212
-
1236 mgid.com 208.94.232.200
-
1247 jcpenney.com 23.49.180.228
-
1261 wowhead.com 23.199.195.58
-
1297 gaana.com 223.165.30.26
-
1313 mtime.com 59.151.32.20
-
1360 refinery29.com 50.22.34.136
-
1361 vente-privee.com 185.45.180.3
-
1364 ynet.co.il 192.115.80.55
-
1383 dhgate.com 124.42.15.198
-
1411 vesti.ru 80.247.32.206vesti.ru 80.247.32.206
-
1424 adxcore.com 188.165.36.101
-
1456 sweet-page.com 50.97.32.133
-
1484 binaryprofessional.com 50.7.157.122
-
1502 globososo.com 184.173.140.162
-
1571 estadao.com.br 23.199.200.37
-
1573 jcrew.com 23.37.8.44
-
1586 17173.com 220.181.90.240
-
1599 bmi.ir 89.235.64.67bmi.ir 89.235.64.67
-
1620 zdnet.com 50.112.160.88
-
1646 accountonline.com 192.193.200.101
-
1662 umich.edu 141.211.243.44
-
1680 cornell.edu 128.253.173.241
-
1684 lg.com 165.244.62.23
-
1693 uludagsozluk.com 188.132.225.181
-
1722 yixun.com 111.30.131.20
-
1738 priceminister.com 212.23.167.62
-
1856 ibtimes.co.uk 64.147.114.55
-
1860 extra.com.br 23.221.0.145
-
1864 jiameng.com 117.78.2.204
-
1866 ihg.com 23.202.251.213
-
1878 miui.com 42.62.48.148
-
1902 syosetu.com 111.64.91.10
-
1915 thrillist.com 50.57.33.153
References
http://securityaffairs.co/wordpress/34404/hacking/freak-ssl-tls-vulnerability.html
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-0204
http://securityaffairs.co/wordpress/34506/hacking/freak-affects-all-windows-versions.html
http://blog.cryptographyengineering.com/2015/03/attack-of-week-freak-or-factoring-nsa.html
http://securityaffairs.co/wordpress/34554/hacking/nsa-site-vulnerable-freak-flaw.html
http://securityaffairs.co/wordpress/34730/hacking/apple-microsoft-fix-freak.html
http://securityaffairs.co/wordpress/34506/hacking/freak-affects-all-windows-versions.html
https://technet.microsoft.com/en-us/library/security/3046015?f=255&MSPPError=-2147217396
Learn Vulnerability Management
http://securityaffairs.co/wordpress/34495/security/secure-from-freak-vulnerability.html