How to build security awareness & training to NIST standards
Most security and IT professionals understand the importance of workforce security awareness and training for organizational cybersecurity. This is an important first step, but it still leaves many wondering exactly how to run a training program, the best ways to educate employees and even the most important cybersecurity topics to cover.
Leaning on an established framework to build and mature your security awareness and training program can help. That’s where NIST comes in.

Two year's worth of NIST-aligned training
Deliver a comprehensive security awareness program using this series' 1- or 2-year program plans.
In this blog post, we’ll examine NIST’s cybersecurity training resources and guidelines and explore how you can use Infosec IQ to not only follow NIST recommendations but also prepare your workforce for the cybersecurity threats they face.
What is NIST?
The National Institute of Standards and Technology (NIST) is an agency within the United States Department of Commerce. NIST serves as the U.S. national laboratory, promoting innovation and industrial competitiveness in numerous industries by setting measurement standards, performing research and building organizational frameworks — including frameworks to help organizations structure and mature their security awareness and training programs.
NIST cybersecurity training guidelines
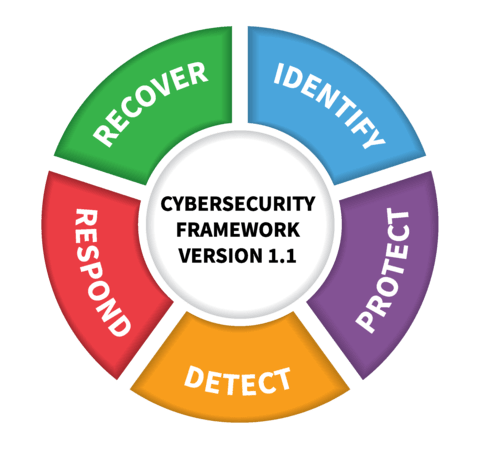
NIST maintains a series of publications dedicated to cybersecurity training and employee awareness.
NIST Framework for Improving Critical Infrastructure Cybersecurity
The NIST Cybersecurity Framework is a voluntary set of standards, guidelines and best practices to help organizations manage cybersecurity-related risk.
Protecting your organization with security awareness and training
NIST highlights security awareness and training as a core component of the Protect function of the Cybersecurity Framework.
"The Protect Function supports the ability to limit or contain the impact of a potential cybersecurity event."
NIST recommends awareness and training for an organization’s entire workforce and partners as a necessary defense against cyber attacks.
NIST Special Publication 800-50, Building an Information Technology Security Awareness and Training Program
NIST Special Publication 800-50 provides guidelines for designing an employee awareness and training program, developing training materials and implementing a program.
Security awareness and training objectives
In Special Publication 800-50, NIST provides two clear objectives for security awareness and training.
"Material should be developed with the following in mind:
What behavior do we want to reinforce? (awareness); and
What skill or skills do we want the audience to learn and apply? (training)."NIST recommends training that includes educational, awareness-based content as well as skill development to help employees understand the threats they face and take the right action to prevent security incidents.
Security awareness and training topics
NIST Special Publication 800-50 recommends security awareness and training covering the following nine topics:
- Phishing
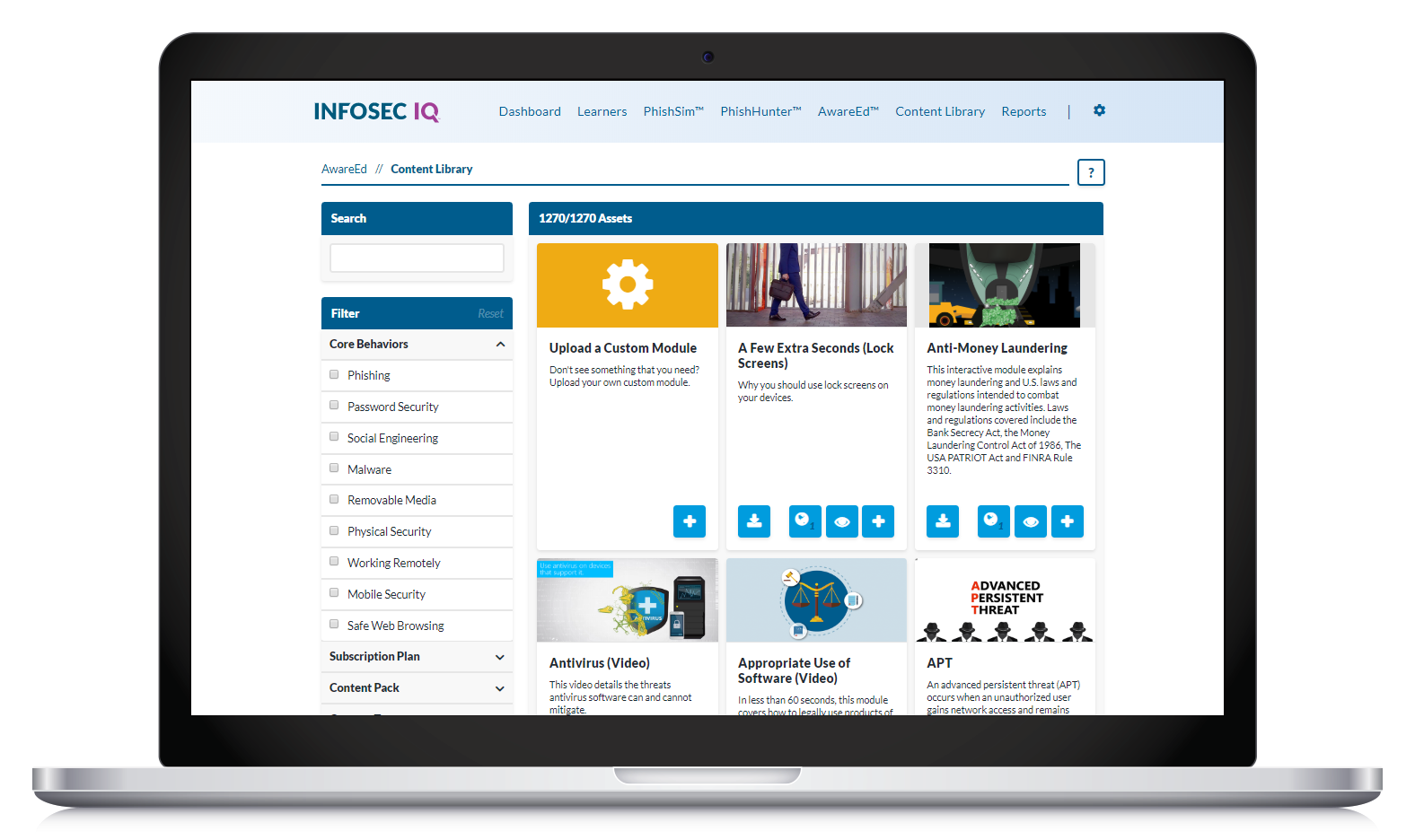 Password security
Password security- Safe web browsing
- Social engineering
- Malware
- Mobile security
- Physical security
- Removable media
- Working remotely
Although each of the core cybersecurity topics can be broken down into detailed sub-topics, this list serves as a foundational training recommendation for all employees.
Reporting and monitoring compliance
NIST Special Publication 800-50 also provides guidance on reporting and monitoring compliance:
"Once the program has been implemented, processes must be put in place to monitor compliance and effectiveness. An automated tracking system should be designed to capture key information regarding program activity (e.g., courses, dates, audience, costs, sources)."
With the right tracking and reporting tools, program managers can identify gaps in training and continuously update and improve their training curriculum.
NIST special publication 800-53, security and privacy controls for information systems and organizations
NIST Special Publication 800-53 provides a catalog of security and privacy controls, recommendations for cybersecurity training and guidance on role-based training.
Industry and role-based training
In Special Publication 800-53, NIST provides guidance on tailoring training based on employee roles and duties.
"Comprehensive role-based training addresses management, operational, and technical roles and responsibilities covering physical, personnel, and technical safeguards and countermeasures. Such training can include, for example, policies, procedures, tools, methods, and artifacts for the security and privacy roles defined."
NIST also recommends training to address unique regulations, standards and risks associated with each organization's industry. NIST encourages security awareness managers to take their awareness and training program a step beyond general workforce training by educating each employee on the cybersecurity threats they are most likely to face.
Building your security awareness & training program
The NIST Cybersecurity Framework and special publications listed above are useful resources for guiding your security awareness and training program. However, most organizations lack the time and resources to build an entire program mapped to NIST recommendations from the ground up. That’s why we designed the Infosec IQ security awareness and training platform to align with NIST standards and recommendations.
Infosec IQ & NIST recommendations
At Infosec, we rely heavily on NIST guidelines to not only develop our security awareness and training curriculum, but also build features, automation tools and reports into the Infosec IQ platform that make it easy for you to track compliance and mature your program.
Training content
Every Infosec IQ training module and adaptive assessment is mapped to one of the nine core security behaviors. This allows you to easily select topic-specific training content and measure learner comprehension for each of the nine core security behaviors.
Industry- and role-based training
Infosec IQ training also provides a wide range of training modules and styles for all industries and employee roles. This allows you to build a custom training curriculum from 2,000+ training resources mapped to the nine core security behaviors or use a turnkey training program built from NIST recommendations. With Infosec IQ, you have the flexibility to train for each core security topic while emphasizing the most relevant security information for each employee.
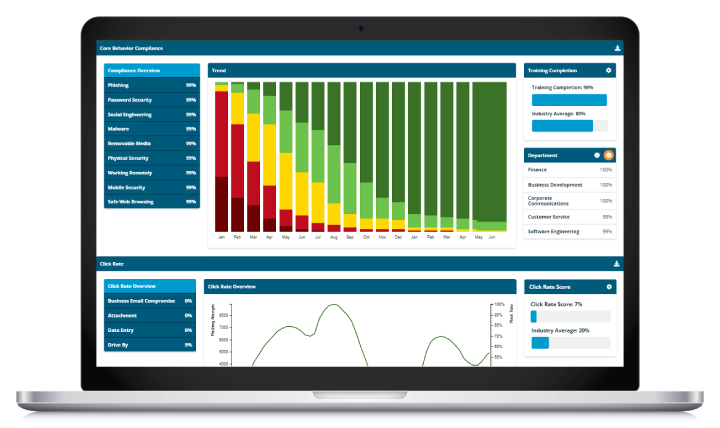
NIST compliance reporting
Using Infosec IQ reporting, you can track both individual and organization-level training completion and learner comprehension of each core security behavior. This allows you to quantify security training compliance with NIST guidelines and easily identify security topics, departments or even individual learners who require training. The Infosec IQ core behavior compliance dashboard tracks your organization’s progress over time and helps you deliver reports for auditors and stakeholders.
Achieve NIST compliance — Build a cyber-aware workforce
Whether you’re building your organization’s first security awareness and training program or looking to mature and refine an existing program, choosing a training platform built from NIST recommendations gives you both the structure and the flexibility you need to keep your employees and your organization secure.
Phishing simulations & training
The Infosec IQ security awareness and training platform gives you the resources and a clear path to NIST compliance. Infosec IQ makes it easy to follow NIST recommendations so you can focus on maturing your security awareness program, empowering your employees and achieving the ultimate goal of fewer security incidents.









