Security Awareness & Training Resource Center
Featured content

Deconstructing Human-Element Breaches | Infosec HRM
Human risk management isn’t just rebranded SA&T — it’s a profound change of mindset, strategy, process and technology that approaches human-related breaches in a new way.
![Inside an Infosec Boot Camp: All your questions, answered! [replay]](/globalassets/is-wb-24-05-inside-an-infosec-boot-camp_thumbnail2.webp?width=338&height=304&rmode=Max&bgcolor=transparent)
Inside an Infosec Boot Camp: All your questions, answered!
You need to get certified, but is an Infosec Boot Camp the right choice for you — or your team? Find out in this live Q&A with two Infosec instructors.

Emerging trend checklist: Which certifications cover which new skills?
Boost your team's cybersecurity skills with the right certifications. Discover the most in-demand skills and the certifications that cover them in our free guide.

Security Awareness Outcomes with Infosec IQ
See security awareness and training outcomes from more than five million Infosec IQ learners.
Our resources

Process: Pre-Engagement

Common malware persistence mechanisms

The Breach of Anthem Health - the Largest Healthcare Breach in History
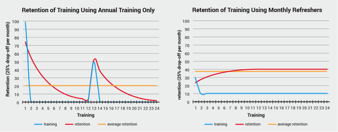
Building Serialized Phishing Simulation and Security Awareness Campaigns

Ethical hacking vs. penetration testing

Why GIAC? A Suitable Choice that Meets Professional Needs

New Wave of Cyber-attacks on Banks
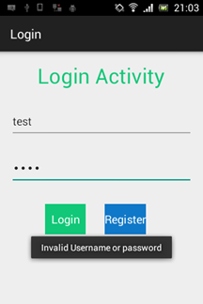
Hooking and Patching Android Apps Using Cydia Substrate Extensions
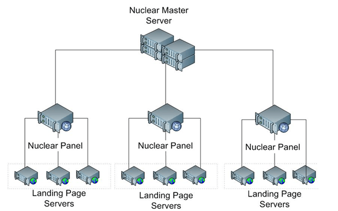
Ransomware: A Highly-Profitable Evolving Threat

Data sanitization for cloud storage

Ransomware Mitigation and Prevention
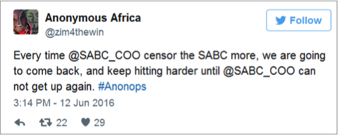
Phishing: Denial of Service (DoS) Implications

Financial Losses from Phishing

Android Malware Analysis
Firmware Analysis for IoT Devices
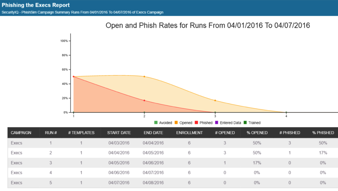
Phishing Simulation – How Do You Calculate Effectiveness and ROI? (Part 2 of 2)
Metasploit Certification Overview

Phishing Definition, Prevention, and Examples
The Dark Web: a Paradise for Scammers
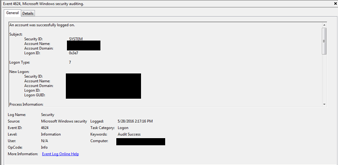
Relevance of Windows EventIDs in investigation
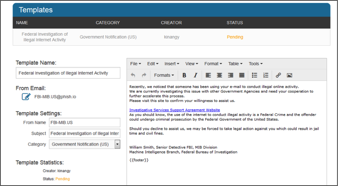
Phishing Attacks in the Government and Military

Ransomware as a Service: 8 Known RaaS Threats
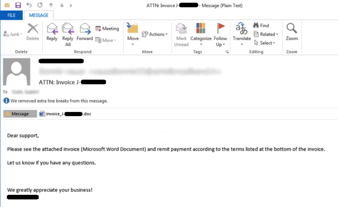
Case Study of Phishing for Data Theft/Ransom: Locky Ransomware

Website Forgery