Ransomware: A Highly-Profitable Evolving Threat
Introduction
Ransomware is considered by the security industry one of the most dangerous threats to Internet users and organizations across the world.
Malware authors are developing new malicious codes that implement new features to improve evasion and spreading abilities.

What should you learn next?
The efforts are sustained by the conviction that ransomware-based attacks are effective and allow crooks to easily cash out their illegal activities.
Let's see which are the novelties in the threat landscape and let's try to understand better the way the bad actors spread ransomware and which are their real profits.
Self-propagating ransomware spreading in the wild
Recently Microsoft issued an alert relates a new strain of ransomware that exhibits worm-like behavior. The malware was designed to compromise Windows systems; it propagates itself through removable and network drives.
"We are alerting Windows users of a new type of ransomware that exhibits worm-like behavior. This ransom leverages removable and network drives to propagate itself and affect more users. We detect this ransomware as Ransom:Win32/ZCryptor.A." states Microsoft." It has self-replicating worm behavior that will also enumerate network drives, logical drives."
The experts from Microsoft, who investigated the threat, confirmed that bad actors behind this campaign leveraged spam emails to spread the ransomware dubbed Ransom:Win32/ZCryptor.A.
The authors of Ransom:Win32/ZCryptor.A implemented a mechanism of persistence through the Windows registry, in this way the threat will run at the system start-up.
The registry key used is
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun
zcrypt = {path of the executed malware}
Once ZCryptor is executed drops autorun.inf in removable drives, a zycrypt.lnk in the start-up folder:
%User Startup%zcrypt.lnk
along with a copy of itself as {Drive}:system.exe and %APPDATA%zcrypt.exe. It also changes the file attributes to hide from the user that browses the file system.
For example: c:usersadministratorappdataroamingzcrypt.exe
The ransomware encrypts files having a large number of extensions then he changes the extension to .zcrypt (i.e. originalfilename.zcrypt)
It then displays the ransom note to users in an HTML file, a file named "How to decrypt files.html" that also includes the instruction for the payment that has to be made in Bitcoin.
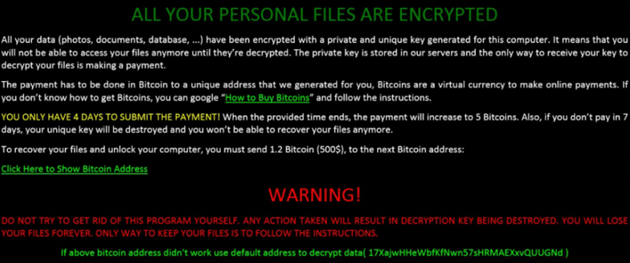
Infected machines are observed to have zcrypt1.0 mutex which denotes that an instance of this ransomware is already running on the infected machine.
The researchers from Microsoft observed the ransomware connecting to a remote host with the following URL.
http://<obfuscated>/rsa/rsa.php?computerid={Computer_ID} where the {Computer_ID} is entry found inside a dropped file %AppData%cid.ztxt
For example, c:usersadministratorappdataroamingcid.ztxt
Ransomware, a profitable business
As experts have explained in many reports, ransomware is a profitable instrument for organized cyber criminal gangs and wannabe crooks.
For this reason in the criminal underground, several actors offer services that allow criminals to create and distribute their ransomware
A key component in the attack chain for any malware-based attack, including ransomware, is the exploit kit. Authors of malware are offering for sale malware as a cloud-based service. There are many Exploit kits available in the Malware-as-a-Service market, and Nuclear EK is one of them since 2010.
"Developers create tools that they sell or rent to customers through online black markets, complete with sales, money-back guarantees, and reputation systems to provide customers with assurances that they won't get ripped off." reads the 2016 Trustwave Global Security Report,
Crooks can rent the popular Nuclear EK just for the time of their campaign, in this way they are ready to launch their attack once in possess of their malware. Recently, experts from the Check Point security firm detailed one of this infrastructure; the researchers detailed a hierarchical architecture where all the control panels are fed by a master server that contains the exploit code and pushes the malware onto targeted systems.
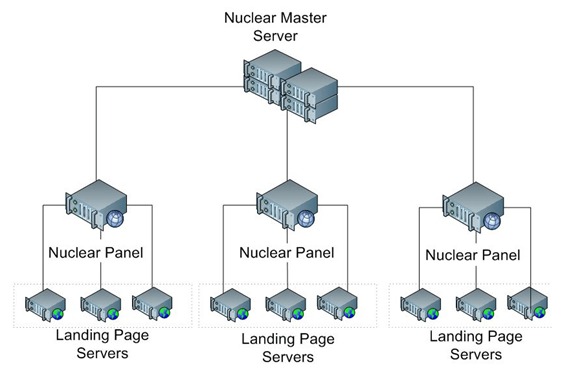
Figure 1 - Malware-as-a-Service - EK infrastructure (Source CheckPoint)
In one case, the researchers from Check Point reported that they have found 15 active control panels for the Nuclear EK that are rented for a few thousand dollars per month. It has been estimated that the creators of the Nuclear EK are gaining nearly 100K USD each month.
The authors of the code check the country from which the victim is browsing, it is not eligible for countries Azerbaijan, Armenia, Belarus, Georgia, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan, Uzbekistan, and Ukraine. It is most probably to avoid problems with the law in these countries.
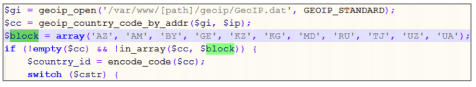
Check Point statistics say that 1,846,678 machines were attacked, and 184,568 machines were successfully exploited, nearly 10% success.
According to the report, the Europe and the US are the main targets. Despite many banking trojans are distributed by the exploit kit, the number of ransomware infections is nearly three times that of banking trojan infections.
Another interesting study published by Bitdefender give us further information to understand the impact of ransomware in the criminal underground. Below the Key findings of the report:
-
Half of the users can't accurately identify ransomware
-
Half of the victims are willing to pay up to $500 to recover encrypted data. This means according to the graph below; there are nearly 200K infected users. If half of them pay 500 USD, it makes a total of 50,000,000 USD!
-
Personal documents rank first among user priorities.
-
UK consumers would pay most to retrieve files.
-
US users are the main target for ransomware.
One of the most interesting aspects of ransomware campaigns is that they could also be very profitable for small gangs without specific skills.
The researchers from the security firm Flashpoint have been following a ransomware-as-a-service campaign operated by a Russian gang since December 2015.
They tracked the activities of a small gang, from the constitution of the group until the cashout. The experts followed the payment processes, the recruitment of new members for specific tasks, and the distribution of the malware to profile the group and understand the return on investment.
The Flashpoint researchers identified the leader of the gang (the boss), a cyber criminal active since at least 2012; then they observed how he hired other members to organize the ransomware campaign.
"Based on our coverage of the Deep & Dark Web, this particular ransomware crime boss has been active since at least 2012. His primary institutional targets have included corporations and individuals in various Western countries. Based on multiple indicators, it appears that the ransomware boss operates out of Russia." states the report published by FlashPoint.
The boss recruited people with the promise of sharing the profits from his campaign; he has chosen low-level cybercriminals without specific coding skills to help him reaching out to users in the Russian underground on the Deep Web.
"This offer is for those who want to earn a lot of money via, shall we say, not a very righteous path. No fees or advance payments from you are required, only a large and pure desire to make money in your free time," states the recruitment notice. It is desirable, of course, that you have already had some minimal experience in this business. But if you have no experience, it is not a problem. In addition to the file, you will receive detailed instructions on how and what to do – even a schoolboy could do it; you need only time and desire."
The leader recruited from 10 to 15 affiliates that supported him in spreading the ransomware via:
-
Botnet installs
-
Email and social media phishing campaigns
-
Compromised dedicated servers
-
File-sharing websites
The gang requested the victims a payment of a $300 fee to rescue to encrypted files, the communications with the victims are handled directly by the boss.
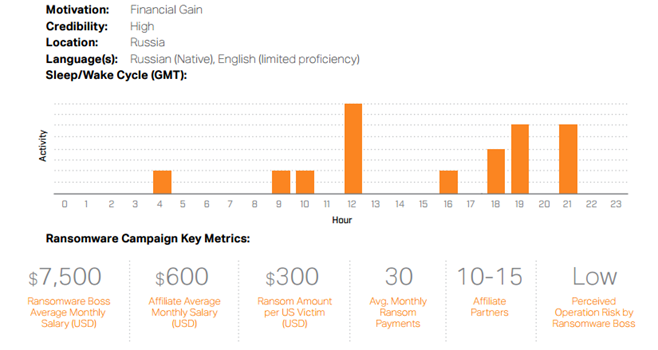
Figure 2 - Statistics Ransomware Campaigns (FlashPoint)
The gang requested the payment in Bitcoins and laundered the money via Bitcoin exchanges.
The boss compensated the affiliates with 40 percent of the ransom keeping for himself the rest.
The researchers followed the payments discovering that at least 30 ransom were paid by victims, netting the boss around $90,000 a year and his affiliates an average $600 a month depending on their abilities to spread the ransomware. Larger ransomware gangs will trouser far larger sums, of course, as much as $90,000 a week or more.
The data are very interesting if we consider that larger organization can earn larger sums, more than hundreds of thousands of dollars per month.
Below the key findings shared by the security firm:
-
From the ransomware affiliate perspective, such campaigns have significantly lowered the barriers to entry for low-tier Russian cyber criminals.
-
Ransomware revenue amounts are not as glamorous and fruitful as they are often publicly reported. Average ransomware crime bosses make only $90K per year on average.
-
Our findings dispute the common perceptions of cyber criminals as being larger-than-life, smart, well off, unreachable, undoable, and unstoppable. The report provides the complete payout structure and Bitcoin laundering operation related to the ransomware-as-a-service campaign
-
The report provides the complete payout structure and Bitcoin laundering operation related to the ransomware-as-a-service campaign.
93% of phishing emails are now ransomware
The emails are a privileged vector for spreading ransomware, and the rapid diffusion of this family of malware was also noticed by security firms that monitor phishing campaigns in the wild. The anti-phishing company PhishMe published a report that confirms this trend, according to this study, as of the end of March, 93 percent of all phishing emails contained a ransomware.
Experts from PhishMe observed the overall phishing emails reached 6.3 million in Q1 2016, a 789 percent increase over the same period of 2015; most worrisome is the fact that 51 percent of all malicious messages in March were used to spread ransomware, an increment respect February of 29 percent and 15 percent in January.
"Thus far in 2016, we have recorded an unprecedented rise in encryption ransomware attacks, and we see no signs of this trend abating. Individuals, small- and medium-sized businesses, hospitals, and global enterprises are all faced with the reality that this is now one of the most favored cyber criminal enterprises," explains Rohyt Belani, CEO, and Co-Founder of PhishMe.
The data is not surprising if we consider that in the criminal underground are proliferating ransomware-as-a-service platforms that allow cybercriminals to easily and quickly arrange a ransomware campaign.
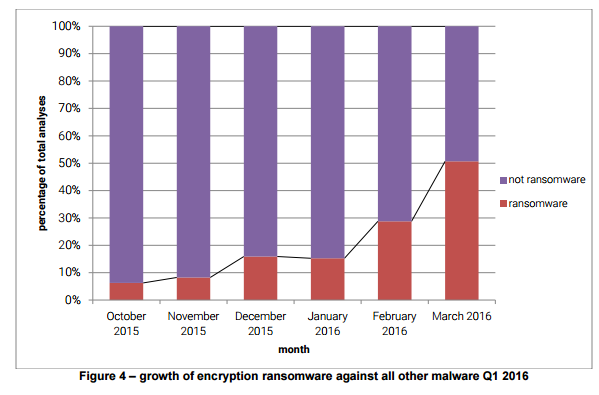
Figure 3 -Growth of Ransomware against all other malware in Q1 2016 (Source PhishMe Report)
Another advantage of ransomware campaign is that they are easy to organize and don't request specific effort to be managed, the sale of stolen payment card data, for example, it needs a different level of organization especially of the sale of the card.
Giving a close look to the type of ransomware spread by threat actors, it is possible to verify a significant decrease of the CryptoWall threat respect October and November 2015. Meanwhile, Locky and TeslaCrypt are becoming the most popular families of ransomware in the criminal ecosystem.
In March, nearly 75 percent of all samples were Locky ransomware samples.
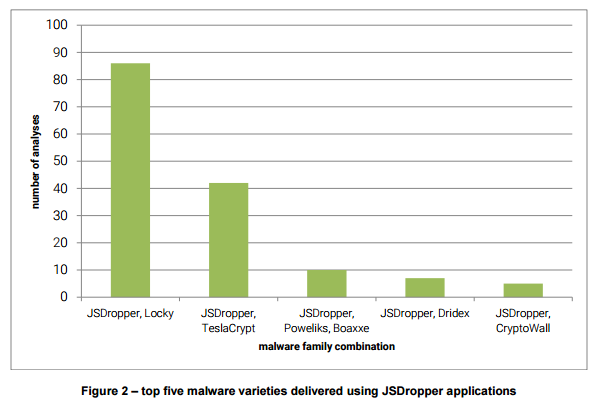
Figure 4 -Top, five malware varieties, delivered via JSDropper apps (Source PhishMe Report)
Conclusion
Ransomware is a dangerous threat for both SMBs and enterprises, a growing number of bad actors are entering in the cyber arena attracted by the easy and rapid profits.
The criminal underground is following this trend offering new services to support criminal gangs without specific technical skills. We are assisting to the rapid diffusion of the ransomware-as-a-service model in the criminal ecosystem, and a growing number of actors are offering any services for spreading the kind of threat.
Without awareness and a proper security posture, the number of ransomware infections will increase in the next months.
References
http://securityaffairs.co/wordpress/47890/malware/self-propagating-ransomware.html
http://securityaffairs.co/wordpress/47990/cyber-crime/ransomware.html
http://securityaffairs.co/wordpress/47696/malware/economic-considerations-nuclear-ek.html
https://resources.infosecinstitute.com/ransomware-in-the-wild-its-an-emergency/
https://blogs.technet.microsoft.com/mmpc/2016/05/26/link-lnk-to-ransom/
http://phishme.com/phishme-q1-2016-malware-review/
http://phishme.com/phishme-q1-2016-malware-review/

FREE role-guided training plans
http://www.csoonline.com/article/3077434/security/93-of-phishing-emails-are-now-ransomware.html









