Security Awareness & Training Resource Center
Featured content

Deconstructing Human-Element Breaches | Infosec HRM
Human risk management isn’t just rebranded SA&T — it’s a profound change of mindset, strategy, process and technology that approaches human-related breaches in a new way.
![Inside an Infosec Boot Camp: All your questions, answered! [replay]](/globalassets/is-wb-24-05-inside-an-infosec-boot-camp_thumbnail2.webp?width=338&height=304&rmode=Max&bgcolor=transparent)
Inside an Infosec Boot Camp: All your questions, answered!
You need to get certified, but is an Infosec Boot Camp the right choice for you — or your team? Find out in this live Q&A with two Infosec instructors.

Emerging trend checklist: Which certifications cover which new skills?
Boost your team's cybersecurity skills with the right certifications. Discover the most in-demand skills and the certifications that cover them in our free guide.

Security Awareness Outcomes with Infosec IQ
See security awareness and training outcomes from more than five million Infosec IQ learners.
Our resources

Expected Ransomware Evolution in Coming Years

German Intelligence First Developed Attacks Against Tor

How to draft an incident response policy

Innovative Methods of Information Security Training

8 tips for IT certification success

Equifax Breach Exposes Personal Information of 44% of U.S. Consumers

DragonFly 2.0: The Alleged Nation-State Actor Hits the Energy Sector Again

Russian APT Groups Continue Their Stealthy Operations

Acid Server: CTF Walkthrough

Average Network Security Administrator Salary
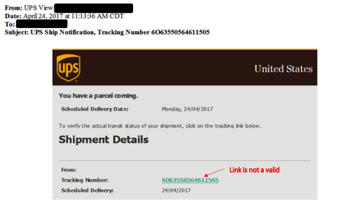
Top 10 Anti-Phishing Best Practices
Intelligent Personal Assistant (IPA) Sample Security Policy

OWASP Top 10 #9: Using Components With Known Vulnerabilities

Anti-Phishing Laws & Regulations

Anti-Phishing Services: Pros and Cons

Anti-Phishing Hardware & Software

Top 5 Questions to Ask Your Vendors about Their Security Policies

Security Awareness Statistics
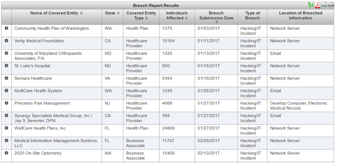
What Kind of Security Training Does HIPAA Say I Need to Provide?

PCI Security Awareness: Who Needs Training and Compliance?

Security Awareness Compliance Requirements: Understanding Regulatory Mandates

Managing Wireless Network Security

Security Awareness for Sales Representatives
Top 10 Threats from Unprotected Intelligent Personal Assistants (IPAs)