Vulnerabilities

Vulnerabilities
What happens when your phone provider is hacked? That’s what AT&T customers are facing. Learn how to keep yourself and your organization safe.

January 15, 2025
Jeff Peters
Vulnerabilities
A warning was issued about a recent iPhone vulnerability that could bypass pointer authentication. Learn about vulnerability and how it affects you.

January 15, 2025
Jeff Peters
Vulnerabilities
Binary exploitation and techniques during stack exploitation.

November 29, 2023
Pedro Tavares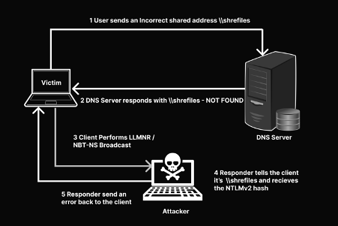
Vulnerabilities
Active Directory (AD) networks are insecure by default. Learn how you can perform an Active Directory assessment to identify and secure any weaknesses.

November 17, 2023
Pedro Tavares
Vulnerabilities
Find out why CISA mandated vulnerability scanning and the role asset visibility plays in ensuring that security threats are detected.

September 15, 2023
Drew Robb
Vulnerabilities
Learn about the dangers web shells have on Digium phones.

September 27, 2022
Pedro Tavares
Vulnerabilities
Lazarus' advanced persistent threat (APT) operations use malware specially crafted for attacking financial institutions, espionage, and disruptive purposes.

August 30, 2022
Pedro Tavares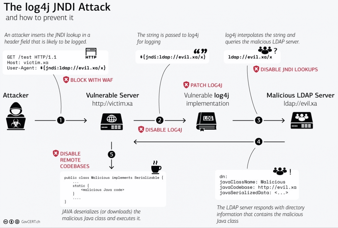
Vulnerabilities
This article will spotlight some of the most dangerous vulnerabilities that threat actors exploited in the first half of 2022.

August 17, 2022
Pedro Tavares
Vulnerabilities
Microsoft tracked as CVE-2022-30190 a new vulnerability, also called “Follina,” that leverages Microsoft Office to lure victims and execute code without thei

August 11, 2022
Pedro Tavares
Vulnerabilities
Spring4Shell is a remote code execution vulnerability (CVSS 9.8) published at the end of March 2022 that impacts Spring Framework.

August 10, 2022
Pedro TavaresIn this series
- AT&T data breach: What happened and how to protect your organization
- Bypassing pointer authentication: Understanding the 2024 iPhone attack
- The most popular binary exploitation techniques
- Roadmap for performing an Active Directory assessment
- The importance of asset visibility in the detection and remediation of vulnerabilities
- Digium Phones Under Attack and how web shells can be really dangerous
- vSingle is abusing GitHub to communicate with the C2 server
- The most dangerous vulnerabilities exploited in 2022
- Follina — Microsoft Office code execution vulnerability
- Spring4Shell vulnerability details and mitigations
- How criminals are taking advantage of Log4shell vulnerability
- Microsoft Autodiscover protocol leaking credentials: How it works
- How to write a vulnerability report
- How to report a security vulnerability to an organization
- PrintNightmare CVE vulnerability walkthrough
- Top 30 most exploited software vulnerabilities being used today
- The real dangers of vulnerable IoT devices
- How criminals leverage a Firefox fake extension to target Gmail accounts
- How criminals have abused a Microsoft Exchange flaw in the wild
- How to discover open RDP ports with Shodan
- Time to patch: Vulnerabilities exploited in under five minutes?
- Whitespace obfuscation: PHP malware, web shells and steganography
- Turla Crutch backdoor: analysis and recommendations
- Volodya/BuggiCorp Windows exploit developer: What you need to know
- AWS APIs abuse: Watch out for these vulnerable APIs
- How to reserve a CVE: From vulnerability discovery to disclosure
- SonicWall firewall VPN vulnerability (CVE-2020-5135): Overview and technical walkthrough
- Top 25 vulnerabilities exploited by Chinese nation-state hackers (NSA advisory)
- Zerologon CVE-2020-1472: Technical overview and walkthrough
- Unpatched address bar spoofing vulnerability impacts major mobile browsers
- Software vulnerability patching best practices: Patch everything, even if vendors downplay risks
- What is a vulnerability disclosure policy (VDP)?
- Common vulnerability assessment types
- Common security threats discovered through vulnerability assessments
- Android vulnerability allows attackers to spoof any phone number
- Malicious Docker images: How to detect vulnerabilities and mitigate risk
- Apache Guacamole Remote Desktop Protocol (RDP) vulnerabilities: What you need to know
- Linux vulnerabilities: How unpatched servers lead to persistent backdoors
- Tesla Model 3 vulnerability: What you need to know about the web browser bug
- How to identify and prevent firmware vulnerabilities
- Will CVSS v3 change everything? Understanding the new glossary
- URGENT/11 vulnerability
- 32 hardware and firmware vulnerabilities
- The Zero Day Initiative
- CVE-2018-11776 RCE Flaw in Apache Struts Could Be Root Cause of Clamorous Hacks
- XML vulnerabilities are still attractive targets for attackers
- Broadpwn Wi-Fi Vulnerability: How to Detect & Mitigate
- Mobile Systems Vulnerabilities
- 10 Security Vulnerabilities That Broke the World Wide Web in 2016
- Most Exploited Vulnerabilities: by Whom, When, and How
Get certified and advance your career!
- Exam Pass Guarantee
- Live instruction
- CompTIA, ISACA, ISC2, Cisco, Microsoft and more!
