VERIS INCIDENT FRAMEWORK
The VERIS methodology was created by Verizon back in 2010. This was an effort to create an environment for the classification of specific information.
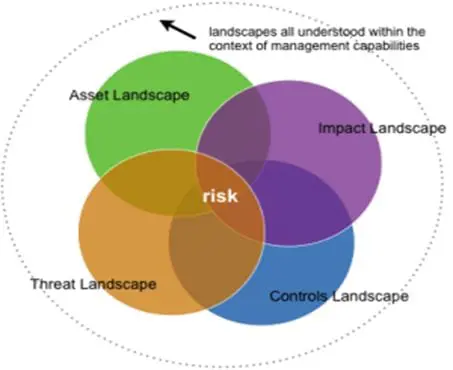
The VERIS model is applied through the process of collecting different data points that separate various sections of security incidents, which are as follows:
Become a certified threat hunter
- The incident threat landscape;
- The Impact landscape;
- The control landscape and asset landscape
This is illustrated in the diagram below:
Veris uses the A4 threat model for the information gathering process, to understand the unique characteristics which can be pointed out. These are described as follows:
- Actors: Which actions affected the asset? This is used to determine the main source of the security threat.
- Actions: What kind of actions affected the asset? This determines the impact of specific actions that were detected by the performance state of the asset.
- Assets: What assets were directly harmed? This serves to manage the amount of damage that the assets actually receive.
- Attributes: Which characteristics affect the assets? This section defines the characteristics of the security incidents which negatively impact the assets.
There are also other sections in the Veris model that further define the structure of the security incidents. These are as follows:
Victim Analysis:
This creates an environment that can be used to describe the level and magnitude of the security incident that occurs from within an organization. It can also be used to identify which department has been impacted the most. This analysis is also utilized to create a priority scheme to list the security characteristics that are deemed to be the most important for the business or corporation.
Actor Analysis:
This creates a method to discover the source of the security incidents that take place in an organization. VERIS can also further evaluate the size and impact of them as well.
Event Analysis:
The section represents the scale and importance of each element inside the VERIS environment. It also reviews the magnitude and impact of the various security incidents that occur in an organization, and the frequency of them.

Action Analysis:
This section defines the origin of the specific threats to a business stemming from the following:
- Hacking;
- Social media misuse;
- Errors in the source of the various applications that are deployed and utilized;
- Malware;
- Unknown vulnerabilities in the IT environment.
Asset and Attribute analysis:
The assets are defined as the resources that are impacted by any kind of security breach. They include the following:
- Technology equipment;
- Personal (employee) information;
- The integrity and authenticity of customer information.
Impact Analysis:
The impact characteristics measure the degree of the security incidents that actually occur. The VERIS structure provides different tools to calculate this, using these three criteria:
- The categorization of the loss experience;
- The estimation of the magnitude of impact;
- The evaluation of the overall effect upon the entire organization.
Response Analysis:
This section serves as a guide for analyzing future security threats (both internal and external) to the organization, and it also provides various methods to counter them effectively.
Conclusion:
The VERIS framework is a sophisticated vehicle in which to classify security incidents to prevent them from occurring into the future. It also creates a record of the IT assets, whether they are tangible (such as hardware/software) or intangible (such as intellectual property).
It also serves as a vehicle to help protect the CIA triad of mission-critical information and data that belongs to an organization.
References:
http://veriscommunity.net/veris-overview.html
http://www.verizonenterprise.com/verizon-insights-lab/VES/veris-incident-classification-mindmap
https://github.com/vz-risk/veris/wiki/VERIS-Overview
Become a certified threat hunter
http://searchsecurity.techtarget.com/definition/Verizon-VERIS-Vocabulary-for-Event-Recording-and-Incident-Sharing-Framework








