Foreign Hackers Constantly Target US Critical Infrastructure
US critical infrastructure under attack
US authorities are warning companies operating in every industry of a significant increase in the number of cyber attacks that target US critical infrastructures every day.
State-sponsored hackers and cyber criminals are constantly targeting control systems and other vital components present into critical infrastructures. The energy and financial industries are within the most targeted sectors. The Department of Homeland Security (DHS) has already issued several alerts on the risk of cyber attacks explaining that national systems are constantly under attack.
Recently, the Department of Homeland Security (DHS) revealed that Russian hackers have infiltrated networks at several critical infrastructure of the country, explaining that foreign hackers are continuously probing US networks for cyber espionage and sabotage purposes.
The US-CERT reported that during the fiscal year of 2014, there were 79 hacking incidents at energy companies. The number of attacks detected in the previous year was 145. The numbers are probably not indicative of the phenomena; in many cases the attackers adopting sophisticated evasion techniques are able to avoid detection for a long period. Many of the attacks are difficult to detect, and often ATP groups are able to operate in the shadows for years before being discovered.
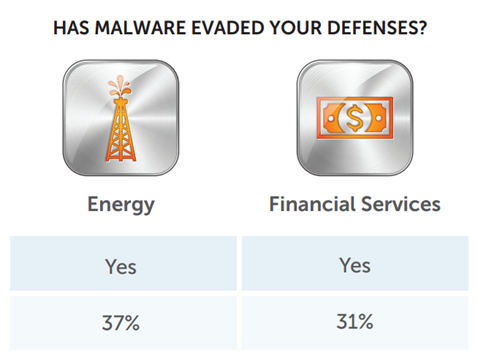
According the results of a survey by ThreatTrack Security, between April 2013 and 2014 bad actors hit 37% of energy companies, evading defenses deployed by the targeted organizations. In the majority of the cases (58%), the attackers deployed highly sophisticated malware to compromise the systems, and email was the top threat vector, followed by Web exploits.
"The survey found that 35% of respondents reported endpoints on their network had been infected by malware that evaded their defenses during the last 12 months. Moreover, 58% of respondents cited the complexity of malware as the most difficult aspect of defending their organization," reports the survey, highlighting the difficulties of tracking the threats due to their level of sophistication. "Respondents within the energy sector (37%) reported a 6% higher rate of infection than their financial services counterparts."
Figure 1 - ThreatTrack Survey Results
Security experts at FireEye confirmed the massive offensive against the US energy industry. The company has identified nearly 50 strains of malware that was specifically designed to target energy companies in 2013.
According the annual report published by FireEye, energy firms were mainly hit by spyware and RATs. For example, the most common vertical targets of Dark Comet operations in 2013 were financial services, energy/utilities, and education.
According to the experts, almost every attack detected against the US critical infrastructure was conducted for long-term cyber espionage campaigns. The information gathered during these years by foreign hackers allowed them to collect a huge amount of data that could be used in future cyber attacks. Principal activities run by threat actors through a hacking campaign uncovered recently are:
-
Discovery of the models of the ICS-SCADA systems and other hardware and software components present in the targeted critical infrastructure.
-
Reverse engineering of the software running in critical components deployed into critical infrastructure. The activity could allow attackers to discover presence of zero-day vulnerabilities in the targeted systems and design specific exploits to use for successive attacks or to compromise other plants.
-
Evaluation of the efficiency of countermeasures deployed by the US government to mitigate the cyber threats.
-
Information gathering on the patch management process adopted by the staff of the single infrastructure. This information is crucial in case of attack to estimate the window of exposure of the targets.
The Havex malware
This year, researchers at CrowdStrike security firm investigated several attacks that hit companies operating in the energy sector. The threat actors spread a variant of the Havex Remote Access Trojan (RAT) that uses a server written in PHP.
Figure 2 - Havex Source Code
"This adversary uses two primary implants: one dubbed HAVEX RAT by CrowdStrike and another called SYSMain RAT. These implants are closely related with several TTP overlaps and clear code reuse, particularly within secondary tools associated with the HAVEX RAT. It is possible that the HAVEX RAT is itself a newer version of the SYSMain RAT, although both tools are still in use concurrently and have been operated by the attackers since at least 2011. The investigation into this actor uncovered more than 25 versions of the HAVEX RAT, with build times up to October 2013. Each version will install itself as DLL with a name beginning 'TMPprovider', such as TMPprovider037.dll for version 37," reported the company blog post.
In June, a group of experts at F-Secure investigated different strains of the Havex malware that were used in the previous months in several targeted attacks against different industries.
Researchers at F-Secure noticed that Havex was used by attackers to hit Industrial Control Systems (ICS). The criminal crews behind the hacking campaigns customized the RAT infecting software available for download from ICS/SCADA manufacturer websites in an attempt to infect the computers where the software is installed.
According to the investigators, the level of sophistication of the attacks was high. The attackers conducted surgical offensives implementing a "watering-hole attack" scheme that involved ICS vendor sites as an intermediary target. The SCADA vendors targeted by the Havex campaign are based in Germany, Switzerland and Belgium. Two of them are suppliers of remote management software for ICS systems, and the third one develops high-precision industrial cameras and related software.
"Our research uncovered three software vendor sites that were compromised in this manner. The software installers available on the sites were trojanized to include the Havex RAT. We suspect more similar cases exist but have not been identified yet…Our research uncovered three software vendor sites that were compromised in this manner. The software installers available on the sites were trojanized to include the Havex RAT. We suspect more similar cases exist but have not been identified yet," states F-Secure.
The Havex RAT infections were spread exploiting one the following attack vectors:
-
Trojanized installers planted on compromised vendor sites
The researchers at F-Secure speculated that attackers used the Havex RAT for reconnaissance operations. The attackers included in the malware code a data-harvesting component used to gather information on the targeted ICS/SCADA systems and the surrounding system deployed in the targeted infrastructure.
The malware experts at F-Secure detected 88 different instances of Havex RAT used to compromise networks hosting ICS systems. The company analyzed 146 Command and Control (C&C) servers and traced nearly 1500 IP addresses used in the hacking campaign. The infections are mainly located in Europe, the list of victims includes educational institutions, industrial application or machine producers and companies specialize in structural engineering.
Once it has infected the targeted system, the trojanized software installer will drop and execute the malicious code that allows the attackers to install a backdoor to gain complete control of the PC. Experts have no doubts that the recently uncovered use of Havex is part of an industrial espionage campaign, which exploited a trojanizing version of ICS/SCADA software installers. A particular detail that caught the attention of experts is that the attackers managed the Command & Control infrastructure, revealing lack of experience in operations.
"The additional payload used to gather details about ICS/SCADA hardware connected to infected devices shows the attackers have direct interest in controlling such environments. This is a pattern that is not commonly observed today."
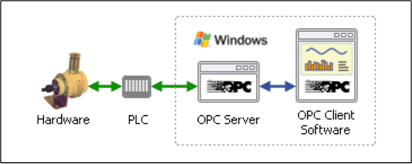
It has been estimated that the number of compromised energy companies in the US and Europe is nearly 1000, an impressive number that gives us an idea of the impact of the Havex operation. Security experts detected many variants of the Havex malware in the wild. FireEye detected a new variant of the Havex RAT that implements a function to scan OPC (Object linking and embedding for Process Control) systems. The RAT collects system information and data directly from targeted machines through the OPC standard. In industrial scenarios, ICS or SCADA systems includes OPC client component that exchanges data with OPC server, which communicates with a PLC (Programmable Logic Controller) to control industrial hardware.
"The OPC is a software interface standard that allows Windows programs to communicate with industrial hardware devices," states the OPC datahub.
The feature allowed the attackers to gather any data stored on the machines in the targeted networks and details about the connected devices. The information collected was sent back to the Command and Control server.
Figure 3 - SCADA OPC Interface
"Threat actors have leveraged Havex in attacks across the energy sector for over a year, but the full extent of industries and ICS systems affected by Havex is unknown," "We decided to examine the OPC scanning component ofHavex more closely, to better understand what happens when it's executed and the possible implications," blogged Kyle Wilhoit, threat intelligence researcher at FireEye.
Security experts believe that the new variant of Havex RAT is an excellent tool for intelligence. This instance of the RAT didn't present any component that could be used by attackers for sabotage.
Russian BlackEnergy malware targeting critical infrastructure
Recently a new version of the Russian malware BlackEnergy was discovered in the wild by experts at ESET. BlackEnergy is a popular DDoS Trojan that gained notoriety in 2008 when it was reported to have been used during the Russia-Georgia conflict. The malicious code was in fact used to launch cyber attacks against the infrastructure of Georgia. The new variant was used in targeted attacks on government entities and private companies across a range of industries.
According to the report proposed by experts at ESET, the new strain of malware has been found targeting more than 100 government and industry organizations in Poland and the Ukraine, and according to F-Secure, another attack hit the European Parliament or European Commission in Brussels, Belgium.
Recently government officials reported to the ABC News agency that hackers have compromised systems in many US critical infrastructures. Bad actors compromised the software that runs in the critical infrastructure with a malware. The circumstance creates a lot of anxiety in the intelligence and military sectors. Government sources reported to the news agency that the attacks appear to be part of a state-sponsored hacking campaign.
According to the sources, Russia is the nation that is coordinating them against US infrastructure in order to gather sensitive information on the targets.
"A destructive 'Trojan Horse' malware program has penetrated the software that runs much of the nation's critical infrastructure and is poised to cause an economic catastrophe, according to the Department of Homeland Security. National Security sources told ABC News there is evidence that the malware was inserted by hackers believed to be sponsored by the Russian government, and is a very serious threat," reports ABC News.
The Department of Homeland Security (DHS) has recently disclosed the news that critical infrastructure entities in the U.S. have been systematically targeted by a malware based campaign since 2011. The alert comes a few weeks after another security advisory issued by the US ICS-CERT on the BlackEnergy malware; the organization alerted on a series of cyber attacks which compromised industrial control systems at several national facilities.
"ICS-CERT has identified a sophisticated malware campaign that has compromised numerous industrial control systems (ICSs) environments using a variant of the BlackEnergy malware. Analysis indicates that this campaign has been ongoing since at least 2011," the advisory stated.
"Multiple companies working with ICS-CERT have identified the malware on Internet-connected human-machine interfaces (HMIs).
"ICS-CERT has determined that users of HMI products from various vendors have been targeted in this campaign, including GE Cimplicity, Advantech/Broadwin WebAccess, and Siemens WinCC. It is currently unknown whether other vendor's products have also been targeted. ICSCERT is working with the involved vendors to evaluate this activity and also notify their users of the linkages to this campaign."
The experts at ICS-CERT confirmed that it has not detected any attempts to "damage, modify, or otherwise disrupt the victim systems' control processes." Anyway, security experts are aware that due to the modular structure of this kind of malware, a threat actor would be able to drop a further malicious payload to use for sabotage purpose.
"However, typical malware deployments have included modules that search out any network-connected file shares and removable media for additional lateral movement within the affected environment. The malware is highly modular and not all functionality is deployed to all victims," the ICS-Advisory stated.
In a recent interview that I released to the Bloomberg agency, I commented the fact that these attacks apparently haven't caused any damage:
"Whatever they were up to, the cyber-infiltrators didn't use the digital weapons they'd planted to do any damage … This suggests that attackers are collecting detailed information on systems and processes running the vital infrastructure of the U.S.…to coordinate further attacks."
As reported by security firm involved in the investigation, the hacking campaign has been running at least since 2011, but no sabotage act has been observed since now. The circumstance suggests that attackers are collecting detailed information on systems and processes running on the vital infrastructure of the US. It is my opinion that the attacks are coordinated by a so called persistent collector that is acquiring data to coordinate further attacks.
The information collected during these years by foreign hackers allowed them to gather precious information to mount further attacks.
The energy industry and many other industries as a result are particularly vulnerable to cyber attacks due to the lack of security by design for the majority of the equipment and machineries they use. Several Industrial Control Systems were designed to operate alone, without having security in mind, and in a scenario completely different from the actual, in which the threats are completely different.
The fear of possible major attacks against the energy industry was also highlighted recently by NSA director Admiral Mike Rogers during the power grid security conference in San Antonio, Texas in October.
"Power… is one of the segments that concerns me the most," he said, according to a transcript obtained by CNNMoney explaining that the energy and power infrastructure were not designed to be resilient to today's cyber attacks.
The US government started an awareness campaign that is involving the authorities, including DHS and FBI, and national energy providers and utility companies. The intent is to discuss the threats and improve the security of the infrastructure with a series of specific countermeasures.
Dragonfly gang is targeting Western energy industry
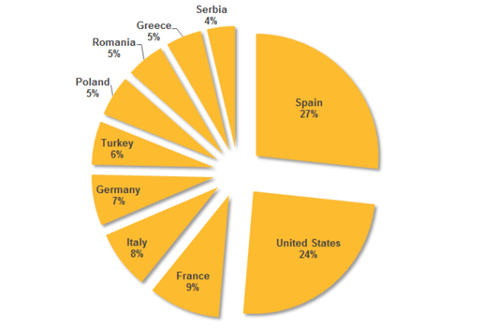
As revealed by the last alert issued by the US ICS-CERT, US infrastructure is continuously under attack. In reality, the systems all around the world are under constant pressure by state-sponsored hackers and cybercriminals. In July, researchers at Symantec discovered a hacking campaign targeting organizations located in the US, Italy, France, Spain, Germany, Turkey, and Poland. The experts identified the perpetrators behind the attacks as the "Dragonfly" gang.
Figure 4 – Dragonfly gang's Victims
The Dragonfly gang, also known by other security firms as Energetic Bear, seems to be operating since at least 2011 when it targeted defense and aviation companies in the US and Canada. In a second phase, Dragonfly focused its efforts on US and European energy firms in early 2013.
Symantec immediately reported the results of its investigation to the targeted organizations and by national authorities, including Computer Emergency Response Centers (CERTs).
"The attackers, known to Symantec as Dragonfly, managed to compromise a number of strategically important organizations for spying purposes and, if they had used the sabotage capabilities open to them, could have caused damage or disruption to energy supplies in affected countries," states a blog post from Symantec.
The Dragonfly crew once again focused its efforts against energy grid operators, major electricity generation firms, petroleum pipeline operators, and energy industry industrial equipment providers.
The group operated with the primary intent to gather intellectual properties and other sensitive information. Its members adopted different attack vectors, including watering hole attacks, spear-phishing emails and trojanized ICS software updates like the case of Havex RAT.
Experts at Symantec revealed that Dragonfly crew was well resourced. Its members used several hacking tools during the campaigns. The two main malware used by attackers are the Backdoor.Oldrea and the Trojan.Karagany.
"Its most ambitious attack campaign saw it compromise a number of industrial control system (ICS) equipment providers, infecting their software with a remote access-type Trojan. This caused companies to install the malware when downloading software updates for computers running ICS equipment. These infections not only gave the attackers a beachhead in the targeted organizations' networks, but also gave them the means to mount sabotage operations against infected ICS computers," states Symantec.
The experts believe that the Dragonfly gang was mainly interested in data exfiltration from targeted industrial systems. The motivation for such attacks is still unclear, but the Symantec team suspects that behind Dragonfly there are state-sponsored hackers and that the hacking campaign uncovered is just the tip of the iceberg.
Conclusion
In recent weeks, different attacks hit US government entities; networks at the State Department, at the US Postal Service systems, and at the White House were compromised by foreign hackers. In all these cases, the security experts blamed state-sponsored hackers, explaining that cyber espionage activities represent a serious element of concern for the national intelligence.
China, Russia, North Korea, and Syria are countries with significant cyber capabilities that have necessary skills and equipment to organize a major attack against US critical infrastructure.
Admiral Mike Rogers, the director of the U.S. National Security Agency, confirmed that "probably one or two" countries represent a danger for the country due to their capabilities to infiltrate US networks and shut down critical systems.
Admiral Rogers stated that vital components of the U.S. infrastructure are privileged targets of state-sponsored hackers, including power utilities, telecommunication networks, aviation networks, financial companies, and energy firms.
Speaking to the House of Representatives Intelligence Committee about cyber threats, Rogers explained that threat actors can penetrate national systems to gather sensitive data in a "reconnaissance" activity, and data collected could be used in successive attacks.
"What concerns us is that access, that capability can be used by nation-states, groups or individuals to take down that capability," he said.
Rogers explicitly refers to China as one of the countries that can compromise US infrastructure.
"There's [sic] probably one or two others," Rogers said, declining to provide further comments.
As concern about data breaches continues to grow, the US industry remains vulnerable to advanced cyber threats. The overall U.S. economy also depends on the capability of the government to secure its critical infrastructure.
The US government is considering the defense of critical infrastructure from cyber threats a primary goal for its polities.
It's time to consider security by design for any applications and components to use in vital systems.
References
http://securityaffairs.co/wordpress/30328/cyber-crime/cyber-attacks-energy-industry.html
http://securityaffairs.co/wordpress/26092/cyber-crime/cyber-espionage-havex.html
http://securityaffairs.co/wordpress/26778/cyber-crime/havex-variant-opc.html
http://securityaffairs.co/wordpress/26273/cyber-crime/dragonfly-gang-energy-industry.html
http://securityaffairs.co/wordpress/28582/cyber-crime/blackenergy-lite-targeting-eu.html
http://blog.norsecorp.com/2014/11/13/blackenergy-malware-hit-us-critical-infrastructure/
https://ics-cert.us-cert.gov/alerts/ICS-ALERT-14-281-01A
http://www.symantec.com/connect/blogs/dragonfly-western-energy-companies-under-sabotage-threat
http://securityaffairs.co/wordpress/29210/security/ics-cert-report-may-aug-14.html
http://www.fireeye.com/blog/technical/targeted-attack/2014/07/havex-its-down-with-opc.html
http://abcnews.go.com/US/trojan-horse-bug-lurking-vital-us-computers-2011/story?id=26737476
https://www.f-secure.com/weblog/archives/00002718.html
http://www.bloombergview.com/articles/2014-11-13/under-attack-your-bank-your-grid-yourself