ICS/SCADA Access Controls
Industrial controls systems (ICS) and supervisory control and data acquisition (SCADA) systems (a subset of ICS) manage our critical national infrastructure. Controlling logical access to these systems is not easy, given their often-distributed nature and the large number of employee and support roles needing access.
Learn ICS/SCADA Security Fundamentals
This article provides an overview of ICS logical access management challenges and ways to meet them, including network segmentation, risk-based access control and context-aware authentication and authorization.
Definitions
Before we continue, it is essential to understand the concepts and terms used in ICS (Stouffer, Pillitteri, Lightman, Abrams, & Hahn, 2015).
- Industrial control system (ICS): Using an array of technology and protocols, ICS controls include management of
- Industrial processes
- Delivery of electricity
- Delivery of water
- Processing of wastewater
- Delivery of natural gas
- Supervisory control and data acquisition (SCADA): A subset of ICS, SCADA is used to manage distributed systems, such as
- Water distribution
- Electrical utility transmission
- Rail and other public transportation
- Oil and natural gas pipelines
- Human-machine interface (HMI): The HMI is the interface used by humans to interact with ICS and SCADA systems and devices. It is the portal to the ICS/SCADA supervisory computers used for monitoring and control
Challenges
To ensure covering both ICS and SCADA, let’s imagine an example. The headquarters building includes a business office network, a business data center and the ICS network. The cloud represents the various ways an ICS organization might communicate with controls at distributed locations.
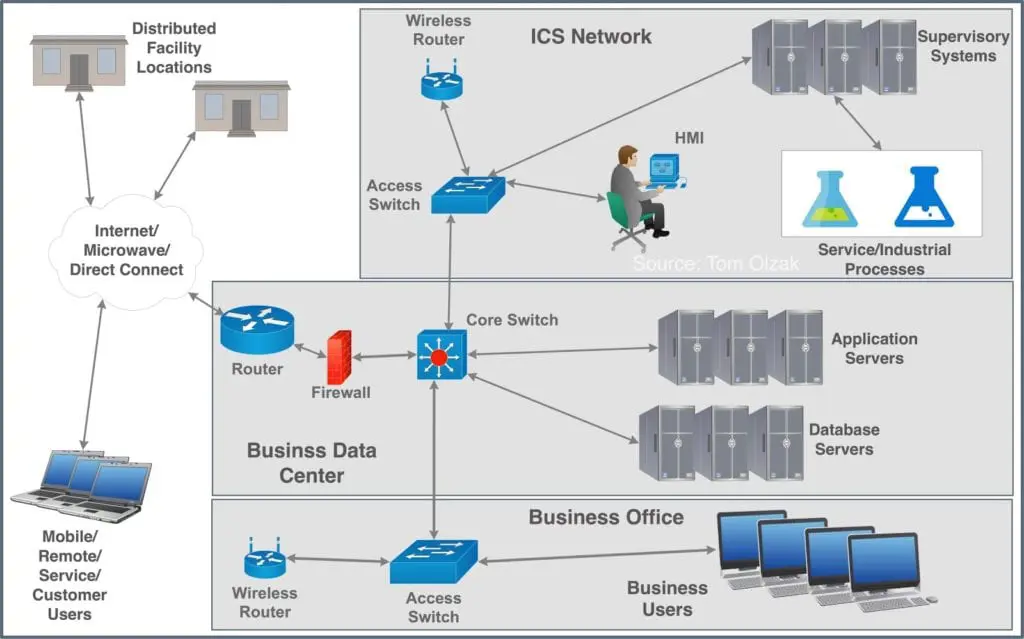
The networks are all connected via a core switch and all are potentially available to the internet. This can make the ICS and SCADA systems susceptible to cyber-intrusions started on remote or local user devices. This is a significant access control challenge associated with employees. However, this is not the biggest challenge.
Critical infrastructure requires access by a variety of roles: both internal and external. They include (Center for the Protection of National Infrastructure, 2010):
- System operators and engineers for local systems
- System operators and engineers for remote systems
- Vendors
- System integrators
- System support specialists and maintenance engineers
- Field technicians
- Business partners
- Reporting or regulatory entities
- Customers
- Supply chain representatives
- Managed service providers
Logical access control must address how these roles access resources, what resources what they can see, what accessed resources can see each other, the risk of user/device context during sessions and other considerations.
ICS access control
Meeting the challenges above requires three approaches to access control: segregation, context-based policy enforcement and strong authentication.
Segregation
The first step in controlling ICS access is isolation. Organizations should segregate ICS and SCADA networks from the office network and the internet. We do this with technologies like VLANs, VxLANS and software-defined perimeters. When possible, physical separation is preferred.
Separation is important because one of the most popular methods of malicious access is targeting employees and IoT devices. For this reason, business user workstations and IoT devices should have no access to the ICS network.
Context-based policies
Given the number of remote access needs for ICS management, organizations must understand where and how users are accessing resources. The emerging way to do this involves context-aware access control.
Context includes both the user and the device used: the user/device entity. Users include applications. Context is the collection of user/device characteristics during each session, including:
- Role of the user
- Type of device
- Owner of the device
- Time and day of access
- Resource being accessed
- Location of the user/device
- Health of the device
In this approach, both the user and the device must authenticate, and the health of the device is checked. For remote users, VPN is also needed to ensure the safe transfer of information.
Strong authentication
Access to ICS should include strong authentication. Strong authentication includes at least two authentication factors. However, this is not enough today. We must ensure that user/device contexts continue to meet a level of trust we expect when accessing critical infrastructure. This is particularly true for remote users.
Risk-based authentication helps ensure the continued trust levels of authenticated entities (Olzak, 2018). It includes continuous monitoring of the behavior of the user/device and the device state. If the state changes too far from baselines, additional authentication is required.
All of the access controls above are included in emerging zero-trust network solutions. In zero-trust, we trust nothing and no one. For ICS, this is the way we should look at access control.
Conclusion
ICS infrastructure manages our national critical infrastructure and manufacturing processes. When ICS is compromised, services that continue the healthy operation of the country are subject to interruption.
Authenticated entities must only be able to see ICS resources if directly responsible for managing them. This requires network segmentation, both logically and physically.
Because of the extensive list of roles needed to manage and support ICS, both remote and local, we need zero trust approaches to access control. This begins with establishing and managing user/device trust before and during each session, coupled with multi-factor authentication.
Learn ICS/SCADA Security Fundamentals






