Security+ Domain #1: Network Security (SY0-401) [DECOMMISSIONED ARTICLE]
NOTE: This article reflects an older version of the Security+ Exam – please see the current Security+ Certification page for the most up-to-date information.
Introduction
Network security falls into the first domain of CompTIA’s Security+ exam (SYO-401) and contributes 20% to the exam score. Network security domain provides necessary skills to IT professionals to implement security configuration parameters on network devices, use secure network administration principles, understand network design elements and components, apply common protocols and services, and troubleshoot security issues related to wireless networking.
Implementing Security Configuration Parameters on Network Devices
In a network infrastructure, network devices perform various functions, including network security, network segmentation, and traffic management. In this section, only the security functions of the network devices and other technologies will be discussed.
Firewall—A firewall is used to protect one network from another by managing the network traffic entering and leaving the network. It controls traffic using rules or filters. The three basic types of firewall are:
- Packet filtering
- Circuit-level gateway
- Application-level gateway
The fourth type combines the features of the above three and is called a “stateful inspection firewall.”
Router—it connects various networks and receives/pass the traffic among them. The traffic must be relayed through a router’s filter to make the transition secure.
Switch—This is another network device used to connect other devices and implement traffic management on their communications. Switches are frequently used to connect VLANs.
Load Balancer—This is used to distribute a network’s traffic load across various network devices or network links. Load balancers help to optimize infrastructure utilization, reduce overloading, maximize throughput, minimize response time, and eliminate bottlenecks.
Proxy Server—It is a variation of a circuit-level firewall or an application-level firewall. The proxy server acts as a middleman or proxy between clients and server.
Intrusion Detection System (IDS)—IDS is an automated system that either views activities in real time or analyzes the content of audit logs to detect intrusion.
Network-based IDS (NIDS) and host-based IDS (HIDS)—An NIDS watches a network traffic in real time, while an HIDS watches log files and audit trails of a host system. Furthermore, NIDS detects network-focused attacks, such as a bandwidth-based DoS attack. On the other hand, HIDS detects attacks directed against a host.
Response Method—When an attack is detected, the IDS quickly shuts down the server or disconnects the suspicious connections to minimize the potential damage. Three types of detection methods are used to detect the attacks. These include:
- Behavior-based
- Signature-based
- Anomaly-based
Protocol Analyzer—This is a tool used to analyze the content of network traffic.
Spam Filter—Spam is unsolicited email that contains malicious code. A spam filter is used to block all unwanted spam emails.
Application Aware Devices—these are security devices that include IDS, IPS, proxies, and firewalls.
Give a Scenario and Use Secure Network Administration Principles
To make a secure network, network experts must select the right hardware and software. They also need to configure and maintain the network properly. There are some principles for secure network administration, such as:
Rule-Based Management—This controls the security of communication through a filter-driven system. Examples of rule-based security management tools are firewalls, routers, proxies, IPS, IDS, and antivirus software.
Access Control Lists (ACLs)—ACLs are used to describe who is allowed or denied permission (authorized or unauthorized) to execute a specified activity.
Understand 802.1x—This is a port-based authentication mechanism based on extensible authentication protocol (EAP) and is often used in wireless networks but can also be used in VPN gateways, firewalls, and proxies.
Loop Protection—In networking, a loop is a repeatable transmission pathway. Loop protection includes IP header TTL value and Ethernet.
Implicit Deny—This is a set of predefined rules applied to the by-default granted list that provide access only to authorized resources. Configurations are made by default and, therefore, the access to any new resource will be denied if this resource is not included in the granted list.
Explain Network Design Elements and Components
When a network infrastructure is crafted, it is necessary to understand the various design elements and components. These design elements and components include:
Demilitarized Zone (DMZ)—A DMZ is a network area that is specifically designed for access by public users. In fact, the DMZ acts as a buffer network between the untrusted internet of the public and the private trusted local area network (LAN).
Extranets—An extranet is an intranet that acts as a DMZ specifically for business-to-business (B2B) transactions. By using an extranet, a company can provide specialized services to customers, suppliers, business partners, and distributors.
Subnetting—it’s used in networks to divide large groups of hosts into smaller collections.
Virtual LANs (VLANs)—VLANs are hardware-based solutions that are used to logically segment a network without altering its physical topology.
NAT—An NAT acts as a firewall by hiding the IP structure and its addressing scheme from external users. NAT only allows trusted traffic.
REC 1918—This describes the range of private IP addresses that are not routable across the internet.
Remote Access Server (RAS)—An RAS is a network server used to support connections from remote users. RAS supports VPN links, modem banks, and connections to terminal services.
Telephony—Telephony is a collection of techniques whereby telephone services are provided to organizations. Telephony includes PSTN or POTS services combined with modems, and PBX, VPN, and VoIP.
Network Access Control (NAC)—NAC includes strict security policies controlling internal and external access to the network.
Virtualization—Virtualization technology refers to the act of hosting one or more virtual—rather than actual—guest operating systems, servers, network resources, or storage devices in the single host machine.
Cloud Computing—Cloud computing is a form of Internet-based computing, in which a large number of computers are connected in public and private networks to provide a scalable infrastructure for file storage, application, and data.
Given a Scenario, Implement Common Protocols and Services
Among the thousands of protocols supported in the TCP/IP stack, only a few are about security, which is included in CompTIA’s Security + exam.
Internet Protocol Security (IPSec)—IPSec is both a module and a stand-alone VPN protocol that can be used with Layer 2 Tunneling Protocol (L2TP). It works at the network layer and can be used in dial-up or any network-to-network connection. Two primary IPSec’s protocols include the encapsulating security payload (ESP) and authentication header (AH).
Internet Key Exchange (IKE)—IKE helps to establish an encrypted VPN tunnel between two communication partners by securing the exchange of secret keys between them.
Internet Security Association and Key Management Protocol (ISAKMP)—ISAKMP provides authenticating keying material for security associations in secured manners. It has four functional components:
- Authentication of communication peers
- Threat mitigation
- Security association, creation, and management
- Cryptographic key establishment and management
Domain Name Servers (DNS)—DNS maintains a directory of domain names and translates them to IP addresses.
Secure Sockets Layer (SSL) and Transport Layer Security (TLS)—Both SSL and TSL are used to encrypt traffic between a web server and a web browser.
TCP/IP—This is a primary protocol used on the Internet and private networks worldwide. Other protocols required for network security purposes include FTP, Secure FTP, HTTPS, TFTP, SCP, and ICMP.
IPv4 and IPv6—IPv4 and IPv6 use a 32-bit addressing scheme and 128-bit addressing scheme, respectively. IPv6 eliminates broadcasts and fragmentation and contains an essential communication-encryption feature.
Open Systems Interconnection (OSI) Relevance—The OSI model was developed to describe protocols and their designs. However, its relevance has faded away because protocols weren’t designed following the OSI model.
Given a Scenario, Troubleshoot Security Issues Related to Wireless Networking
This section includes the techniques, services, standards, and devices related to wireless network security.
802.11 And 802.11a, b, g, n—802.11 is an IEEE standard for wireless network communications. Its versions include:
- 11a: 2Mbps
- 11b: 11Mbps
- 11g: 54Mbps
An 802.11 standard also describes the wired equivalent privacy (WEP). WEP is used to provide the same level of encryption and security on wireless networks as is found on cabled or wired networks.
Wi-Fi Protected Access (WPA)—This was an alternative to WEP and based on TKIP and LEAP cryptosystems and used a private passphrase. WPA2 is a new encryption scheme which is based on AES encryption method.
Extensible Authentication Protocol (EAP)—EAP is an authentication framework, not a mechanism for authentication. It allows for new authentication technologies to be compatible with existing point-to-point or wireless connection technologies.
MAC Filters—MAC filters are used to block access to unauthorized devices.
SSID—Wireless networks use SSID to establish connectivity between each other.
Antenna Types—various antenna types can be used for base stations and wireless clients. These include:
- Omnidirectional pole antennas
- Directional antennas, such as panel, parabolic, and Yagi
Performance-Based Questions in Security+ Exam
Performance-based questions (PBQs) test candidates’ ability to solve problems in a simulated environment. The candidates can manage their time wisely when working on the PBQs. The exam requires the student to solve a specific problem for each performance-based question. After that, a simulated environment is provided in which the student completes the required steps. Also, the candidates cannot see a clock when solving the PBQs.
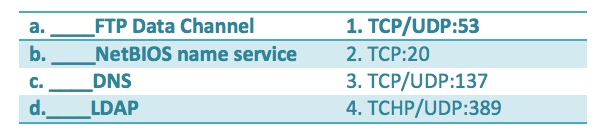
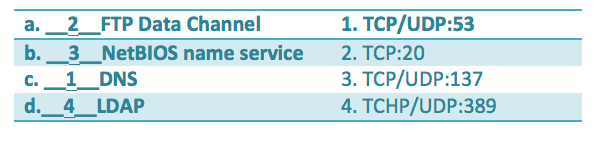
Example:
Question: Match the port to the protocol
Answer:
Where Should You Focus Your Study Time?
Quizzing and doing mock exams are the best ways to assess your understanding of this subject and your preparation before taking the Security+ exam.
Moreover, studying the right material is also very important. Some official books recommended by the CompTIA for Security+ exam, SYO-401, include:
- Cert-SYO-401 written by David L. Prowse
- CompTIA Security + All-in-One Exam Guide: Fourth Edition, published by McGraw Hill
- CompTIA Security + Certification Study Guide, published by McGraw Hill
How Is This Information Useful in the Real World?
The applications of network security are implemented in the organizations worldwide, including:
- Business communities
- Governmental organizations (law enforcement, military, etc.)
- Non-governmental organizations (NGOs), such as UN AIDS, Orbis International, Acumen Fund, Danish Refugee Council, and so on.
For example, in March 2015, Primera Blue Cross, a health insurance company based in Washington, came under cyber-attack. The network security professionals discovered that the hackers had accessed the employees’ names, social security numbers, dates of birth, phone numbers, and other sensitive details.
Recently, Gottfried Leibbrandt, the CEO at SWIFT, a provider of secure financial messaging services, revealed that the banks stopped three new attempts to compromise the Swift financial transfer network this summer. He further added that Swift imposed tighter network security to thwart cyber-attacks.
By using the network security solutions in the organizations, the network security experts can thwart the possibility of following network attacks.
- Reconnaissance attack
- Passive attack
- Active attack
- Distributive attack
- Insider attack
- Phishing attack
- Hijack attack
- Spool attack
- Buffer overflow attack
- Password attack
- Ping sweep attack
- Denial of service attacks
Security+ Boot Camp
The InfoSec Institute offers a Security+ Boot Camp that teaches you information theory and reinforces theory with hands-on exercises that help you learn by doing.
InfoSec also offers thousands of articles on all manner of security topics.