Windows Resource Protection
In this article, we will learn about a not-so-well known but a very useful security feature in Windows: Windows Resource Protection. This feature can help a great deal in developing an exclusion list for monitoring files and folders.
Introduction
There are some critical system files, folders, and registry keys that are installed as part of the operating system which should not be modified by applications. If an application attempts to modify a WRP-protected resource, it can have the following results:
-
Application installers that attempt to replace, modify, or delete critical Windows files or registry keys may fail to install the application and will receive an error message stating that access to the resource was denied.
-
Applications that attempt to add or remove sub-keys or change the values of protected registry keys may fail and will receive an error message stating that access to the resource was denied.
- Applications that rely on writing any information into protected registry keys, folders, or files may fail.
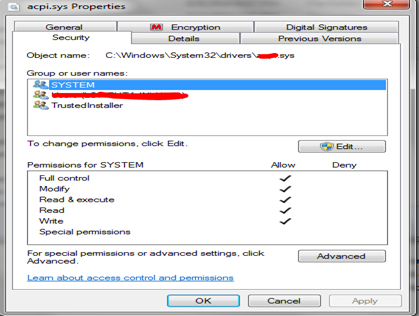
This all is possible due to a feature known as Windows Resource Protection, which itself is a new version of "Windows File Protection" and was started with Windows Server 2008 and Windows Vista. Windows Resource Protection (WRP) protects the system files, folders, and registry keys that are installed as part of the operating system from being replaced in an unauthorized way. All resources that are protected by Windows Resource Protection (WRP) are in turn managed by an account known as Trusted Installer. Protecting these resources prevents application and operating system failures.
What is Windows Resource Protection, and how does it work?
Windows Resource Protection sets up discretionary access control lists (DACLs) and access control lists (ACLs) defined for protected resources. Only the Windows Modules Installer service account known as TrustdInstaller has the full permission to modify the WRP protected resources. The "Trusted Installer" account is used to secure core operating system files and registry keys. Protected files and registry keys have an access control list applied that prevents other user accounts and programs that execute under any other user account except the TrustedInstaller account from making changes.
Windows File Protection works by registering for notification of file changes in Winlogon. If any changes are detected to a protected system file, the modified file is restored from a cached copy located in a compressed folder at %WinDir%System32dllcache. Administrators no longer have full rights to system files. Protected resources can be modified or replaced only if administrators take ownership of the resource and add the appropriate Access Control Entries (ACEs).
What is the difference between WRP and WFP?
The main difference between WRP and WFP is that WRP also protects several critical folders and is extended to include registry values also. WRP copies only those files that are needed to restart Windows to the cache directory located at %WinDir%WinSxSBackup, which brings us to another major difference between WFP and WRP: WRP does not copy those critical files that are not needed to restart Windows to the cache directory, unlike Windows File Protection, which cached the entire set of protected file types in the Dllcache folder. The size of the cache directory and the list of files copied to the cache cannot be modified. The third difference between WFP and WRP is that Windows Resource Protection applies stricter measures to protect files by setting ACLS on a per-item basis. Thus in taking ownership of any single item, that particular item can be replaced while other items remain protected, whereas with WFP, if we have to replace a single protected file, then WFP has to be disabled completely.
What resources does WRP protect?
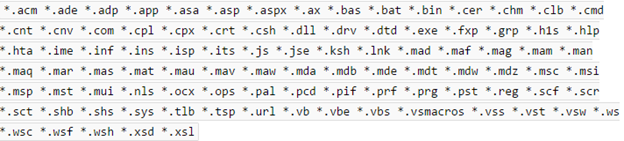
A folder containing only WRP-protected files may be locked so that only the Windows trusted installer SID is able to create files or subfolders in the folder. A folder may be partially locked to enable administrators to create files and subfolders in the folder. An important point to note is that if a key is protected by WRP, all its sub-keys and values can be protected. Also System File Checker is also integrated with WRP which can be used to check the integrity of files under specific folder paths, including the Windows folder and the boot folder.
Below is a screenshot of the all the types of resources being protected by WRP.
System File Checker
System File Checker is also integrated with WRP which can be used to check the integrity of files under specific folder paths, including the Windows folder and the boot folder. The system file checker utility, Sfc.exe, allows administrators to scan all protected resources to verify their versions. Since the TustedInstaller stores all the signed versions in the cache, if the utility found that files which are critical to restart Windows that do not match the expected Windows version, they may be replaced with the correct versions from the cache. The following is the command-line syntax for Sfc.
SFC options [=full file path]. The below table shows the options value along with their meanings.
Below are the examples that illustrate the commands shown above:
sfc /SCANNOW
sfc /VERIFYFILE=c:windowssystem32kernel32.dll
sfc /SCANFILE=d:windowssystem32kernel32.dll /OFFBOOTDIR=d: /OFFWINDIR=d:windows









