Certificates overview and use in Windows 10
The CIA Triad is one of the core tenets of Information Security, consisting of the ideals of Confidentiality, Integrity and Availability. Certificates are one example of a widely used technology in both the Confidentiality and Integrity spaces, depending on how they have been implemented. Today we are going to briefly go over what Certificates are, and how Windows 10 can make use of them.
What is a Certificate?
Digital Certificates are simply a piece of data that has been issued by a Certificate Authority, whether public, private or the device itself, which says that a device or a person is who they say they are. As a result, Trust becomes a commodity that is critical when it comes to 'who is vouching for whom'.
Learn Windows 10 Host Security
Certificates and Web Browsing
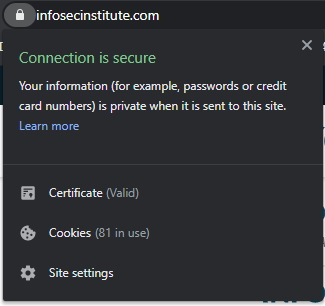
If we take a look at a website such as https://www.infosecinstitute.com, in most modern browsers we will see a 'padlock' icon- signifying that the connection we are using is secured. We can dig into this more by clicking on the padlock and verifying this.
We can also see more specifics about the certificate being used here by clicking on the Certificate (valid) button.
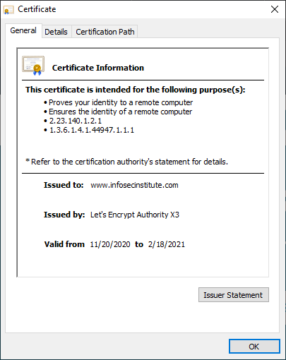
In this instance, the certificate was issued by 'Let's Encrypt'- a Certificate Authority (CA) that exists to promote secure browsing across the web- with an expiration date in 2021. The fact that certificates can expire can be both annoying and critical to security in equal measure. It can be annoying because it means that updated certificates must be re-issued to the appropriate devices, sites and services that use them on a regular basis before they expire. It can be critical however because without this ability to expire or be disallowed, compromised certificates could continue to be used forever. The CA will keep track of certificates that are allowed and blocked, and provide this information on demand to users trying to access this resource.
Normally CA's themselves police certificates that have been compromised, but occasionally browser manufacturers step in to block certificates at the browser level for one reason or another. Recently Apple, Google, Microsoft and Mozilla banned a Root Certificate being issued by the Kazakhstan government that was to be installed on all devices belonging to residents of that country. The reasoning behind their block of this was that this could potentially allow for interception of HTTPS protected traffic by said government.
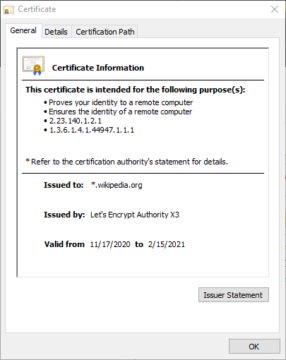
We also can notice on this certificate that it was issued explicitly to 'www.infosecinstitute.com'. While this may not seem to be anything special at first glance, it is a massive difference from something such as '*.wikipedia.org'.
Even though these certificates were both used by Let's Encrypt, the certificate being used for InfoSec is far more narrow in scope than Wikipedia's. InfoSec's can only be used specifically for traffic going to www.infosecinstitute.com and no other subdomains. Wikipedia's on the other hand is considered a 'Wildcard Certificate' can be used for anything at all ending in wikipedia.org, such as en.wikipedia.org (the English version), ru.wikipedia.org (the Russian version), or any of hundreds of others. This can be massively useful if you only want to deal with a single certificate across a massive infrastructure, but it is also a potential security risk. If the certificate is obtained by a 3rd party, they could potentially create a malicious subdomain ending in wikipedia.org and sign it with the legitimate certificate- thus preventing users from being able to tell at a glance that anything is wrong.
Certificates and Integrity
While the above examples use certificates in order to say that a web server is who they say they are, certificates can also be used in order to verify that a person is who they say they are through the use of Digital Signatures. For example, if someone was filling out a form in person for a loan, they would need to physically sign for it. However if that same person is filling out a form online for that same loan, they could use a digital signature to sign for it. This sort of signature can be used across a wide variety of file types, including adobe PDF's for instance. When the user signs the document, the signature is placed into the file, along with a timestamp of when it was set. This forces the file to be saved at that time and if any modifications happen after the timestamp- the signature is nullified. This helps to ensure the integrity of the file and eliminates the ability of the user to say that they did not sign for it through non-repudiation.
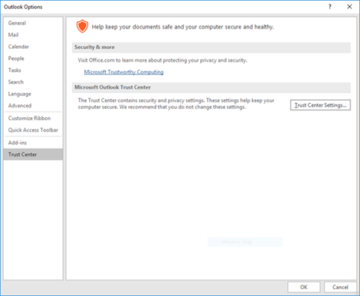
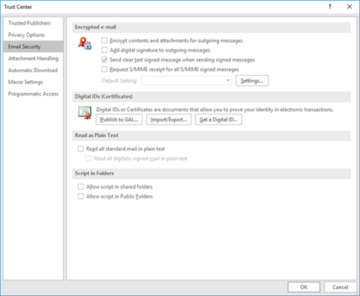
This can also be used when sending emails such as through Outlook. To add this signature to our emails, we will want to go up to File and select 'Options'. Once here, we will want to navigate to 'Trust Center' and click on the 'Trust Center Settings' button.
After we have arrived in Trust Center, we will want to click on 'Email Security'.
Once here, we have the option to 'Add digital signature to outgoing messages'. This will allow us to be able to sign our outgoing emails by attaching a version of our certificate to it. If anything happens to the email during transit, the recipient will be able to tell at a glance if it is no longer what we sent out. You may also notice the option to 'Encrypt contents and attachments for outgoing messages'- this is another method that we can use to help keep our data confidential, as we will go into below.
Certificates and Confidentiality
Certificates can also be used to protect files in transmission through the use of Public Key Infrastructure (PKI). Public Key Infrastructure allows for the transmission of messages and other data that can theoretically be only decrypted by the person on the other end of the conversation. By encrypting data with the recipient's public key, it can only be decrypted via the recipient's private key- which only they possess. While this does require some form of key sharing at the outset, once this has been performed it is a very fast and efficient way to transmit secure data.
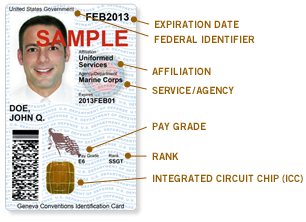
Certificates can also be used during other confidential situations such as logging into a system. Through the use of a certificate embedded on a smart card and a Personal Identification Number (PIN), we can create a 2 Factor Authentication (2FA) system via something the person knows (PIN) and something the person possesses (smart card). A great example of this is the Common Access Card (CAC) used by various United States Government agencies.
This ID card allows for quick secure identification in both human-to-human contact as well as multiple methods of human-to-computer contact. For example, if the user wanted to login to their Windows 10 workstation, they would place the chip into a reader, which will then recognize the user and ask for a PIN to finish authentication. If they enter the correct PIN, they will be logged in to Windows. If not, it would react exactly the same way as if the user had entered a bad password.
Learn Windows 10 Host Security
Conclusion
Certificates are extremely versatile and have tremendous power to make sure data and systems remain secure. However, like most authentication schemes, they must remain up to date in order to stay that way. Windows 10 and other programs have built in support for Certificates to the point now where they are nearly ubiquitous. While not required for every use, they have enormous benefits in situations requiring Integrity and/or Confidentiality.
Sources
- https://www.venafi.com/education-center/pki/how-does-pki-work - How does PKI Work [Public Key Infrastructure]
- https://www.digicert.com/faq/ssl-cryptography.htm - Behind the Scenes of SSL Cryptography
- https://www.zdnet.com/article/apple-google-microsoft-and-mozilla-ban-kazakhstans-mitm-https-certificate/ - Apple, Google, Microsoft and Mozilla ban Kazakhstan's MitM HTTPS certificate
- https://letsencrypt.org/ - Let's Encrypt
- https://helpx.adobe.com/sign/using/digital-signatures.html - Use digital Signatures
- https://en.wikipedia.org/wiki/ - Non-repudiationNon-repudiation
- https://support.microsoft.com/en-us/office/secure-messages-by-using-a-digital-signature-549ca2f1-a68f-4366-85fa-b3f4b5856fc6 - Secure Messages by using a digital Signature
- https://docs.microsoft.com/en-us/troubleshoot/windows-server/windows-security/enabling-smart-card-logon-third-party-certification-authorities - Guidelines for enabling smart card logon with third-party certificate authorities
- https://en.wikipedia.org/wiki/Common_Access_Card - Common Access Card