How to use Microsoft DirectAccess
When you are physically located at an organization's site, it is relatively straightforward to present users with an experience that is consistent across the board. This could entail standardized firewall settings, shared drives, intranet sites- anything located on the local network. With the market as a whole pivoting to support working remotely, however, trying to make sure that those settings remain consistent can be a significantly greater challenge when users are at home.
Some options of course will still be accessible on the open Internet, but if we want to keep our security the same as when users are on-site, that is going to require some form of remote access. A good number of VPN connections as a rule are initiated by users, which means that this could be considered a choice — whether the user wants to use their own local settings or the organization's. Unfortunately, this could lead to a time when the device becomes compromised and then is brought into the organization's network quickly. The way around this then would be requiring the device to be connected to the organization's internal network at all times, regardless of its physical location using something like an Always-On VPN.
Some organizations are able to do this with advanced networking hardware- creating a permanent point-to-point tunnel between locations. However, in the case of individual users this becomes extremely cost-prohibitive- especially in situations where their IP address regularly changes, such as with residential Internet Access. Therefore, we would want something between a regular user-initiated VPN software client and a dedicated hardware solution. Enter Microsoft DirectAccess.
Learn Windows 10 Host Security
![]()
Microsoft DirectAccess allows systems to automatically connect up to a remote network on startup so that users are effectively always 'on-site'. There are multiple requirements for setting up such an environment, such as your workstations having at least the "Enterprise" edition of operating systems running Windows 7 or higher.
Additionally, while DirectAccess is a core part of the Windows Server operating system as of Server 2012, you will want to have at least 2012 R2 in order for it to be anything more than a 'basic' setup. If you are taking a look at implementing a fresh environment using Microsoft DirectAccess, it would be recommended as of the time of writing to at least consider using a newer operating system version, as support for both Microsoft Server 2012 and 2012 R2 will be ending in 2023. With all of that in mind, let's have a quick overview of how to use Microsoft DirectAccess.
Installation
Before you begin the installation, you MUST make sure that you already have an Active Directory domain set up in your environment along with creating the Machine OU that you will be using to target your DirectAccess Clients ahead of time. This is because DirectAccess will only work for systems that are joined to your domain. You will also want to verify what the end goal of this deployment is, since as we mentioned before only Workstations of Windows 7 Enterprise or higher will work, along with Servers of Windows Server 2008 R2 or higher.
For the purposes of the example today, we are going to be using Windows Server 2019 Standard. Additionally, even if your environment does not use IPv6 at all, this server will need to have it active due to the tunneling requirements of DirectAccess.
On your Server operating system, we will want to go to Server Manager to begin with. If it does not come up automatically for you, this can be accessed by default on server operating systems of 2016 or higher by going to Start and select 'Server Manager' on the Start Menu.
From here, you will want to click on 'Add roles and features'.
Upon reaching the landing page, you will want to click 'Next'.
We are going to be doing a standard role/feature install here, so we can just click 'Next' to continue.
You will need to select the destination servers you are choosing to install the role onto, and for the purposes of our example here, we are located directly on the server in question. Once we choose the server we need, click 'Next'.
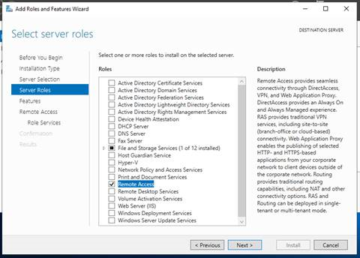
We are going to want to select the 'Remote Access' Server Role before clicking 'Next'.
We do not need to choose any additional features at this time, so we can just click 'Next'.
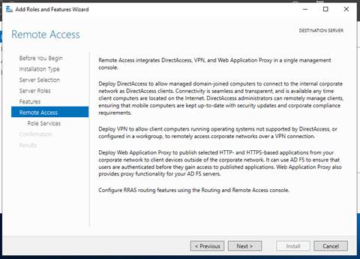
Once you have read the description for what 'Remote Access' does, please click on 'Next'.
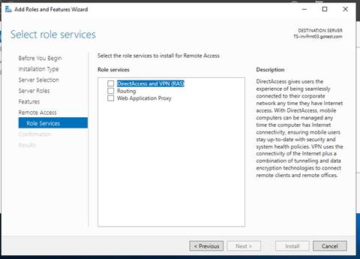
We are only going to need the DirectAccess and VPN (RAS) Role right now, so select that option.
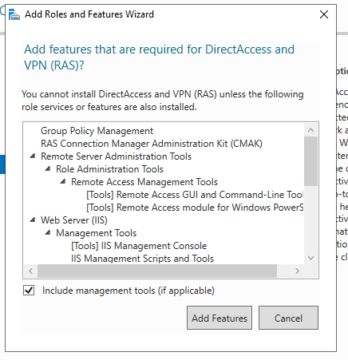
A screen displaying the prerequisites for installing this role will appear, such as management tools and IIS. Once you are satisfied with the additional options, click on 'Add Features' followed by 'Next'.
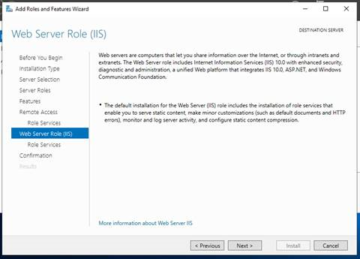
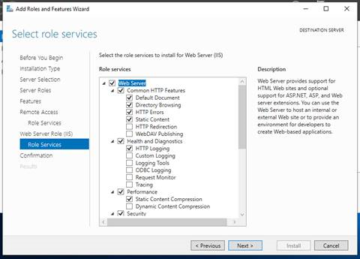
As mentioned before, if not already installed you will need to install IIS. Once you have read over the description, please click 'Next'.
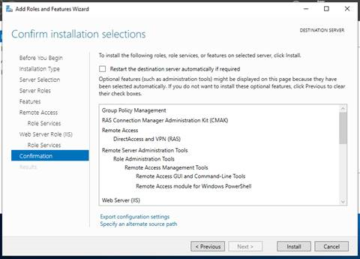
You will be asked to confirm the options selected for IIS, after which you can click 'Next'.
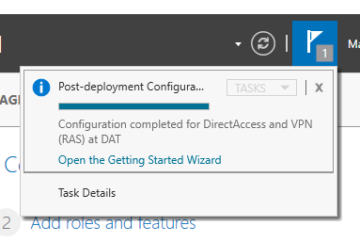
Final confirmation will be displayed, asking if you are certain that you wish to go through with the installation. If you are satisfied with what will be installed, click 'Install'. Post-install, you will want to reboot the system just to make sure that everything is good to go. When it comes back up again, Server Manager will have an attention flag to show you that something needs post-installation configuration- in this case, completion of DirectAccess setup.
When ready to continue, click on 'Open the Getting Started Wizard'.
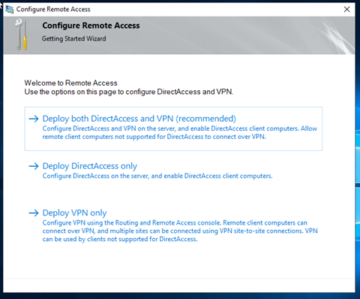
We are only going to be dealing with DirectAccess right now, so we can click on 'Deploy DirectAccess only'.
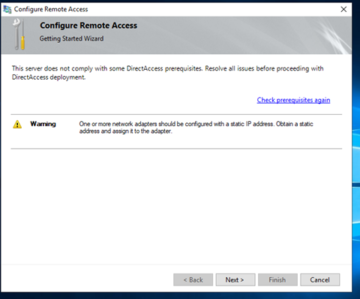
The wizard will scan for any required prerequisites and display prompts accordingly.
After this has been resolved, you will want to click on 'Check Prerequisites again', after which it will continue.
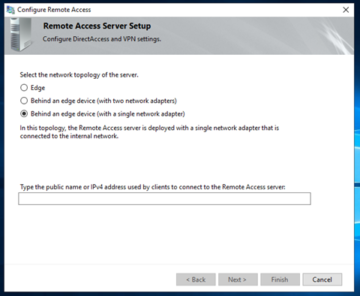
Here is where the settings will start to vary depending on your environment- whether this server is directly connected to the web, acting as an intermediary between a DMZ and the internal network, or is only on the internal network. Once you have set up your connection and address/IP that clients will be using, you will want to click on 'Next'. This step is why we made sure that IPv6 is enabled on our connection earlier; as if you do not have it turned on, you will receive an error message on this phase.
Learn Windows 10 Host Security
![]()
Important
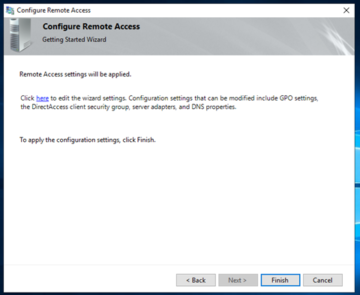
When you click on ‘Next’ to go to the next page, DO NOT CLICK ON FINISH YET. It will ask you if you want to adjust group membership and GPO settings, which you absolutely will want to do. This may not necessarily be required in a test environment, but it is essential in a production one. You will want to click on the ‘click here’ to go into client configuration.
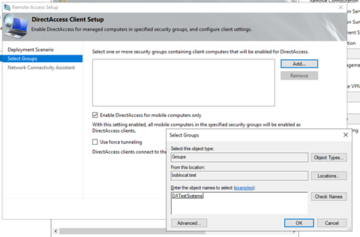
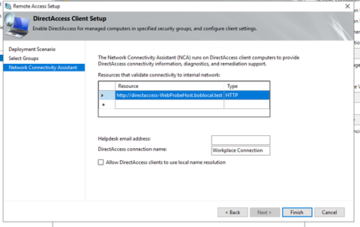
We still want to use DirectAccess for clients, so we can just click on 'Next' on the first screen before going to the 'DirectAccess Client Setup'. We will want to remove 'Domain Computers' from this section, as we do not need to have everything go through this single point. Rather, we can select a particular group of computers from AD, which can be quickly modified through standard methods. Also at least during the testing phase, we will want to remove the checkbox from 'Enable DirectAccess for mobile computers only'. After we select the group, click 'Finish'.
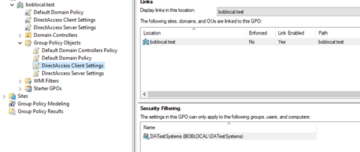
We can verify that the GPO settings are assigned to the proper group in Group Policy Management available via our Domain Controller or other standard means.
Once this is all set up, we can run a GPUpdate /force on our test system in this group, which will bring down the appropriate GPO settings. If we have configured everything properly, the next time the system reboots we will be using DirectAccess. There are a LOT of possible settings that can be adjusted to meet your environment's needs in DirectAccess, and reading Microsoft's official documentation located here is well worth your time. DirectAccess does have a high bar to entry, and is not for everyone that is certain. That being said, it has the potential to be well worth it if your organization needs something fast and completely supported from a single vendor from end to end.
Sources
- Compare Windows 10 Editions, Microsoft
- Install and Configure Basic DirectAccess, Microsoft
- Step by Step Installing & Configuring DirectAccess in Windows Server 2016, New Help Tech
- Install and configure Direct Access on a Windows Server 2016 Essentials for hassle-free remote access, Server Essentials