What you must know about OS fingerprinting
For those of us in the information technology field, there are two reasons why we should understand operating system fingerprinting.
The first reason is to better design and implement security controls in networks and local machines.
The second reason is that effective OS fingerprinting is a vital penetration testing skill.
If an attacker can identify the operating systems that run on specific target machines, they can then learn which exact vulnerabilities to exploit. Each and every OS in deployment has unique bugs and vulnerabilities. When an exact OS is determined, it's really easy to research what they are. That's even often true when bug reports haven't been sent to vendors already, and the corresponding patches have yet to be developed! So, hardening against OS fingerprinting can, in some cases, prevent zero-day attacks.
OS fingerprinting techniques can be generalized into two categories, active and passive.
Active OS fingerprinting
Active fingerprinting is a lot easier than passive fingerprinting, and is much more likely to return the information an attacker wants. The main reason why an attacker may prefer a passive approach is to reduce the risk of being caught by an IDS, IPS, or a firewall.
It's still important to harden against active fingerprinting. It's the easier course of action for an attacker to execute, and they may decide to DoS (denial of service) attack network security systems first, in order to facillitate active fingerprinting.
Active fingerprinting works by sending packets to a target and analyzing the packets that are sent back.
Almost all active fingerprinting these days is done with Nmap. Nmap is usually used by network adminstrators to monitor the security of their networks. With Nmap, they can check to make sure that all of the firewalls in their network are properly configured, and they can also make sure that all of the TCP/IP stacks they maintain are functioning properly.
But like pretty much all security tools, Nmap is an effective application for both admins and attackers.
Running an OS fingerprinting scan in Nmap is as simple as typing "nmap -A ip_address_or_domain_name_of_target"
Here, I OS fingerprinted my own machine by targeting "localhost". Alternatively, you can do the same thing by targeting the IPv4 loopback address, 127.0.0.1.
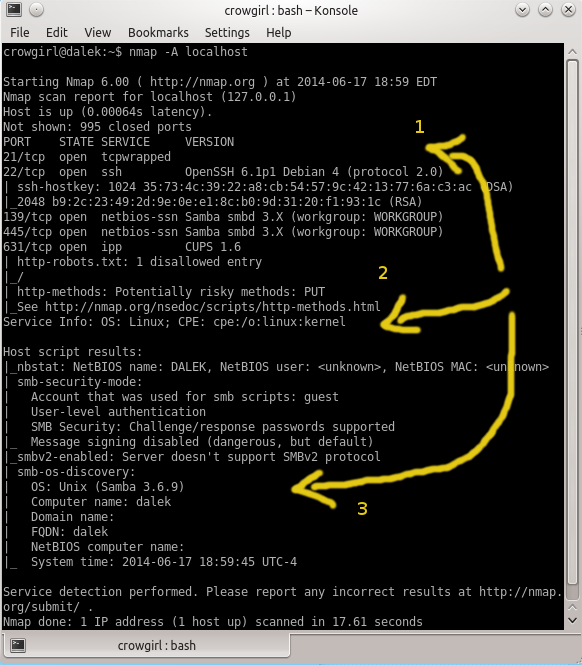
In the first pertinent line in the printout, I discovered that the Debian version of OpenSSH is running from port 22. That version of OpenSSH is only compatible with Debian-based Linux distros such as Ubuntu, Xubuntu, and of course, the original Debian.
The second line I indicated in the printout is information that came directly from my OS kernel, it's Linux!
The third line is information the Nmap scan got about the Samba server I'm running. It says I have Samba 3.6.9, the Unix version. Although the Unix and GNU/Linux kernels are different, Samba will say it's the Unix version for all Unix and Linux distros.
So, if you put all three details together, you can infer that I'm running a Debian-based Linux distro. My machine is running Kubuntu 14.04. An attacker won't know to try to exploit vulnerabilites specific to the Linux kernel version in Kubuntu/Ubuntu 14.04, nor will they know to exploit vulnerabilities that are specific to KDE. But there are some vulnerabilities that apply to all current Debian-based OSes. An attacker would at least know where to start.
When I ran that Nmap scan, what it did was send a number of TCP, UDP, and ICMP probes to my local machine. As I'm using a well-configured firewall, I didn't have many ports that were open. Nonetheless, Nmap sent probes to lots of different TCP/IP ports, and analyzed what returned.
Specific OSes and network service applications leave different types of data in their TCP, UDP, and ICMP packets. Nmap utilizes scripting that analyzes that data to print out results that are useful for OS fingerprinting.
It's possible to sometimes get inaccurate results. If you're unsure of the accuracy of the OS information in the Nmap printout, there's another command you can try. "sudo nmap -O -sV -T4 -d ip_address_or_domain_name_of_target". Using"sudo" is necessary, because the command requires root privileges in most versions of Nmap.
Passive OS fingerprinting
Passive fingerprinting sniffs TCP/IP ports, rather than generating network traffic by sending packets to them. Hence, it's a more effective way of avoiding detection or being stopped by a firewall.
As of this writing, the most frequently used tools for passive fingerprinting are NetworkMiner and Satori. NetworkMiner is developed to run in Windows, but there are both native Windows and GNU/Linux versions of Satori. If you're using a Debian-based, Fedora, or Arch Linux distro, you can still install NetworkMiner, but you'll need to install the Mono framework first. Keep in mind that if you install NetworkMiner in a Mono-compatible GNU/Linux distro, you won't be able to actively sniff packets. So if you're not using a Windows machine, I'd recommend Satori instead.
Passive fingerprinting uses a pcap (packet capture) API. In GNU/Linux and BSD/Unix operating systems, pcap can be found in the libpcap library, and for Windows, there's a port of libpcap called WinPcap.
While sniffing traffic, passive fingerprinting does its best to determine a target machine's OS by analyzing the initial Time To Live (TTL) in packet IP headers, and the TCP window size in the first packet of a TCP session, which is usually either a SYN (synchronize) or SYN/ACK (synchronize and acknowledge) packet.
The Internet Engineering Task Force's (IETF) Request For Comments (RFC) recommends a default TTL of 64 milliseconds for optimal functionality. But that's a mere recommendation, not a requirement.
Passive fingerprinting can make a guess of a target's OS, because different OSes have different TCP/IP implemetations.
Typical packet specifications per OS are an initial TTL of 64 milliseconds and a TCP window size of 5840 kilobytes for Linux kernel versions 2.x, an initial TTL of 64 milliseconds and a TCP window size of 5720 kilobytes for Android and Chrome OS, 128 milliseconds and 65535 kilobytes for Windows XP, 128 milliseconds and 8192 kilobytes for Windows 7 and Server 2008, and 255 milliseconds and 4128 kilobytes for Cisco routers.
But it's imperfect to rely on those typical figures. The TTL can be changed as a sniffed packet goes from router to router. TCP window sizes can change according to a number of variables, too.
Hence, passive OS fingerprinting is less accurate than active OS fingerprinting, but may be a technique chosen by an attacker or penetration tester who wants to avoid detection.
If you want to better hide the OSes that run on your network devices, a lot of work is necessary.
Definitely active and passive fingerprint your network first. Then you'll know what an attacker may be able to discover.
Properly configured, implemented, and maintained IDSes, IPSes, and firewalls can mitigate active fingerprinting.
Passive fingerprinting can be mitigated by assuring that NICs (network interface cards) don't operate in promiscuous mode. Or if some NICs must operate promiscuously for the sake of functionality, watch them closely and on a regular basis!
Make sure there are no hubs in your network. Use switches only, and configure them properly. Implementing strong encryption in as much of your network as possible also makes packet sniffing difficult for an attacker.
And finally, check all of your network logs as frequently as you can. Often, all sorts of network attacks can be prevented by analyzing logs on a regular basis. They exist for a reason, you know!
Sources
- Techniques in OS Fingerprinting- Nostromo
- Chatteronthewire.org- Satori
- Passive OS Fingerprinting- NETRESEC
- TCP/IP Fingerprinting Methods- Nmap
- Dealing With Misidentified and Unidentified Hosts- Nmap
- Remote OS Detection Via TCP/IP Stack Fingerprinting- Phrack Magazine
- Service and Application Version Detection- Nmap









