Introduction to Blackberry Balance Technology
Blackberry is known for its email and security rather than a company which produces fancy mobile phones. This is one of the reasons why Blackberry is preferred as a platform when it comes to corporate users. Many organizations provide Blackberry Phones to their employees to ensure their around the clock availability and connectivity for urgent matters.
This article will look at the security of Blackberry mobile devices from an organization's perspectives.
We will cover "Blackberry Balance Technology" and understand major features of this technology that can help organizations push corporate policies on mobile devices to protect device & corporate data.
Objective:
The objective of this article is to introduce users to the technology and touch upon the features briefly. This article is not a how-to or a hands-on guide for implementing "Blackberry Balance Technology". For step by step instructions on how to implement, one can refer to the product manuals or contact Blackberry support.
This article explains the features of "Blackberry Balance Technology" that can be utilized to secure the data that resides on the mobile device.
Background
Mobile devices are critical as all the employees given a corporate mobile phone connects to the organization's network, even if it only for checking emails. If the device gets compromised, it can infect the organization's network as well.
There are multiple ways in which an organization can protect corporate mobile devices; however the focus of this article will be on "Blackberry Balance Technology".
The core focus of this technology is at the segregation of personal and work data. This is very important for a mobile device purchased by an organization for an employee – although provided for official purposes; it can also contain personal data – e.g. pictures and videos taken by the camera, etc. If organization's policy permits users to install third party applications like Twitter, Facebook or similar apps, these apps store local data on phone, which as well is personal data.
System Requirements:
OR
Classification of Work Data and Personal Data
Before we understand how to exactly do work and personal data segregation, we need to understand two more concepts – IT Policy & IT Policy Rules. Blackberry Enterprise server works based on IT Policy. These Policies can be used to control and manage the following:
-
Blackberry Desktop Software
-
Blackberry Devices
-
Blackberry Web Desktop Manager
IT Policy & IT Policy Rules
An IT policy consists of multiple IT Policy rules. How these rules are configured defines how above mentioned devices (including mobile devices) behave.
Now that we have an understanding of what IT Policy Rules are, we'll understand how these rules can be helpful in achieving our objective of data segregation.
The following is a pictorial representation of how policies, rules, mobile devices, and enterprise server create an ecosystem and what comes where:
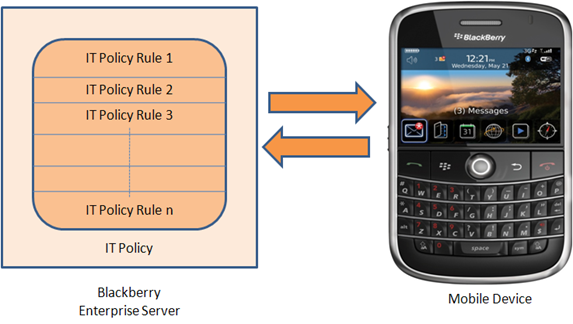
During this article we will discuss following IT Policy rules:
-
Enable Separation of Work Content IT Policy rule
When this rule is enabled, a Blackberry device classifies the data into work and personal data. Additional rules are required to be configured, however this is the primary rule that needs to be enabled.
-
Work Domains IT Policy rule
This rule contains a list of domain names, email addresses, etc… which a Blackberry device identifies as work data.
-
Desktop Backup IT Policy rule
This rule specifies which mobile device database can be backed up by backed up by the Blackberry Desktop Manager
-
Is access to Corporate Data API - application control policy rule
Blackberry mobile devices check this rule to decide which non-work related applications needs to be granted access to work data
-
Disable Forwarding of Work Content using Personal Channels IT Policy rule
This rule controls whether a Blackberry user can forward work data via personal channels such as SMS, MMS, and BBM.
Segregation of Data
Segregation of data can be achieved using "Enable Separation of Work Content IT Policy" rule. This rule is disabled by default. Once this rule is enabled, organizations can control data transfer between work applications and personal applications and many more tasks that control work data.
The device determines whether the data is work data or personal data, based on domain information of the organization. A list of domain names, email addresses, etc… can be configured into the "Work Domains IT Policy" rule.
Once the policy is enabled:
Specific rules can further be implemented for third party applications as well as to configure whether work data can be accessed by these applications. These applications can be developed by RIM or any other vendor or individual developers (e.g. game developers). Unless the policy permits, these third party applications will not be able to access work data.
Corporate Data that can be protected
The following work data can be controlled using the "Enable Separation of Work Content IT policy" rule:
-
Work Emails and attachments
-
Calendar entries for outlook/lotus dominos
-
Work Email Addresses/Contacts, Tasks, Memos, etc…
-
Files downloaded from corporate network
-
Work Application generated files which are stored on memory cards (in case where they are used to extend device's memory)
Once data is classified as work data, it cannot be reclassified as personal data, hence defining the policy should be done with due care.
The following are some of the examples of personal data:
-
Non-corporate Email addresses/Contacts which do not match the domain name(s) specified in the policy.
-
Phone data (call logs get deleted upon deleting work data)
-
Browser Cache, Media Files, Passwords, SMS, instant messages (unless it is a corporate chat application developed for blackberry), etc…
Actions that can be performed after Data Classification is completed
The following are some of the things that can be controlled by setting the "Enable Separation of Work Data IT policy" rule:
-
Copying and pasting of work data
Copy pasting work data into personal applications can be allowed or restricted based on organization's expectations.
Applicable Rule: "Enable Separation of Work Content IT Policy rule"
-
Forwarding work data
Forwarding work data using SMS, MMS,etc… can be controlled.
Applicable Rule:"Disable Forwarding of Work Content using Personal Channels IT Policy rule"
-
Transferring of work data to personal application
If a user tries to transfer work data to personal applications such as twitter, the same can be restricted/allowed based on the policy configurations.
Applicable Rule: "Is Access to Corporate Data API application control Policy rule"
-
Deleting work data from the device
When an employee quits the company, in order to protect data, organizations can even wipe the work data from the mobile device. This way critical corporate data like emails, attachments, call logs, contacts, etc… can be removed permanently from the device while leaving the personal data of the employee intact.
These kinds of policies make more sense where an organization supports BYOD (Bring Your Own Device) Policy and allows an employee to configure their device to download corporate emails. The device is still the employee's asset and hence it cannot be collected back from the employee when he quits the organization.
However, in such a situation, if work data can be wiped out from the device, it can help organizations in protecting their data.
This can be achieved using "Blackberry Administrative service". Once configured, organizations can remotely wipe the data using option – "Delete only organization data"
Detailed information on configuration is out of this articles scope.
-
Control Blackberry Mobile Device's Browser
The internet is full of rogue sites and visiting a rogue site can lead to downloading of malicious software on user's mobile device.
To protect against these risks, organizations can control the Blackberry's internal Browser and ensure that it only connects to the internet via Blackberry Enterprise Server – which is controlled by the organization.
Applicable rules: "Allow other Browser services IT Policy rule"
Additionally, the following are some more rules that can be explored. These rules can control the Blackberry browser further:
"Allow IBS Browser IT Policy rule", "Allow Hotspot Browser IT Policy rule" and"Enable WAP Config IT Policy rule".
-
Backing up of work data
Organizations can even restrict users from backing up the work data if required.
Applicable rule:"Desktop Backup IT Policy rule"
This rule is not enabled by default, however if required, it can be configured.
Blackberry Balance Technology is very powerful and effective as itcan help organizations protect corporate data. The types of rules that are packed into the technology makes it useful for organizations to implement a Bring Your Own Device (BYOD) policy if required – that can not only improve employee satisfaction, but also saves money – as new corporate devices don't need to be purchased if any employee already has blackberry device.
References:
http://docs.blackberry.com/en/admin/deliverables/27987/Corporate_Data_1388491_11.jsp
http://docs.blackberry.com/en/admin/deliverables/27987/Personal_Devices_policy_group_1337524_11.jsp
http://docs.blackberry.com/en/admin/deliverables/4222/Desktop_Backup_204186_11.jsp









