Cyber attack on Sony Pictures is much more than a data breach - updated
Sony Pictures corporate network compromised by a major cyber attack
At the end of November, computer systems at the corporate network of Sony Pictures were breached and taken offline by a malware-based attack. TheNextWeb portal was one of first outlets to publish the news. Sony Pictures Entertainment manages distribution of Sony films and TV productions, and according to the first information reported on the attacks, the internal architecture was compromised and sensitive data was stolen by the hackers.
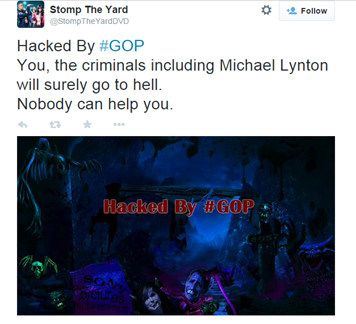
A thread started on the Reddit social news website just after the cyber attack announced that every computer in the network was shut down due to a hack. The thread also reported an image that was displayed on all the computers in the corporate network. The picture was reading that the company was "Hacked" by the #GOP team, also known as Guardians of Peace.
Phishing simulations & training
"Hacked by #GOP … Warning: We've already warned you, and this is just the beginning...We have obtained all your internal data including secrets and top secrets … If you don't obey us, we'll release data shown below to the world. Determine what will you do till November the 24th, 11:00 PM (GMT)," is the disturbing message that appeared on the employee' machines.
The hackers threatened the company to reveal many uncomfortable truths if the company did not go along with their demands.
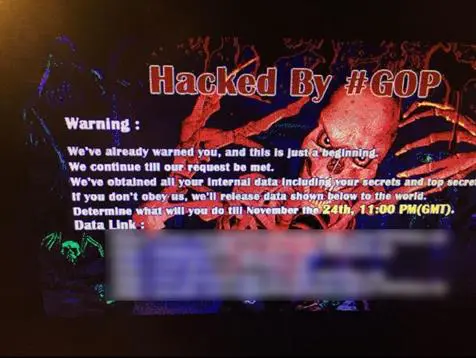
Figure 1 - GOP message appeared on infected computers
The user that started the thread on Reddit referred in a thread published a year ago that he has worked at Sony Pictures. As proof of the attack, the GOP team released several zip files which contain the data stolen from Sony Pictures servers. The leaked archives include a list of filenames of a number of documents pertaining to financial records and private keys for access to servers. The GOP team disclosed an 894MB archive containing thousands of files, covering a period between 2008 and 2012.
The cyber attack had a severe impact on the company. More than a week since the data breach, Sony Pictures is still working to restore the compromised system and eradicate the malware from the network.
Figure 2 - A Tweet is confirming the cyber attack
TheNextWeb reported that a source within Sony has confirmed the attack, and it explained that internal activities have been blocked due to the hack.
"A source within Sony has anonymously confirmed to TNW that the hack and image that have appeared on computers inside Sony Pictures is real. They said that 'a single server was compromised and the attack was spread from there.'
According to our source, everyone was going home following the hack: 'We're all going to work from home. Can't even get on the internet,'" states the post on TheNextWeb.
In response to the attack, the internal security staff warned the employees to disconnect their computers from the internal network and requested the personnel to avoid checking corporate email. Other incident response measures include the switch-off of the company VPN and disabling of Wi-Fi connection on every mobile device.
"Sony Pictures Entertainment has told employees company-wide to not connect to corporate networks or access email, after the studio was hit Monday by what appeared to be a malicious hacker attack threatening to disclose "secrets," reported the online magazine Variety.
Sony Pictures data breach may have exposed much more than preview copies of movies
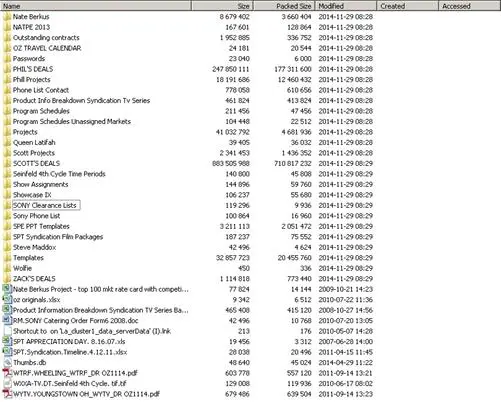
The statements posted by alleged members of the GOP have suggested to experts the presence of an insider access to the network, which supported the activity. Just after the announcement of the attack, the GOP team released two lists, including names of several documents, password files, private key files, source code files (CPP), financial data, PII, inventory lists for hardware and other assets, network maps and outlines, production outlines and schedules.
Figure 3 - List of stolen data from Sony Picture servers
In the following days, the GOP hacking team released preview copies of several Sony movies, including Annie, Fury, and Still Alice, but the intent of the group is to disclose much more data.
With each passing day, the investigators and security experts shared more findings and theories about the data breach. The cyber attack has caused much more than the online distribution of pirated movies, because a batch of sensitive employee data is also circulating on the Internet. A circumstance caught the attention of security experts: the servers used by members of GOP to leak online employee information belong to Sony Corporation too. Security experts have different opinions on the facts. Some researchers speculate that hackers gained access to other Sony infrastructure by abusing their resources. Others believe that Sony Pictures and law enforcement are using honeypots to gather further information on the attackers.
The popular investigator Brian Krebs confirmed that the archive of employee information includes Social Security numbers, dates of birth, and salary and medical information that are now being circulated via torrent websites.
"According to multiple sources, the intruders also stole more than 25 gigabytes of sensitive data on tens of thousands of Sony employees, including Social Security numbers, medical and salary information. What's more, it's beginning to look like the attackers may have destroyed data on an unknown number of internal Sony systems. Several files being traded on torrent networks seen by this author include a global Sony employee list, a Microsoft Excel file that includes the name, location, employee ID, network username, base salary and date of birth for more than 6,800 individuals," said Krebs.
Figure 4 - Data stolen from Sony Pictures (Brian Krebs)
A detailed list of employees is available online in a Microsoft Excel file together with other files, including a status report from April 2014 that reports a list of details for 700 employees in excess. The gizmodo.com web portal confirmed the presence of scripts for pilots, budgets, employee criminal background checks, salary negotiations, and other data in the leaked archives.
"BuzzFeed's discoveries include documents detailing 'employee criminal background checks, salary negotiations, and doctors' letters explaining the medical rationale for leaves of absence.' They also include 'the script for an unreleased pilot written by Breaking Bad creator Vince Gilligan to the results of sales meetings with local TV executives.' Better call Saul," states Gizmodo.
The last batch of files released during the weekend includes contracts between the Sony Pictures Television and several TV stations.
"In the documents viewed by Salted Hash, the sales items were for airing rights to various shows such as Dr. Oz, Judge Hatchett, Outer Limits, and Stargate, SG-1. The documents also disclose details related to syndication rights for sitcoms such as King of Queens, Seinfeld, and Rules of Engagement," states a blog post published on csoonline.com.
The archive contains an internal phone list and a detailed organizational chart of the Sony Pictures, which includes a huge quantity of information, such as cell phone numbers of the employees. The leaked data puts the company at serious risk of further cyber attacks. Hackers in fact could exploit the information to run further targeted attacks and open the doors to other hacking crews. Attackers can run social engineering attacks or organize spear phishing campaigns to gather other information from targeted employees or to steal intellectual proprieties from Sony.
"In addition, one outdated document disclosed network usernames, passwords, and American Express account information (card data and Internet account details), something else that could be used in a targeted attack," continues CSOonline.
On Saturday, a member of the GOP announced that the ongoing data leakage was just the beginning, announcing that the crew "will release all of the data…" which they claimed was under 100 TB or "tens of [TB]."
According to the findings of the investigation conducted by the security researcher Dan Tentler, Director of Security Research for IT security firm Carbon Dynamics, 65 servers belonging to the Sony PlayStation network were being used to spread the stolen data.
Tentler has traced the IP addresses of the servers hosting the information and has discovered that they are inside the Sony PlayStation infrastructure hosted on the Amazon EC2 cloud. The Sony PlayStation servers were spreading a nearly 27 gigabyte dump, "spe_01." The links to the torrent to download the sensitive data stolen in the attack against Sony Pictures are circulating on the Pastebin.
Figure 5 - Sony Pictures stolen data shared through torrents
The experts noticed that it is very strange that despite that Sony's PlayStation Network and Sony Pictures Entertainment are different companies from a legal perspective, the first one apparently didn't stop servers from distributing the stolen information. Tentler highlights that the EC2 servers disappeared from the list of peers on the torrent late Tuesday.
GOP sent threatening emails to Sony Pictures employees
The massive data breach at Sony Pictures Entertainment is having a serious impact on the organization and its employees. At the time of this writing, the GOP crew is using the stolen data to conduct a campaign of intimidation against Sony employees. The massive data breach at Sony Pictures has also caused the exposure of other sensitive document; among them, the Social Security numbers of more than 47,000 celebrities, freelancers, and current and former Sony employees.
Several media agencies are spreading the news that Sony Pictures employees received e-mails from hackers threatening to harm them and their family members. This frightening turn of events has no precedent.
According to the media agencies, employees at Sony Pictures Entertainment received threatening emails from hackers breaching the company network. The emails were written in less than pristine English as follows:
"Please sign your name to object the false (sic) of the company at the email address below, if you don't want to suffer damage. If you don’t, not only you but your family will be in danger."
The employees at the Sony Picture were requested to turn off their cell phones after receiving this email. Here is the full text of the message:
"I am the head of GOP who made you worry.
Removing Sony Pictures on earth is a very tiny work for our group which is a worldwide organization. And what we have done so far is only a small part of our further plan. It’s your false if you if you think this crisis will be over after some time. All hope will leave you and Sony Pictures will collapse. This situation is only due to Sony Pictures. Sony Pictures is responsible for whatever the result is. Sony Pictures clings to what is good to nobody from the beginning. It’s silly to expect in Sony Pictures to take off us. Sony Pictures makes only useless efforts. One beside you can be our member.
Many things beyond imagination will happen at many places of the world. Our agents find themselves act in necessary places. Please sign your name to object the false of the company at the email address below if you don’t want to suffer damage. If you don’t, not only you but your family will be in danger.
Nobody can prevent us, but the only way is to follow our demand. If you want to prevent us, make your company behave wisely."
Did North Korea hack Sony Pictures?
In this phase, is very difficult to attribute the cyber attack to a specific threat actor or to understand the nature of the offense. Is it an act of cybercrime or a state-sponsored attack run by a foreign government?
Who is behind the GOP group?
Though the investigation is at an early stage, Sony Pictures has reportedly begun investigating the possible involvement of hackers from North Korea. The news was reported by Re/code, which cited insider sources. The investigators speculate that North Korean hackers hit Sony Pictures operating from China.
"The timing of the attack coincides with the imminent release of 'The Interview,' a Sony film that depicts a CIA plot to assassinate North Korean leader Kim Jong-Un. The nation's ever-belligerent state propaganda outlets have threatened 'merciless retaliation' against the U.S. and other nations if the film is released," states the Re/code portal.
According to the BBC, North Korea has refused to deny involvement in a cyber-attack on the Sony Pictures network. When asked about the cyber attack, a spokesman for North Korea's UN mission replied:
"The hostile forces are relating everything to the DPRK (North Korea). I kindly advise you to just wait and see."
The Reuters News Agency reported the comment of another North Korean diplomat, which confirmed that his country didn't do it. The New York-based official speculated on a media fabrication to blame the North Korean government.
"[It's] another fabrication targeting the country," commented the diplomat. "My country publicly declared that it would follow international norms banning hacking and piracy."
The FBI is warning US businesses on risks of destructive malware-based attacks
Following the severe data breach at Sony Pictures Entertainment, the Federal Bureau of Investigation issued an alert to U.S. businesses on possible destructive malware-based attacks.
A five-page document was sent to security staff at some US companies via email. The Bureau also requested to avoid sharing it. The news was reported by the Reuters Agency. The FBI alert describes possible attacks that could use a wiper malware as an attack vector.
The FBI issued a confidential "flash" warning to US businesses on Monday, which includes technical details about the malicious code in the attack and suggestions to implement an effective incident response.

Figure 6 - FBI flash warning on Wiper Malware
The recent attack against Sony Pictures is alarming the national authorities. Intelligence agencies and law enforcement fear that a major destructive cyber attack could compromise the operation of other companies on U.S. soil with serious repercussions on the economy.
The activities to restore normal operations are time-consuming and expensive. As explained in the confidential warning, they often require technicians to either manually replace the compromised systems or remove the threat agents from their components.
A crucial factor to consider while analyzing the attack is that the data breach at Sony Pictures is the first attack that hit a multinational firm in the US to have such destructive effects. A similar attack caused the block of operations at the Saudi Aramco firm in 2012, when a virus infected 30,000 workstations and all the company servers targeted were cleaned and restored, causing the block of the company activity.
"I believe the coordinated cyberattack with destructive payloads against a corporation in the U.S. represents a watershed event," said Tom Kellermann, chief cybersecurity officer with security Trend Micro Inc. "Geopolitics now serve as harbingers for destructive cyberattacks."
The warning issued by the FBI reports that the malware delete all data on hard drives of the target computer, including the master boot record to prevent victims' machines from booting up.
"The overwriting of the data files will make it extremely difficult and costly, if not impossible, to recover the data using standard forensic methods," states the report.
At the time of this writing, Sony Pictures hasn't provided an official comment on the warning issued by the FBI. The FBI warning did not include the name the victim in the warning, but two cybersecurity experts who analyzed the document confirmed to the Reuters that "it was clearly referring to the breach at the California-based unit of Sony Corp."
"This correlates with information about that many of us in the security industry have been tracking," said one of the people who reviewed the document. "It looks exactly like information from the Sony attack.
"The FBI routinely advises private industry of various cyber threat indicators observed during the course of our investigations … This data is provided in order to help systems administrators guard against the actions of persistent cyber criminals," said FBI spokesman Joshua Campbell, confirming the distribution of the alert to private US businesses.
The Wiper malware
Security experts at TrendLabs have detected a sample of malware that appears to have been used in the attack against Sony Pictures systems by the GOP (Guardians of Peace) hacking crew. The hackers have compromised the entire network and have stolen a huge amount of data, including unreleased movies, employee data and business sensitive information.
Sony Pictures Entertainment is investigating the incident with the FBI and the private firm FireEye – Mandiant that was hired by the company to support its incident response activities. A few days after the attack, the FBI issued an alert to warn US companies of a destructive malware that had been used in an attack against a target in the U.S. Despite that the FBI memo doesn't explicitly mention Sony Pictures, security experts are convicted that the Federal Bureau of Investigation is referring to the attack on the entertainment company.
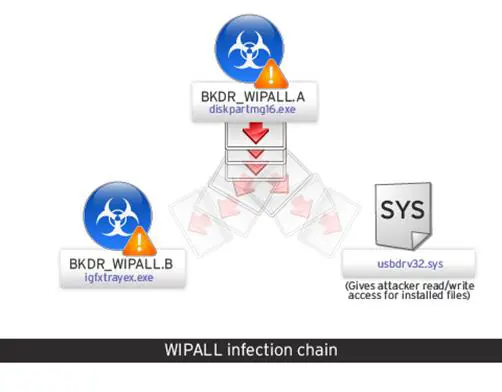
Experts at Trend Micro have detected the malware as BKDR_WIPALL, malware that in the first stage of the attack chain starts with BKDR_WIPALL.A, which is the main installer, and it is disguised as an executable file named "diskpartmg16.exe."
Figure 7 - DKDR Wiper malware (Trend Micro)
The malware BKDR_WIPALL.A protects a set of usernames and passwords with encryption (XOR 0x67) to gain access to the targeted organization's shared network.
"These user names and passwords are found to be encrypted by XOR 0x67 in the overlay of the malware sample and are then used to log into the shared network … Once logged in, the malware attempts to grant full access to everyone that will access the system root," states Trend Micro in a blog post.
BKDR_WIPALL.A, once infected in the system, drops the BKDR_WIPALL.B agent, which is disguised as a file named "igfxtrayex.exe" and is the malware component responsible for causing damage. Once BKDR_WIPALL.B is dropped, it sleeps for 10 minutes before starting to delete files and stopping the Microsoft Exchange Information Store service. The malicious code then sleeps for two hours and forces a system reboot.
BKDR_WIPALL.B is very aggressive and invasive. It implements a feature that allows it to execute copies of itself with various parameters. With this mechanism the malware carries out several tasks, including deleting files and dropping additional components. The additional component "usbdrv32.sys" for example gives attackers read/write access to installed files.
Why do experts believe that the malware is the same as that used in the Sony Pictures cyber attack?
The experts at Trend Micro discovered a different variant of the malware, dubbed BKDR_WIPALL.D, which drops BKDR_WIPALL.C. This agent in turn drops an image file called "walls.bmp," which is the "Hacked by GOP" image that was seen by the employees at Sony Pictures on the display of their infected computers.
"This appears to be the same wallpaper described in reports about the recent Sony hack last November 24 bearing the phrase 'hacked by #GOP.' Therefore we have reason to believe that this is the same malware used in the recent attack to Sony Pictures," states Trend Micro.
The Wiper malware was written in korean
New evidence has emerged from the investigation of the Sony Pictures data breach. Experts at Alien Vault provided further information on the malware that was used in the attacks, which now appears to be linked to North Korea.
The AlienVault labs director, Jaime Blasco, analyzed a sample of the wiper malware detected by company's honeypots, provided by the FBI in the recently released flash warning. The experts revealed that the malware was compiled a few days before the Sony Pictures attack (between November 22th and 24th) by a computer with Korean language text settings.
Analysis conducted by AlienVault revealed that the source code was specifically designed to target the Sony Pictures. The source code examined by Alien Vault used a simple login and password to gain access to Sony Pictures corporate network. This suggests that the hackers had already targeted the company; by, for example, stealing network credentials in an earlier spear phishing attack.
Experts believe that attackers reused the code from preexisting wiper malware, with their analysis revealing that it was customized and deployed by Korean speaking hackers.
Stay tuned for further information!
Sources
http://krebsonsecurity.com/2014/12/sony-breach-may-have-exposed-employee-healthcare-salary-data/
http://www.bbc.com/news/technology-30328510
http://www.reuters.com/article/2014/12/02/us-sony-cybersecurity-malware-idUSKCN0JF3FE20141202
http://www.reuters.com/article/2014/12/04/us-sony-cybersecurity-nkorea-idUSKCN0JI1NZ20141204?feedType=RSS&feedName=technologyNews
http://gizmodo.com/north-korea-no-we-didnt-hack-sony-1666246282?rev=1417711559470&new_editor_css
http://securityaffairs.co/wordpress/30724/cyber-crime/fbi-warns-major-malware-based-attacks-following-sony-pictures-hack.html
http://www.bbc.com/news/world-asia-30283573
http://www.reddit.com/r/hacking/comments/2n9zhv/i_used_to_work_for_sony_pictures_my_friend_still/
http://www.vice.com/read/was-north-korea-behind-the-cyberattack-on-sony-1203
Phishing simulations & training
http://www.csoonline.com/article/2852982/data-breach/sales-contracts-and-other-data-published-by-sonys-attackers.html