MITRE ATT&CK vulnerability spotlight: Access token manipulation
Introduction
MITRE is a U.S. government federally-funded research and development center (FFRDC) which performs a large amount of research and assessment as a trusted third party for the government. One of their research areas is cybersecurity, and they have developed the MITRE ATT&CK matrix to help with research and education about cybersecurity threats.
The MITRE ATT&CK matrix breaks the process of a cyberattack into its different stages. For each stage, ATT&CK describes the various means by which the objectives of that stage can be accomplished by an attacker. The matrix is a useful tool for cybersecurity professionals because it can be used as a basis for a formalized threat assessment and detection process.
What is access token manipulation?
Access token manipulation is one of the techniques included in the MITRE ATT&CK matrix under privilege escalation. The intention of access token manipulation is to grant a malicious process the same permissions as a legitimate user and to pretend to be a process started by that user. This may increase the capabilities of the malicious process or reduce its probability of detection.
Access tokens are designed as a security feature on Windows. Their purpose is to describe the exact permissions that a particular user should have on a computer. This allows for a great deal of granularity of permissions on a system and the implementation of least privilege, since permissions can be individually granted or denied to a particular user.
Access tokens are generated once a user has authenticated to a Windows system. Once the user’s login credentials are generated, they are given an access credential that encodes their particular permissions on the system. When a user launches an application, a copy of their access token is given to that application as well. This ensures that processes or threads run by a user are limited to the same permissions as the user.
Performing access token manipulation
The goal of access token manipulation is to change the permissions of a particular application by associating it with the access token of another user. There are three main applications of this:
- Granting an application SYSTEM permissions
- Attributing a process to another user
- Gaining access to a user’s account on a remote system
Getting the token
An attacker who wants to perform access token manipulation first needs to have a token of the target account. This can be accomplished either by logging in as the user or by token stealing.
Logging in as the user is the easier option if the credentials of the target account are known. This technique is useful if an attacker has stolen a user password and wants to attribute malicious activity to another account to avoid detection. However, it is of limited use for privilege escalation.
Token stealing involves copying the token by used by running processes of the target account. This technique is much more flexible; however, it requires administrator permissions to perform. The most common use is to escalate Administrator privileges to the SYSTEM level on Windows. Token stealing is performed using the DuplicateToken(Ex) API call on Windows.
Using the token
Once an attacker has access to the desired token, they can use it in an access token manipulation attack. Two different options exist for using the acquired token:
- Token Impersonation/Theft: Once a token has been stolen, a process can use ImpersonateLoggedOnUser to associate with the current thread or SetThreadToken to assign it to another thread
- Create Process with a Token: Using the CreateProcessWithTokenW API call, a new process can be created with a stolen token
Using these methods, an attacker can create a process that operates with all of the permissions of a given user and pretends to have been executed by that user.
Examples of access token manipulation
Access token manipulation is commonly used for malicious purposes. However, it was designed as a security measure on Windows. The principle of least privilege states that no application or user should be granted any more privileges than the minimum necessary to perform their job roles.
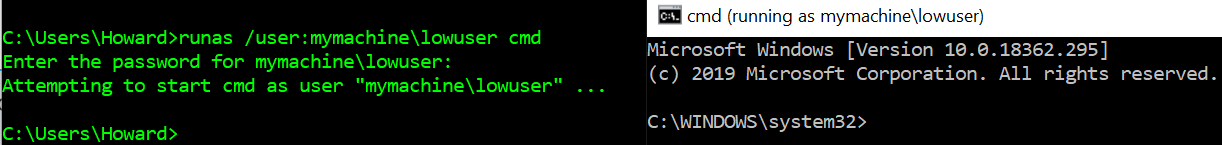
Access token manipulation can be used to enforce least privilege. If a user wants to run an application, such as a web server, they may want to run it in its own account with privileges limited to those necessary for a web server. To accomplish this, they can use the runas command.
The image above shows the result of using the runas command to start the Windows command line running in another Windows account. runas does not require elevated privileges, and any account can use it if they know the target account’s password.
In this case, runas was used to run the command prompt using another account with extremely limited privileges (lowuser). The command prompt can now be used to run untrusted commands in a more secure manner. This is because if the application is compromised, it will not have the more elevated privileges of the other account.
Detection and mitigation
Access token manipulation takes advantage of built-in Windows functionality. The use of access tokens is considered to be a Windows security best practice, so blocking use of the functions in question is not a viable solution.
However, monitoring the use of the Windows functions that are necessary for access token manipulation can help with detection of this attack vector. The following actions should be monitored to detect access token manipulation:
- runas (command-line instruction)
- LogonUser (API call)
- DuplicateTokenEx (API call)
- ImpersonateLoggedOnUser (API call)
While these commands and API calls can be used for legitimate functions, monitoring their use and investigating the processes that use them can help detect attempts to perform access token manipulation.
Conclusion: Protecting against access token manipulation
The ability to manipulate access tokens is an intentional part of the Windows security model. Using access token manipulation, users can implement the principle of least privilege by operating in a low-privilege account on a day-to-day basis and only running applications with elevated privileges when necessary.
The potential for access token manipulation attacks can be mitigated through monitoring for use of the commands and API calls used to perform them. Since the most common attack target is SYSTEM-level commands, watching for access token manipulation targeting a SYSTEM token is a good security precaution.
Sources
- Access Token Manipulation, MITRE
- Access Tokens, Microsoft
- Privilege escalation through Token Manipulation, HacknPentest