Secure process audit
Introduction
A secure process audit is a type of security audit in which the tester (auditor) tests the application or server or any network device where he or she captures and analyzes a detailed view of the application workflow, functionalities and their process and then identifies the loopholes and security misconfigurations.
The objective of this activity is to assess and discover weak links, immunity level, security misconfigurations and so on. Generally, a tester needs to install the application on the system, followed by installing a few testing tools. It depends on the client and their network infrastructure; many organizations may call a penetration tester to their premise due to criticality of their network infrastructure.
Some of the following measures and controls that must be a part of this assessment are as follow:
- A packet transmission review
- Inspect the entry in Registries (before, during and after the running phase of an application)
- Analyze if an application is creating or storing any sensitive information in the parent directory, logs, config files and so on
- Analyze memory and CPU performance during the running phase of an application
- Review the deployment diagram and find loopholes in all of the above
How to perform process auditing
Tools: Echo Mirage, Wireshark, Regshot, TCPView, Process Hacker, Strings, CFF Explorer, WinHex, Fiddler, Nmap, Process Monitor and more
Ask for the network and deployment diagram and have a detailed understanding of the network flow and how the process is getting initiated. The deployment diagram should cover each detail being deployed in real scenario. A detailed understanding of each node and function is required.
Inspect and analyze to see if the firewall is being placed in the right location and if the organization needs to have one more firewall at another node (to provide more security). Internal and external firewalls are recommended or even mandatory for every organization. An external firewall is placed between the application and the external network gateway. An internal firewall is placed between internal systems (servers, database and so on).
Check if a packet is flowing though the firewalls. If not, advise them to re-route the packet flow and network transmission through the firewalls. Also, inspect firewall rules and policies to check whether there is any security misconfiguration present. Inform the network team immediately that they need to make necessary changes and controls. Each critical database should be segmented from the rest of the system. Data should be encrypted and should be only managed locally. By doing the above, we wrap up for the first step and jump on to the second.
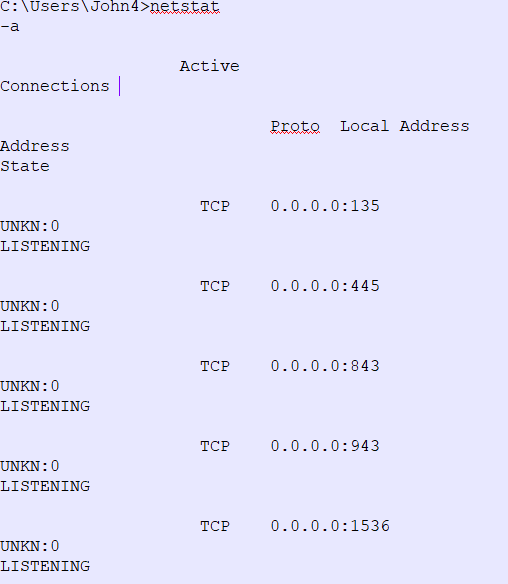
Next, observe the network transmission. Ask for the public IP address and private IP address of the server and do a port scan to check if any unnecessary services are running or unnecessary ports are open. Analyze the connection using the Netstat command [netstat -a] in three phases:
- While running the application
- Before starting the application
- After stopping the application
Install Wireshark and run it in the background throughout the process; verify and analyze the packet transmission to the application and server and vice versa. Transmission of each packet should always be transmitted over a secure communication channel.
Logs contain crucial information maintained by an organization. Check to see if the application/network device is maintaining any kind of logs. It also helps to suspect an attack during bad times.
There should be a dedicated log server deployed within the network infrastructure and must be completely secured. Check if any sensitive information is being stored in logs, such as bank details, personal and private details, health information data and so on. If this information must be stored in the logs (e.g., if it is a business requirement), make sure that it is masked or encrypted. If the data is not encrypted, an attacker compromising a log server would be a huge loss to an organization.
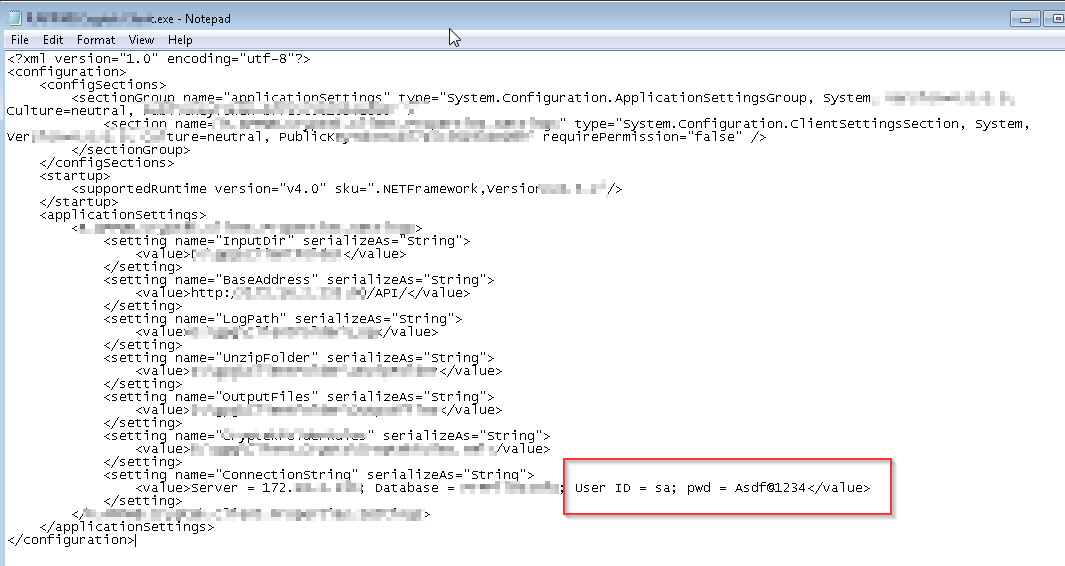
Analyze the parent directory to see if any sensitive and insecure information is being stored. Inspect the configuration file carefully. Along with this, also check for the registries to analyze the read and write permissions. Encryption of the config file is as crucial as protecting your network infrastructure via firewalls.
Check for the database and its connection settings. Inspect the configuration file and analyze it to see if any kind of connection string is getting exposed in plaintext.
Observe the CPU and memory utilization while running the application. Memory usage should be moderate and as low as possible. Also check for running threads from the application. If CPU utilization is above 85%, report this immediately, as applications may crash afterwards. There would always be a threat of malware getting executed along with an application, which can secretly initiate a connection and send packets to an anonymous server. There are several cases in which such scenarios have been seen.
Refer to the proof of concept below for a better understanding.
Proof of concept
- Download any demo application from which you can start process auditing. (https://freefilesync.org/download.php).
- Install the application with all the requirements managed by it.
- Capture the application information like its hash, version, build name, company name and so on, for reporting purposes. You can do this by using the CFF Explorer tool:
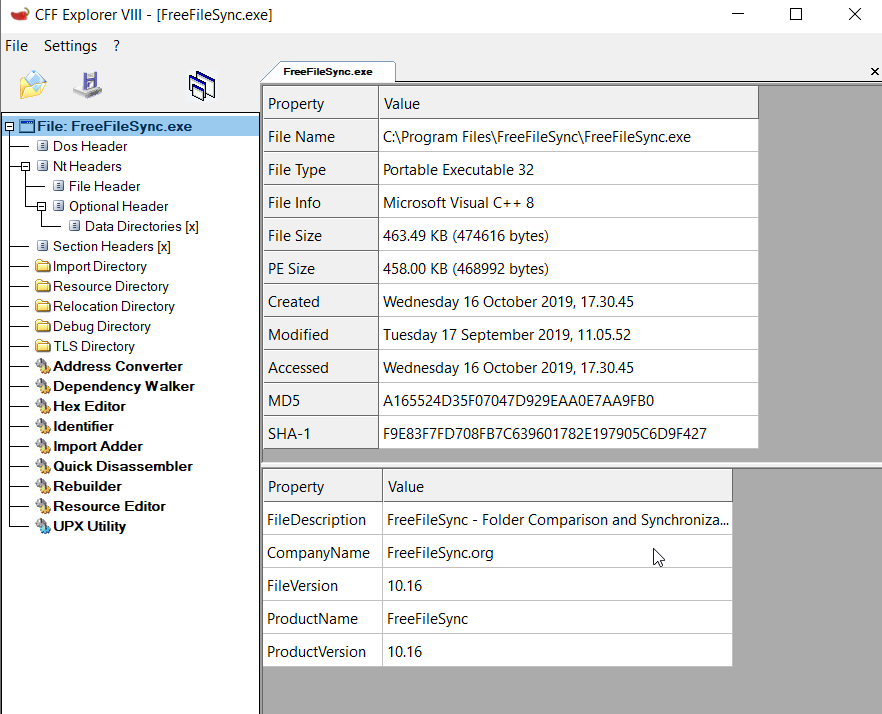
- Start Wireshark before starting off the application and let it run throughout the process.
- Run the netstat command before the starting off the application to identify the active listening connection. Keep using netstat while running the application modules to check if any unauthorized service is getting initiated at the back end.
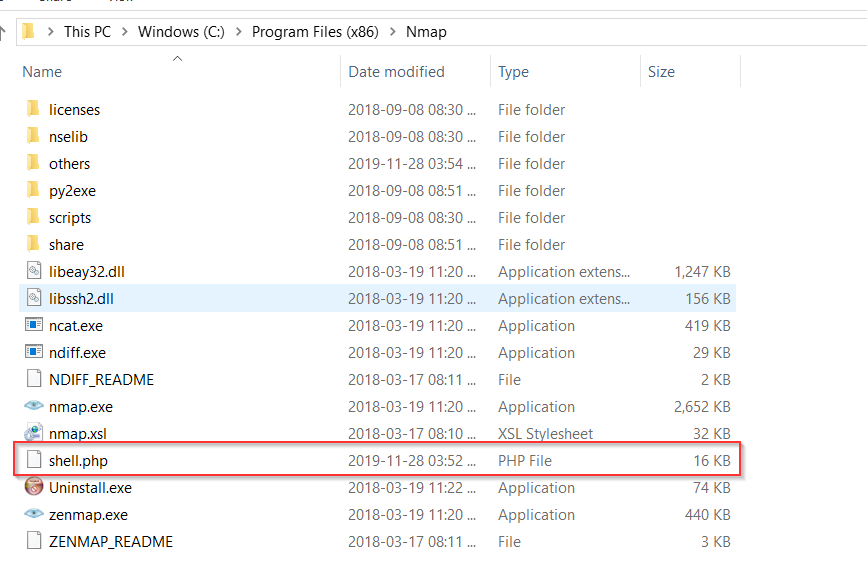
- Analyze the parent directory and config file of an application to check if any sensitive information is getting stored. Also check for any suspicious file other than application’s required system files in the parent directory.
Note: There is no such suspicious/malicious file in this case.
In the other case, as shown in the screenshot below, shell.php (which triggers remote code execution) is in the parent directory, which is a big alert to an organization. Remove the file immediately and dig more to find similar structured files.
Be cautious while inspecting the files and folders, and look out if you find a file with the below syntax code:
preg_replace ("/.*/e","x65x76x61x6Cx28x67x7Ax69x6Ex66x6Cx61
It is always a good practice to encrypt the whole config file to circumvent such information disclosure attacks.
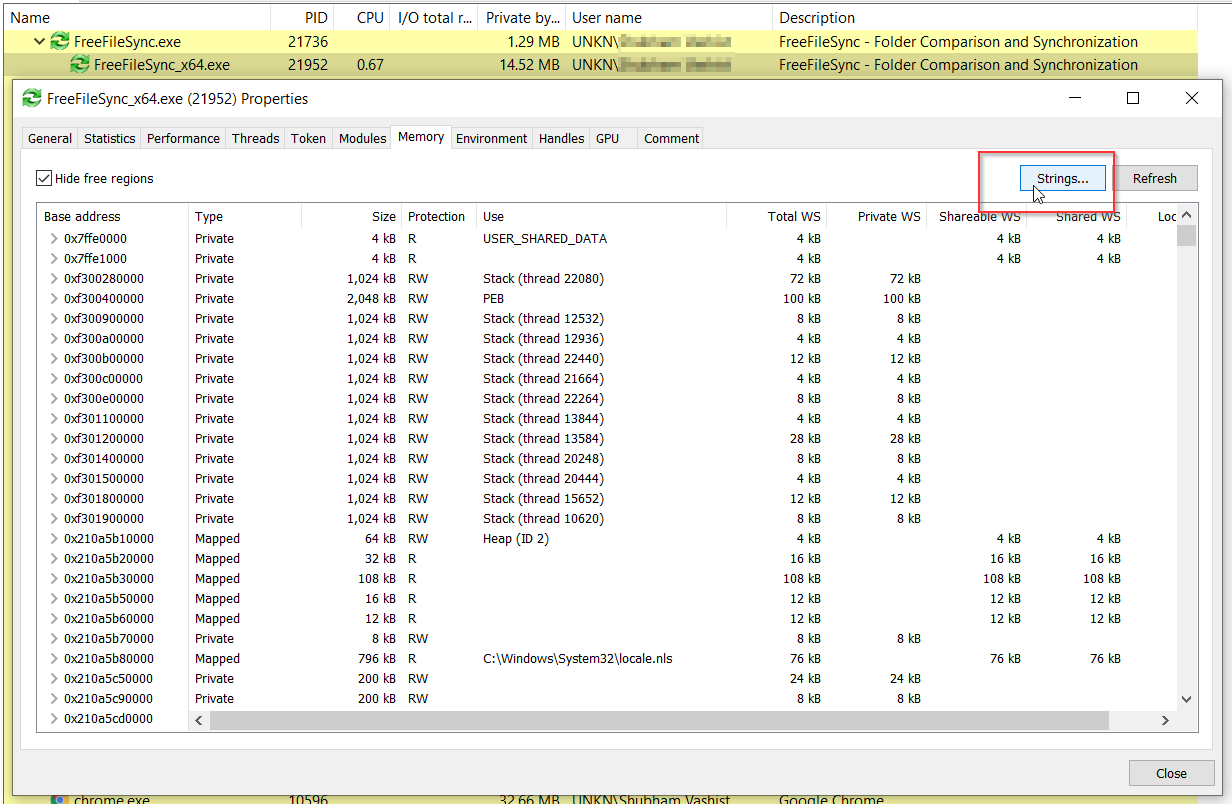
8.1 Double-click on the application name and click on Strings.
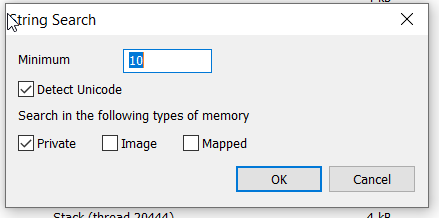
8.2 Set the Minimum String value to 10 and click OK.
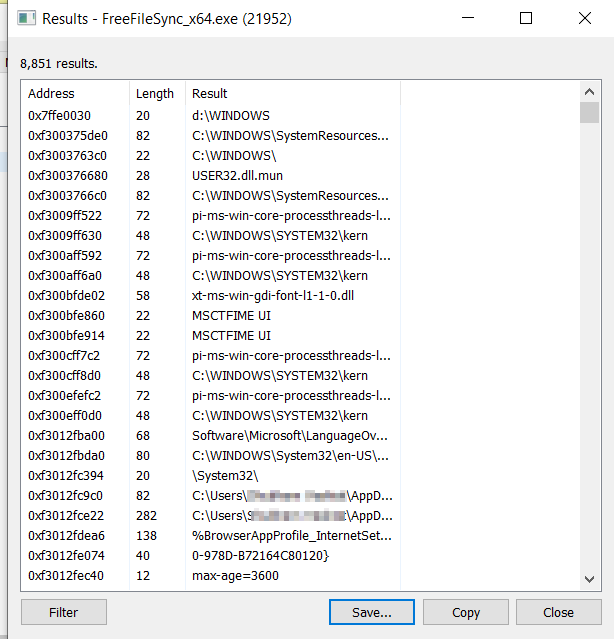
8.3 Lastly, save the string values and analyze for any sensitive information being stored. Check if any unauthorized service is being initiated along with an application. Focus more on files with *.exe/*.php/*.bat file extensions.
8.4 Open the saved text file in the notepad:
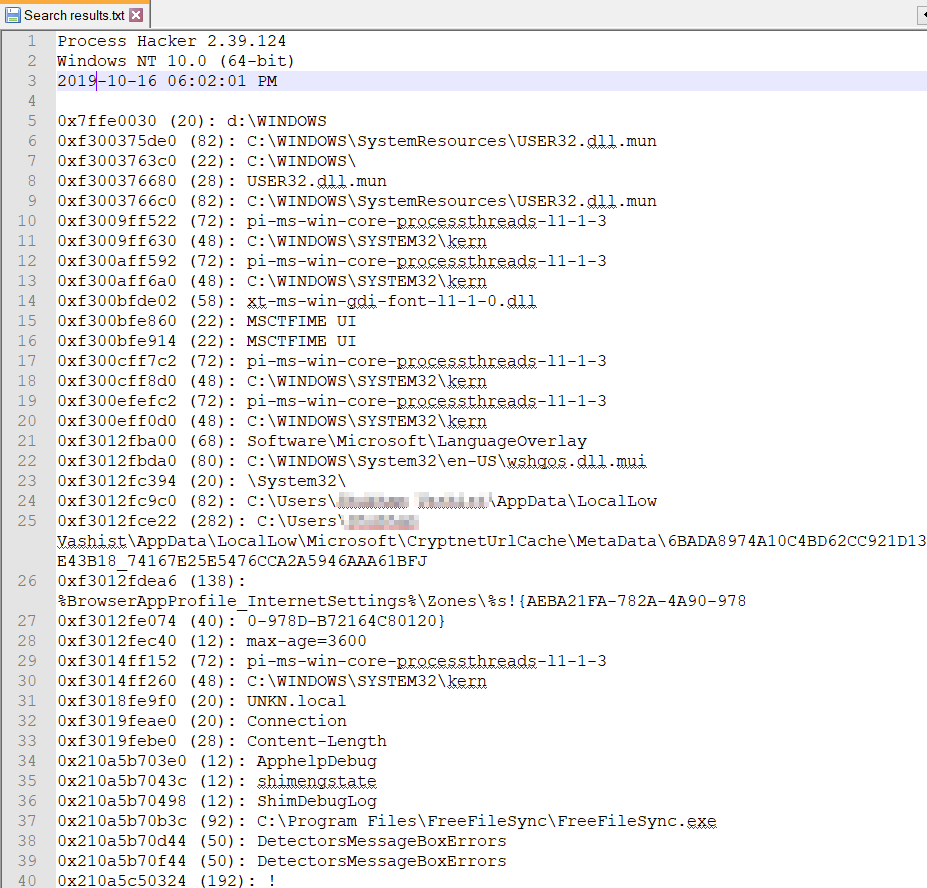
Here, refer to step 6 for a more detailed understanding of the procedure.
Conclusion
- Analyze everything about the workflow of each packet transmission and check to see if any security misconfiguration is getting exposed. Encrypt the sensitive information everywhere it is present and delete if it’s not required
- Performance also needs to be tested. If CPU usage is more than 85%, you need to keep your eye on the process and packet, as there is a possibility of malware getting executed along with an application that is utilizing more memory
- Analyze each file to check for any security misconfiguration and sensitive data exposure vulnerability. Encrypt it!
- Analyze the firewall rules and policies to check if they are in the best place
- Analyze each packet transmission to check if there is any sensitive data flowing in an unencrypted way or through unencrypted channel.
Sources
- Download Process Monitor 3.50 for Windows, Tom's Guide
- Download Process Hacker, Process Hacker
- Download FreeFileSync, FreeFileSync
- CFF Explorer, download.cnet.com
- Download Wireshark, Wireshark
- Memory Dump Analysis – Extracting Juicy Data, CQURE Academy