6 key elements of a threat model
How to identify threats and discover vulnerabilities with threat modeling
Threat modeling is a process for threat discovery and risk management. Any system carries potential risk, and a clear understanding of these risks is essential to managing them.
Threat modeling is the foundation of risk management, providing insight into the threats, vulnerabilities and risks that need to be managed.
Learn Threat Modeling
Threat modeling key elements
Mapping relationships is a key component of threat modeling. A clear understanding of the elements of a system and how they interact is essential to determining the potential risks associated with a system and how to mitigate or remediate them.
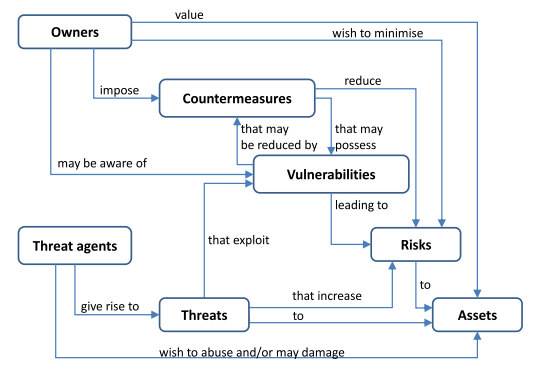
Figure 1: The relationships between elements of a threat model. (Source)
ISO/IEC 15408-1:2005 defines the key elements of a threat model. The diagram above (drawn from the standard) outlines the relationship between these various elements. Each of these elements has an essential role to play within a threat model.
1. Key stakeholders
The key stakeholders are the owners of the system. Their goal is to have a system that works well and carries a minimal amount of risk. Owners will use countermeasures to mitigate the risks to an asset.
A number of different types of stakeholders can exist for any asset. Some examples include the development and security teams, executives and product owners. In general, anyone within the organization who finds value in a particular asset and could suffer from it being compromised can be considered an owner or stakeholder.
2. Assets
An asset is something under the control of an owner or stakeholder and is valued by them. Examples of assets can be computing systems, data or anything that, if compromised, causes damage to the owners.
An important early step in a threat modeling exercise is identifying the assets that should be included in the model. Based upon this identification of assets, it is possible to identify the potential security risks and threats to these assets.
3. Security risks
Risk is a measurement of the potential for something to go wrong with a particular asset. It is calculated as the combination of the probability of a particular threat occurring and the impact if the event occurs.
Threat modeling and risk assessments are directly interrelated. Threat modeling activities identify the potential threats to a particular asset. Risk analysis takes the list of identified threats and identifies the probability and impact for each. The result of this analysis is used to identify and prioritize potential countermeasures that can be applied to reduce the risk to the asset.
4. Security threats and threat agents
Security threats and threat agents are distinct but related concepts. A threat agent is an actor that is motivated to abuse or cause damage to an asset. This includes cybercriminals, advanced persistent threats (APTs) and similar groups. Threat actors can be classified based upon their sophistication, goals, relationship to the system (insider versus external threat) and the amount of trust that they possess on the system.
Threats are the results of actions by threat actors. Threats are the combination of three factors:
- Hostile intent: For a threat to exist, a threat actor needs to have the desire to abuse or cause damage to some asset.
- Capability: For a potential threat to be realized, an attacker needs to have the ability (skills, tools, knowledge and so on) to carry it out.
- Opportunity: For a potential threat to be acted upon, an attacker needs an opportunity to carry out their objective.
With the combination of hostile intent, capability and opportunity, a threat actor can pose a real threat to a system, increasing its risk. Threat mitigations should work to eliminate one or more of these three essential components.
5. Security vulnerabilities
A vulnerability is an example of a realized threat to a system. They are potential attack vectors that carry cost to the organization (time, money, resources and so on) if exploited.
Mitigating vulnerabilities is the primary objective of countermeasures like security controls and mitigations. A one-to-one relationship should exist between threats, vulnerabilities and countermeasures, and countermeasures reduce the risk to an organization’s assets.
6. Security controls and mitigations
Security controls and mitigations are countermeasures that are designed to eliminate or mitigate threats and vulnerabilities. These countermeasures decrease the probability that a threat becomes a vulnerability and that an attacker can exploit this vulnerability to cause harm to assets.
Countermeasures can be implemented as technical mitigations or business decisions. A technical mitigation is designed to reduce the risk associated with a potential threat or vulnerability. A business decision is the choice to accept the risk of a potential threat or vulnerability because the probability and/or impact is determined to be acceptably low. A threat model maps identified threats to the countermeasures that address them.
Learn Threat Modeling
Managing risk through threat modeling
Every system carries risk, and the primary goal of risk assessment and management processes is to ensure that this risk is acknowledged and managed. While completely eliminating risk is impossible, risk management enables an organization to make informed decisions about actions to take regarding these risks.
Threat modeling is an essential component of the risk management process. Threat modeling identifies the potential threats that create risk for an organization’s assets. Based upon this information, risk management processes can assign probabilities and impacts to threats and identify countermeasures designed to reduce or accept these risks.
Sources
ISO/IEC 15408-1:2005, ISO
ISO/IEC 15408-1:2009, ISO