How to Become an Information Systems Security Auditor
Cybercrime numbers never fail to impress. According to Ponemon’s 2017 Cost of Cyber Crime Study, the number of security breaches increased over 27% in 2017. Data breaches and cyber threats are also costing organizations 23% more when compared to 2016. Often these expenses result from incident response actions, such as managing incidents and recovering from a security-related disruption that affects both the organization and their customers.
This extreme level of impact is one of the most obvious reasons why cybersecurity professionals are in high demand. However, while cyberattacks steadily increase in both number and sophistication, the availability of skilled security professionals is not keeping pace.
This cyber skill shortage is so huge that ISACA estimates there will be a global shortage of two million cyber security specialists by 2019. For professionals thinking about working with information security, this is probably one of the best moments to maximize knowledge and invest in career development.
What Does an Information Systems Security Auditor Do?
An information systems security auditor is just one of many career options in the information security industry. It is an excellent choice, since there is a high demand and salaries can pay up to $99,000 per year.
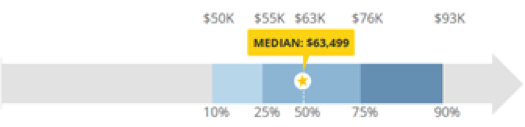
Information Technology (IT) Auditor Salary. Source: https://www.payscale.comAuditors are essential to most information security efforts. They are not directly responsible for implementing or running security controls, instead an auditor can provide an independent view, ensuring the integrity and security of information systems by testing the safety and effectiveness of cybersecurity components. They also check for compliance with any laws and regulations a company must follow.
The most common tasks associated with this role include:
- Documenting the audit process planning
- Executing security audits
- Evaluating security policies and controls
- Writing both executive and technical reports analyzing and interpreting audit results
- Evaluating compliance with any applicable policy, law or regulation
An information systems security auditor can also play a key role in corporate risk management, although not directly. For instance, having an internal audit team working closely with the risk management team can lead to better results and continuous improvement on risk reduction. However, for clear governance purposes and to ensure the independence of either role remains uncompromised, it is crucial to make sure they report to separate senior managers.
What is a Security Compliance Audit?
In general terms, auditing for compliance is a comprehensive in-depth review of an organization's adherence to corporate or regulatory mandates. Essentially, an audit makes sure the business is meeting organizational and legal requirements. In the case of an information security compliance audit, the auditor focus should be collecting sufficient evidence to independently ascertain if a company’s security controls, either technical, physical or administrative, conform to a set of established criteria.
Of course, there is a great level of variance on what this “established criteria” is. For instance, an internal security compliance audit may require evaluating specific systems configurations, checking if the latest security patches are being applied, or reviewing the data center physical access records. It all depends on factors such as the industry branch, country and even geographic region.
As for external compliance, audits may include an adherence validation with both best practices and security practice requirements imposed by industry or government bodies. These could include:
- Sarbanes Oxley (SOX) for publicly traded companies
- Payment Card Industry Data Security Standard (PCI DSS) for retailers
- Defense Information Systems Agency Security Technical Implementation Guide (DISA STIG) standard for U.S. federal contractors and agencies
- General Data Protection Regulation (GDPR) for organizations that collect or process data from EU residents
Security compliance can also be an important part of a corporation’s strategy. For example, having an ISO/IEC 27001 certification is quite a marketable feat, as it means the organization’s information security management system (ISMS) is adherent to the best-known international security standards. That however, can only be obtained by organizations deemed as compliant by an independent and accredited certification body on successful completion of a formal compliance audit.
Auditing for compliance requires both a sound understanding of the criteria being evaluated and the expertise to conduct the audit itself, including aspects such as planning, evidence gathering and, specially, being able to report any findings both from a technical and a business (i.e., executive) point of view.
How Can I Become an Information Systems Security Compliance Auditor?
The first steps into the security auditor career are quite basic — the role requires both education and experience.
Step 1: Education. In most cases, having an bachelor's degree in IT or, even better, an information security related area, is necessary. It is important to understand that there are cases where security auditors are not required to have a technical background, especially for a compliance audit. So, professionals from areas such as law and administration may also follow this career path.
Step 2: Gain work experience. An audit internship is an excellent option, but having firsthand experience in related areas (e.g., IT, IT security or risk management) will also be of great value.
Step 3: Get certified. As a final recommendation, certifications also are a common requirement for security auditors. In this context, ISACA’s Certified Information Systems Auditor (CISA) is considered the preferred IS audit certification program by individuals and organizations around the world. It is designed for professionals that specialize in information systems auditing, with skills to understand aspects such as the necessary controls and security features.
The CISA certification encompasses five domains:
- Protection of information assets
- Process of auditing information systems
- Governance and management of IT
- Information systems acquisition
- Development and implementation
- Information systems operations
- Maintenance and service management
A detailed review of the certification process (and some essential tips for the exam!) can be found in another InfoSec Institute article: 10 Tips for CISA Exam Success. In short, it suffices to say the CISA is quite a challenge, and this high level of requirements assures companies around the world that CISA professionals are both highly qualified and experienced in every IT audit aspect, making it a typical requirement for senior IT auditor positions.
As a career advancement, earning the CISA should be a top priority for professionals that wish to become an information systems security compliance auditor. This certification, when combined with the other items in Step 1 and 2, should be more than sufficient to stand out in this era of cybersecurity skills gap.
Sources:
- PayScale, https://www.payscale.com/research/US/Job=Information_Technology_(IT)_Auditor/Salary
- Ponemon’s 2017 COST OF CYBER CRIME STUDY, https://www.accenture.com/t20171006T095146Z__w__/us-en/_acnmedia/PDF-62/Accenture-2017CostCybercrime-US-FINAL.pdf