The essentials of an acceptable use policy
What is an acceptable use policy?
An Acceptable Use Policy (henceforward mentioned as "AUP") is agreement between two or more parties to a computer network community, expressing in writing their intent to adhere to certain standards of behaviour with respect to the proper usage of specific hardware & software services. More specifically, it is a set of rules created and enforced usually by an owner or manager of a website, network, online service, or larger computer infrastructure that aims to restrict the unseemly ways their information assets may be used. In order to minimize the risk of legal action, business entities such as corporations, ISPs, website owners, schools and universities choose to implement an AUP. Hence, an AUP gives directions on what behaviour and use of technology is approved by the owner or the community as a whole.
Similar to the terms of service
AUP documents often fulfill the same function as the ubiquitous Terms of Service or End-user License Agreement texts that can be found on virtually all software applications. However, there are slight differences between those documents. By comparison, first, AUPs cover larger computing resources, e.g., websites or LAN; second, they emphasize etiquette and respect for fellow users (presumably not applicable to single-user programs or other computer services).
Connection to IT security
There is a great deal of details in an AUP relating to computer security – managing passwords, online intellectual property and software licenses. Other chapters can give an account of basic international etiquette (e.g., a short description of firm's email policy), or deal with excessive use of system resources, for instance, the superfluous traffic generated by playing computer games.
Intended subjects
AUPs seem handy in situations where new members sign on to join an information system or network. For this reason, an AUP must remain clear and concise, inter alia, and cover the points of vital importance regarding what behaviour is permissible and what is not when it comes to usage of company's IT system. Where relevant, users should be referred to a more comprehensive policy.
In public organizations such as libraries or universities, AUPs may be used to protect young people from profanity, pornography and bad influence. On the other hand, the policies in question at corporate level spread out to include business interests.
To this end, a useful aspect concerning AUPs is that they, as an integral part of the entire monitoring procedure, can be an effective tool in identifying cyber-slackers and abusers among employees within an organization. Human Resources experts and the courts are certain that this measure may provide the needful evidence of a "duty of care" that will reduce the unacceptable employee activity. As a generally accepted rule, monitoring Internet and email services is considered legal provided that the employer has communicated an AUP to his employees. Getting prior consent may allow employers to come off clear and not be held liable for some mischiefs in contravention of the policy done by their employees.
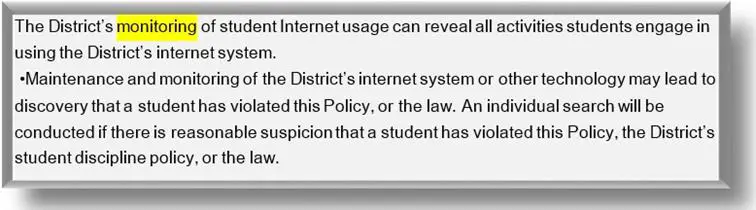
Source: Student Internet/Software Acceptable Use Policy by MSD Decatur Township

Source: How to Create an AUP - Acceptable Use Policy byMitchell Bradley
Moreover, policies like those against racial or religious discrimination and compulsory email archiving are stipulated by law or regulation, and others, such as sexual harassment or prohibition against smoking outside designated areas may be seen as necessary from a common business ethics point of view. What is important is that all of them can be expressed in an AUP – an employee handbook of a kind – simplifying their applicability on the ground and at the same time making them translatable to every worker regardless of rank and status.

Source: How to Create an AUP - Acceptable Use Policy by Mitchell Bradley
- Structure
- Preamble or Purpose
This is an introductory part that clarifies the application of what follows in terms of policy text. Basically, it explains why this document is needed, its aims, and perhaps an indirect reference about the motives behind its coming into existence.

Scope
The range and coverage of AUPs vary more or less. A policy could apply to specific users, departments, regions, systems, components, software or data that are employed or connected to the owner's network/computer systems.
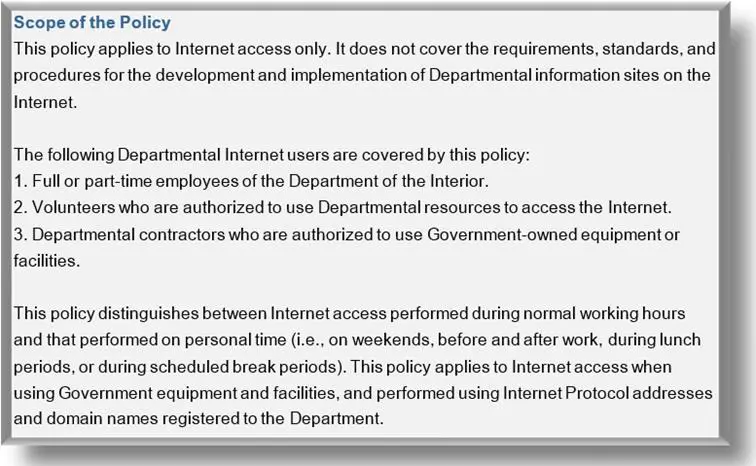
Source: INTERNET Acceptable Use Policy by U.S. Department of the Interior
Policy
That's the policy's pulp (usually the most delicious or essential part of a fruit) in which are accentuated requirements users must observe. Frequently, there will be a list with prohibited activities. It is important to remember that at the heart of the AUP as a regulatory document is the concept of respect and ethical use. Thus, AUPs rely on the good behaviour demonstrated by everyone under its influence, trying to instill what is appropriate "by persuasion". If the power of persuasion proves itself insufficient, then one should face the consequences.
Presumably, the section that outlines the unacceptable uses of given online service has a central part in almost all AUP documents. Unacceptable behaviour may include:
- creation and distribution of material that is indecent, obscene, offensive, or causes inconvenience, annoyance, or anxiety to other users or service providers (i.e., technical staff). Several examples:
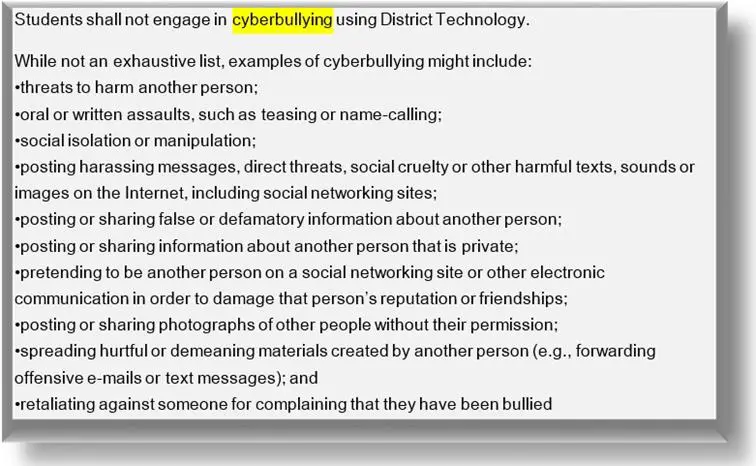
Source: Student Use of Technology/Acceptable Use Policy by Fountain Valley School District
- unsolicited messages, regardless whether of commercial/advertising character or not, sent deliberately to other users
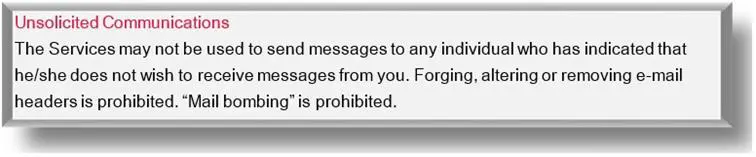
Source: Acceptable Use Policy by Rogers Communications Inc.
- violating the privacy of others online
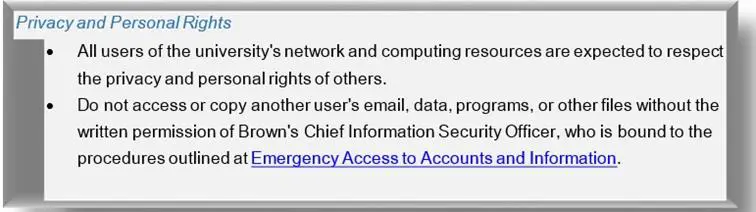
Source: Acceptable Use Policy by Brown University
- misusing the network in such a way to deny the services to all the rest of the users (that is DDoS attacks).

Source: Acceptable Use Policy by Rogers Communications Inc.
- "waste of time" activities performed by a malevolent or negligent user that require technical staff to troubleshoot the problem.
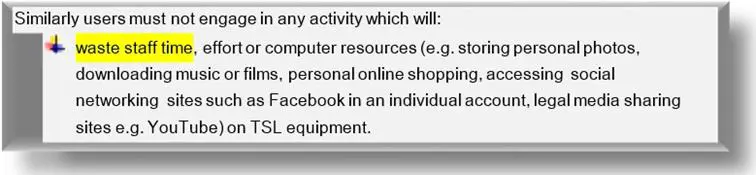
Source: ICT Acceptable Use Policy by Training Strategies Ltd.
- any other kind of technical misuse, such as releasing viruses into the network.
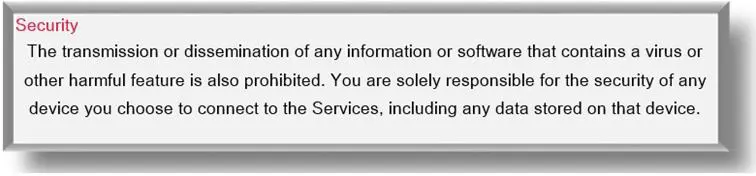
Source: Acceptable Use Policy by Rogers Communications Inc.
- creation and distribution of any kind of illegal content (e.g., defamatory, infringing copyright acts or such unauthorized by nature).
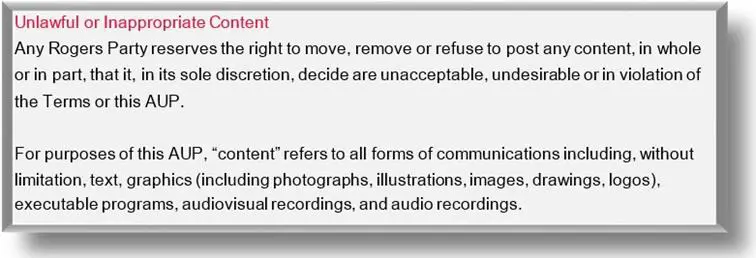
Source: Acceptable Use Policy by Rogers Communications Inc.
Disclaimers can be found most of all on AUPs referring to the use of websites. They exonerate an organization from responsibilities under specific circumstances. After all, connection to the Internet or use of a website is a privilege, not a right, as stated by the AUP of the Loughborough Universiy.
Sanctions
In many AUP statements there is a text that sets forth the consequences of violating the policy – sanctions applicable to everyone that breaks the AUP. For instance, subscribers to broadband Internet service may be subject to either bandwidth limitation, suspension, or termination of contract on a variety of grounds. If the activities are illegal, the company may call on law enforcement authorities. When the violator is an employee, then the company may terminate the employment. It is important to note that the policy has pretty much direct effect and could be enforced without legal proceedings.

Source: Acceptable Use Policy by Rogers Communications Inc.
Conclusion
Ideally, an AUP should do the following:
 Clearly specify the owner(s);
Clearly specify the owner(s);
 Define the exact components covered by the policy: Internet, email, voice mail, computer systems and files;
Define the exact components covered by the policy: Internet, email, voice mail, computer systems and files;
 Underline that these components are for business purposes only;
Underline that these components are for business purposes only;
 Incorporate "use cases," "situational analyses," or "what if" scenarios illustrating how the policy works in reality;
Incorporate "use cases," "situational analyses," or "what if" scenarios illustrating how the policy works in reality;
 Ban content that is harassing, offensive, defamatory, insulting, discriminatory, pornographic or obscene;
Ban content that is harassing, offensive, defamatory, insulting, discriminatory, pornographic or obscene;
 Prohibit distributing confidential or proprietary information, including copyrighted software, or unauthorized access by electronic means performed by employees;
Prohibit distributing confidential or proprietary information, including copyrighted software, or unauthorized access by electronic means performed by employees;
 Underline the repercussions non-compliance would entail. Warn policy's recipients that they may be subject to disciplinary measures in case of violation of the policy.
Underline the repercussions non-compliance would entail. Warn policy's recipients that they may be subject to disciplinary measures in case of violation of the policy.
Sources
- Brown University (2003). Acceptable Use Policy
- Education World Inc. Getting Started on the Internet: Developing an Acceptable Use Policy (AUP).
- Fountain Valley School District (2010). Student Use of Technology/Acceptable Use Policy
- GFI (2011). The Importance of an Acceptable Use Policy
- Mitchell Bradley.Acceptable Use Policy – AUP
- Mitchell Bradley.How to Create an AUP - Acceptable Use Policy
- Techopedia. Acceptable Use Policy (AUP)
- Training Strategies Ltd. ICT Acceptable Use Policy
- Rogers Communications Inc. Acceptable Use Policy
- U.S. Department of the Interior (1997). INTERNET Acceptable Use Policy
- Wikipedia. Acceptable Use Policy.
- Worcester Polytechnic Institute (2008). Acceptable Use Policy (AUP).






