Cyber Insurance
Introduction
Cyber insurance coverage has been available on the market for a decade, but only recently companies have been seeing a significant growth—sales of cyber insurance in 2013 escalated 30 percent in comparison with 2012, according to the Global Head of Professional Liability for AIG Tracie Grella.
Now cyber insurance is among the fastest growing sectors in the insurance business. Owing to the increased competition with respect to cyber insurers, many mid- and small-companies can afford to buy a policy. Cyber insurance policies nowadays cater to business needs only, but given how many individuals have personal websites, social media profiles or online books that could be compromised directly, it is easy to imagine how applications for personal cyber insurance will soon come to market. An Atlanta-based cyber insurance broker even opines that "[e]ventually this coverage will be a standard purchase by most businesses."
However, cyber insurance is not the ultimate solution to your security problems. Beware of the self-delusion factor – the feeling that you are immune to deal with any security issue that gets in your way – since cyber insurance cannot make up for weaknesses and merely transfers the risk from the insured to the insurer.

In Search of the Best Cyber Insurance for You: Who Can You Turn to for Advice?
Legal Counsel
Legal counsel will define obscure legal terms regarding cybercrime or cyber liability, and it can also assist a given firm in assessing the risks it faces of cyber-related losses and explain the scope of coverage provided under cyber insurance policies. Additionally, legal counsel will manage litigation for any future cyber insurance products.
Insurance Broker
As already mentioned, there are no strict rules yet in cyber insurance dealings, and therefore it is advisable to speak first with an insurance broker, not an insurance agent. An experienced specialist in this line of business can guide you on what product is most suited to your company. He will assist you negotiating a favourable price and terms, so share with him your list of estimated expenses and costs.
Premium Prices of Cyber Coverage
The insurance premiums range from $25,000 and $50,000 per million USD in coverage for larger policyholders, and for smaller ones the prices are between $15,000 and $20,000 (Info given by Patrick Donnelly, co-managing director of professional risk solutions for Aon Financial Services Group).
Statistical data collected by Marsh & McLennan Companies shows that the U.S. cyber insurance market in 2013 reached $1 billion (€0.73bn) in gross written premiums, and by their estimation can get to the $2 billion (€1.4bn) mark in 2014. Compared with these numbers, the European market with its $150 million (€110mn) is just a fraction of its American counterpart. Nevertheless, it is growing at the good pace of 50 to 100% annually.
Given the lack of standardization, there can be big discrepancies (even up to 25%) between premiums offered by different carriers for the insurance of the same risk. Most of the terms of cyber insurance are considered highly negotiable (See the  text blocks).
text blocks).
Companies should know very well the risks existing in their particular business field and should base their cyber policy on this knowledge. As the divisional director of FINEX Global Erica Constance says: "No two businesses are the same when it comes to cyber risks, therefore it is key to understand the cyber risks your business faces and to ensure your cyber policy is tailored to mirror those risks."
Shades of Skepticism
Despite all the positive factors associated with the fast development of the cyber insurance industry, there are some drawbacks as well. Companies that are victims of cyber attacks often do not want to report the incident, creating a grey area in statistics used by insurers to determine the correlation between risk and price. The lack of actuarial data on cyber incidents, the lack of experience by many insurers, and the immaturity of the market result in unstandardized insurance prices and policies.
Moreover, insurance tycoons fear a cyberhurricane – an occurrence where a major cyber attack simultaneously brings down many targets worldwide, which would bring about, in turn, a tsunami of insurance claims. For that reason, among other things, limited insurance or reinsurance is popular across the industry, but it may not be enough to give the umbrella type of liability firms need.
As the Stroz Friedberg's managing director Bryan Rose takes it, the fact that cyber insurers do not undertake rigorous assessment before creating cyber policies in writing means that they fail to identify the high-risk clients. Consequently, "[t]here's a real risk that insurance companies are not appropriately pricing the risk," Rose concludes.
Evaluation of the Security Postures in Place
Finding an insurer to underwrite a cyber policy might be difficult, because they closely examine potential clients, most of all their information policies (or the lack of such), security systems, and data protection prior to making a final decision to insure them.
As a general requirement concerning signing cyber insurance policies, an evaluation of current information security conditions of the insured party is to be made. Larger corporations are examined by impartial third-party analysts, usually at their own expense. The assessment is thorough and encompasses documentation of security plans, security configurations, backup procedures, password management, and more.
On the other hand, a small firm can issue a self-assessment on its basic information security no longer than a page or two. Yet George Hulme's blog post reveals that these questionnaires may be misleading—giving a wrong impression and false sense of security. Security effectiveness measured by evidence-based cyber metric is perhaps needed (Related topic here).
Cyber insurance can come along with a whole pack of requirements concerning fortifying security: detailed vulnerability assessment, data security training to employees, security plan development and more. It will not be an exception for the insurer to insist on you making serious precautionary improvements by installing extra security measures in terms of technology, or by simply amending positively the human factor. Thus, wanting to add a cyber insurance policy will in itself improve the overall level of cyber security because it will make you inspect your practices in detail.
Security products such as managed service providers (MSPs), system integrators (Sis) and value-added resellers (VARs) get to keep their gravity in the world of information security, no matter whether a company has a cyber insurance in place. In short, possessing a countermeasure of a certain kind does not render all the rest useless, nor it does necessarily express dissatisfaction with them.
Types & Range of Cyber Insurance Coverage
Insurers have more experience dealing with natural disasters, but they are rushing to get a foothold in transferring the risk coming from cyber threats. Traditional insurance products do not provide coverage for those risks related to intangible assets. This was confirmed when a NY state court ruling decided against the claim made by Sony Corp, in which the company sought to milk their general commercial liability insurer to pay the bill for lawsuits following a huge cyber attack on Sony PlayStation Network in 2011. Therefore, if insurers want to offer insurance policies that cover the cyber risks, they need to implement a specialized, purpose-made cyber policy.
There are two main kinds of coverage:
1) First-party coverage – it insures for damages to the policyholder's data, income or other type of harm arising from a data breach/cyber attack;
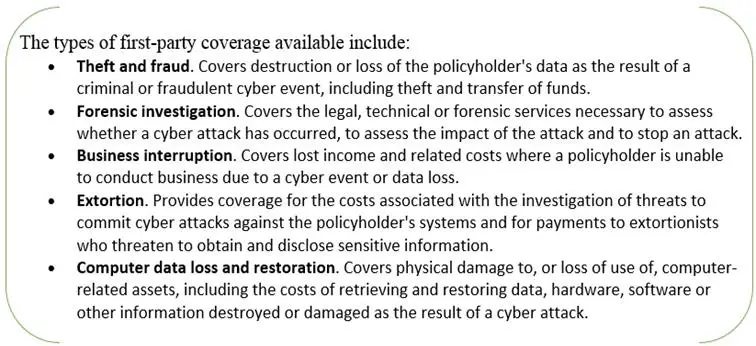
Source: United States: A Buyer's Guide To Cyber Insurance by L. D. Simmons II
 Source: An introduction to cyber liability insurance cover by Sembhi, S.
Source: An introduction to cyber liability insurance cover by Sembhi, S.

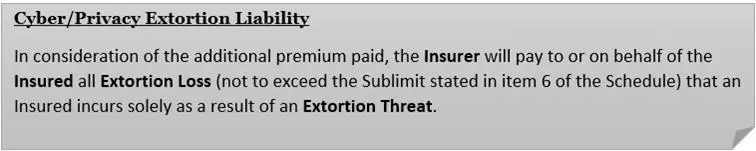
Source: Policy Wording by AIG
2) Third-party coverage – it is meant to insure the policyholder for the liability to a third party, such as clients or government institutions, resulting from a data breach/cyber attack.
 Source: United States: A Buyer's Guide To Cyber Insurance by L. D. Simmons II
Source: United States: A Buyer's Guide To Cyber Insurance by L. D. Simmons II
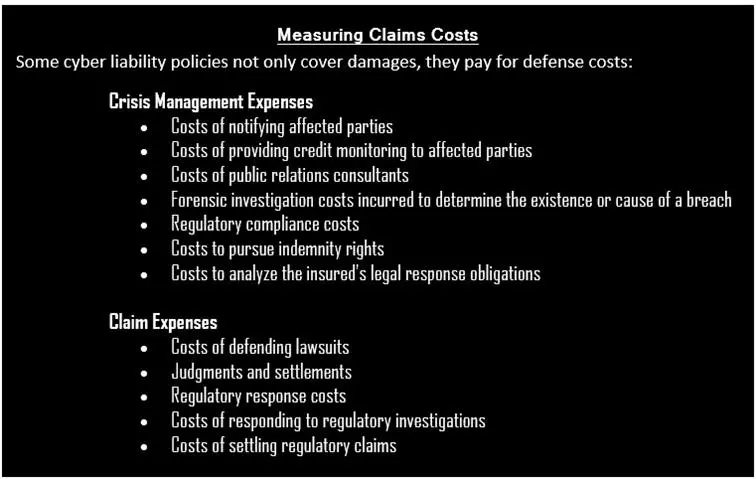
Source: Cyber Insurance—Mitigating Loss from Cyber Attacks by Simens, R. & Beck, D.
The Fine Sense of Negotiating Workable Terms & Conditions
Choose Retroactive Coverage
Cyber policies could come into effect after a specific date, for instance, the inception date of the policy. In reality, it means that the insurer will not cover incidents that occurred before this date. Since many cyber attacks are latent and may remain undetected for a long time, purchasing a policy with the earliest possible date may prove important.


Source: Policy Wording by AIG
Consider Coverage for Acts and Omissions by Third Parties
In today's world of intensive globalization, many western companies outsource and subcontract their work to third parties elsewhere, or even use products and services of foreign entities. That would most likely increase the risk, and cyber insurance policy may include coverage for claims that originate from misconduct of vendors and distant affiliates.
Get to Know The "Triggers"
It is always useful to know what exactly activates coverage procedure under your concrete cyber policy.
Consider Coverage for Loss of Information on Unencrypted Devices
Many employees take their work home or simply somehow decide to perform their duties on computers and mobile devices outside the office. If that is the case with your firm, you better consider a provision that will reimburse you if something bad happens.
Consider Coverage for Regulatory Actions
An insurance policy may be negotiated to provide coverage for regulatory investigations or other regulatory actions following cyber incidents.
Example of Cyber Insurance Terms


Source: Policy Wording by AIG
Under the Microscope: Cyber Insurance in the Event of a Data Breach



Source: Policy Wording by AIG
Data breach can potentially cause onerous costs related to compromised privacy information. This is especially true for valuable data, such as regulated personal, medical or financial information about consumers. Insuring your information infrastructure is one avenue of protecting end-user organizations when they are struck by financial tolls in the aftermath of a data breach. Lost business accounts come in at 38 percent of the total costs associated with a data breach. Legal services and investigations/forensics follows with 16 and 13 percent respectively.
A study by Aon emphasizes the fact that one-third of all companies operating in the financial sector have experienced either significant system failures or data breaches. Travelers' head insurer Tim Francis confirms that "[t]he trend early on was tech, financial and health-care companies buying insurance. That still continues. In the last couple of years you've seen more retail and manufacturing firms buying insurance and now you are seeing small- and middle-market firms buying too."
Another statistical source reveals that while more small businesses tend to get by without cyber insurance since the Target incident, those that buy choose higher coverage limits. Before the Target breach, 93% went for the minimum policy, the number now is 85%.
Surprisingly, compared to large companies (with more than 100,000 records), smaller ones (having no more than 10,000 records) are more like fall victim to hackers because their security defence is not so robust. Sarah Stephens, who is the European head of cyber and commercial errors and omissions insurance at Aon Risk Solutions, warns: "We find that banks and other financial institutions have not yet fully baked cyber risk into their operation risk processes." Curiously, a study by Gartner ascertains that some 94 percent of all companies experienced a significant turbulences due to data loss went out of business within two years or so.
It is important to realize that cyber insurance can be a real solution, not something that will be out there to soothe customers' nerves and remain on paper only. By way of example, the cyber policy helped Partner HealthCare to cover regulatory expenses when its employee left 192 records of patients on a train.
When it comes to data breach, not sustaining the might of the blast is one thing, being negligent is totally other:
"Being able to prove that they weren't negligent could save organizations millions in the long-run. [I]f something happens when a client loses data, they can tell the regulator that they did everything within reason to try to ensure that there was an environment of security where its employee knew where its employees knew how to handle client information."
Presumably, cyber insurance as a means to transfer risk is applied mostly in countries that have mandatory data breach notification laws.
With 46 of 50 states that have that kind of laws, the United States relies heavily on mandatory data breach notifications.
Yet the draft EU data protection rules could galvanize the European cyber coverage market due to provisos that impose obligations on corporate bodies to disclose information breaches to all customers involved.
A Matter of Reputation
One of the issues insurance companies struggle with, as mentioned earlier, is quantifying losses from potential cyber attacks, because damages are more often than not intangible, like the negative impact on brand name in the aftermath of massive data breach. As a result, business entities looking for cyber insurance usually cannot get as much coverage as they need, making them vulnerable to excessive losses.
A classic case in this area would be the data breach of Target's point-of-sale systems in December 2013 and the public relation disaster that followed. According to The New York Times, the American retailer managed to collect $100 million in coverage, of which $10 million was the deductible, coming from multiple carriers. This sum, however, will barely compensate for the expected $1 billion in losses, as some experts are predicting. The company has incurred by now $88 million in breach-related expenses, with the cyber insurance indemnity for that particular cost calculated to be approximately $52 million.
The Aon's Donnelly thinks that insurance companies cannot make up for reputation losses, which is maybe the biggest damage of all. Even if an organization duly notifies its customers of a data breach and manages to recover the notification costs, that would certainly reduce the customer confidence in the organization in question. One study made by PwC evaluated that the average loss in brand value and reputation for a given company victim of a data breach can range between $184 million and $330 million.


Source: Policy Wording by AIG
A sensitive subject among cyber coverage companies, data breaches bear distrust in the abilities of a legal entity to guarantee before its customers that the future is bright and shiny. Insurers are not insured against being targets themselves. They store an enormous quantity of personal information like social security numbers, credit card data, names, addresses, etc. The rigorous nature of the underwriting process conduces to the fact that insurers have a knowledge of details straight from the backyard of corporations and individuals across different industries. Credentials to insurers' systems alone could cost a lot on the black market.
The ultimate truth shared by Scott is that "[r]egardless of the strength of your system, you're going to have a high percentage of companies suffering data breaches [See Largest data breach in history: Protect yourself now]." Therefore, cyber insurers need to collaborate as much as possible with international and national authorities and external security vendors.
Conclusion
Everything we know about cyber insurance, as one way to diminish the damages from eventual cyber security problems, shows that it is worth it. This method is not perfect, not at all, but it gives business more than just a tad of extra tolerance to endure big time troubles – it can keep your company afloat. The cyber policy is a secondary contingency plan, hence having it always means that you wear one bulletproof vest more. Well, just do not forget that dodging bullets is something you can achieve only by fortifying your existing defences in the first place.
References
AIG (2013). Policy Wording. Retrieved on 05/08/2014 from http://www.aig.com/chartis/internet/uk/eni/AIGPROFCYBER%20CyberEdge%20Cyber%20Liability%20Insurance_tcm2538-409823.pdf
Ashford, W. (2014). Cyber insurance complements security controls, says Aon. Retrieved on 05/08/2014 from http://www.computerweekly.com/news/2240224437/Cyber-insurance-complements-security-controls-says-Aon
Chabrow, E. (2012). 10 Concerns When You Buying Cyber Insurance. Retrieved on 05/08/2014 from http://www.bankinfosecurity.com/10-concerns-when-buying-cyber-insurance-a-4859/op-1
Capgemini (2012). Using Insurance to Mitigate Cybercrime Risk. Retrieved on 05/08/2014 from http://www.capgemini.com/resource-file-access/resource/pdf/Using_Insurance_to_Mitigate_Cybercrime_Risk.pdf
Daily News (2014). Fewer small businesses buying cyber liability insurance since Target breach. Retrieved on 05/08/2014 from http://www.canadianunderwriter.ca/news/fewer-small-businesses-buying-cyber-liability-insurance-since-target-breach/1003173715/0w3s40Wrus403lvpsnvs3M20/?ref=enews_CU&utm_source=CU&utm_medium=email&utm_campaign=CU-EN07252014
Hulme, G. (2014). Questionnaires Lead to a False Sense of Security for Third Party Risk Managers. Retrieved on 05/08/2014 from http://blog.bitsighttech.com/questionnaires-false-security-for-third-party-risk-managers
Insureon (2014). Insureon: Fewer Small Businesses Buying Cyber Liability Insurance since Target's Breach. Retrieved on 05/08/2014 from http://finance.yahoo.com/news/insureon-fewer-small-businesses-buying-130000404.html
Komando, K. How cyber insurance might ease your (network) insecurity. Retrieved on 05/08/2014 from http://www.microsoft.com/business/en-us/resources/finance/business-insurance/small-busines-cyber-insurance.aspx?fbid=bPQgxYX6a12
Komando, K. (2014). Largest data breach in history: Protect yourself now. Retrieved on 05/08/2014 from https://www.komando.com/tips/265866/largest-data-breach-in-history-protect-yourself-now
Ouellette, P. (2014). Organizations adding cyber insurance in lieu of data breaches. Retrieved on 05/08/2014 from http://healthitsecurity.com/2014/02/18/organizations-adding-cyber-insurance-in-lieu-of-data-breaches/
Pelroth, N. & Harris, E. (2014). Cyberattack Insurance a Challenge for Business. Retrieved on 05/08/2014 from http://www.nytimes.com/2014/06/09/business/cyberattack-insurance-a-challenge-for-business.html
Richmond, R. (2012). How to Determine If Cyber Insurance Coverage Is Right for You. Retrieved on 05/08/2014 from http://www.nbcnews.com/id/48109945/ns/business-small_business/t/how-determine-if-cyber-insurance-coverage-right-you/#.U-J4HaOE6_Q
Scharf, I. (2014). The Problem with Cyber Insurance. Retrieved on 05/08/2014 from http://www.darkreading.com/risk/the-problem-with-cyber-insurance/a/d-id/1269682
Schroeder, D. (2014). Cyber Insurance: Just One Component of Risk Management. Retrieved on 05/08/2014 from http://blogs.wsj.com/cio/2014/03/27/cyber-insurance-just-one-component-of-risk-management/
Sembhi, S. (2014). An introduction to cyber liability insurance cover. Retrieved on 05/08/2014 from http://www.computerweekly.com/news/2240202703/An-introduction-to-cyber-liability-insurance-cover
Simens, R. & Beck, D. (2012). Cyber Insurance—Mitigating Loss from Cyber Attacks. Retrieved on 05/08/2014 from http://www.pillsburylaw.com/publications/cyber-insurancemitigating-loss-from-cyber-attacks
Simmons II , L. D. (2013). United States: A Buyer's Guide To Cyber Insurance. Retrieved on 05/08/2014 from http://www.mondaq.com/unitedstates/x/267482/Insurance/A+Buyers+Guide+To+Cyber+Insurance
Stanganelli, J. (2014). Cyber Insurance: 6 Facts You Should Know. Retrieved on 05/08/2014 from http://www.esecurityplanet.com/network-security/cyber-insurance-6-facts-you-should-know.html
Steele, C. (2007). Cyber insurance supplements, not replaces, data breach security. Retrieved on 05/08/2014 from http://searchitchannel.techtarget.com/news/1262357/Cyber-insurance-supplements-not-replaces-data-breach-security
Thomas L. & Finkle J. (2014). Insurers struggle to get grip on burgeoning cyber risk market. Retrieved on 05/08/2014 from http://uk.reuters.com/article/2014/07/14/uk-insurance-cybersecurity-idUKKBN0FJ0BG20140714
Thompson. M (2014). Why cyber-insurance will be the next big thing. Retrieved on 05/08/2014 from http://www.cnbc.com/id/101804150#.
Virgillito , D. (2014). Insurance Companies are Facing Major Cyber Risks. Retrieved on 05/08/2014 from http://vpncreative.net/2014/07/14/insurance-companies-major-cyber-risks/






