5 Steps to Conducting an Enterprise Security Risk Analysis
In the world of cybersecurity, identifying risks and how they will impact the organization is of paramount importance. In general terms, risk is comprised of two specific components:
- The statistical probability of something going wrong
- The negative consequences that transpire as a result of it
A risk analysis can help organizations identify risks and their associated consequences.
How Can I Perform a Risk Analysis?
There are many modeling tools available to conduct risk analyses. These include the Scenario Analysis, the Failure Mode and Effects Analysis and the SWOT Analysis. But, deciding upon which methodology to utilize to in order to ascertain and mitigate risk is dependent heavily upon the specific needs of the business entity.
The general steps required to conduct an effective risk analysis are as follows:
-
Identify the information assets being used.
In this step, you determine what kinds of information and data your company stores and uses. After all, this is the prized target for any cyber attacker. For instance, this could include social security numbers, credit card numbers, healthcare information (such as patient records) and employee data.
-
Determine the specific location of these information assets.
In this part of the risk analysis, you determine the specific location of where these datasets reside at. For example, are they stored on certain employee workstations, laptops, wireless devices, databases, file servers, storage portable devices, etc.?
-
Classify information assets.
Once you have determined where assets reside at, the next step is to classify them according to their level of importance as it relates to your business. Consider using a 1-10 ranking scale, with the breakdown being as follows:
In between the two extreme ranks (1 and 10), and the midrange (5), you can also assign other values. This quantitative level of importance will vary upon the types of datasets that are stored and used.
The end result of this step is that you will have determined which types of information and data will cause the most damage (both in terms of money and brand reputation losses) to your organization in the event they were unintentionally disclosed, maliciously altered or covertly used for launching identity theft attacks.
-
Launch a real world, threat modeling scenario.
In this phase, you are taking datasets which are ranked as having the "utmost value" (these will most likely have a ranking of 8-10, as determined in the previous step) and putting them into a cyber threat classification scheme. A popular modeling tool here is known as "STRIDE," which was developed by Microsoft. For example, are these datasets prone to a:
-
Rank the STRIDE factors.
In this stage, you are ranking the statistical likelihood of these cyber threats actually being a real attack onto your business. Once again, utilize a numerical scale of 1-10, with the breakdown as follows:
Once again, like in the third step, mid-range values can also be assigned.
Once this step has been accomplished, you will now have a much better scope of the cyber threat landscape that your business or corporation is facing (these will most likely have a ranking of 8-10), and the datasets which are also at most risk, as a result.
Therefore, a prudent methodology is to focus on mitigating those cyber threats first, then working down to cyber threats which pose the least risk. Remember, the ultimate goal of a comprehensive risk analysis is to protect your entity from all cyber threats while also protecting all of your data assets.
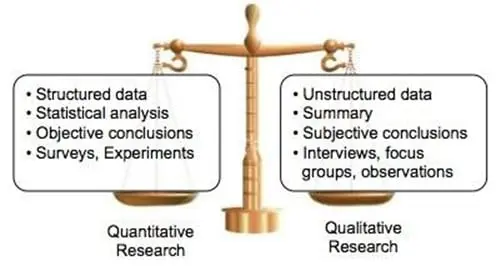
Should I Use A Qualitative or Quantitative Risk Analysis, or Both?
When conducting a risk analysis, you must decided to use a qualitative or quantitative approach. Deciding upon which to utilize depends upon what the exact needs of the business or corporation are. For example, one approach might be better than the other, or a hybrid of both approaches can also be used.
In general, a qualitative risk analysis takes a holistic approach at what needs to be assessed. In this regard, all variables are taken into consideration, and are thus ranked according to a predefined scale. This is best exemplified in the last section of this article. For example, all information and data in an organization were examined, and from there, they were also ranked in terms of their level of importance and value.
One of the main advantages of the qualitative risk analysis is there are hardly any mathematical computations involved. Thus, determining the level of risk is quick, and relatively easy to compute.
But, one of the main disadvantages of this is it is subject to the perceptions and biases of the individuals involved in conducting the study. Thus, a qualitative risk analysis is considered a "local" approach.
On the other hand, a quantitative risk analysis examines a subset of the results that were formulated from the qualitative risk analysis. Typically, variables that are deemed to have a high level of risk are further evaluated using a mathematical approach.
From this, a numerical value is then assigned to the appropriate risk factor. In these instances, it is typically a monetary value that is used, in order to give a real-world impact of the amount of loss or damage that could occur to an organization.
There are three broad categories used to calculate this monetary value:
- The Single Loss of Expectancy, or SLE:
This is the amount of money that is expected to be lost if an incident (such as a cyber attack) occurs.
- The Annual Rate of Occurrence, or ARO:
This is how many times in a year a particular incident will occur (such as a cyber attack, and any variations of it).
- The Annual Loss Expectancy, or ALE:
This is discussed in more detail in the next section of this article.
The table below summarizes some of the important differences between the qualitative and quantitative risk analysis approaches:
Qualitative Risk Analysis
Quantitative Risk Analysis
Also, a hybrid approach can be utilized, which combines both qualitative and quantitative risk analysis methodologies. For example, an organization may use the qualitative approach first in order to quickly and effectively identify all of the risks that are present in normal, every day business operations.
From there, the quantitative approach can be used to focus on risks that will have the most impact on a business. Remember, the ultimate goal for any corporation is to eradicate all risks. In this regard, the hybrid approach will be the best methodology to accomplish this.
What Is Annual Loss Expectancy (ALE)?
One of the most important metrics used in conducting a risk analysis is the Annual Loss Expectancy (ALE). The ALE is the expected financial loss for an asset to due risk over a one-year period.
Mathematically speaking, it is the product of the Single Loss Expectancy (SLE) and the Annual Rate of Occurrence (ARO):
ALE = SLE * ARO
It is important to note the monetary value of the ALE can fluctuate dramatically, as the actual Rate of Occurrence can vary quite a bit in just a one-year time frame. If an organization expects it could be impacted by a cyber attack several times in a single year, (for example, Google has reported a 32% annual increase in the number of websites hacked), then sophisticated statistical analyses (such as that of Poisson Probability Distribution) may be required in order to get a more accurate reflection of the ALE.
The ALE is often used in conducting a benefit-cost analysis, especially when deciding upon what kind of risk control measures are to be deployed. For instance, if the cost of a control is less than the calculated ALE, then yes, that control should be implemented. But if the cost of the control is greater than the calculated ALE, then other, more cost-effective security measures should be further examined.
Conclusion
This article examined what risk is, how to conduct a risk analysis, whether a quantitative or qualitative approach should be used, as well as some of important risk analysis metrics. Maintaining a proactive mindset about assessing risk is very important for any business or corporation, and conducting these kinds of analyses should be conducted at least once a quarter.
In fact, it may be beneficial for an organization to employ an outside consultant when conducting a risk analysis, especially when the qualitative approach is used first. This will help eradicate any biases and misperceptions.
It is important to keep in mind a risk analysis is only one component in the security arsenal of an organization when it comes to staying one step ahead of the cyber attacker. It also requires a constant human vigilance, and making sure your entire IT infrastructure is always up to date with the latest software patches and upgrades.






