StingRay Technology: How Government Tracks Cellular Devices
StingRay Technology
StingRay is an IMSI-catcher (International Mobile Subscriber Identity) designed and commercialized by the Harris Corporation. The cellular-surveillance system costs as much as $400,000 in the basic configuration, and its price varies with add-ons ordered by the agency.
The IMSI-catcher is a surveillance solution used by military and intelligence agencies for telephone eavesdropping. It allows for intercepting mobile phone traffic and tracking movements of mobile phone users. Essentially, an IMSI catcher operates as a bogus mobile cell tower that sits between the target mobile phone and the service provider's real towers. The IMSI catcher runs a Man In the Middle (MITM) attack that could not be detected by the users without using specific products that secure communication on mobile devices.

FREE role-guided training plans
The use of the IMSI-catcher is raising a heated debate in the United States because devices like StingRay and other similar cellphone tracking solutions are being widely adopted by law enforcement agencies across the country.
Due to the popularity of StingRay, the name is used improperly to reference several types of cellphone-surveillance solutions. StingRay allows law enforcement to intercept calls and Internet traffic, send fake texts, inject malware on a mobile device, and to locate the targets.
Privacy advocates are concerned with possible abuses of such invasive technology. They speculate that there is the concrete risk that cyber criminals and foreign state-sponsored hackers could use it to track US citizens.
StingRay-like solutions, also known as cell site simulators, trick cellphones into revealing different data, including users' locations and identifying information.
Law enforcement and intelligence agencies can target a specific individual analyzing incoming and outgoing calls and drawing on his social network. The principal problem in the adoption of the StingRay cellphone-surveillance technology is that, different from other solutions, it targets all nearby cellular devices, allowing an attacker to get information from hundreds of devices concurrently.

Figure 1 - StingRay
As explained by Nathan Freed Wessler, an attorney with the ACLU's Speech, Privacy & Technology Project, StingRay equipment sends intrusive electronic signals in the immediate vicinity, sinking private buildings and siphoning data about the locations and identities of cellphones inside.
The Federal Communications Commission (FCC) recently created an internal task force to study the misuse of IMSI catchers in the cybercrime ecosystem and foreign intelligence agencies, which demonstrated that this technology could be used to spy on American citizens, businesses and diplomats.
How does StingRay work?
StingrRay equipment could operate in both active and passive modes. In the first case, the device simulates the behavior of a wireless carrier cell tower. In the second case, it actively interferes with cellular devices performing operations like data exfiltration.
The StingRay system is typically installed in a vehicle in a way that agents can move it into any neighborhood. It tricks all nearby cellular devices into connecting to it and allowing data access by law enforcement.
Let us see in detail the two operative modes implemented by the StingRay technology.
The Passive mode
A StingRay that is operating in passive mode is able to receive and analyze signals being transmitted by mobile devices and wireless carrier cell stations.
The term "passive" indicates that the equipment doesn't communicate directly with cellular devices and does not simulate a wireless carrier cell site.
The activity of base station surveys allows extracting information on cell sites that includes identification numbers, signal strength, and signal coverage areas. StingRay operates as a mobile phone and collects signals sent by cell stations near the equipment.
The Active mode
StingRay equipment operating in "active mode" will force each cellular device in a predetermined area to disconnect from its legitimate service provider cell site and establish a new connection with the attacker's StingRay system. StingRay broadcasts a pilot signal that is stronger than the signals sent by legitimate cell sites operating in the same area, forcing connections from the cellular device in the area covered by the equipment. The principal operations made by the StingRay are:
-
Data Extraction from cellular devices - StingRay collects information that identifies a cellular device (i.e. IMSI, ESN) directly from it by using radio waves.
-
Run Man In The Middle attacks to eavesdrop on Communications Content
-
Writing metadata to the cellular device
-
Denial of Service, preventing the cellular device user from placing a call or accessing data services.
-
Forcing an increase in signal transmission power
-
Forcing an abundance of signal transmissions
-
Tracking and locating
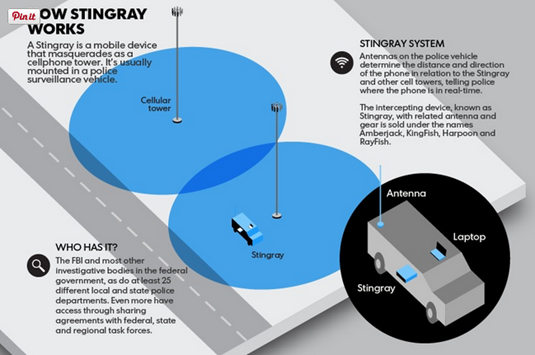
Figure 2 - StingRay case study
USA – StingRay is a prerogative of intelligence agencies
Surveillance of cell phones is a common practice in intelligence agencies. Agents have used devices like StingRay for a long time, and the use has extended to local law enforcement in the USA.
Dozens of local law enforcement and police agencies are collecting information about thousands of cell phone devices at a time by using advanced technology, according to public records obtained by various media agencies in the country.
USA Today reported that records from more than 125 police agencies in 33 states reveal that nearly 25 percent of law-enforcement agencies have used "tower dump," and at least 25 police departments have purchased StingRay equipment.
Many police agencies have denied public records requests, arguing that criminals or terrorists could benefit from the disclosure of information and avoid surveillance methods adopted locally by law enforcement.
Security experts and privacy advocates raise the discussion regarding the use of StingRay technology and the way the law enforcement agencies manage/share citizens' data.
The militarization of America's local police agencies is a phenomenon attracting the attention of the media as never before, probably also as a consequence of the debate on privacy and surveillance triggered by the Snowden's revelations.
The phenomena are not limited to the US. Recent documents released by the City of Oakland reveal that the local Police Department, the nearby Fremont Police Department, and the Alameda County District Attorney jointly requested an upgrade for their cellular surveillance equipment.
The specific update to StingRay is known as Hailstorm, and is necessary to allow the equipment to track also cellular devices of new generation.
According to the Ars web portal, the upgrade will cost $460,000, including $205,000 in total Homeland Security grant money and $50,000 from the Oakland Police Department.
Cellular tracking technology like StingRay is still considered a privileged solution to track cellular devices and siphon their data. The interest of local law enforcement in the surveillance solutions is increasing and the decision to update their configuration led privacy experts to believe that their diffusion will continue to increase.
A look at the technologies that track cellular devices
To better understand the StingRay technology, let us familiarize ourselves with the names of the principal surveillance solutions available on the market.
Triggerfish
Triggerfish is an eavesdropping equipment that allows law enforcement to intercept cellular conversations in real time. Its use extends the basic capabilities of StingRay, which are more oriented to device location monitoring and gathering metadata. Triggerfish allows authorities to monitor up to 60,000 different phones at one time over the targeted area.

Figure 3 - Triggerfish
According a post published by the journalist Ryan Gallagher on Ars, its cost ranges between $90,000 and $102,000.
Kingfish
Kingfish is a surveillance transceiver that is used by law enforcement and intelligence agencies to track cellular devices and exfiltrate information from mobile devices over a targeted area. It could be concealed in a briefcase and allows gathering of unique identity codes and shows connections between phones and numbers being dialed. Its cost is slightly higher than $25,000.

Figure 4 - Kingfish
Amberjack
Amberjack is an important accessory for the surveillance systems like StingRay, Gossamer, and Kingfish. It is a direction-finding system antenna that is used for cellular device tracking. It costs nearly $35,015.
Harpoon
Harpoon is an "amplifier" (PDF) that can work in conjunction with both Stingray and Kingfish devices to track targets from a greater distance. Its cost ranges between $16,000 and $19,000.

Figure 5 - Harpoon
Hailstorm
Hailstorm is a surveillance device that could be purchased as a standalone unit or as an upgrade to the Stingray or Kingfish. The system allows the tracking of cellular devices even if they are based on modern technology.
"Procurement documents (PDF) show that Harris Corp. has, in at least one case, recommended that authorities use the Hailstorm in conjunction with software made by Nebraska-based surveillance company Pen-Link. The Pen-Link software appears to enable authorities deploying the Hailstorm to directly communicate with cell phone carriers over an Internet connection, possibly to help coordinate the surveillance of targeted individuals," states an Ars blog post.
The cost of Hailstorm is $169,602 if it is sold as a standalone unit, and it could be cheaper if acquired as an upgrade.
Gossamer
Gossamer is a portable unit that is used to access data on cellular devices operating in a target area. Gossamer provides similar functionality of StingRay with the advantage of being a hand-held model. Gossamer also lets law enforcement run a DoS attack on a target, blocking it from making or receiving calls, as explained in the marketing materials (PDF) published by a Brazilian reseller of the Harris equipment.
Gossamer is sold for $19,696.

Figure 6 - The Gossamer
The Case: Metropolitan Police Department (MPD) uses StingRay
StingRay has been used for a long time by the police. In 2003, the Metropolitan Police Department (MPD) in Washington, DC was awarded a $260,000 grant from the Department of Homeland Security (DHS) to acquire StingRay.
The purchase was officially motivated by the need to increase capabilities in the investigation of possible terroristic events. Unfortunately, the device was not used by law enforcement for five years due to the lack of funds to pay for training for its use.
In 2008, the Metropolitan Police Department decided to again adopt StingRay for its investigations, and received funds to upgrade it.
The VICE News has documented numerous purchases made by the DC police department and related to the solution of services offered by the Harris Corporation.
The problem is that according to government officials the systems weren't used to prevent the terrorism act, but law enforcement is using it in routine investigations involving ordinary crime. There is no documentation regarding the use of StingRay made by the agents of the department.
In a memo dated December 2008, DC chief of police and other top department officials by the commander of the Narcotics and Special Investigations Division explained how the department intended to use StingRay.
"If DC police are driving around with a Stingray device, they're likely capturing information about the locations and movements of members of Congress, cabinet members, foreign dignitaries, and all of the other people who congregate in the District.
"The [redacted] will be used by MPD to track cellular phones possessed by criminal offenders and/or suspected terrorists by using wireless technology to triangulate the location of the phone," "The ability to [redacted] in the possession of criminals will allow MPD to track their exact movements, as well as pinpoint their current locations for rapid apprehension," states the document. "The procurement of this equipment will increase the number of MPD arrests for fugitives, drug traffickers, and violent offenders (robbery, assault with a deadly weapon, Homicide), while reducing the time it takes to locate dangerous offenders that need to be removed from the streets of DC."
The memo confirms that the department has used the StingRay for many purposes other than counter terrorism activities.
Many organizations are condemning the use of such technology because it represents a serious threat to the privacy of the citizens. When an agency uses StingRay to track a specific individual, it is very likely that the system will also catch many other devices of innocent and unaware people.
"When it's used to track a suspect's cell phone, [it] also gather[s] information about the phones of countless bystanders who happen to be nearby," explains the representatives at the American Civil Liberties Union (ACLU).
StingRay is also a privileged instrument to collect information about ongoing communications, including phone numbers of interlocutors. It is important to understand that its use opens the door to a "sort of invasive surveillance".
The principal problem related to the use of Stingrays and similar solutions is related to their application context. This category of equipment, in fact, was mainly designed to support intelligence activities, but today its use has been extended to local law enforcement, as explained by Nathan Wessler:
"Initially the domain of the National Security Agency (NSA) and other intelligence agencies," the use of the tracking device has now "trickled down to federal, state, and local law enforcement."
The extensive use of StingRay is a violation of the Fourth Amendment; it is threatening the rights of tens of thousands of DC residents.
The ACLU has identified 44 law enforcement agencies in 18 states in the US that use StingRay equipment for their investigation, but as explained by Wessler it must be considered that the use of such devices in the vicinity of government offices is a circumstance of great concern. That's why he mentioned the case of the capital Washington.
"An inherent attribute of how this technology functions is that it sweeps in information about large numbers of innocent bystanders even when police are trying to track the location of a particular suspect. If the MPD is driving around DC with Stingray devices, it is likely capturing information about the locations and movements of members of Congress, cabinet members, federal law enforcement agents, and Homeland Security personnel, consular staff, and foreign dignitaries, and all of the other people who congregate in the District…. If cell phone calls of congressional staff, White House aides, or even members of Congress are being disconnected, dropped, or blocked by MPD Stingrays, that's a particularly sensitive and troublesome problem," said Wessler during an interview with VICE News.
The documents obtained by the website Muckrock from the FBI revealed that law enforcement agencies are required to sign a non-disclosure agreement with the Bureau before they can start using StingRays for their investigation. The ACLU obtained emails that explain that the vendor Harris Corporation misled the FCC for approval of Stingray by supposing its adoption for "emergency situations." In reality, the equipment is used by law enforcement for any kind of investigation.
The following map reports the use of the StingRay tracking system by state and local police departments. According to the ACLU, 46 agencies in 18 states and the District of Columbia own StingRays. According to privacy experts, the data underestimates the real diffusion in the use of the StingRay system because of lack of official documentation that would report the number of investigations in which the equipment has been used.
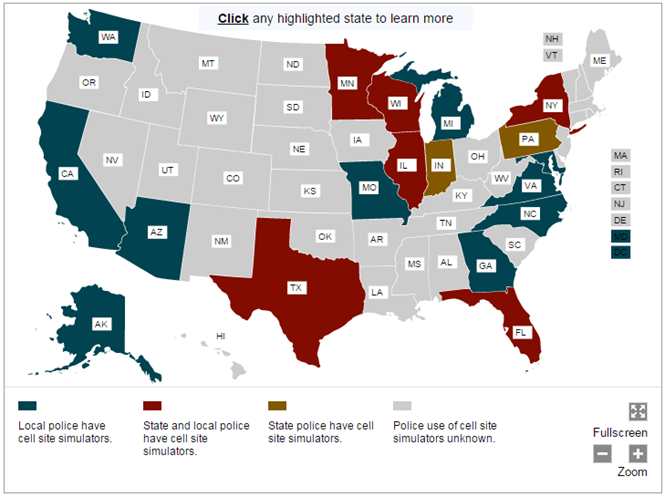
Figure 7 - StingRay diffusion in the USA
Conclusion
StingRay technology raises serious privacy concerns because of the indiscriminate way it targets cellular devices in a specific area. The dragnet way in which StingRay operates appears to be in contrast with the principle of various laws worldwide. Government and law enforcement shouldn't be able to access citizen's private information without proving to a court order that must be issued to support investigation activities.
In the US, for example, the Fourth Amendment stands for the basic principle that the US government cannot conduct a massive surveillance operation, also indicated as "general searches". The Supreme Court recently reiterated that principle in a case involving cell phone surveillance, and confirmed that law enforcement need a warrant to analyze data on the suspect's cellphone.
Organizations for the defense of civil liberties ask governments to provide warrants to use surveillance technologies like StingRay. The warrant still represents a reasonable mechanism for ensuring the right balance between the citizen's privacy and law enforcement needs.
Organizations such as the American Civil Liberties Union and Electronic Privacy Information Center (EPIC) highlighted the risks related to the indiscriminate collection of a so large amount of cellular data.
"I don't think that these devices should never be used, but at the same time, you should clearly be getting a warrant," said Alan Butler of EPIC.
Unfortunately, cases such as the one disclosed in this post suggest that governments are using StingRay equipment in secrecy. In some cases, a court order is issued for specific activities, but law enforcement arbitrarily extends the use of technology in other contexts that may be menacing to citizens' privacy.
References
http://securityaffairs.co/wordpress/28397/hacking/surveillance-solutions.html
https://www.aclu.org/blog/national-security-technology-and-liberty/trickle-down-surveillance
https://www.aclu.org/maps/stingray-tracking-devices-whos-got-them
http://www.phonearena.com/news/Cellphone-spying-gear-law-enforcement-has-it-and-it-wants-you-to-forget-about-it_id58920
https://www.scribd.com/doc/238334715/Stingray-Phone-Tracker
http://www.usatoday.com/story/news/nation/2013/12/08/cellphone-data-spying-nsa-police/3902809/
https://www.aclu.org/files/assets/rigmaiden_-_doj_stingray_emails_declaration.pdf
http://arstechnica.com/tech-policy/2013/09/meet-the-machines-that-steal-your-phones-data/2/
http://cdn.arstechnica.net/wp-content/uploads/2013/09/amberjack.pdf
http://records.oaklandnet.com/feedback/request/2595

FREE role-guided training plans
http://cdn.arstechnica.net/wp-content/uploads/2013/09/oakland-penlink-hailstorm.pdf









