Privacy risks of beacons
On October 6th 2014, buzzfeed.com published a report stating that Titan, a company controlling a number of New York City's phone booth advertising displays, installed tiny wireless devices called beacons in hundreds of phone booths. The beacons pinged out a Bluetooth signal that could be received by mobile phones on which certain apps are installed and activated. Such apps can identify the location of the mobile phones on the basis of the received Bluetooth signals and send targeted advertisements to the users of the phones. The term "targeted advertising" refers to placing advertisements in such a way as to reach consumers based on various behavioral, demographic, and psychographic attributes.
Because beacons are inexpensive (a beacon costs less than USD 25) and can be easily placed wherever people carrying mobile phones walk by, it is expected that the use of beacons in the near future will increase significantly. BI Intelligence forecasts that by 2018 there will be 4.5 million beacons. An article published by Business Insider stated that the business of in-store beacons is "the fastest-growing in-store technology since mobile credit card readers."
Although businesses invest significant financial and human resources in developing mobile phone applications collecting data from beacons, businesses do not put significant efforts in informing the users of such applications about the privacy risks associated with beacons. This article examines the privacy risks posed by beacons (Section 2) and proposes solutions as to how to reduce such risks (Section 3). Finally, a conclusion is drawn (Section 4).
Privacy risks posed by beacons
The use of beacons is associated with at least two privacy risks, namely, a risk of unlawful surveillance (Section 2.1) and a risk of receiving undesired targeted advertisements (Section 2.2). These two risks are examined in more detail below.
Risk of unlawful surveillance
The location data submitted by beacons can be used not only by legitimate software applications, but also by malware programs which can provide criminals with information about the location of individuals. In this regard, it is worth mentioning that there is a large number of malware programs designed specifically for operation systems of mobile devices. In the first half of 2014, the research team of Kaspersky found 175,442 new unique malware programs created specifically for Android. A large number of these malware programs are invisible. As a result, a victim whose location data is collected may not even know about the unauthorized collection of his/her data.
Criminals may use the collected location data to identify behavior patterns of potential victims. Such patterns will facilitate the criminals in the selection of their victims. For instance, an individual who often visits rich parts of a city may be more attractive for thieves than an individual who visits poor parts of a city. Thieves already use online information for the selection of their victims. In 2014, thieves stole jewelry amounting to GBP 100,000 from the owners of an English law firm after reading on the Internet about the luxury lifestyle of the lawyers.
Risk of receiving undesired targeted advertisement
Many users simply agree with the terms and conditions statements and the privacy policies of the mobile applications without reading them. It was estimated that a person needs 244 hours per year to read every new privacy policy encountered by her. Hence, many users would not read a legal provision in a privacy policy stating that "You agree that we may collect location data from beacons. You agree that we may pass the collected location data to third parties who may then regularly send communications to you and provide information offers and services that may be of interest to you." Once the user agrees to such a provision, hundreds of advertisers can send advertisements customized in accordance with the location of the user. Such targeted advertisements would not be "unsolicited" or "unlawful" within the meaning of many national laws. This is because the user agrees to receive them.
Reducing the privacy risks posed by beacons
The privacy risks posed by beacons can be reduced by enhancing the information security protection of mobile phones (Section 3.1) and obliging the companies selling mobile phone applications to obtain users' express consent before collecting location data (Section 3.2).
Enhancing the information security protection of mobile phones
The information security protection of mobile phones requires the joint efforts of users and manufacturers of mobile phones, developers of mobile phone operation systems and anti-malware software, and governments. The roles of these players in the enhancement of the information security protection are examined below.
Users of mobile phones
In order to avoid information security issues, the users of mobile phones may: (1) install up-to-date anti-malware software; (2) avoid the installation of suspicious software programs; and (3) learn how to avoid being tracked if they suspect that their mobile phones are affected by malware programs. For example, the users can avoid being tracked via beacons by turning off their Bluetooth devices.
Manufacturers of mobile phones
Manufacturers of mobile phones may: (1) reduce the vulnerabilities of their mobile phones to the maximum possible extent; (2) inform the users about the problems that may be caused by users' negligence in relation to the information security of their phones; and (3) de-incentivize the public disclosure of vulnerabilities related to mobile phones.
The mobile phone producers need to conduct extensive testing in order to reduce the vulnerabilities of their mobile phones. The manufacturers will incentivize the users to protect their mobile phones by informing them that malware programs collecting location data facilitate crimes (e.g., thefts of personal belongings). The mobile phone producers will decrease the number of information security attacks using publicly available knowledge by providing the users with full control over the operating systems and the hardware of their phones. If users do not have such control, they need to "root" or "jailbreak" their phones by finding, publicly disclosing, and exploiting vulnerabilities.
Developers of mobile phone operation systems
Most malware programs for mobile phone applications exploit the security vulnerabilities of mobile phone operations systems. For instance, the DroidDream malware used two exploits of the Android operating system, namely, Exploid6 and RageAgainstTheCage7. The utilization of these two exploits allowed DroidDream malware to gain root control of the operating system and install software applications without the permission of the user. The non-malicious web page JailbreakMe 3.0 for iOS devices exploits two vulnerabilities to "jailbreak" (i.e., unlock features) the operation systems of mobile phones. It is up to the developers of mobile phone operation systems to detect and remove information security vulnerabilities in their operation systems.
Developers of anti-malware software
The developers of anti-malware software have an important role in the enhancement of the information security protection of mobile phones. This role relates to the detection and neutralizing of malware.
Governments
To enhance the information security protection of mobile phones, governments can prohibit the sale of mobile phone spyware which collects data from users without their permission. In this regard, it should be noted that the sale of apps which transmit location data without permission of the user is a crime in some countries. For instance, in 2014, the CEO of a Pakistani company InvoCode was indicted in the United States of America for selling an app called StealthGenie which allows the buyers of the app to collect data, including location data, from the users of the app without their permission. In relation to the arrest, Assistant Attorney General Caldwell stated:
"Apps like StealthGenie are expressly designed for use by stalkers and domestic abusers who want to know every detail of a victim's personal life – all without the victim's knowledge. The Criminal Division is committed to cracking down on those who seek to profit from technology designed and used to commit brazen invasions of individual privacy."
Obtaining users' express consent before collecting location data
In the EU countries, the websites using cookies are obliged to obtain the express consent of the users before installing cookies on their computers. In order to obtain express consent, websites place a pop-up window on the main page. The pop-up window asks the users whether or not they agree with the installation of cookies. If the users disagree, the websites will not install cookies on their computers.
If the sellers of mobile phone applications are obliged to use similar pop-up windows when collecting location data, users would be aware of the fact that their location data is being collected. The screenshot below displays a sample pop-up window that can be used for obtaining users' consent to collect location data from beacons.
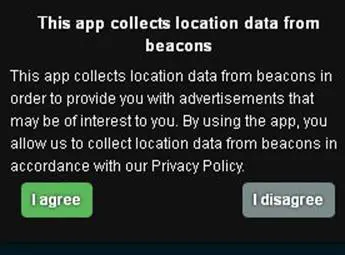
Conclusion
The use of beacons is associated with at least two privacy risks, namely, a risk of unlawful surveillance and a risk of undesired targeted advertisements. The risk of unlawful surveillance can be significantly reduced by the joint efforts of users and producers of mobile phones, developers of mobile phone operation systems and anti-malware software, and governments. The risk of undesired targeted advertisements can be reduced by the adoption of regulatory measures obliging the sellers of mobile phone applications to obtain the express consent of the users before collecting location data from beacons.

FREE role-guided training plans
Sources
- Bernstein, J., Ryley, S., Singer-Vine, J., 'Exclusive: Hundreds of Devices - Hidden Inside New York City Phone Booths', BuzzFeed, 6 October 2014.
- Brandom, R., 'Advertising beacons discovered in hundreds of NYC phone boots', The Verge, 6 October 2014
- Brunty, J., Miller, L., Helenek, K., 'Social Media Investigation For Law Enforcement', Routledge, 2014.
- Gross, G., 'CEO indicted for company's alleged mobile spyware app', NETWORKWORLD, 29 September 2014.
- Federal Bureau of Investigation (FBI), 'Pakistani Man Indicted for Selling StealthGenie Spyware App', FBI.GOV, 29 September 2014.
- Hill, K., 'How To Avoid Being Tracked By The Hidden Devices In New York City's Phone Booths', Forbes, 6 October 2014. Available on .
- Light, J., Pering, T., Sundar, M., Want, R., 'Privacy, Security and Trust Issues
- Raised by the Personal Server Concept', in 'Privacy, Security and Trust within the Context of Pervasive Computing', Robinson, P. (Ed.), Vogt, H. (Ed.), Wagealla, W. (Ed.), Springer Science & Business Media, 2006.
- Lloyd, I., 'Information Technology Law', Oxford University Press, 2014.
- Masnick, M., 'To Read All of The Privacy Policies You Encounter, You'd Need to Take A month Off from Work Each Year', TechDirt, 23 April 2012.
- 'Mobile Threat Report 2011', Lookout.com.
- Neagle, C., 'Secret ad beacon network uncovered, shut down in New York City', NETWORKWORLD, 6 October 2014.
- O'Reilly, L., 'Hundreds of Ad Beacons Have Been Placed Inside NYC Phone Booths Without Public Consent', Business Insider, 6 October 2014.
- Perry, K., 'Law firm couple suffer £100,000 jewellery raid after thieves 'read about their luxury lifestyle on company website'', The Telegraph, 19 November 2014.
- Smith, C., 'THE BEACONS REPORT: Growth Forecasts For The Most Important Retail Technology Since The Mobile Credit Card Reader', Business Insider, 14 November 2014.
- Wagstaff, K., 'New York City Nixes Advertising 'Beacons' in Telephone Boots, NBC News, 6 October 2014










