The End of Bitcoin Ransomware?
Section 1. Introduction
Bitcoin, a virtual currency generated through peer-to-peer technology and not controlled by any central authority, is used not only for paying for goods and services, but also as a means to collect ransomware. The reason why ransomware creators use the virtual currency is the anonymity that Bitcoin provides, i.e., one can conduct Bitcoin transactions without the need to use his/her real name. In this regard, an FBI report on ransomware issued in 2015 points out: "Criminals prefer Bitcoin because it's easy to use, fast, publicly available, decentralized and provides a sense of heightened security/anonymity."
Despite the alleged anonymity of Bitcoin transactions, there are several ways in which the identity of Bitcoin users can be revealed. The purpose of this article is to examine them in the context of Bitcoin ransomware. More specifically, we will examine the classical forensic approach (Section 2) as well as two innovative approaches, namely, the use of the software applications BitCluster
(Section 3) and Elliptic (Section 4). Finally, we provide concluding remarks (Section 5).
Section 2. Classical forensic approach
Bitcoin is anonymous, yet pseudonymous virtual currency. This means that the names of the participants in Bitcoin transactions are anonymous, but the pseudonyms under which the transactions are concluded are public. The public key hashes of Bitcoin users are their pseudonyms. Hence, if law enforcement authorities succeed to link all public key hashes used by a criminal with his/her name, the authorities will receive information about all Bitcoin transactions completed by the criminal.
The classical forensic approach used for revealing the identities of Bitcoin users is to attempt to link a public key hash with a real name. Such a link can be established by using two methods, namely, (1) identifying a Bitcoin user solely on the basis of personal information collected by Bitcoin-processing businesses and (2) identifying a Bitcoin user on the basis of information about his/her use of a public key hash.
The first method consists of the following three steps: (1) sending a legal demand to Bitcoin-processing businesses (e.g., Bitcoin wallets and Bitcoin exchanges); (2) analyzing the received information; and (3) identifying the user of a particular public key hash. Regarding the first step, it should be noted that a large number of Bitcoin-processing businesses collect personal information from their customers. For example, all e-shops which accept Bitcoin use shipping addresses collected from their customers. Such addresses can be used for the identification of the buyers. As for the second step, many e-discovery software applications provide their users with the opportunity to analyze a vast amount of electronic data, such as paper documents, web data, cloud data, and data stored on mobile applications. The third step will be easily completed if the user of a particular public key hash has provided Bitcoin-processing business with his/her personal information.
The second method also consists of three steps, namely, (1) collecting information about the use of a public key hash, (2) combining the collected information with other available information, and (3) analyzing the research findings. For example, if a public key hash is discovered in the same time slots as the activity of a particular Facebook account, one can reasonably conclude that the user of the public key hash is the same person who owns the detected Facebook account.
The classical forensic approach still helps numerous law enforcement authorities in revealing the identities of participants in Bitcoin transactions. As Peter Van Valkenburgh, director of research at a Washington think tank focused on digital currencies, states: "Old fashioned police work is always going to be the main method of investigation." The classical forensic approach is particularly helpful when investigating illegal Bitcoin exchanges which are related to ransomware. This is because such exchanges often use traditional payment accounts (e.g., a bank account) to keep the money received in exchange for Bitcoins. For example, in 2015, the FBI arrested two individuals for operating an illegal Bitcoin exchange, which was allegedly used for selling Bitcoins to victims of ransomware. The individuals transferred money to bank accounts in Eastern Europe, Hong Kong, and Cyprus and received money in bank accounts in the British Virgin Islands and Cyprus.
Section 3. BitCluster
BitCluster (freely downloadable at https://www.bit-cluster.com/) is an open-source tool which allows its users to group Bitcoin transactions by their participants. Such groups of transactions may be used for identifying Bitcoin users. Commenting on the purpose of the tool, Professor David Décary-Hétu, one of the creators of BitCluster, stated: "Our goal was to see, how much data can you gather on people who are using the Bitcoin network, and can you aggregate the Bitcoin wallets which seem to be anonymous and isolated from one another?"
BitCluster allows law enforcement authorities to calculate the amount of money generated by public key hashes. Consequently, the tool can be used for detecting ransomware schemes which generate significant amounts of ransom money. However, it is worth mentioning that BitCluster has an important disadvantage. Namely, the tool becomes useless if a ransomware creator generates a new public key hash for every payment transaction.
Although BitCluster is not created to be specifically used by law enforcement authorities, it can be used as a prototype for the development of comprehensive Bitcoin forensic software which is specifically tailored to the needs of the FBI and its foreign counterparts.
Section 4. Elliptic
Elliptic is a new technology which allows researchers to (1) trace entities transactions through the blockchain automatically and instantly; (2) uncover relationships between different entities; and (3) employ artificial intelligence to acquire digital clues from the Internet and the dark Web which can be used for uncovering the real identities of participants in Bitcoin transactions. Also, it should be noted that Elliptic assigns a risk score (0 = low risk, 10 = high risk) to participants in Bitcoin transactions.
The relationships between different entities are presented in Elliptic in the form of a comprehensive graphical user-interface. A screenshot of such a user-interface is provided below.
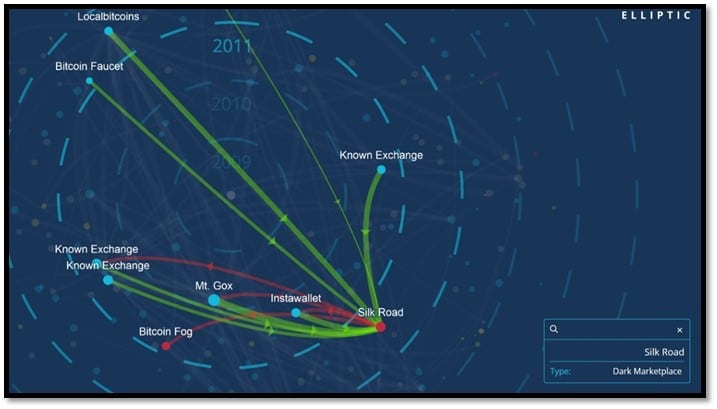
Figure 1: A screenshot of Elliptic user-interface
The screenshot indicates the relationships between the illegal marketplace "Silk Road" and various other entities processing Bitcoins. According to a report published by Trend Micro in 2013, "Silk Road" generated sales amounting to over 9,5 million Bitcoins, which equals to USD 1,2 billion.
Financial institutions widely use Elliptic, and law enforcement authorities to trace the origin of Bitcoins. Up until the present moment, it has processed more than USD 2 billion in Bitcoin transactions. Without the possibility to trace the origin of Bitcoins, legitimate financial organizations may trade with Bitcoins coming from illegal activities. Consequently, such processing may raise legal issues (e.g., violation of anti-money laundering laws) as well as reputational implications (acquiring the reputation of an institution involved in criminal activities). In an interview on this subject, Dr. Tom Robinson, COO & Co-Founder of Elliptic, pointed out: "We realized that what was holding back Bitcoin use by financial institutions was illicit activity on the dark Web. Financial institutions were scared to death."
By providing actionable intelligence to law enforcement agencies and financial institutions, Elliptic may significantly hamper the operation of ransomware schemes. More specifically, Elliptic may facilitate the arrest of operators of ransomware schemes and enable financial institutions to refuse to process Bitcoins collected through ransomware attacks.
Section 5. Conclusion
The appearance of Bitcoin and other cryptocurrencies was the main cause for the recent proliferation of ransomware attacks. As Craig Williams, a security expert at Cisco, observed: "The ability to demand payment in Bitcoin, a difficult-to-trace virtual currency not controlled by any country, was 'the birth of ransomware' and has helped drive its success since the currency's introduction in 2009." The most widely known Bitcoin ransomware applications are CryptoWall and CryptoLocker.
The main reason for the success of Bitcoin ransomware is the difficulty related to tracing Bitcoin transactions. If this issue is eliminated, we can expect a decrease in the number of ransomware attacks which request victims to pay a ransom in Bitcoin. Although Bitcoin is considered to be anonymous cryptocurrency, our article examined three approaches to revealing the identity of criminals involved in Bitcoin ransomware schemes. Although none of the three approaches guarantees the complete identification of such criminals, the discussed approaches may provide a vast amount of information necessary for guiding governmental authorities in the investigation of ransomware attacks.
However, cyber-criminals do not remain passive observers of the developments of the discussed technologies. According to a study by Kharraz, Robertson, Balzarotti, Bilge, and Kirda, organizers of ransomware schemes started using techniques to protect their privacy, such as using multiple independent Bitcoin addresses, wherein each address processes small Bitcoin amounts. According to the same study, 84,46% of the examined Bitcoin addresses which were used for receiving ransomware payments had no more than six transactions. 68,93% of the examined addresses were active for no more than ten days. In 48.9% of the analyzed addresses, a Bitcoin address received no more than 2 Bitcoins. In the light of the findings of the aforementioned study, we may conclude that the new approaches to revealing the identity of Bitcoin users must constantly evolve to reflect the ever-changing ransomware landscape.
Sources
- Brook, C., 'Bitcoin Phishing Campaign Uncovered,' Threat Post, 21 June 2016. Available at https://threatpost.com/bitcoin-phishing-campaign-uncovered/118799/.
- Butnix, J., 'Haggling The Price After A Ransomware Infection Can Pay Off,' Live Bitcoin News, 19 July 2016. Available at http://www.livebitcoinnews.com/haggling-the-price-after-a-ransomware-infection-can-pay-off/.
- Caffyn, G., 'FBI: Malware Victims Should Pay Bitcoin Ransoms,' CoinDesk, 26 October 2015. Available at http://www.coindesk.com/fbi-malware-victims-should-pay-bitcoin-ransoms/.
- Ciancaglini, V. et al., 'Deepweb and Cybercrime', Trend Micro. Available at
http://www.trendmicro.com/cloud-content/us/pdfs/security-intelligence/white-papers/wp-deepweb-and-cybercrime.pdf . - Cox, J., '7 Ways the Cops Will Bust You on the Dark Web', MotherBoard, 26 June 2016. Available at https://motherboard.vice.com/read/7-ways-the-cops-will-bust-you-on-the-dark-web.
- Cox, J., 'This Open Source Tool Can Map Out Bitcoin Payments,' MotherBoard, 18 July 2016. Available
at http://motherboard.vice.com/read/open-source-tool-bitcluster-can-map-out-bitcoin-payments. - Datt, S., 'Learning Network Forensics,' Packt Publishing: 2016. Available at https://books.google.be/books?id=VWxLDAAAQBAJ&pg=PA199&dq=Bitcoin+ransomware&hl=en&sa=X&redir_esc=y#v=onepage&q=Bitcoin%20ransomware&f=false.
- Detsch, J., 'Could bitcoin hold the key to stopping ransomware?', The Christian Science Monitor, 1 July 2016. Available at http://www.csmonitor.com/World/Passcode/2016/0701/Could-bitcoin-hold-the-key-to-stopping-ransomware.
- Dunn, J. E., 'Elliptic: UK Bitcoin startup plots future in dark web forensics,' Tech World, 19 July 2016. Available at http://www.techworld.com/security/elliptic-uk-bitcoin-startup-plots-future-in-dark-web-forensics-3643784/.
- Elliptic. Available at https://www.elliptic.co/ .
- 'Evaluating the Customer Journey of Crypto-Ransomware and the Paradox Behind It,' F-Secure, 18 July 2016. Available at
https://fsecureconsumer.files.wordpress.com/2016/07/customer_journey_of_crypto-ransomware_f-secure.pdf. - Gautham, 'Bitcoin Ransomware May Soon Become a Thing of the Past', News BTC, 3 July 2016. Available at http://www.newsbtc.com/2016/07/03/bitcoin-ransomware-may-soon-become-thing-past/.
- Kharraz, A. et al., 'Cutting the Gordian Knot: A Look Under the Hood of Ransomware Attacks,' NEU SecLab, 23 June 2015. Available at http://seclab.ccs.neu.edu/static/publications/dimva2015ransomware.pdf.
- 'KSN Report: PC ransomware in 2014-2016', Securelist, 22 June 2016. Available at https://securelist.com/analysis/publications/75145/pc-ransomware-in-2014-2016/.
- 'Manhattan U.S. Attorney Announces Charges Against Two Florida Men for Operating an Underground Bitcoin Exchange', FBI, 21 July 2015. Available at https://www.fbi.gov/contact-us/field-offices/newyork/news/press-releases/manhattan-u.s.-attorney-announces-charges-against-two-florida-men-for-operating-an-underground-bitcoin-exchange.
- Narayanan, A. et al., 'Bitcoin and Cryptocurrency Technologies: A Comprehensive Introduction,' Princeton University Press: 2016. Available at https://books.google.be/books?id=LchFDAAAQBAJ&pg=PA138&dq=%22Bitcoin%22+%22anonymity%22&hl=en&sa=X&redir_esc=y#v=onepage&q=%22Bitcoin%22%20%22anonymity%22&f=false.
- Stevenson, A., 'We're finally getting some answers over the massive JPMorgan hack,' Business Insider UK, 22 July 2015. Available at http://uk.businessinsider.com/the-fbi-just-arrested-4-men-for-suspected-involvement-in-scams-tied-to-the-jpmorgan-breach-2015-7.
- Titcomb, J., 'Bitcoin surveillance firm Elliptic raises $5m as banks push into blockchain', The Telegraph, 20 March 2016. Available at http://www.telegraph.co.uk/technology/2016/03/20/bitcoin-surveillance-firm-elliptic-raises-5m-for-blockchain-push/.
- Van Impe, K., 'Will Blockchain Technology Replace Traditional Business Models?', Security Intelligence, 6 July 2016. Available at https://securityintelligence.com/will-blockchain-technology-replace-traditional-business-models/.
- Williams-Grut, O., 'New bitcoin technology can tell banks where coins come from with incredible accuracy,' Business Insider UK, 18 June 2015. Available at http://uk.businessinsider.com/bitcoin-elliptic-startup-anti-money-laundering-tool-get-banks-interested-cryptocurrency-2015-6.
Co-Author

 Rasa Juzenaite works as a project manager in an IT legal consultancy firm in Belgium. She has a Master degree in cultural studies with a focus on digital humanities, social media, and digitization. She is interested in the cultural aspects of the current digital environment.
Rasa Juzenaite works as a project manager in an IT legal consultancy firm in Belgium. She has a Master degree in cultural studies with a focus on digital humanities, social media, and digitization. She is interested in the cultural aspects of the current digital environment.






