Getting started with Damn Vulnerable iOS Application
In this article, I will write about how to get started with Damn Vulnerable iOS Application. Damn Vulnerable iOS App (DVIA) is an iOS application that I wrote to provide a platform to mobile security enthusiasts/professionals or students to test their iOS penetration testing skills in a legal environment. This application covers all the common vulnerabilities found in iOS applications (following OWASP top 10 mobile risks) and contains several challenges that the user can try. Every challenge is coupled with an article that the users can read to learn more on that topic. This application can also be used by absolute beginners in iOS application security as the tutorials that come with DVIA are written keeping beginners in mind. The users can also buy a comprehensive guide of solutions for DVIA if they want. DVIA is also open source and its Github page can be found here.
Installing DVIA
Note: DVIA only supports IOS 7 devices, older versions of IOS are not supported. DVIA also supports 64 bit devices. Please make sure to download the latest version of DVIA.

11 courses, 8+ hours of training
The very first thing to do is set up an iOS pen-testing environment on your iOS device. You can audit DVIA using simulator as well, but I would recommend trying it out on a device. You can read articles about setting up a pen-testing environment for iOS7. Once you have set up the environment, there is a very good video created by Kyle Levin where he talks about multiple ways of installing DVIA on your device.
[youtube id="PwES8Sk00wk" width="600" height="350"]
In any case, here are the text instructions of installing DVIA on your device. You can jump to the next section on Exploring DVIA if you have already installed it on your device.
Running on System or Device using Xcode
Download the latest source code of Damn Vulnerable iOS Application from here.
Note that you will need to have Xcode installed on your computer to build this application. Once you have installed the latest version of Xcode, you can just run the application on your computer by using Xcode and do all the analysis on the simulator if you want.
Please open DamnVulnerableIOSApp.xcworkspace to run the project. Don't use the file DamnVulnerableIOSApp.xcodeproj as the build will fail. This is because DVIA uses Cocoapods.
To run the application on your system using iOS simulator, just run the application (Cmd + R) after selecting the target and the application will install on the simulator.
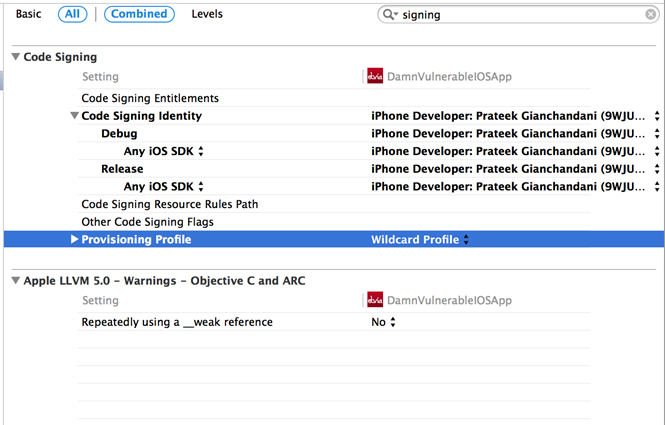
To install and run the application on your device using the source code, you need to have a valid provisioning profile. This requires purchasing the iOS developer program that comes at a cost of $99/year. Go to the DVIA Project, Select your Target -> Settings -> Code Signing and make sure the proper Code Signing identity and Provisioning profile are selected.
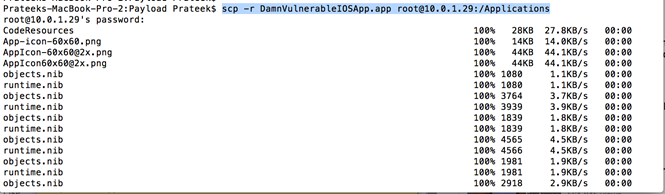
Copying the .app file on device and using uicache
Download the .ipa file from the downloads page, change its name from DamnVulnerableIOSApp.ipa to DamnVulnerableIOSApp.zip and unzip this file. This will unzip to a folder named Payload. Inside it, there will be a file named DamnVulnerableIOSApp.app. Then copy the .app file to the /Applications directory on the device using Scp. You can also use sftp or the utility iExplorer to upload this application.
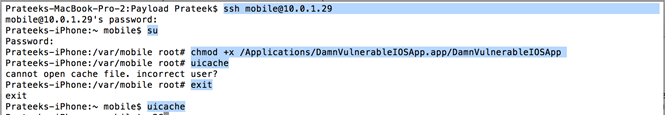
Now login as the mobile user, use the command su to get root privileges and give the DVIA binary executable permissions. Then use the exit command to go back as the mobile user, and use the command uicache to install the application. If this doesn't work, you can reboot the device or try this method again.
Using IPA Installer
Requires a device running IOS 7 and Appsync installed. Please note that we don't promote the use of Appsync, and hence this method should only be used as a last alternative.
Download the latest IPA of Damn Vulnerable IOS Application here.
One of the ways to install the application is by using the terminal utility IPA Installer Console. Make sure you install it on your device.
Now sftp into your device and upload the IPA file that we have just downloaded.
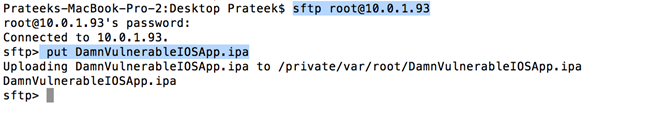 Now use the command "ipainstaller DamnVulnerableIOSApp.ipa" or "installipa DamnVulnerableIOSApp.ipa" to install the application on your device.
Now use the command "ipainstaller DamnVulnerableIOSApp.ipa" or "installipa DamnVulnerableIOSApp.ipa" to install the application on your device.
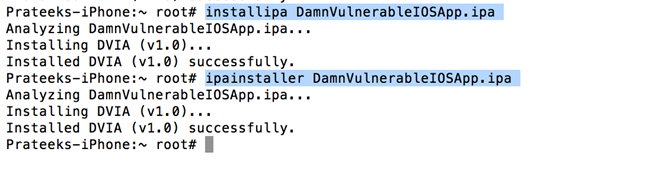
Using AppSync
Make sure AppSync is installed on your device. To install AppSync on your device, follow these steps.
- Launch Cydia app on your device
- Select Manage
- Select Sources
- Select Edit
- Select Add
- Add the source repo.hackyouriphone.org
- Now search for AppSync
- Install AppSync for IOS 7+.
Now double click on the ipa file that you just downloaded on your computer. This will add the application to iTunes. Now go to iTunes, select the install option on DVIA application and sync it to your device. This will install the application on your device.
Exploring DVIA
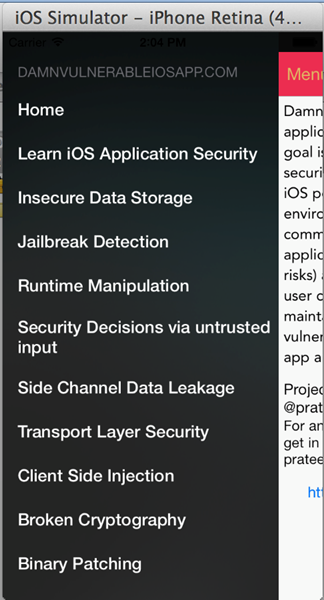
DVIA comes loaded with a lot of challenges covering most of the common vulnerabilities found in iOS applications. The current list of vulnerabilities and challenges includes:
- Insecure Data Storage
- Jailbreak Detection
- Runtime Manipulation
- Transport Layer Security
- Client Side Injection
- Information Disclosure
- Broken Cryptography
- Application Patching
- Security Decisions via Untrusted input
- Side channel data leakage
You can just swipe from the left in the application and see a list of vulnerabilities and challenges you can have a go at. Since almost every vulnerability comes with a related tutorial, you can read it up to learn more on that specific vulnerability before attempting the challenge.
Auditing DVIA
Well, let's try and solve some challenges. You can audit DVIA both on device and the simulator, however I would recommend you do all the auditing on device. Let's open up the Client Side injection section.
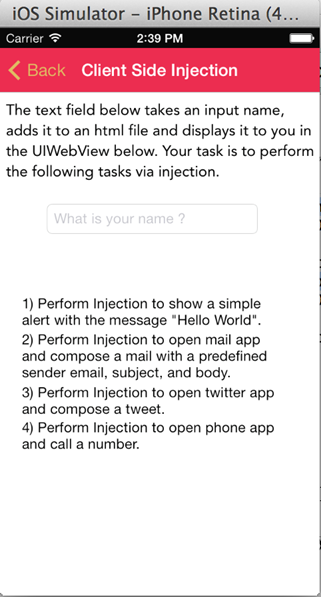
Let's enter a random name and press enter, say Apple.
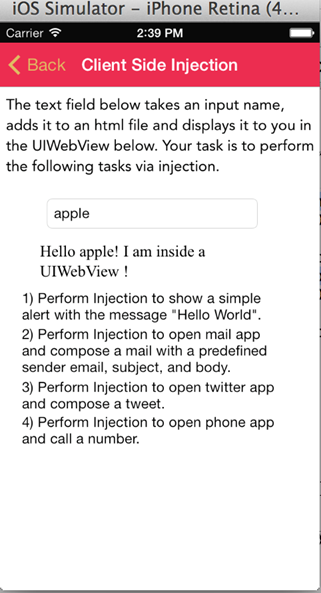
The first challenge is to show a simple alert with injection. It is clear from the above image that the text is added to this UIWebview. If this input is not validated properly, we might be able to inject some Javascript that will get executed in the UIWebview. Let's enter the following as the input.
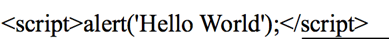
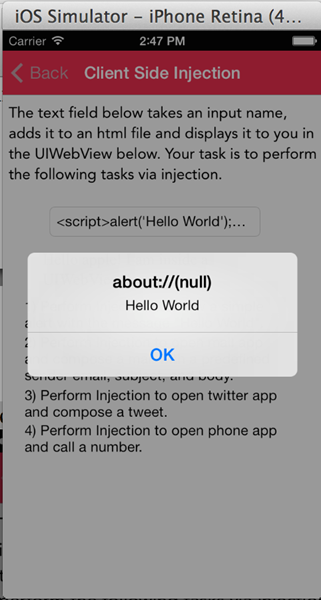
Awesome, it looks like this injection worked. For the other challenges, you can use Javascript to call native functions on the device. Well, how do you do that ? Let me give you a hint, read about URL schemes and what they are used for.
Now let's move on to some other challenges. Let's have a look at the Jailbreak Detection section and try to solve the first challenge. Our task is to fool the application into thinking that it is not jailbroken even though we are running the application on a jailbroken device.
So let's ssh into the device and dump the class information for this application by navigating to the folder where the application binary is located and using the command class-dump DamnVulnerableIOSApp .
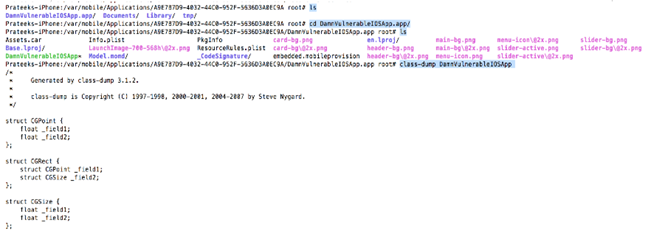
On scrolling down a bit, we see the function (BOOL)isJailbroken; in the class JailbreakDetectionVC that returns a BOOL value.
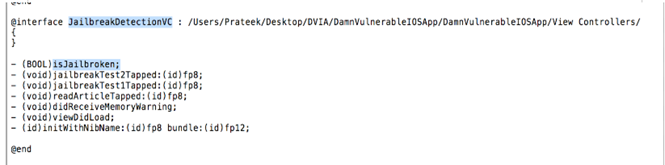
Looks like this method is the one that is used to check whether a device is jailbroken or not. If we modify the implementation of this method to return NO, then our task will be accomplished. Let's use cycript to overwrite this method's implementation. First, lets hook into the application by finding the process ID of the application and using the command cycript -p PID. Make sure the application is running in foreground or we won't be able to hook into this application.
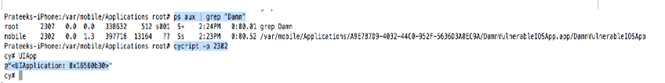
Now modify the implementation by using the following command in the cycript interpreter.
JailbreakDetectionVC.messages['isJailbroken'] = function () {return NO};

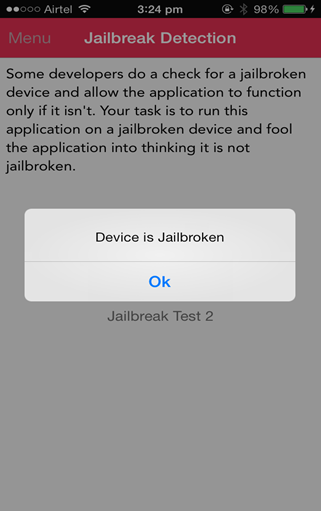
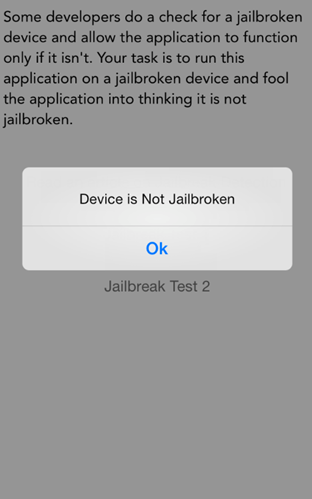
And now, if you tap on the button Jailbreak Test 1 in the application, you will see that the alert says Device is not jailbroken, even though the device I am currently running the application on is actually jailbroken.
Similarly, you can try other challenges in the application as well. As I said before, DVIA is open source, however I assume that when you audit the application to solve challenges, you do a black box audit and don't look at the source code. If you are unable to solve some challenges, you can buy the solutions. The proceeds from this purchase support the DVIA project and give us dedicated time to improve the application, add new challenges, etc.

11 courses, 8+ hours of training
Any feedbacks, comments for the application are welcome. My next aim is to add more challenges and vulnerabilities in DVIA as time progresses. I hope you enjoy using and learning from DVIA as much as I enjoyed developing it :-).






