Free Web Application Scanners, Part 1
With the rapid increase in technology usage, every company is desperate to provide their services over the Internet. They believe that by offering their services online they come closer to the people, which in turn increases their revenue. For instance people no longer have to step out of their room to book a movie ticket or to transfer money to another account. In this race to provide online services, companies have blindly moved to the Internet to increase their power. But with great power comes great responsibility. With the rapid increase in cyber-attacks the industry has realized the importance of securing their content on the web. With a simple well-crafted payload a hacker might steal the passwords of all the users of a social networking site or millions of bucks from a commercial bank. So securing the web applications would mean assuring the continuity of business.
What is a Web Application Scanner?

11 courses, 8+ hours of training

11 courses, 8+ hours of training
A web application scanner or web application vulnerability scanner is a tool which aids security analysts and professionals in identifying the vulnerabilities present in a web application. It is a black box testing tool which means the vulnerabilities are detected by actually performing the attack. They scan the application to identify a variety of vulnerabilities which may range from critical issues like SQL injection to low severity issues like server platform information leakage.
Why Use a Scanner?
A tool can never be a replacement for the human mind. Given that let me explain how a web application scanner can help you process your job. A tool may not identify all the vulnerabilities present in an application, but it certainly identifies those issues which are easy to find and it identifies them in no time. Thus if you have 100 applications and you want to make sure that you at least fix those issues which are out there inviting unwanted attention, you can use a scanner to scan all of them in a single day and go ahead and fix them. So in short a vulnerability scanner offers 2 things - basic scan coverage and quick scan time.
Free Web Application Scanner
There are free web application scanners available each with its own advantages and limitations. However one thing has to be noted here. Free web application scanners take a back step when compared with the available commercial tools in terms of in-depth scan coverage and options available. However not every developer can afford to go for a commercial tool as it involves the cost factor. Hence a free scanner helps many developers and security researchers to at least discover the basic vulnerabilities present in their web applications. But these scanners lack the complete features which are included in the licensed versions. This article identifies the tools available, lists the features and provides steps to scan a web application using the tools. Let's have a look at the tools and how to use them to scan the applications.
Free Web Application Scanners Available
Scanning of web applications these days is a hot skill and there is no surprise why you wouldn't find free web application scanners that can compete with the commercial ones. But still there are a few tools which can serve your purpose depending on your requirements. However they may not contain all the features. But I felt listing the free tools under a single article would definitely help many people who would like to have a hands-on experience and also the web developers who would like to scan their web applications. Netsparker Community Edition, OWASP ZAP, N-Stalker free edition, Skipfish, wapiti, webscarab, scrawl, watcher, Accunetix free version, XSS Me, SQL inject Me, etc. are some of the best free or open source tools available for web application scanning. This article aims to cover each tool with its basic introduction followed by available features, steps to scan and conclusion. All the tools covered in this article are either free or open source tools. Note that it's not legal to perform unauthorized scans on external websites using any of these tools.
Netsparker Community Edition
Netsparker Community Edition helps not only Penetration testers but also web developers who can scan their web application instantly and find the vulnerabilities for free. But this edition scans only for XSS, SQL injection, Boolean SQL injection, backup files and static tests. So you can mainly consider this as an XSS and SQLi scanner. The user interface will definitely impress you. Netsparker scans all kinds of web applications without limiting itself to any platforms or technologies. It is from Mavitunasecurity and can be downloaded from the below link.
http://www.mavitunasecurity.com/communityedition/
For those people who are interested to know more about the full edition of Netsparker, here is the list of vulnerabilities that Netsparker licensed edition scans for.
Vulnerabilities : E-mail Address Disclosure, Internal IP Disclosure, Cookies are not marked as Secure, Cookies are not marked as HTTPOnly, Directory Listing, Stack Trace Disclosure, Version Disclosure, Access Denied Resources, Internal Path Disclosure, Programming Error Messages, Database Error Messages, SQL Injection, Local File Inclusions & Arbitrary File Reading, Remote File Inclusions, Remote Code Injection / Evaluation, XSS (Cross-site Scripting), OS Level Command Injection, CRLF / HTTP Header Injection / Response Splitting, Find Backup Files, Crossdomain.xml Analysis, Finds and Analyses Potential Issues in Robots.txt, Finds and Analyses Google Sitemap Files, Detect TRACE / TRACK Method Support, Detect ASP.NET Debugging, Detect ASP.NET Trace, Checks for CVS, GIT and SVN Information and Source Code Disclosure Issues, Finds PHPInfo() pages and PHPInfo() disclosure in other pages, Finds Apache Server-Status and Apache Server-Info pages, Find Hidden Resources, Basic Authentication over HTTP, Password Transmitted over HTTP, Password Form Served over HTTP, Source Code Disclosure, Auto Complete Enabled, ViewState is not Signed, ViewState is not Encrypted, Custom 404 Detection, Heuristic URL Rewrite Detection.
Once downloaded, it shouldn't take any trouble to install it. Before actually going into the scan details let's have a brief look at the main features of Netsparker community edition.
Main Features of Netsparker Community Edition:
- Netsparker boasts of generating false positive free report which means that Netsparker assures that all the vulnerabilities reported by it are real and existing. Netsparker not only tries to identify but also exploits the issue to make sure that it's a valid finding. For those issues where the tool is not confident or issues which might require manual investigation, the issue is mentioned as 'Possible' or 'High Possibility' etc.
- It supports AJAX and JavaScript.
- Netsparker supports several authentication methods: Basic, Form, NTLM and Digest Authentication. So depending on your application, you can use any of the mentioned methods. Unfortunately this option is not provided in the community edition.
- Netsparker identifies the issue, classifies it further and presents the remediation details. For instance if an XSS vulnerability is identified, the summary of the vulnerability and remediation details are provided.
- Supports error based and Boolean based SQL injection. Time based SQL injection is not supported in the community edition.
-
Community edition provides free automated updates.
Steps to scan:
- Start the Netsparker Community Edition and go to File Start New Scan
- In the window that appeared enter the target URL (say http://demo.testfire.net/ ) and select 'full scan' in the drop down window adjacent to it.
- Now click on 'Start scan' present at the bottom of the window.
- The scan will be started and the screen would be populated with the identified vulnerabilities one by one.
-
At the end of the scan you will be presented with the below screen which shows the Site Map, Dashboard, Issues, vulnerabilities identified, etc.

As shown in the above figure, it has identified issues related to SQL Injection, Cross site scripting, Cookie not marked HTTPOnly, autocomplete enabled etc. It's up to the penetration tester or the developer to analyse and confirm whether it's a false positive or a valid finding.
The Site map provides hierarchical structure of the website listing the directories and pages under them. Click on a particular vulnerability and its corresponding details can be viewed under 'Vulnerability' tab. The 'Browser View' tab shows the same in browser. HTTP Request/Response tab is the one where you can analyse the issue, see the request parameters etc.

You can also group the issues by severity, Vulnerability type, Confirmed/Not Confirmed and URL. You can play with the scan configuration by selecting the 'Settings' option where you can modify settings related to scanning, crawling, proxy etc.
Conclusion:
Overall, this tool comes in handy if you want to get a feel of working a with web application scanner. It identifies critical issues like XSS, SQLi and also other low severity issues.
N-Stalker Free edition
This free edition of N-Stalker provides a restricted vulnerability check to identify the security holes in your web application. It also identifies web server related vulnerabilities apart from the issues like cross site scripting, etc. But one limitation is that it can scan only til 100 pages within target application. The free edition can be downloaded from the below link where the details including email id need to be submitted:
http://www.nstalker.com/products/editions/free/
Upon opening the tool, this is how the interface of the tool looks. The top section shows the tools available in N-Stalker.

Main Features of N-stalker free edition:
- It supports OWASP Policy, Full XSS assessment, manual test (spider only) and also webserver infrastructure analysis.
- Provides set of tools like HTTP Bruteforce, web discovery, encoder tool etc.
- Free edition provides automatic updates too.
Steps to scan:
- Enter the URL of the target site and select the scan policy from the dropdown box. Note that N-Stalker does not allow scanning of demo sites.
- Scan policy can be OWASP policy, XSS policy or webserver infrastructure analysis.
- Click on 'Start Scan Wizard' and in the next window click on next unless you have something to edit.
- You may choose to click on 'Optimize' button which gives you a list of recommendations which you may even ignore. If implemented they would help for a better scan analysis. Click on next.
- Click on 'Scan Settings' tab to have a look at various options under it. It contains wide range of options related to spidering, crawl options etc. Press "Next" to continue.
- Highlights of Scan settings will be presented for your review. You can modify any of these setting by clicking the back button.
-
Click 'Start Session' to initiate the scan and the click on 'Start scan' in the next window.
This is how the scanner dashboard looks like while the scan is in progress.

Under the 'Website Tree' the hierarchical structure of the site is revealed. All the pages and folder present in the site are listed as per the directory structure. 'Scanner events' section contains details about scanner and vulnerabilities. Vulnerabilities are added to this section as they are discovered. The dashboard shows the overall security posture of the application by mentioning the number of low, medium and high severity vulnerabilities present. As you select the options under 'Scanner events', the corresponding details appear in the adjacent window.
Expand the vulnerabilities tab to see the list of vulnerabilities which were identified by N-stalker. Click on a particular vulnerability to see the corresponding details. For instance upon clicking a cross site scripting vulnerability the below vulnerability information is shown.
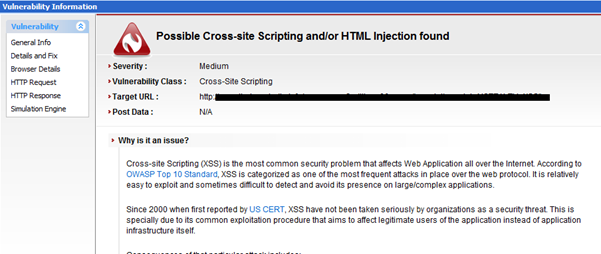
The HTTP Request and Response is mentioned for a clear understanding. The remediation details are also provided in order to fix the issue. There is also an option called simulation engine which can be used to simulate an attack. The parameters can be modified and the request can be forwarded to observe the response. These vulnerabilities need to be analysed in this manner to eliminate the false positives.
Conclusion:
N-Stalker free edition is definitely worth trying mainly as it picks up wide range of issues even though there is limit on the total scan coverage. So if you are dealing with a small application and want to find out the basic vulnerabilities present in the application then you can attempt to work with this tool.

11 courses, 8+ hours of training

11 courses, 8+ hours of training
The remaining tools will be covered in next part of this article. Happy scanning!!






