Security Awareness & Training Resource Center
Featured content

Deconstructing Human-Element Breaches | Infosec HRM
Human risk management isn’t just rebranded SA&T — it’s a profound change of mindset, strategy, process and technology that approaches human-related breaches in a new way.
![Inside an Infosec Boot Camp: All your questions, answered! [replay]](/globalassets/is-wb-24-05-inside-an-infosec-boot-camp_thumbnail2.webp?width=338&height=304&rmode=Max&bgcolor=transparent)
Inside an Infosec Boot Camp: All your questions, answered!
You need to get certified, but is an Infosec Boot Camp the right choice for you — or your team? Find out in this live Q&A with two Infosec instructors.

Emerging trend checklist: Which certifications cover which new skills?
Boost your team's cybersecurity skills with the right certifications. Discover the most in-demand skills and the certifications that cover them in our free guide.

Security Awareness Outcomes with Infosec IQ
See security awareness and training outcomes from more than five million Infosec IQ learners.
Our resources

Cybersecurity Weekly: UScellular data breach, Emotet takedown, Washington State breach

Wireless attacks and mitigation

Zerologon CVE-2020-1472: Technical overview and walkthrough

Wireless network overview

Incident response and recovery best practices for industrial control systems

Introduction to full disk encryption

Average IT manager salary in 2021

Upskilling to deepen employee engagement & retention
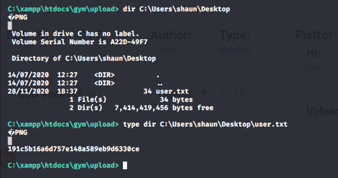
Hack the Box (HTB) machines walkthrough series — Buff

8 reasons you may not want to use VPNs

Security vs. usability: Pros and cons of risk-based authentication

Email forensics: desktop-based clients

What is a Honey Pot? [updated 2021]
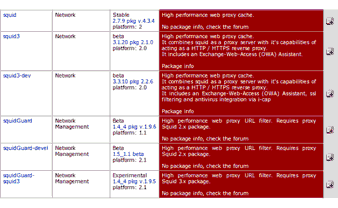
Hacking clients with WPAD (web proxy auto-discovery) protocol [updated 2021]

CloudGoat walkthrough series: Remote code execution

PenTest+: DoDD 8570 overview

Proper use and training are the keys to mastering secure C++, says Infosec Skills author Martin Dubois

Open source IDS: Snort or Suricata? [updated 2021]

Email forensics: Web-based clients

Email analysis

Software maturity models for AppSec initiatives

Investigating wireless attacks

Wireless networking fundamentals for forensics

What is enumeration? [updated 2021]