Advanced Technical Review of VPN Infrastructure Impacts
Introduction
As it was reviewed in the last article, the procurement and deployment of a Virtual Private Network Infrastructure can be a complex task. In fact, it can lie on either extreme; it can be very small implementation or a very large one.
This is largely dependent upon the size of the business or the corporation (the most important variable in this circumstance is the total number of employees), and the specific Security requirements that are involved.
Learn Network Security Fundamentals
While using a Virtual Private Network Infrastructure is one of the best ways to ensure the security of the lines of communication between the sending and the receiving parties, it should not be relied on as the sole means either.
For instance, just using a password alone to confirm the identity of an individual is not enough, using just a VPN is not enough either. There are other Security mechanisms which should be implemented as well.
Let us illustrate this with an example. Suppose that a remote employee wishes to login into the Central Server(s) at the place of business or corporation. As they log in, he or she will establish the remote connection via a VPN tunnel.
In this regard, the login credentials will be encapsulated into various Data Packets which will then be further encapsulated into other Data Packets to keep them "invisible" to the outside world.
Also, primary lines of communication will be established between the employee's remote workstation and the Central Server(s).
This will be visible to the outside world, but the second line of communications will be subsequently established as well (going into the same direction as the first line of communications), but this too will be "invisible" to the outside world. It is on this medium upon which the encapsulated Data Packets will travel upon.
However, one of the cardinal rules of Cybersecurity is that never take anything for granted when it comes to the mind of the Cyber attacker. In other words, it is when you think that you are the most secure that you will most likely be caught off guard, and fall prey to the Cyber attacker.
So, even though there are two layers of defense already offered (namely the "invisible" Data Packets and the second lines of communications), there should be more.
For example, along with the password, there should be other types and kinds of login credentials which should be used, such as a Biometric (like a Fingerprint or Iris Scan), and a Remote Access FOB (such as those manufactured by RSA Security).
Then, along with the lines of communications, there need to be several automated "checkpoints" installed to confirm that the contents of the Data Packets are still intact, and have not been altered in any way, shape, or form.
Although this is the primary function of the Hashing Algorithm, it is important to keep in mind that it only checks the integrity of the Data Packets at the destination point, not while they are in transit.
As the Data Packets from the employee's remote workstation enter into the perimeter of the business or the corporation, they will no doubt be inspected by the Firewall(s) to make sure that they are legitimate, and not malformed.
Although the Firewall does an effective job of this, it too is not enough, and thus the use of Routers and Network Intrusion devices are also required to be used in tandem.
Once inside the IT infrastructure of the business or corporation, the Data Packets are still prone to a Cyber-attack. For example, if there is too much "broadcasting" of the Data Packets which is occurring from the Network based Bridges and Switches, it means that the Data Packets are simply "roaming" around. Thus, they are extremely vulnerable to covert interception by a malicious third party.
So as one can see from this very simple illustration, the impacts of a Virtual Private Network Infrastructure implementation needs to be into serious consideration for both the internal and the external environment.
In this article, we continue on this theme, but looking at the impacts from within the IT infrastructure of a business or a corporation, focusing on the following:
- The Impacts to the Application Server;
- The Impacts to the Database Server;
- The Impacts to the Firewall.
The Impacts to the Application Server
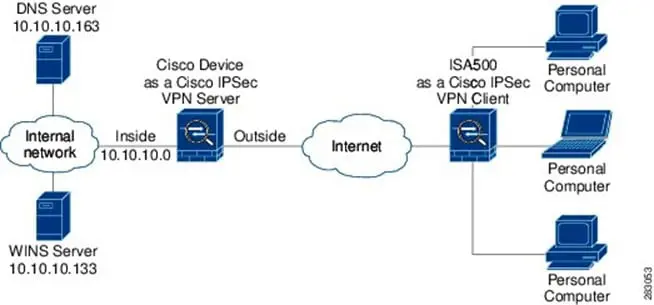
The second level of the Information Technology Infrastructure that will be greatly impacted by the procurement and deployment of a VPN is that of the Application Server. Simply put, these are the specialized software components that are relevant to the organization.
When implementing a Virtual Private Network Infrastructure in this type of setting (where it works in conjunction with the Application Server), the use of a Trusted Host must be considered very seriously.
This type of mechanism makes use of various Access Control Lists (also known as "ACLs") to thwart off Cyber based attack attempts on the various software applications and programs which are running on this specific type of server.
It should be noted that the Access Control information and data that is stored on the Application Servers should be converted into a garbled format (in a manner similar to that of the process which is involved in creating a Ciphertext). This type of metadata should never be stored as Plaintext files.
It is also important to remember that not too much of a workload should be placed on the Application Server, as this could adversely affect the performance of the VPN because, in turn, it will have a very negative impact upon the inflow of the Data Packets.
The Impacts to the Database Server
The third level of Information Technology system which can be impacted by the deployment of a Virtual Private Network Infrastructure is that of the Database Server.
There is no need to underscore the primary importance of this, as it contains the database(s) which are relevant to the products/services, purchasing, and other types and kinds of customer information/data.
More than likely, it will also contain the Data Warehousing Algorithms which are used to comb through and manipulate all of these datasets.
For the Database Servers, it is either an Object Oriented Database Management System, or just the traditional Database Systems in which only tables and columns are utilized.
However, whatever the type of Database Server structure the business or the corporation, in the end, decides to use, the relevant software packages which are contained in them must be compatible with the technology of the Virtual Private Network Infrastructure. This must be ascertained and determined even before it is deployed.
In this regard, it is imperative that to make sure that all of the information/data the organization has is encrypted across all levels when it is incorporated into the VPN. This includes all aspects of the Database structure, which are the fields, the rows, and the tables.
The Impacts to the Firewall

Finally, another key component that cannot be overlooked in Virtual Private Network Infrastructure deployment is that of the Firewall. In fact, many Security experts would agree that putting a VPN in front of the Firewall is one of the best decisions that could be made in fortifying the lines of defense (see the illustration up above). For example:
- A single set of rules allows one to control the flow of Data Packets in and out of the Virtual Private Network Infrastructure.
- A single point of administration helps you to manage changes quickly and effectively as the changing needs of the business or corporation dictate.
- Finally, by having a single point of access at the Firewall level, this allows you to have complete control over the entire IT network.
Conclusions
In summary, the implementation of a Virtual Private Network Infrastructure is in some ways, similar to that of deploying a Biometrics based Infrastructure, as some our earlier articles have reviewed in detail as well. There is both a human component and technical component upon which a VPN can have an impact.
Regarding the former, it is imperative to train the end users (such as the employees of the business or corporation) in how to properly login into the VPN, and making sure that they know how to use the other security mechanisms which are associated with it.
For instance, this could include using an RSA Security FOB, which provides a rotating sequencing of numbers every few minutes. The employees will need to be trained when they need to use this tool (and especially how to use it) during the login process into the VPN. Regarding the impacts to the Information Technology Infrastructure, the following were examined:
- Impacts to the Web Server;
- Impacts to the Application Server;
- Impacts to the Firewall;
- Impacts to the Database Server.
The specific ramifications of each of the above were examined in both the previous article and this one as well. Assuming that all of these issues have been properly addressed, the next step would be to conduct the actual implementation of the Virtual Private Network Infrastructure. Once this has been done, there is yet another key aspect which needs to be covered the formal testing of the VPN, which will be covered in the next article.
Resources
https://www.rivier.edu/faculty/vriabov/Lab11_FirewallsVPN.pdf
http://download.asustor.com/college/en/NAS_323_Using_Your_NAS_as_a_VPN_Server.pdf
https://kb.juniper.net/library/CUSTOMERSERVICE/GLOBAL_JTAC/technotes/dynamic-vpn-appnote-v12.pdf
http://documentation.netgear.com/fvs336g/enu/202-10257-01/pdfs/LAN.pdf
https://www.hhs.gov/sites/default/files/ocr/privacy/hipaa/administrative/securityrule/nist800113.pdf
http://www.cs.ou.edu/~thulasi/Misc2/papericc06-final.pdf
https://www.di.ens.fr/~fouque/ipsec.pdf
http://ws4.insightdirect.com/Download/Website/docs/ServiceCEO_Virtual_Private_Network_FAQ.pdf
http://www.cs.unh.edu/~it666/reading_list/Networking/firewall_concept_terms.pdf
https://www.alliedtelesis.com/sites/default/files/howto_config_vpn_fw_basics1.pdf
https://portal.threatpulse.com/docs/am/PDFBriefs/BCWSSFWVPN.pdf
Learn Network Security Fundamentals






