Microsoft NAP (Network Access Protection)
In this article we will learn about one of the most important features introduced by Microsoft from the perspective of network access protection (NAP). We will also cover all the main concepts surrounding NAP and various design scenarios and best practices.
Introduction
Network Access Protection (NAP) is a platform to check for all incoming requests to access an internal resource. It allows administrators to establish and develop specific levels of controls to allow network access based on requester identity. The level of access that has been granted to requester and a check against the requester must be in compliance with the organization.
Learn Network Security Fundamentals
Components of Microsoft Network Access Protection (NAP)
Below are the components of a Microsoft NAP solution.
-
Policy server: used to evaluate the health of the requester. It basically communicates with an endpoint agent called the NAP agent to determine the health of that agent. Based on the evaluation of the health of the NAP agent, it is permitted further access. A Windows Server 2008 can be configured or NAP with Network Policy Server (NPS) role service can be installed and configured.
-
NAP capable computer: Under this comes all the requesters which have an endpoint agent termed as NAP agent installed or running.
-
NAP Agent: a service that collects and manages health information for NAP client computers. It is also termed as a health agent. It usually monitors health of components like firewall, virus protection, spyware protection, automatic updating, Security Update protection, etc. The examples of Agents include Windows Security Health Agent (WSHA), System Center Configuration Manager SHA and the Forefront Client Security SHA (FCS SHA).
-
Compliant computer: Under this comes the entire computer in the network which is in compliance with policies set up in the policy server.
-
Noncompliant computer: Under this comes the entire computer in the network which is not in compliance with policies set up in the policy server.
- Health status: This parameter defines the client's configuration state like firewall status, antivirus status, automatic updating status, etc. Based on this parameter evaluation result, requester is allowed access to the network.
Network Access Protection Scenarios
The below section discuss the main access scenarios where an inline Network Access Protection Scenario would check for requester health.
How to check access request health by mobile computers or remote users
As the work scenarios are changing in today's world, many employees connect to their office network while roaming. Such employees can connect from home, airport, coffee shops or guest networks at other businesses. As the network through which they are making a request to access the corporate resources is insecure, it poses a significant level of security risk on the end user as well as the corporate network. Thus there is a need to protect these computers through the deployment of NAP.
NAP deployment will keep the computers updated with the latest corporate policies. Whenever a request is made, the request is parsed by the policy server. Then the policy sever checks the endpoint agent i.e. NAP agent health to determine the configuration status. If the status of the agent is outdated, then the request is initially restricted and all the corporate latest policies and updates are applied onto the requester. Once the device is properly updated with the latest policies, then the request for corporate access is granted.
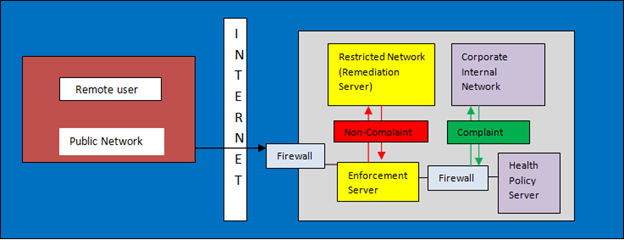
For mobile computers, the NAP protection solution can be divided into two categories.
Defense-in-depth: In this category, prior to leaving the corporate network, all the mobile assets like laptops are properly patched with the latest corporate policies. The policy server evaluates the health of each computer by communicating with the endpoint agent installed on the computer. The policy server evaluates the health of the endpoint agent for components like firewall, antivirus agents, automatic updating status, etc.
IPsec policies: For mobile computers to operate in a secure manner in a public network which is far less secure and is prone to security risks, IPsec policies are enforced. With IPsec, the client computer is configured to communicate freely with other computers when it initiates the connection and also protects the computer from unsolicited inbound communications. IPsec enforcement also provides encrypted communications, authenticated communications, firewall status, antivirus updates, and security updates, etc.
How to protect an internal network including both main and branch offices from non-compliant hosts
Access to the internal network can be protected by restricting access of non-compliant computers. It should be noted here that NAP only provides protection against non-compliant hosts, but it cannot provide protection or restrict a malicious action taken by a NAP compliant host.
With NAP, access restriction means that non-compliant client computers are granted access only to the specified resources. While communicating with the NAP client, if the policy server finds that the NAP client is non-compliant with the network health policy, it is prevented from contacting protected resources either at the point of network access, or for IPsec enforcement, on a peer-to-peer basis. The point of access can be local, remote, or over the Internet. The type of access restriction provided by NAP depends on the enforcement method used. Following are the NAP enforcement methods that can be used for this scenario:
- IPsec Enforcement: It is applied through IPsec policies and provides protect resources by authenticating inbound connections.
-
802.1x Enforcement: It is applied through VLAN or ACL and protects resources by using 802.1x authenticated wireless or wired devices.
-
VPN enforcement: It protects through IP packet filter and protects resources using a VPN connection.
- DHCP enforcement: It protects resources accessed using a IP address provided by a NAP enabled DHCP server.
Each of the above mentioned enforcement methods can be used to provide protection against corporate headquarters as well as branch offices.
While protecting a branch office, an NPS server can be installed locally at the branch site but is managed the NPS server located in the corporate headquarters. There are two types in which the policy can be managed between NPS servers located at headquarters and at the branch office.
-
With centralized policy management, policies are managed centrally and NPS servers at corporate headquarters are configured as NAP health policy servers. If the request is made at the branch office and enforcement mode is chosen to be DHCP or IPsec, then all the requests that arrive at the branch office NPS servers are forwarded to the headquarters NPS server, where the request is evaluated against the centralized policy server. However, if the enforcement method is chosen to be VPN or 802.1x, then there is no need to deploy an NPS server at the branch office. The main advantages of using the centralized policy management is less complexity and lower costs. However, the NAP solution can be seriously affected if there is a connectivity issue between a branch and main office.
- With distributed policy management, NPS servers deployed at the branch office are configured as the policy servers. If the request is made at the branch office and enforcement mode is chosen to be DHCP or IPsec, then all requests that arrive at the branch office NPS servers are evaluated at the local health server itself instead of forwarding to main office health policy server. However, if the enforcement method is chosen to be VPN or 802.1x, then there is need to deploy one or more NPS server at the branch office. The main advantages of distributed policy management is that it is less affected by the connectivity issue between branch and main office, but on the downside, it is more complex and it involves more costs.
Policies to protect corporate assets from unmanaged computers
Corporate assets must be protected from unmanaged computers, as the unmanaged computers are prone to security risks such as virus and other malwares. With NAP, network administrators can enforce health requirements for both managed and unmanaged computers that connect to the network. Health requirements for unmanaged computers can be different from requirements for managed computers. Access to the resources on the corporate LAN can be restricted to only users who meet the conditions you specify, such as membership in a user group, the remote access server used, or compliance with a specific health policy. Some of the policy conditions that can be configured to protect the network from unmanaged systems are:
Learn Network Security Fundamentals
-
Guest VLAN policy: Non-domain hosts that do not authenticate against a domain must be put in a guest VLAN. Their access should be restricted to Internet only and must be prohibited from accessing the Intranet.
-
VPN policy: Hosts that do not join the domain but are compliant and authentic must be placed as per the VPN policy. If the host is authentic against a domain account but is non-compliant, it should have access to the remediation server which will be used to enforce all the updates on the host to make it compliant. Compliant hosts must be given access to the Intranet as well, but the non-compliant hosts must be treated like guests until they are made compliant by the remediation server.
- Local user policy: This policy must stand for those which are in local LAN and is fully compliant with the policy server and is authentic against a domain account. They must have full Intranet access. Non-compliant servers must be granted access to the Internet and remediation server only and should be granted to Intranet only when made compliant by the remediation server.
Conclusion
Thus it can be concluded that NAP can be used to protect corporate assets against remote users or mobile computers, unmanaged hosts, etc.
References
-
msdn.microsoft.com/en-us/library/dd125338(v=ws.10).aspx






