GFI LanGuard – Network Security Scanner
Introduction:
In a corporate environment, every computer connected to the network poses a security threat. As more and more computers get added into the network each day, the security risk associated with them only increases further. There is an imminent need to make sure that these computers are patched so they don't have any security holes which can be exploited by an attacker.
Learn Network Security Fundamentals
The burden of maintaining several tasks related to every system is huge, and verifying that every system is secure is very troublesome. This is where tools like GFI Languard come to the rescue. This article provides details about GFI Languard which can be used for network vulnerability assessments, patch management, security compliance and more.
Features of GFI Languard:
-
Vulnerability Assessment of Network
-
Security Compliance
-
Patch Management
-
TCO reduction
-
Change Management
-
Asset Inventory
-
Automatic Remediation
-
Network/Software Audits
How to install:
Visit http://www.gfi.com/network-security-vulnerability-scanner, click on free trial, provide the necessary information, and then download the setup. The trial key will be sent to the email address you provided, so make sure you use valid credentials. After downloading, double click the setup file to install, which is pretty simple and straight forward. Launch GFI Languard once it's done. The home screen looks like this:
GFI Languard has a lot of options, and there are many features to discuss, but we will focus on the main things going forward.
Scanning the Network:
You can scan your network to identify security vulnerabilities in the connected systems. But before scanning the network, you need to pick a scanning profile first.
Scanning profiles enable you to scan the target systems and look only for specific information based on the profile selected. For instance, a scanning profile you might choose for your DMZ may be different from the one you choose for the internal network. These profiles help your vulnerability program to focus on a specific area of interest, say open ports or security updates. This flexibility helps you to quickly identify your concerned area of interest and get the information.
Also, you don't have to reconfigure them every time; you can just select a profile and then quickly go ahead. You can use the default scanning profiles listed or you can create a new one. Some of the scanning profiles include Full Vulnerability Assessment, Full scan, Top SANS 20 Vulnerabilities, Missing Patches, Port Scanner, Network Discovery and Critical Patches etc. Each name suggests much of the information about each profile. GFI LANguard can also detect whether a scanned machine is real or virtual, and it supports VMware and Virtual PC software.
To start a scan on any host, Click Home à Launch a Scan. Enter your scan target (local host in this example), select a profile (say full scan), and then click 'scan' to scan with the current logged in user. Note that an alternative set of credentials can also be provided if you do not want to scan with the current account. The results would be displayed on the right pane of the screen as highlighted below. Vulnerabilities are classified as high, medium, low, potential, etc.
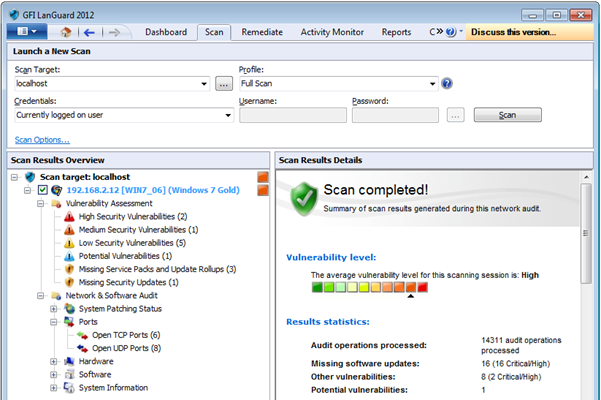
Analysing Scan Results:
As shown above, the vulnerabilities found are displayed along with their. You can expand them further to gain more information about individual results. Similarly, different results will be displayed based on the underlying policy. Scan results are divided into 2 categories – Vulnerability Assessments and Network & Software Audit. Vulnerability assessment includes high, medium, and low vulnerabilities as well as missing service packs, missing security updates, etc. Network & Software Audit contains system patching status, open ports, system information, etc. System information would give details about shares, registry, NetBIOS names, services, audit policy, etc.
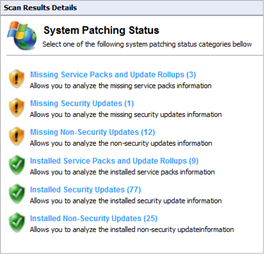
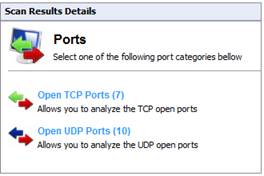
Scan results can be saved by clicking on File → Save scan results, and they can be loaded later on. The files are stored in the GFI Languard database.
Remediating Vulnerabilities:
Remediating the identified vulnerabilities can be done either manually or automatically depending on the underlying issues. In automatic remediation, you can automatically download and deploy missing patches, uninstall unauthorized applications, configure end user reboot and shut down options, and many others.
The 'Remediation Center' allows you to fix the issues found during a network scan. It can be accessed under the Remediation tab. Software updates can be deployed with a single click by selecting the computer and the updates. Similarly, unauthorized applications can also be uninstalled by simply selecting them and clicking uninstall. The tool also automatically downloads patches and service packs, and it can also deploy these updates all over the network, as well as recall any patches that were deployed.
The Malware Protection section can be used to remediate vulnerabilities related to malware on specific systems. With this you can scan the target machines for spyware, viruses etc. There is also 'Remote Support' through which you can control computers remotely using Terminal Services and remote desktop protocol. Using this, you can install missing patches, service packs and any other software through a remote connection.
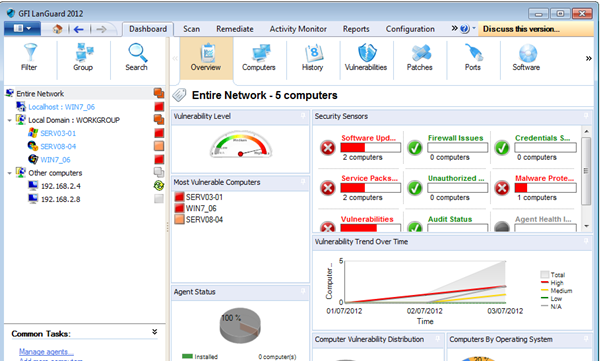
Dashboard:
The Dashboard is an important section to know about, as it displays the data that has been gathered during the scan or audit process. It provides you information about the number of computers connected to the network, vulnerable systems, overall network vulnerability level, etc.
Below is the screenshot referenced from GFI Languard. There are several options present under this. For instance, the actions tab enables you to manage and remediate vulnerabilities. It contains the following options: 'Remediate' to manage missing patches; 'Acknowledge' to acknowledge the issues reported; 'Ignore' to ignore the reported issues so that they will not be shown in the vulnerabilities section; 'Change severity' to change the severity of the reported vulnerability; and 'Rules Manager' to manage configured rules.
Deploying the Agents:
You can deploy the agents automatically on newly discovered computers or on selected computers. The main advantage of deploying agents on systems is it reduces the audit time and also helps preserve the network's bandwidth.
To use this feature, click on Configuration tab → Agent Management. Click on Deploy agents and select the target computers to add. To deploy the agents manually, select Dashboard → Common Tasks → Add more computers and select the systems to add. Right-click the newly added computers in the computer tree to select the computers, and then from the Agent Status, click Deploy Agent. Fill the rest of the details and you will succeed in deploying the agent.
Activity Monitoring:
Click on Activity Monitor tab and you will find the sections Security scans, Software updates download, Remediation Operations and Program updates activity.
Security scans section helps you to monitor the current state of all the scans which are in progress. You can filter the scans to monitor only using the available filter. You can also stop a particular scan.
Software updates download helps you to manage scheduled patch downloads. Using this, you can monitor, stop, pause or change any priority of the patch downloads.
Remediation Operations allows you to monitor and also abort certain remediation operations which are planned.
Program Updates gives you a comprehensive view on the history of updates, including the time, status and the file name of each update.
Reporting:
The Reporting tool enables you to generate both text and graphical reports based on the information obtained from network security scans. You can generate technical reports as well as executive reports, which can both be viewed by the higher management for a comprehensive understanding. Click on the 'Reports' tab and find that there are several kinds of reports – General reports, PCI DSS Compliance Reports, HIPAA Compliance Reports, SOX Compliance reports, etc.
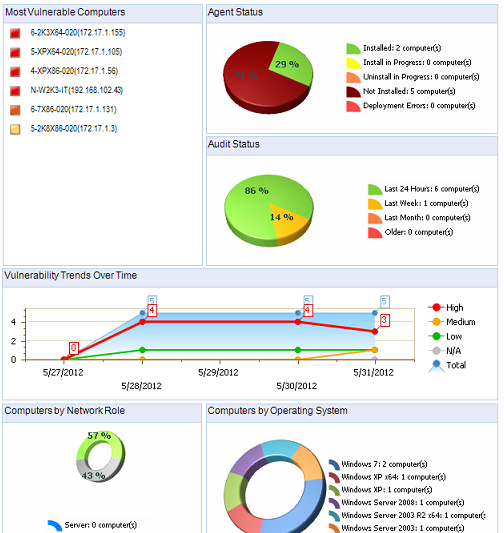
To generate a report on network security overview, select General à Network Security Overview and click generate report. The report would include details about network vulnerability level, most vulnerable computers, agent status, audit status, operating systems in use, etc. Below is a sample screenshot of how the report looks like. You have the option of automating the task of generating the reports and sending you the copies. This can be done under Reports → Actions → Schedule New report.
You can create new reports based on the settings of an existing report. This helps save time and also enables you to use existing reports so that the report generated matches your requirement.
Script debugger:
There may be some custom vulnerabilities which can only be identified by creating specific scripts. GFI Languard lets you create custom scripts using VBScript compatible language or Python.
Launch the script debugger to create a script and then save it in Languard's installation path. Now go to Configuration → Scanning Profile Editor. Under the list of vulnerability checks, click on 'Add ' to add a new vulnerability. Click the conditions tab and click on Add button. Now select the VBScript note and choose your own custom script file which needs to be executed by this check. Now you can scan the systems with the scanning profile where the script is added.
Utilities:
Utilities tab provides access to the following tools which come in handy when you are analysing the network. Below is a description about the available tools:
DNS Lookup:
This tool resolves domain names into the corresponding IP address and shows you detailed information about the target domains. Specify the hostname to resolve in the Hostname/IP to resolve textbox and click on 'Retrieve' to view the results. Also, you can click on options to modify the results based on your interest. It contains details about basic information, host information, aliases, MX records, NS records, etc.
Traceroute:
Traceroute identifies the path to reach a particular target. Enter the target domain name and click on traceroute. The tool enumerates the IP addresses of the traversed computers, the number of times each computer was traversed, and also the time it took to reach one system from another.
Whois:
This shows the information of a particular domain such as administrative contact, registration service provider, etc.
Enumerate Computers:
Identifies domains and workgroups present on a network, their underlying operating systems, and any other information which can be obtained through NETBIOS. You can use this tool to launch a security scan on the identified systems. To do this, just right click on any system and click scan. Similarly, this can be used to deploy custom patches and third party software on enumerated computers.
Enumerate users:
This can be used to scan the active directory and retrieve the list of all users. This tool can be used to enable or disable the identified user accounts.
SNMP Audit:
This tool identifies and reports weak SNMP community strings by performing a dictionary attack using the default values. However, you can edit the community strings file by using a text editor use other dictionary files to accomplish the same. This can be done by specifying the path to the dictionary file that you want to use from the tool options at the right side of the management console. SNMP activity is generally blocked at the firewall level so that internet users cannot SNMP scan your network. Unless this service is required, it is highly recommended to disable it.
SQL Server Audit:
Using this tool, you can test the password vulnerability of the root administrator (i.e. super admin account), and any other SQL user accounts configured on the SQL Server. During the audit process, this tool will perform dictionary attacks on the SQL server accounts using the credentials specified in the passwords.txt dictionary file. However, there is also the option of directing the SQL Server Audit tool to use other dictionary files.
Conclusion:
This article is all about the network vulnerability scanner GFI Languard. We have seen how to use the tool to scan the network, monitor its activities, and remediate the vulnerabilities discovered. We have also discussed the other features which are available in this tool to make your network more secure.
Learn Network Security Fundamentals






