AAnval - SIEM by Tactical Flex
Aanval by Tactical Flex is an event correlation tool also known as a SIEM. Many governmental agencies require a centralized login system to retain and correlate logs from all servers. Other security minded or large scale production environments also benefit from having SIEM as a way to automate logging and auditing. Aanval meets and exceeds SIEM requirements in web-based easy to use software Tactical Flex refers to as a SAS (Situational Awareness System).
Learn Network Security Fundamentals
With Aanval, traditional Linux syslogs for various applications and servers can be piped together to collect and aggregate a large dashboard view of your entire infrastructure's status. Aanval can also operate using Snort to correlate real time IDS/IPS logs and create alerts as needed from various vendors such as Cisco, Barracuda, and others.
The real world use of Aanval can be for a variety of situations: email alerts when a rogue device comes online, alerts of a certain database or apache error, rogue login or authentication attempts, as well as general charts and graphs to report on network security status system-wide.
Community and Commercial Versions
Aanval offers a free version, limited to one sensor, which is sufficient for demo purposes. Commercial Aanval is unlimited for the number of sensors and can monitor ssh, http, and other security-sensitive connections. The commercial version also includes full technical support for the product.
BYO LAMP Server
Aanval installs onto a traditional Linux, Apache, MySQL, and PHP server better known as a LAMP stack. CentOS Linux is recommended, though Aanval can work fine on any current Linux distribution. Also supported is Mac OS X with proper Apache, MySQL and PHP software installed. To install Aanval, some general knowledge of creating MySQL databases and placing the Aanval software in a valid Apache directory is needed. As long as you follow the vendors' documentation, you shouldn't run into any problems setting up.
SIEM
Like other SIEMs, Aanval works by creating an entry into a database for each event - be that a syslog log event or snort event. These events can then be categorized, tagged, and processed as desired by the Aanval software. Some of the features that Aanval brings that makes it unique includes scheduled port scanning with nmap, active geo-location to map locations of traffic sources, something referred to as Situational Awareness - a way to identify high risk areas in a network, as well as various reporting options and customized email alerts. It is the entire package.
Sensors: Monitor via snort or syslog
Aanval has two modes of collecting data. One is via software known as snort. Snort is the industry standard for IDS or Intrusion Detection System used by many hardware vendors. Snort is an open source software that provides real time packet analysis and network intrusion detection. By configuring Aanval to use snort as a sensor, real time network traffic analysis is recorded into Aanval on the fly.
The other mode of collecting data in Aanval is via syslog. Syslog is a Linux and UNIX standard for logging all services such as sendmail, apache, mysql, ssh logs, and any other type of system logging. Syslog has a feature to point or redirect its logging to a central log server. It is this configuration that Aanval takes advantage of in order to collect logs in real time.
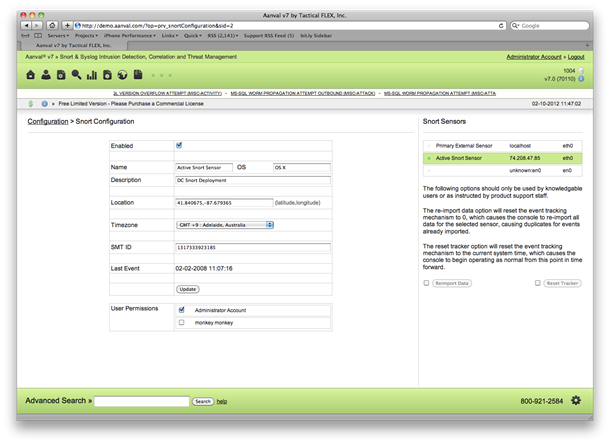
Home Screen and Live Monitor
Once all sensors are configured and are recording data in Aanval, it is now possible to view the data and begin to organize various options.
The Home screen provides a snapshot into current activity including the number of events occurring for all sensors. This is complemented by another view, the Live Monitor view (third icon from the right).
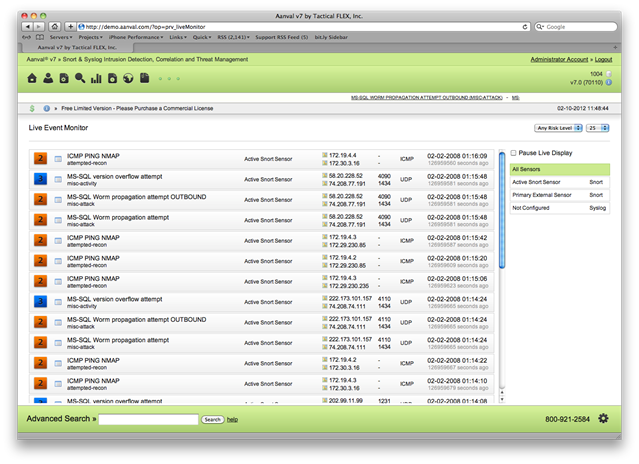
In the Live Monitor view, events scroll by in real time. This is understandably a secondary screen and not the home screen as in a large deployment a live view of events will scroll by a ton of data and information and may not be ideal for a quick overview.
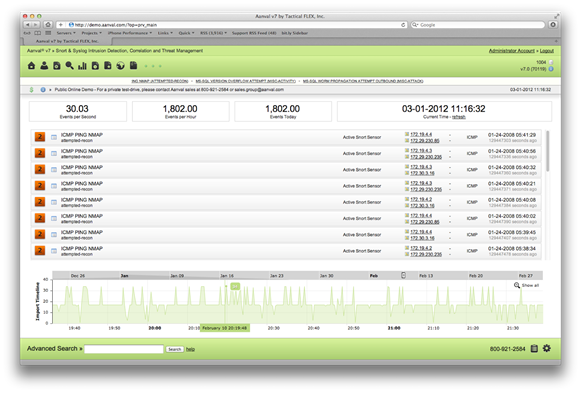
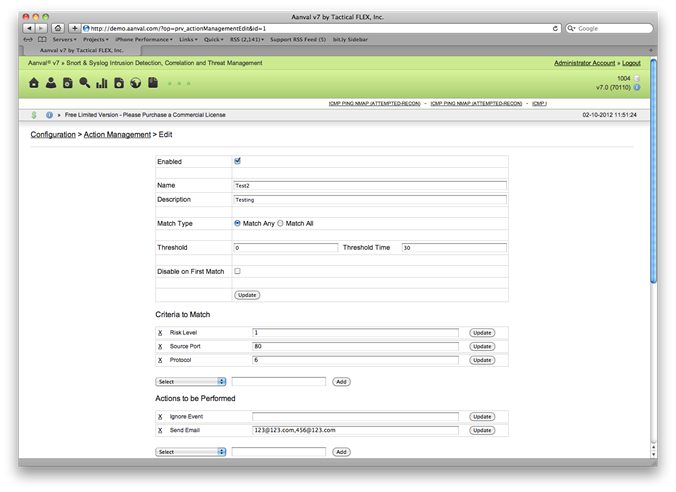
Action Management
Rules and alerts can be created based on certain events occurring. Say that level 1-3 gain no alerts but at 4 or 5, all of the IT staff is notified. For another example, if an apache system warrants a level 5 alert, Aanval sends an email to the apache admin.
Apart from email based on events, Aanval can also perform custom actions including running shell scripts based on a particular event. Imagine if apache or another service is having trouble, Aanval could have an automated action management rule to restart apache on that system.
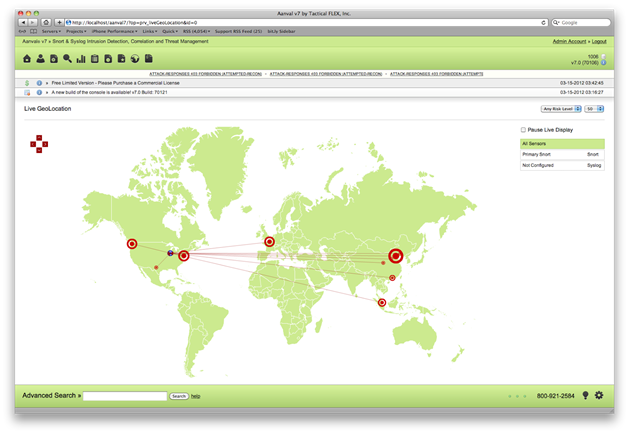
Reporting Options
One of the biggest strengths of Aanval compared to other SIEM solutions is the vast array of reporting options. A visually stunning view is the Live GeoLocation view which provides a real time map of clients connecting to the network.
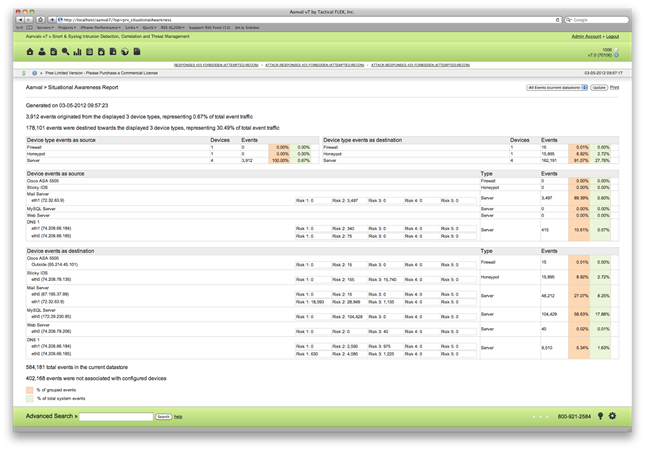
A single click from the top menu provides a Situational Awareness Report. This report can be generated for the last 12 hours, last 24, all the way to report on all database data. In printable view, this is a clean report that can be provided to IT management or IT staff in a quick easy summary of network activity.
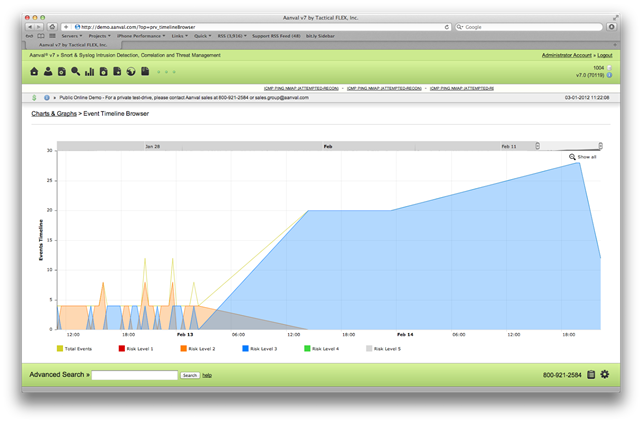
Continuing with reporting, under Charts & Graphs, various options are available including an Event Timeline Browser. This charts out the number of events over a given period of time to easily identify high activity on a network. A real world use of this is that when network attacks or problems occur, it is often difficult to find out when the intrusion began. By graphing events over time, specific time windows can be easily identified of the entire incident window.
Another useful chart is Frequent Offenders. This easily identifies individual IPs which raise most alerts as recorded by Aanval. As a bonus, the IP addresses are mapped in a geographical map to identify their origin.
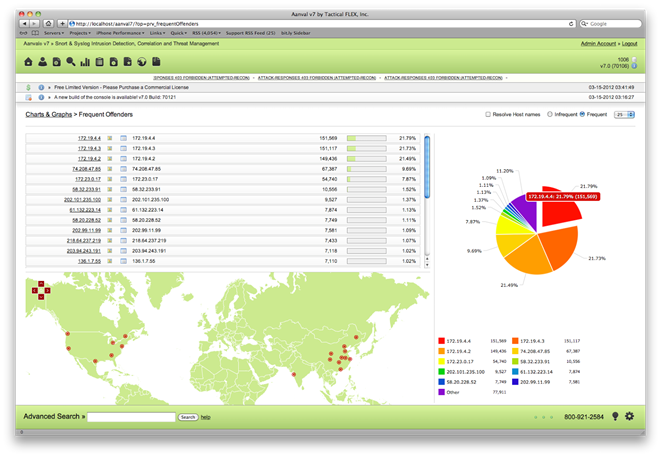
Also noted, general reports of any data in Aanval can be produced from a specific search. Search for risk level 5s, a single specific IP range, and generate. The resulting reports can then be downloaded as HTML, plain text, or XML. The XML output in particular makes the Aanval data easily portable to other systems or data storing.
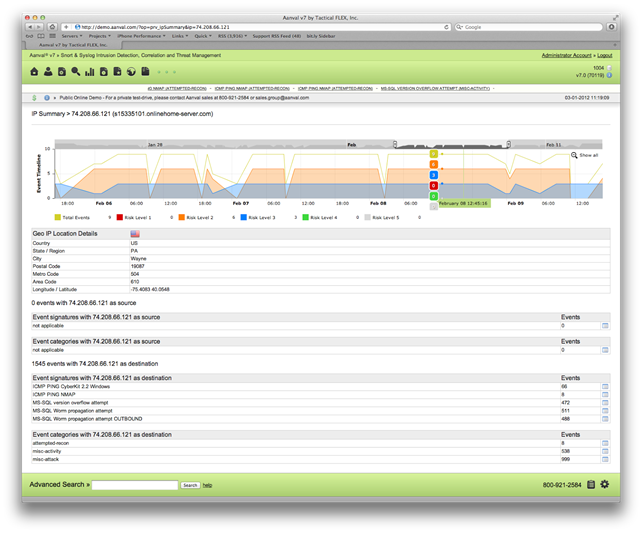
One last view to mention – individual IPs can be selected to show an IP Summary. This is helpful to show what data Aanval has collected on the IP including Geo IP data, events, and events graphed out by risk level.
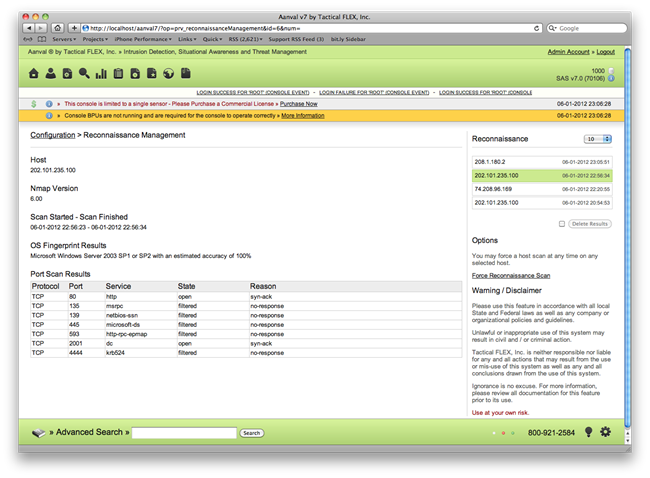
Integrated nmap
As a bonus, Aanval provides a quick and easy way to scan IPs with nmap. Note that nmap must be installed on the host computer, and that host must have proper routing in place to reach all targets. This is extremely helpful to quickly map out running services and open/closed ports on a particular host without the need to open a terminal.
Summary
In all, Aanval provides an extremely polished event correlation system with high-quality reporting and other options. The ability for it to pull in data from both snort and syslog then provides geo IP information is a very attractive feature. Aanval can record 1,500 events per second and can scale with appropriate hardware to record as many as 5,000 events per second. It can also import and export data to OSSIM, which is great for users migrating to Aanval or working with other network monitoring setups. Aanval is provided as downloadable software to run on your own Linux server but also offers a hardware appliance version that runs on dedicated Apple OS X hardware.
The need to have a quick view of network activity or events is necessary today, not only for external activity but also internal network monitoring. Aanval provides a very compelling product which should absolutely be considered as a choice when looking at a SIEM solution. For more information, see the Aanval website: http://www.aanval.com .
Learn Network Security Fundamentals
A live working demo is available at http://demo.aanval.com with the credentials root / demo.






